Rogue advertisers are increasingly able to defeat various ad networks which is not good news for publishers and their visitors. It means more booby trapped ads will be delivering malware on people’s computers via drive-by download attacks.
As always, this malvertising campaign we uncovered goes through multiple layers and ultimately redirects to a domain that belongs to ad platform SmartyAds. Rogue actors are leveraging SmartyAds by creating fake identities and legitimate looking websites which hide a complex infrastructure of conditional traffic redirection.
Indeed, if you visited the ad page directly or without the proper referer, you would only see a benign advert. This is the legitimate façade that these criminal actors want ad networks to see. In fact, they are so good at it that without actual proof of malicious activity, it’s difficult to find anything wrong with them.
However, there are certain signs on the surface that should raise some alarms. We’ve found out that most of the rogue advertisers are leveraging the CloudFlare infrastructure to hide their backend server and encrypt their traffic as well, along with using anonymous proxy registration details for the domain.
Granted, more and more ad networks are serving ads over HTTPS and the use of CloudFlare does not equate to malicious activity. This is nonetheless something to keep in mind when dealing with those actors as it is part of their modus operandi.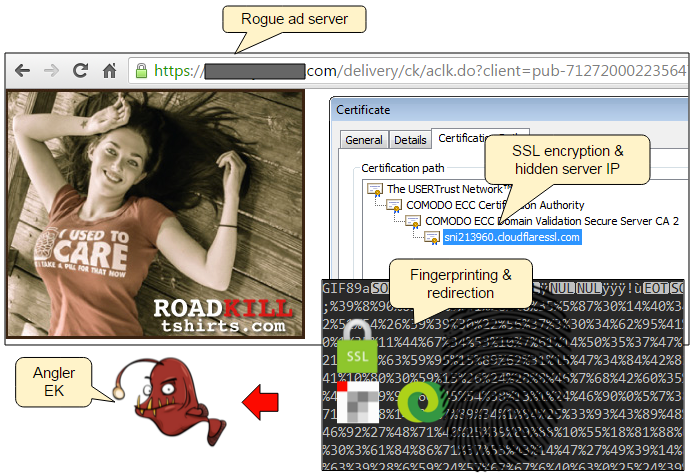
Here are some of the top publishers we found that were affected in this particular malvertising campaign.The average CPM (cost per thousand impressions) of that malicious ad was a mere $0.14. This clearly shows why malvertising is an efficient and cost effective practice.
- rottentomatoes.com 39.1m
- makeuseof.com 28.6m
- lifebuzz.com 22.6m
- fanatik.com.tr 11.6m
- autoblog.com 8.4m
- boredomtherapy.com 6.8m
- leagueoflegends.wikia.com 6.1m
- blitz.bg 5.8m
- jpost.com 4.4m
- …
Traffic in millions of monthly visits, according to SimilarWeb.com.
Traffic flow (example of malvertising on Jerusalem Post):
-
nym1.ib.adnxs.com/if?e={redacted}&referrer=http%3A%2F%2Fwww.jpost.com%2F -
ads.contextweb.com/TagPublish/GetAd.aspx?tagver=1&ca=VIEWAD&cp={readacted}cwu=http%3A%2F%2Fib.adnxs.com{redacted}%26size%3D300x250%26referrer%3Djpost.com{redacted} -
us-nj-e2.traffictradinghub.com/?t=s&winbid=0.16&k=2de91613dd5fbf044ab185dac78d3e13
-
88.214.193.234/?t=win&bwpr=0.16&cd=21717391e4f0194f68e253f606a6e57a&u=http%3A%2F%2Fus-nj-e2.traffictradinghub.com%2F%3Ft%3Ds%26winbid%3D0.16%26k%3D2de91613dd5fbf044ab185dac78d3e13
-
{redacted}/delivery/ck/aclk.do?client=pub-7127200022356478&format=300x250&click=${CLICK_URL_ENC}&output=html&h=60&cb=17475&slotname=391b823acc -
Redirection to Angler EK
When the right user lands on the ad page, the malicious code is triggered to perform a series of checks on this new potential victim. If the conditions are met, a redirection to the Angler exploit kit is performed, ultimately loading a series of exploits and malware.
We have notified SmartyAds and AppNexus about these incidents and will continue to monitor and report them accordingly.
Malwarebytes Anti-Exploit detects the malicious code pushed by these rogue ad servers and ultimately blocks the Angler exploit kit.










