Over the weekend we saw the following rogue Android APK being downloaded to mobile devices via a rogue advert. It claims to be an “Adult Player”, but is really a piece of Ransomware bearing the name “CYBER.POLICE” which has been doing the rounds for a while now:
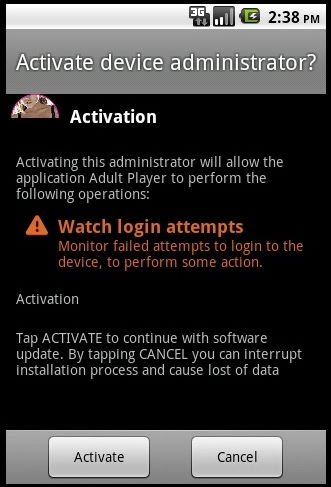
The file doesn’t autorun – it requires human interaction to get things moving. Additionally, you won’t be able to run it if you haven’t enabled the installation of files from unknown sources.
From this point on, it’s downhill all the way in a one-way trip to Ransomware town – and a three day countdown timer to pay the supposed “fine”:
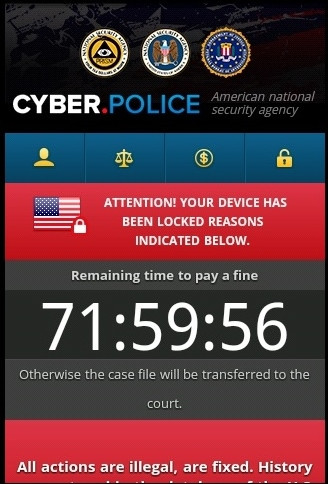
Cyber.PoliceAttention! Your device has been locked reasons indicated below
Remaining time to pay a fine
71:59:56
Otherwise the case file will be transferred to the court
All actions are illegal, are fixed. History query stored in the database of the U.S. Department of Homeland Security
The Ransomware also displays an explicit pornographic image which could be deemed illegal in many jurisdictions – effectively, “Hello, we’ve seen you doing terrible things and just in case, here’s a random image of a terrible thing – now pay up”.
Various heavy duty laws are displayed to the victim, including just some of the below:
Criminal infringement of copyright, imprisonment for not more than 5 years or fineGathering / delivering defence information to aid foreign government, punished by death or imprisonment for any term
Plates, stones or analog for counterfeiting foreign obligations or securities, 25 or more years imprisonment
Economic espionage, fine of not more than $500,000
There’s more, but you get the idea. By the time the victim has waded through endless reams of text telling them about all the years they’re going to spend in jail, they’re probably ready and willing to throw some money at the problem to make it go away. In this case, the Ransomware authors are after some iTunes gift codes.

To unblock your device and close your case you should pay a $200 fine to [the] Treasury accountPay to unblock device with iTunes gift card. Your case will be closed immediately after the transaction processing!
Pay to unblock device with iTunes gift card. Your case will be closed immediately after the transaction processing.Pay 2 x $100 USD
Pay 4 x $50 USD
Type your 1 iTunes gift card code
Type your 2 iTunes gift card code
Pay a fine
This is, of course, complete nonsense – no “Treasury department” investigating supposed criminal activity can be bought off with iTunes gift codes. “Cyber Police” Ransomware was most recently doing the rounds last month, and appears to have moved from exploit driven autoinstalls to “please click on the thing” while hoping for the best. Malwarebytes Anti-Malware Mobile detects the above file as SLocker.cx, and you should most definitely avoid running the above file on your Android.
Whether we’re talking APK-based Ransomware or the browser locking variety, they all seem to want a piece of iTunes at the moment – and Amazon gift cards are also up for grabs. A securely locked down device and a splash of common sense is still the best way to avoid Ransomware – and backing up your data is crucial. Regardless of platform, if you’re not doing it already – there’s never been a better time.
Christopher Boyd (Thanks to Nathan for additional research)