Vonteera is an adware family that has been around for years. They stand out from the rest because of their very intrusive changes to the affected systems, which is why you will see them classified as Trojan by some anti-malware solutions.
Recently, they added a new trick to their arsenal: using system certificates to disable anti-malware and anti-virus software.
Intrusive
What are the main changes they make on your system, you ask? Well, for starters they add a whole bunch of Scheduled Tasks.
All the tasks shown above were created by one Vonteera installer.
Some are created to show you advertisements on a regular basis. Typically, they open a new tab in your default browser.
Besides the Scheduled Tasks, a Service also gets installed.
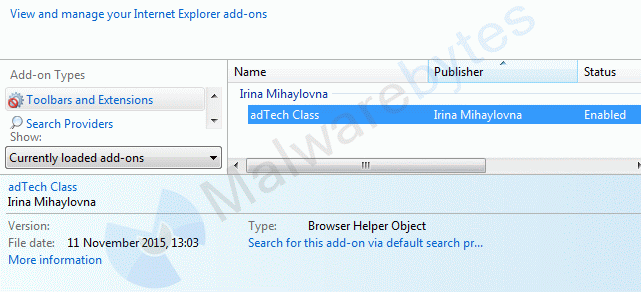
R2 AppInf; C:Users{username}AppDataLocalHofferappinf.exe [242688 2015-11-19] () [File not signed] On the browser side, a new Browser Helper Object (BHO) can be found in Internet Explorer.
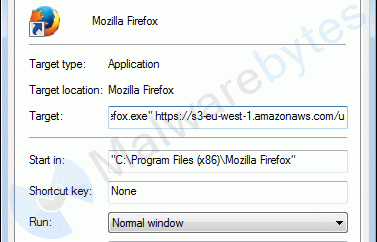
Also, the PUP alters all the shortcuts on your desktop, in your taskbar (Pinned), and in the Start-menu for every browser I have tried, which were:
- Internet Explorer
- Firefox
- Chrome
- Opera
- Safari
It alters them by adding a URL in the Target field.
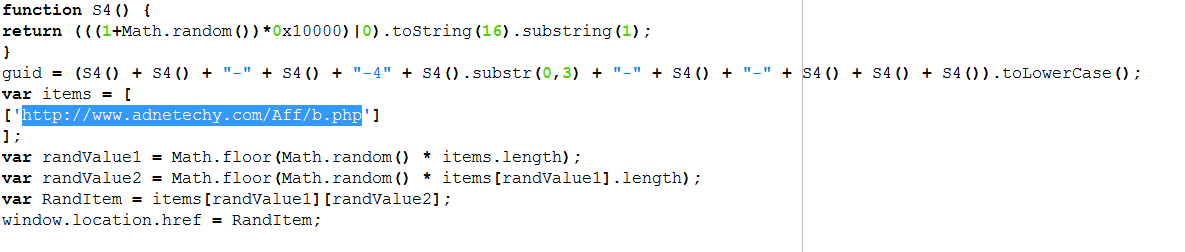
The URL points to a site which contains this script to randomize where users can be re-directed next.
Chrome “superpower” policy
For Chrome, this PUP has a special treat as it enables PoliciesChromiumExtensionInstallForcelist which, and I quote, “Specifies a list of apps and extensions that are installed silently, without user interaction, and which cannot be uninstalled by the user. All permissions requested by the apps/extensions are granted implicitly, without user interaction, including any additional permissions requested by future versions of the app/extension.” That is not something I would grant any app or extension even if I trust it, since it opens up a whole bunch of attack vectors for anything malicious.
… and then the certificates
Now for the reason why I personally feel it stepped over the line between potentially unwanted and malware: The installer for this adware drops 13 certificates in the “Untrusted Certificates”. They are (in listed order):
- “ESS Distribution”
- AVAST Software a.s.
- AVG Technologies CZ
- Avira Operations GmbH & Co. KG
- Baidu Online Network Technology (Beijing) Co.
- Bitdefender SRL
- ESET, spol. s r.o.
- Lavasoft Limited
- Malwarebytes Corporation
- McAfee, Inc.
- Panda Security S.L
- ThreatTrack Security
- Trend Micro
The effect of this is potentially devastating since your system will refuse to run any applications signed with these certificates.
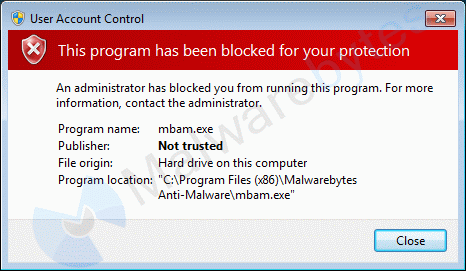
This is what happens when the certificate is listed as “Untrusted”.
Nor will it allow you to download anything from the sites that use any of these certificates.
The AppInf service mentioned earlier makes sure that the certificates are present. If you remove them, you have to be fast, because the service puts them back. To bypass the use of certificates, users have to disable UAC (not a good idea) or use a trick to circumvent it. Personally, I used the “Task Scheduler trick” to get Malwarebytes Anti-Malware to run.
Another option is to go into Certificate Manager and delete the certificates that were classified as “Untrusted” by Vonteera.
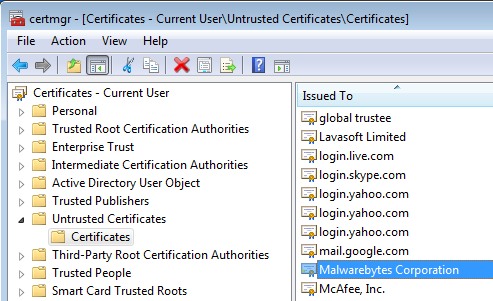
Procedure:
Use Winkey + R to open the Run box.
Type or Copy & paste certmgr.msc Click ok to execute the command and the Certification Manager Window will open. Select the Untrusted certificates > Certificates and you should see something like the above.
You can delete certificates from this list by right-clicking on them and then choose Delete.
Make sure to check back on the certificates after you have removed the adware, since they might have been re-instated in the meantime.
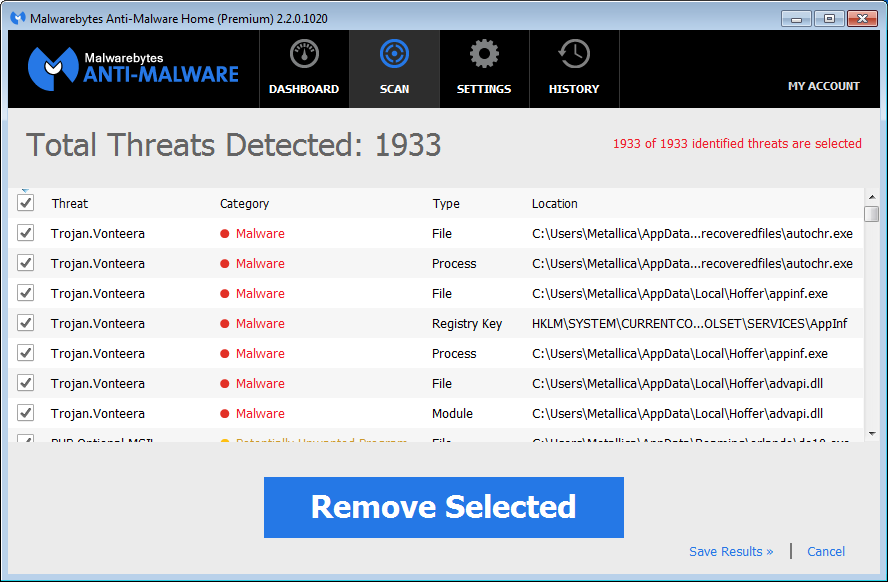
Malwarebytes Anti-Malware detects the elements of this infection as PUP.Optional.Vonteera, PUP.Optional.AdFactory, PUP.Optional.Convertor, PUP.Optional.AdNetwork, PUP.Optional.WinKit, PUP.Optional.NoVooIT, PUP.Optional.Hoffer, PUP.Optional.MSIL and PUP.Optional.AdTech. This may change however if we decide to classify this as something other than potentially unwanted.
[Update]
Effective immediately, the detection for the Vonteera adware has been changed to Trojan.Vonteera.
Be careful out there, the internet can be a jungle.
Pieter Arntz











