Adobe has just released a patch for the infamous Flash Player to fix a vulnerability actively exploited in the wild by some exploit kits. This vulnerability was actually a zero-day (CVE-2016-1019) but exploit kit authors botched its integration which resulted in only affecting older versions of Flash.
Another saving grace was the fact that a “mitigation introduced in Flash Player 21.0.0.182 currently prevents exploitation of this vulnerability, protecting users running Flash Player 21.0.0.182 and later“.
Nonetheless, since this could be tweaked and made functional to work on fully patched versions as well, Adobe went on to fix the bug.
The Magnitude EK which has been very active as of late was in fact using CVE-2016-1019 for some time. As we reported earlier this month, several (still) active malvertising campaigns are pushing Magnitude with a little tweak, including a fingerprinting gate right before the landing page.
Magnitude EK: CVE-2016-1019 with Flash 20.0.0.306:
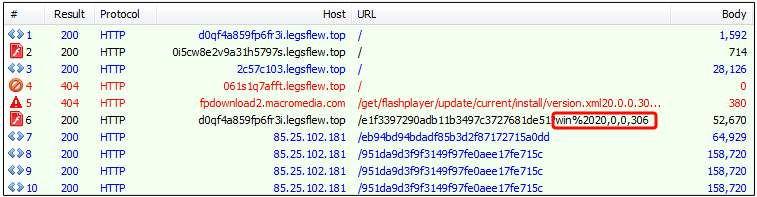
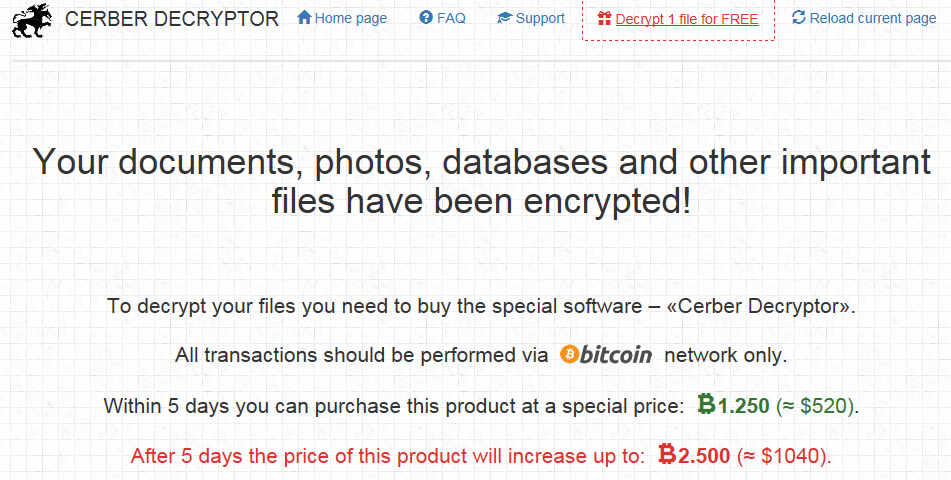
The payload from this attack is the Cerber ransomware:
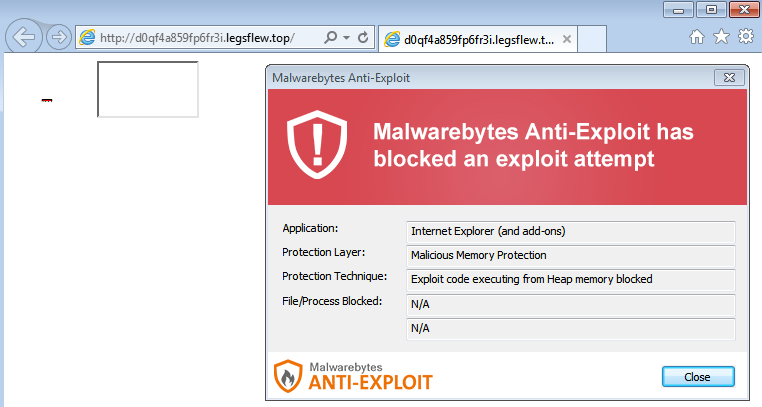
CVE-2016-1019 is blocked by Malwarebytes Anti-Exploit:
Drive-by download attacks that involve compromised sites or malvertising continue to leverage the Flash Player as the preferred piece of software for exploitation.
As an end-user, you need to evaluate your situation and decide whether you should keep it installed or not. If you do, it is critical that you run an exploit mitigation tool in parallel due to the likelihood of zero-day attacks. In other words, the traditional advice to keep your software up to date is not sufficient when it comes to high risk plugins such as Flash.
Malwarebytes customers running Malwarebytes Anti-Exploit were already protected against this latest zero-day.










