Update (12/03): AdXpansion contacted us with the following statement:
Adxpansion can confirm that these ads were disabled within hours of first being reported but, unfortunately, our compliance efforts were unable to prevent the malvertiser from creating new accounts.
We work with the world’s leading security vendors, including RiskIQ, in an ongoing effort to fight malvertising. In light of this recent incident, we are reviewing our compliance processes and have stopped supporting flash ads completely. We are committed to provide a safe environment for all parties working with us.
– –
While malvertising activity on adult sites has been ‘relatively’ quiet for some time, we started picking up dozens of attacks on moderately popular XXX portals, where moderate still means millions of daily visitors.
The modus operandi is quite straightforward and facilitated by a compromised Flash advert directly hosted and served by AdXpansion, an adult ad network, which triggers a hidden Flash exploit loaded from a seemingly innocent XML file. This technique has been used before in other self-sufficient Flash ad/exploit attacks.
This malvertising campaign has been running since at least Nov 21 and is affecting hundreds of adults sites. As soon as the rogue Flash advert is displayed in the browser (no click on it is required) it will attempt to load the exploit code.
Notable sites that were affected include:
- drtuber.com (55.3 M)
- nuvid.com (41.9 M)
- eroprofile.com (14M)
- iceporn.com (6.9M)
- xbabe.com (4.2M)
Monthly traffic in millions, according to SimilarWeb.
The malicious advert:
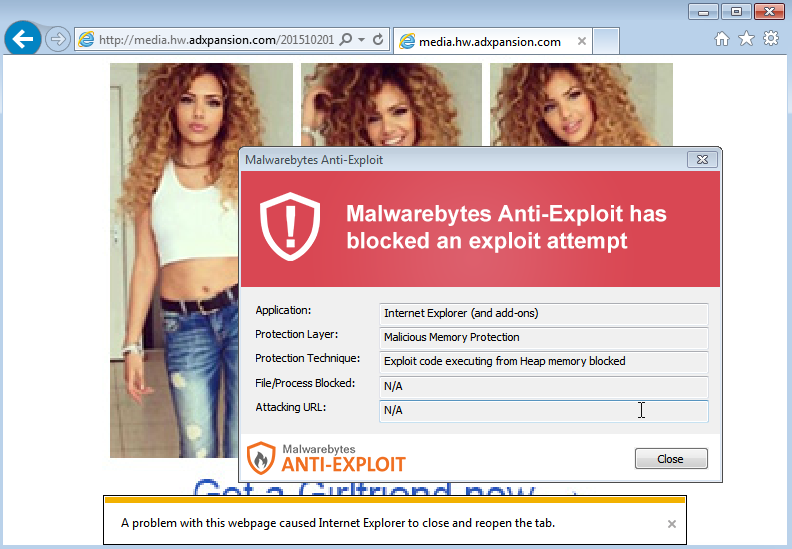
Malwarebytes Anti-Exploit blocks the malicious advert when it attempts to load the remote exploit shell code.
Technical details
An attack ondrtuber.com
:
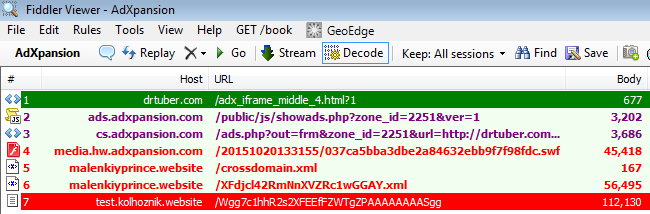
The Flash exploit resides inside of the second XML file loaded from malenkiyprince.website.
Same attack on iceporn.com distributes two different payloads at once:
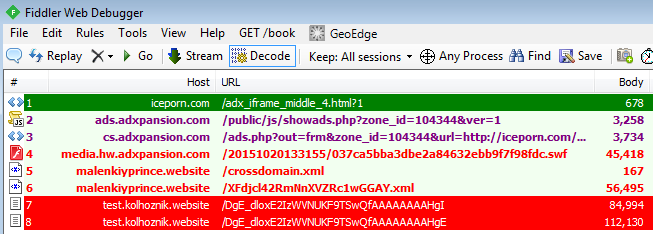
The decoded Flash exploit (CVE-2015-7645):
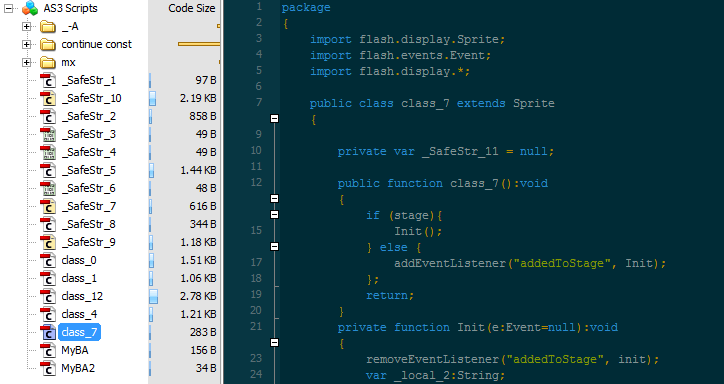
We informed AdXpansion but have not received any response so far.
IOCs:
Malicious advert:
- media.hw.adxpansion.com/20151020133155/037ca5bba3dbe2a84632ebb9f7f98fdc.swf
- MD5: 037ca5bba3dbe2a84632ebb9f7f98fdc
:
- malenkiyprince.website/XFdjcl42RmNnXVZRc1wGGAY.xml
- MD5: f2145598b40e0b0506e6cb4b15513efd
- Decoded SWF MD5: 146d4f6d149c1b0613e1be3f3a777eab
:
- drtuber.com payload: 4bee00fbaede53b7b83192867717289c
- iceporn.com payload (1/2): f502ecb0e450df366fb110d102f34ce0
- iceporn.com payload (2/2): 3f7f1b51bdaccd3931ff78c154bda0b8










