During the past few days we have noticed a higher than usual number of malvertising attacks pushing the Magnitude exploit kit – which had been relatively quiet – to drop ransomware.
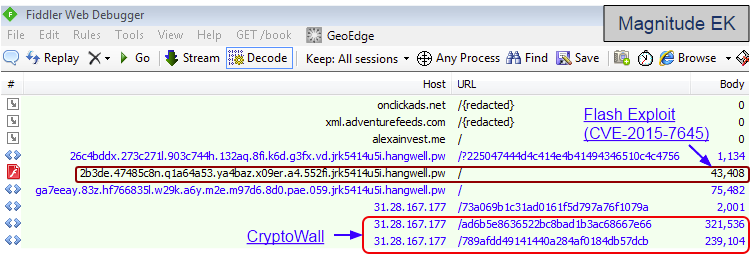
Magnitude EK is one of those exploit kits we don’t hear about as much in comparison to others such as Angler EK or Nuclear EK. Its unique URL pattern makes it easy to spot from the clutter of network traffic captures because it uses chained subdomains typically ending in a shady Top Level Domain like pw (Palau Pacific island).
Some of the ad networks involved in this malvertising campaign include:
- RevenueHits
rvfrm2006.com/adServe/sa?cid=11021-110100501933000000&pid=11021&q=ANUBiH%20-%20Prijava&ap=cmp%3DPOPUNDER clkdeals.com/adServe/getTag?pid=11021&type=inject&cid=110100501933000000&appName=GoHD&q=id195.ea7u.c0.d6177f.53f.j2cb5n.8c974r.xe02c5.j19s72w2gq9.whatplea.pw
- VisAdd
a.visadd.com/internal/reporter?v=2&subid=110100501933000000&format=0&ai=990&ctxu=http%3A//id195.ea7u.c0.d6177f.53f.j2cb5n.8c974r.xe02c5.j19s72w2gq9.whatplea.pw/&fb=false{redacted} - Propeller Ads Media
onclickads.net/?auction_id=d1586e4cbe6a34cf&zoneid=26518&pbk2=97419d16d0b3957f090d85f852f50a5c6216021660945859924&r=%2Foc%2Fhan
Perhaps this increased activity is due to the fact that Magnitude EK is the third exploit kit to leverage the latest Flash Player vulnerability (CVE-2015-7645) recently patched by Adobe.
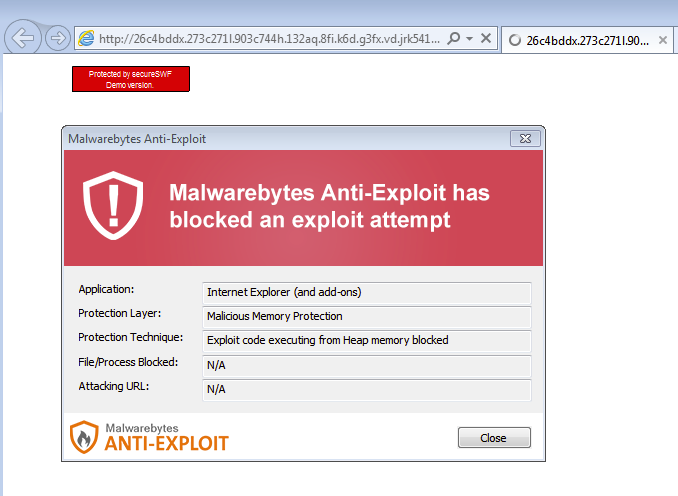
CryptoWall was dropped via two separate malware binaries. Malwarebytes Anti-Exploit users were protected against Magnitude EK and never got to see the malware payload.










