Author’s Note: We at Malwarebytes continue to do our part in educating our product users and constant blog readers about day-to-day online threats and how they can avoid falling prey to them. “PUP Friday,” our latest attempt at getting users acquainted with files they may need to watch out for in the Wild Web, offers an in-depth look at some interesting and quite notable potentially unwanted programs (PUPs). Expect to see this type of content pushed out twice a month at the end of a work week.
This post is about a PUP that has been around for a while, but seems to have gained a lot of “popularity” lately. Since it actively blocks victims from visiting our site and blocks every official download location for Malwarebytes Anti-Malware and some other security software, we have figured it deserves a mention in our PUP Friday series.
What is it?
Dotdo FastInternet is adware that hails from dotap[dot]dotdo[dot]net and fetches advertisements from toi[dot]miifaa[dot]info.
Proxy hijacker
To get these advertisements to their victims, they setup a proxy on the users’ computer. This proxy uses part of the legitimate Fiddler software on port 8877 (proxy is set to 127.0.0.1:8877 for HTTP and HTTPS) to add to and intercept Web traffic. To make sure the user is unable to change or circumvent the proxy settings easily, it uses a few tricks that we have discussed before and some new ones: the “Proxy server” settings in Internet Explorer, which are the system settings, are greyed out and they blame the “System Administrator” for it.
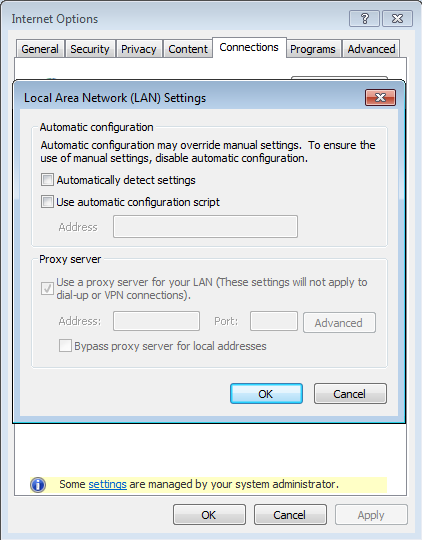
The settings in Chrome are greyed out as well, and if you are using Firefox, you will find this line in user.js:
lockPref("network.proxy.type", 5); The value 5 for “network.proxy.type” tells Firefox to use the systems proxy settings.
As an extra precaution to point Chrome in the right direction, they alter the user’s shortcut links for Chrome and add the argument –proxy-server=http=127.0.0.1:8877 as shown below.
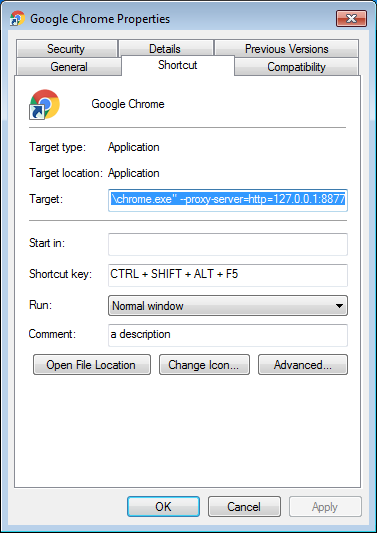
For good measure, a copy of this link is dropped in the Windows Startup folder.
Blocking security software
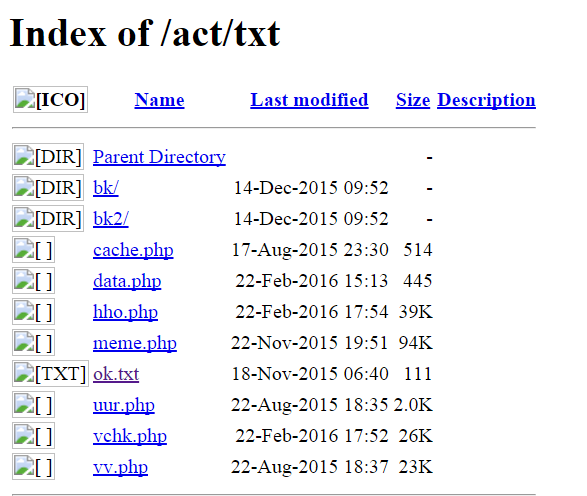
This adware creates a folder named “a” in the %HOMEDRIVE% directory that holds most of the files it uses.
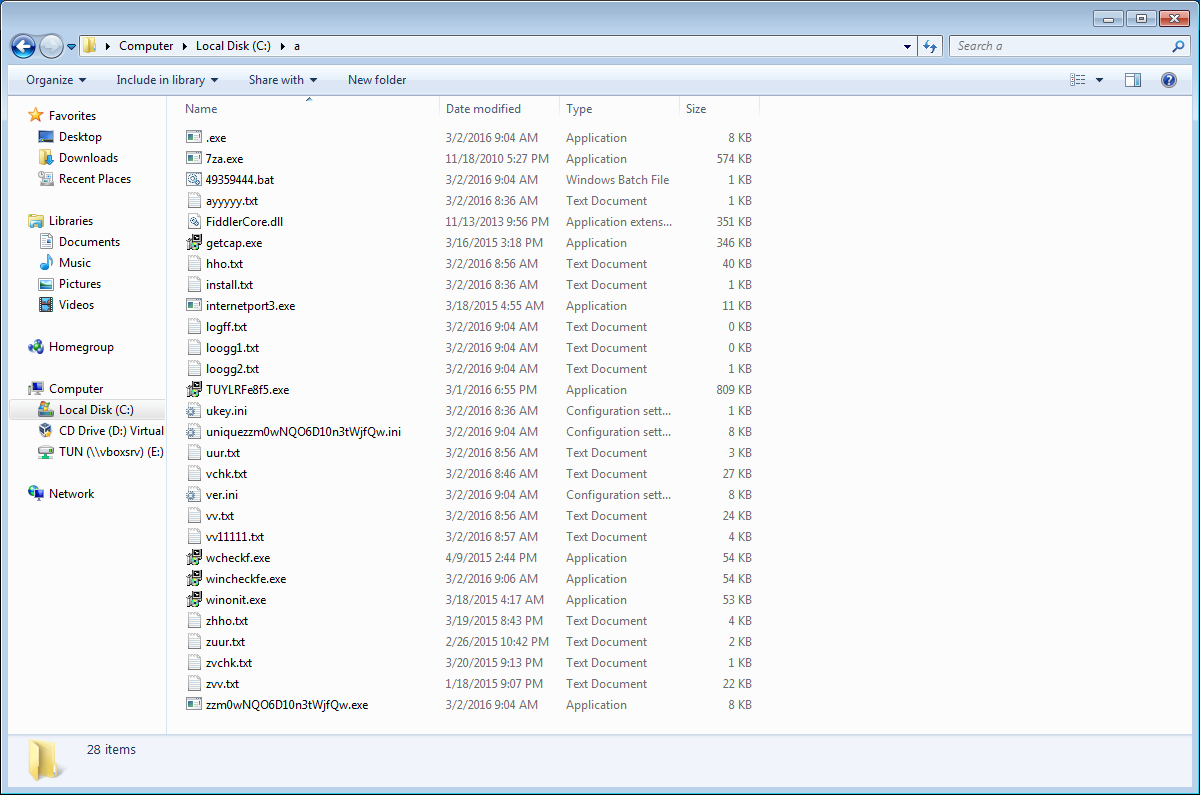
A few of the text (.txt) files in that folder are the block lists. If you look at hho.txt, for example—
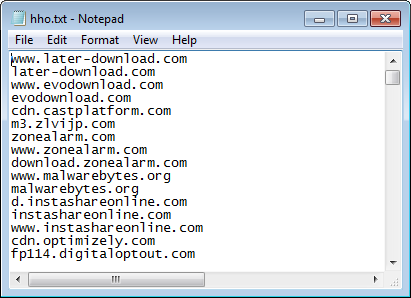
—you will see quite a few security software related (sub) domains listed. In uur.txt, you will see several third-party locations where you can download our software. Screenshot below:
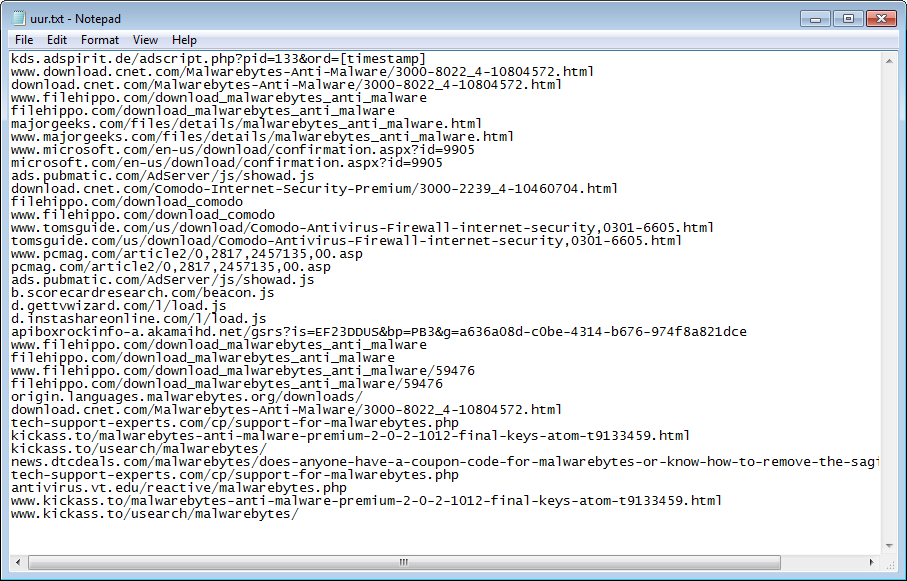
All these and the domains in hho.txt are no longer accessible if you are connected through the proxy. This is the result if you try:
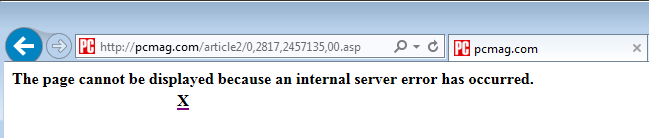
The X marks where it tries to show you an advertisement, which I blocked. Two can play that game.
Remediation
Malwarebytes Anti-Malware can remove this infection completely, but you will have to be able to download it first. If you have access to the internet with another clean machine, you can always download the Malwarebytes Anti-Malware installer and transfer it to the affected machine via a USB flash drive, for example.
If you need to do it with the affected machine, here’s how to do it: Find the file c:ahho.txt (that’s the one with the domain block list we discussed earlier). Right-click the file and choose “Edit”. Your default text editor will open, usually notepad. Click “Edit” > “Select All” and delete the content of the file (pressing the Backspace button once should do). Then type dotap.dotdo.net to replace the old content. Then click “File” > “Save” to save the altered file. You should now be able to visit our site and download the installer.
Here’s an important note: Deleting the hho.txt file will not help as it will be replaced sooner than you can surf to our site. If the adware is active, it downloads a fresh copy from dotap[dot]dotdo[dot]net.
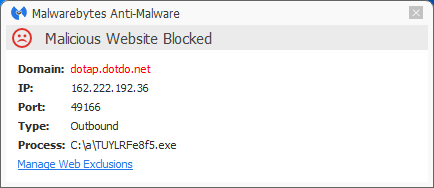
Detection and protection
The installer is detected as PUP.Optional.DotDo. A full removal guide can be found on our forums. The involved domains are being blocked by Malwarebytes Web Protections module.
Prevention
We are not exactly sure how people get infected with this one. If anyone can provide extra information about that, feel free to post it in the comments. As always, be careful what you download and allow to run. Our advice: “Save yourself the hassle and get protected.”
Summary
In our crosshairs for this week is an adware that actively stops its victims from downloading certain security software, including our own Malwarebytes Anti-Malware. We have discussed how they do it and how you can circumvent it.
Special thanks to Ried for bringing this one to my attention.
Pieter Arntz











