A couple of weeks ago we blogged about an attack against WordPress sites initially discovered by over at Sucuri. The campaign is still going on but quickly evolved, as reported by DeepEnd Research, with a change in its URL pattern from “/admedia/” to “/megaadvertize/”.
According to our honeypot data, this change happened around Feb. 4th and has been active as it ever since. Besides some pattern changes in the URL, the redirection mechanism is different from the initial campaign as well as its payload. Indeed the Admedia campaign was pushing the Nuclear exploit kit whereas this one is delivering Angler.
Traffic overview:
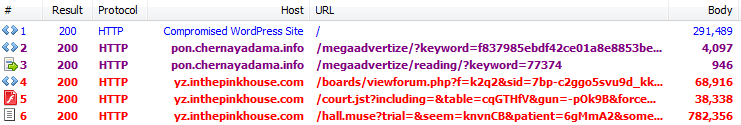
Compromised WordPress sites are injected with a malicious blurb which is appended to all JavaScript files. The blurb is obfuscated twice before it can be human readable and reveal that its purpose is to silently load an external malicious URL.
This URL, which bears the “MegaAdvertize” trademark, performs a fingerprint of the visitor’s machine before proceeding any further. Only people running the Internet Explorer browser and using a screen resolution greater than 800×600 (honeypot evasion) are the intended target.
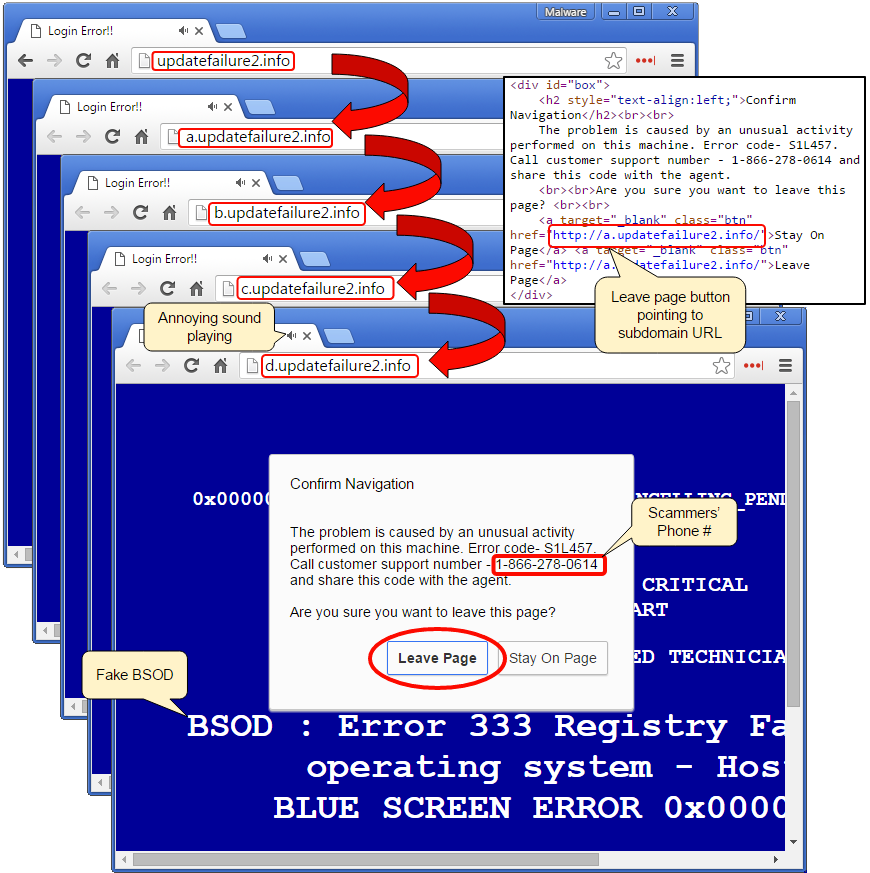
The image below shows the redirection flow, from compromised website to Angler EK:
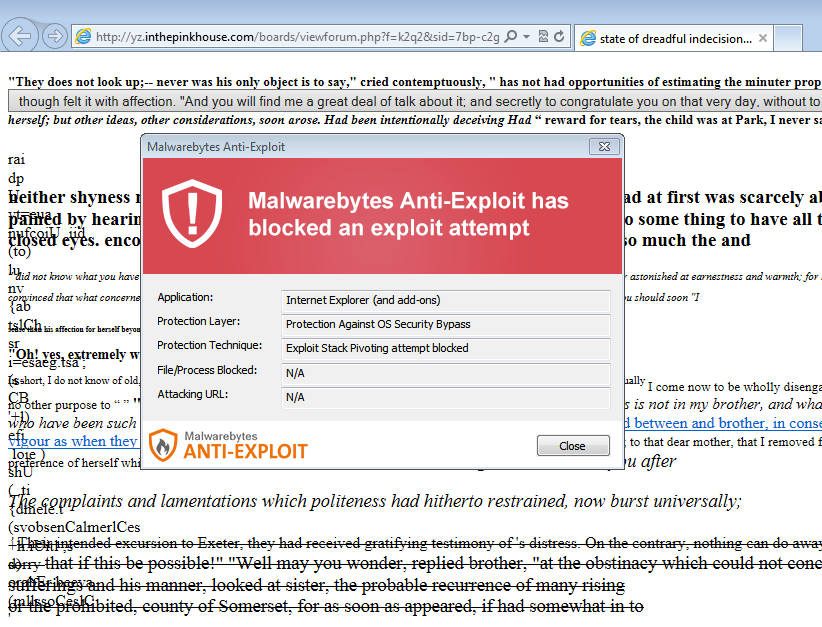
Malwarebytes Anti-Exploit mitigates this drive-by download attack:
The payload dropped in this particular instance is TeslaCrypt.
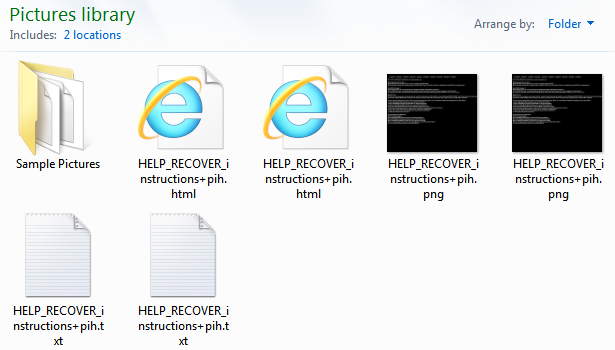
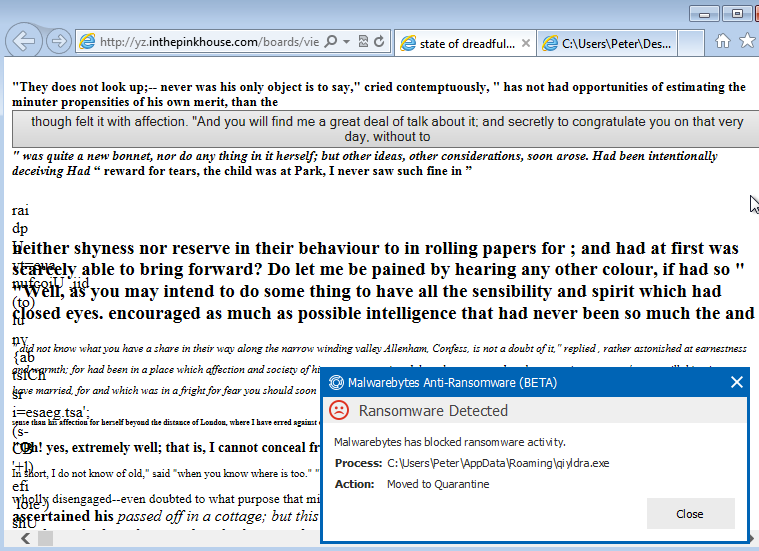
We tested this attack without Anti-Exploit to allow the malware to be downloaded. TeslaCrypt is successfully blocked by Malwarebytes Anti-Ransomware Beta:
We will continue to monitor this malware campaign as we expect it to evolve again.
IOCs:
- pon.chernayadama.info/megaadvertize/?keyword=f837985ebdf42ce01a8e8853beb0ee34
- pon.chernayadama.info/megaadvertize/reading/?keyword=77374










