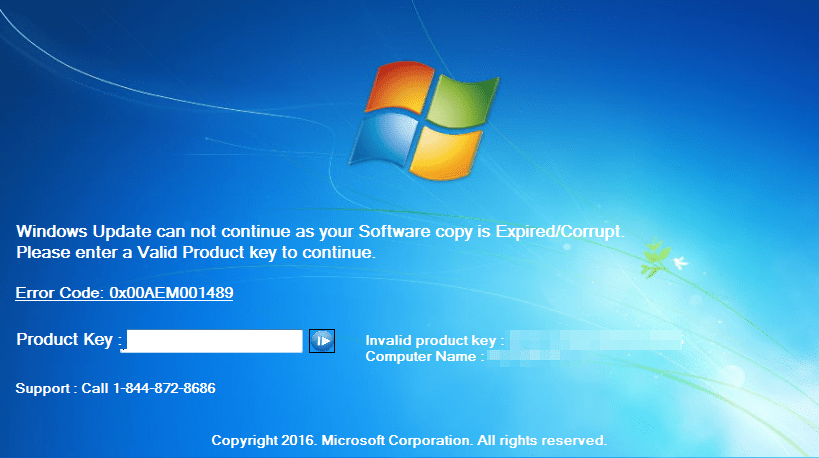
Tech support scammers are well aware of what is going on in the malware scene and often rip off ideas and concepts from other criminals. We see this today with for example bogus browser locks and fake AV alerts which are mostly an annoyance and can somewhat easily be disabled.
But things have been changing with more serious malware-like techniques to force people into calling rogue tech support call centres. We previously saw a case of fake Blue Screen Of Death (BSOD) actually locking up people’s desktops and now there is a growing demand for such ‘products’. Below is a Facebook post advertising a locker specifically designed for tech support scams. It tricks users into thinking their Windows license has expired and blocks them from using their computer.
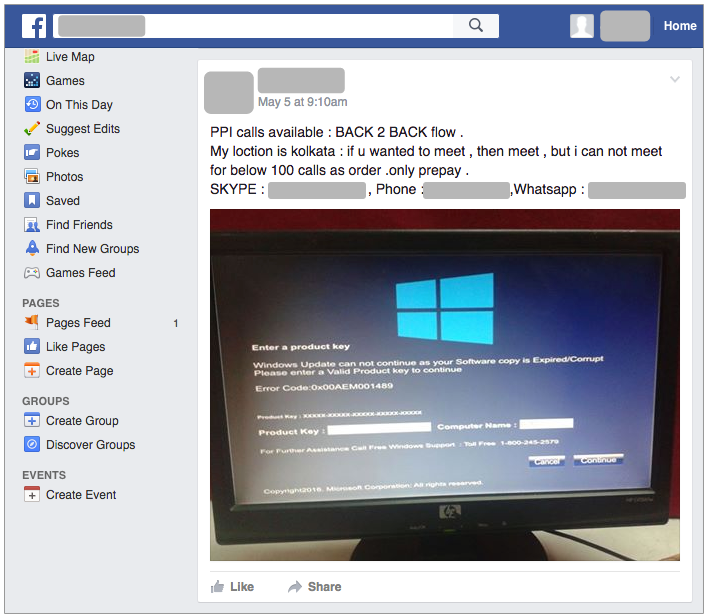
To be clear, this is not a fake browser pop up that can easily be terminated by killing the application or restarting the PC. No, this is essentially a piece of malware that starts automatically, and typical Alt+F4 or Windows key tricks will not get rid of it.
There is an entire ecosystem to distribute these tech support lockers, which includes bundling them into affiliate (Pay Per Install) applications. What you thought was a PC optimizer or Flash Player update turns out to be a bunch of useless toolbars and, in some cases, one of these lockers. Another reason yet, if there weren’t enough already to stay away from adware supported programs.
A security researcher known as @TheWack0lian shared an interesting sample with us which truly resembles a genuine Microsoft program. It installs without any particular incident and waits for the user to restart their computer. When that happens, the program activates to take over the desktop and display what looks like Windows updates being installed:
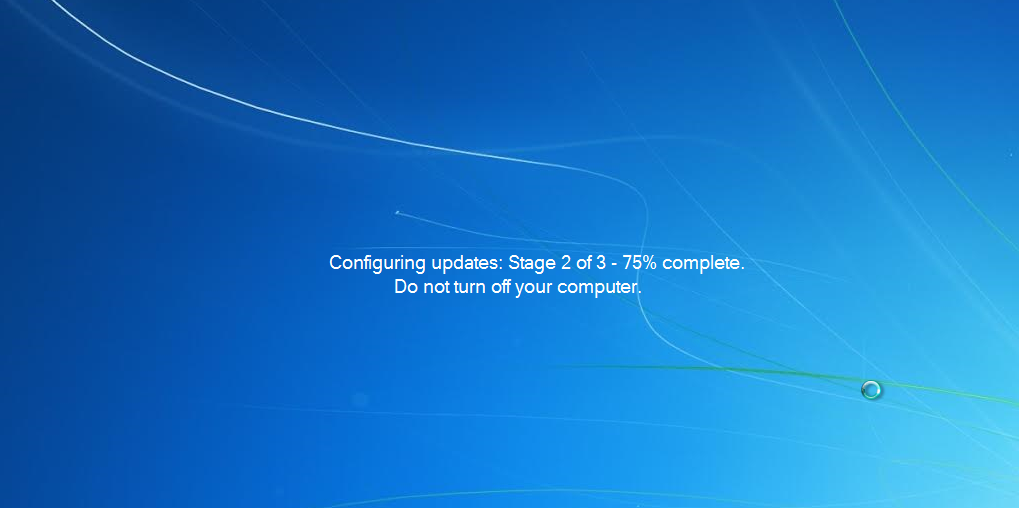
This is a fake Windows update but the average user will probably not see the difference. More troubling is the next screen that comes up and effectively disables the computer because of an expired license key. The message looks legitimate with the license key and computer name being retrieved from the victim’s actual computer.
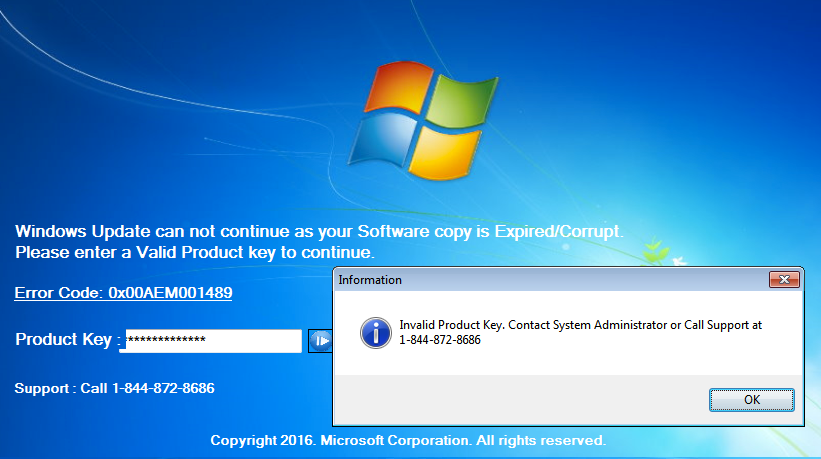
The only recourse it seems is to call the toll-free number for assistance. As you can imagine, these fake Windows programs are great leads for tech support call centres waiting to collect the credit card numbers of unsuspecting users.
We called the number (1-844-872-8686) provided on the locked screen and after much back and forth, the technician revealed a hidden functionality to this locker. There is a built-in installer for TeamViewer which can be launched by a combination of the Ctrl+Shift+T keys:
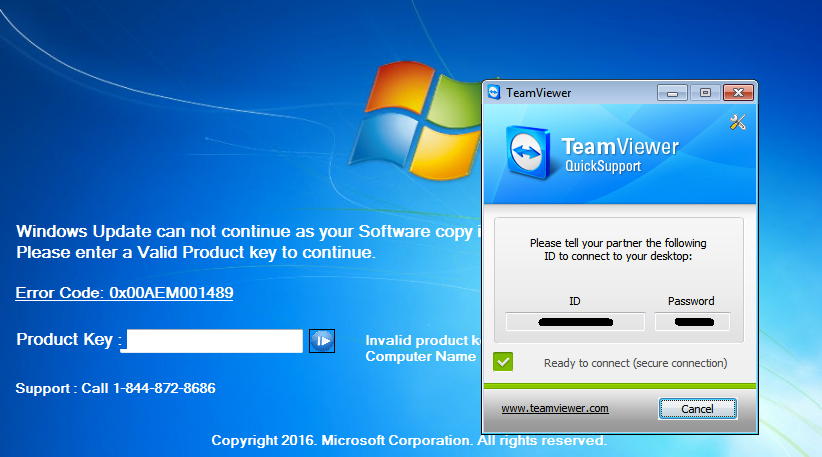
However, the rogue ‘Microsoft technician’ would not proceed any further until we paid the $250 fee to unlock the computer, which we weren’t going to.
@TheWack0lian discovered a keyboard combo to disable the locker by holding Ctrl+Shift and press the S key. Alternatively, if you know someone facing this issue, you may be able to recover their computer by entering one of the hardcoded values for the ‘product key’: “h7c9-7c67-jb” or “g6r-qrp6-h2” or “yt-mq-6w”. Note that these may only work for this particular instance and not all versions of those lockers.
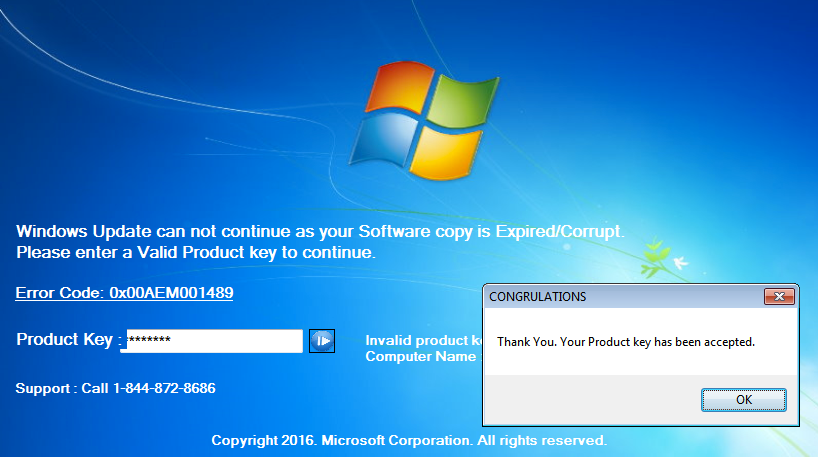
Needless to say this is a worrying trend because in comparison to fake (but mostly harmless) browser alerts, these Windows lockers are a real pain to get rid of and until you do so, your computer is completely unusable. Just in the past few days we have noticed more and more users complaining about these new lockers.
This increased sophistication means that people can no simply rely on common sense or avoid the typical cold calls from ‘Microsoft’. Now they need to also have their machines protected from these attacks because scammers have already started manufacturing malware tailored for what is essentially plain and simple extortion over the phone.
Malwarebytes Anti-Malware detects this tech support locker as Rogue.TechSupportScam. If you have been infected with this locker, we have a removal guide here.