While some ransomware (i.e. Chimera) give bogus threats about stealing and releasing private files, there are other malware families that in fact have made this possibility a reality.
Recently, Bleeping Computer published a short article about an unrecognized Trojan that grabs documents from the attacked computer and uploads them into a malicious server. Looking at the characteristics of the tool, we suspect that it has been prepared for the purpose of corporate espionage. So far, no AV has given any meaningful identification to this malware—it is detected under generic names. Since not much is known about its internals, we decided to take a closer look.
In the unpacked core we found strings suggesting that the authors named the project Shakti, which means “power” in Hindi or may also be a reference to the Shakti goddess. That’s why we refer to this malware as Shakti Trojan.
This post is a part 1 of the research – giving a short glimpse at the malware’s abilities as well as describing it’s background and possible attribution. See also the part 2: Shakti Trojan: Technical Analysis.
Analyzed samples
Recent sample mentioned by Bleeping Computer (submitted to VirusTotal 1st August 2016):
- b1380af637b4011e674644e0a1a53a64: main executable
- bc05977b3f543ac1388c821274cbd22e: Carrier.dll
- 7d0ebb99055e931e03f7981843fdb540: Payload.dll
- C&C: web4solution.net
Other found samples:
- 8ea35293cbb0712a520c7b89059d5a2a: submitted to VirusTotal in 2013
- C&C: securedesignus.com
- 6992370821f8fbeea4a96f7be8015967: submitted to VirusTotal in 2014
- C&C: securedesignuk.com
- d9181d69c40fc95d7d27448f5ece1878: submitted to VirusTotal in 2015
- CnC: web4solution.net
Behavioral analysis
Like most malware, Shakti Trojan comes packed inside the loader executable with an icon added:
After being deployed, it runs silently.
We will not see it on the list of running processes because it uses the disguise of a browser. It deploys a legitimate process and injects itself inside.
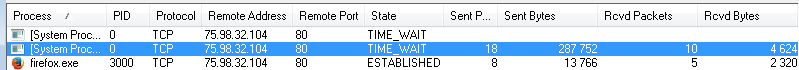
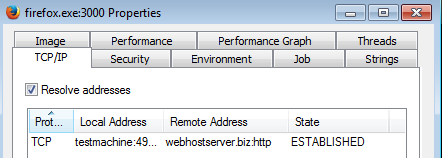
Below we can see the traffic generated by this malware, injected inside firefox.exe:
The Trojan achieves persistence either by installing itself as a service or, if it failed, by adding a key to autorun:
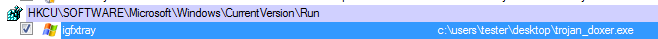
The atypical feature is that it doesn’t try to hide the original file by moving it into a new location. Instead, it prevents users from accessing or removing it. To achieve this, it opens its own file for reading.
Network communication
The Trojan passes the data to its C&C server as a HTTP POST request (URL pattern: http://[ CnC address]/external/update). It also uses headers of MSMQ protocol.
It beacons to the server by sending basic info collected about the victim system. When it gets a response, it uploads the list of all the installed programs:
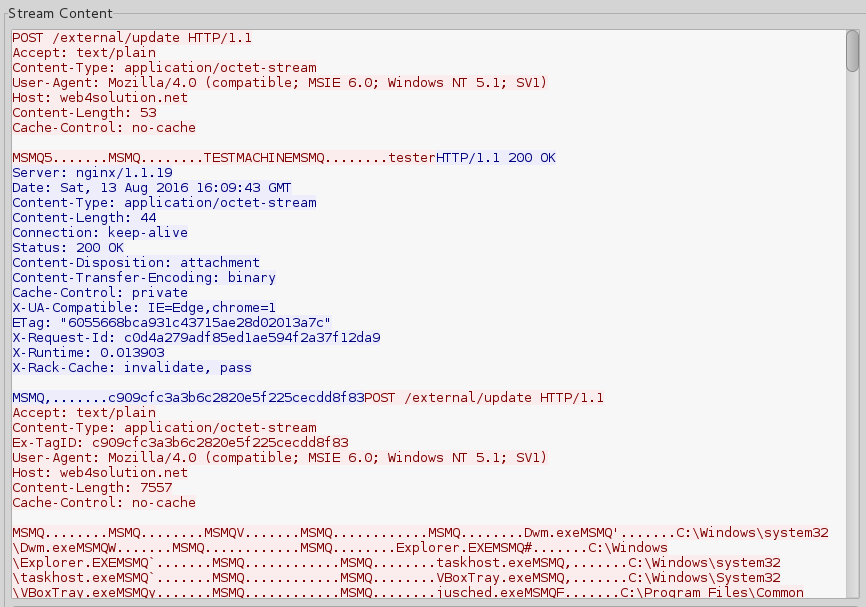
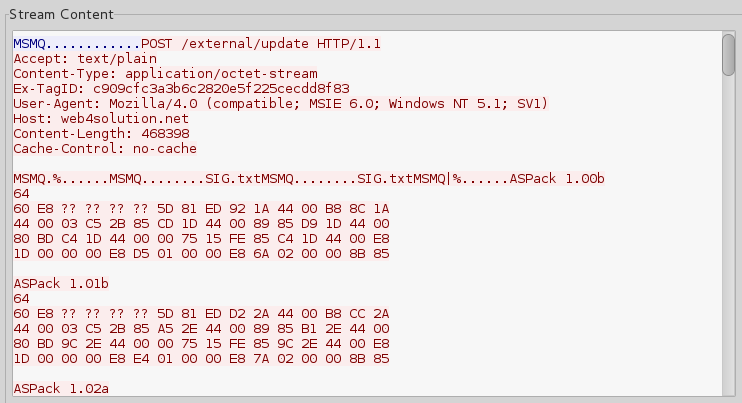
After passing this initial data, the main mission starts: uploading all the files with the desired extensions. Everything is transmitted as open text. First goes the file name, then its full content:
A look inside
Looking at the code we can find more about the goals which authors wanted to achieve and their development environment.The main executable is a loader responsible for unpacking and deploying the core malicious modules: Carrier.dll and Payload.dll. (More details about them will be described in the next post.)
Both DLLs comes with paths to debug symbols. They reveal folders structure on the development machine:
E:ProjectsComplexStatementShaktiCodeCarrierReleaseCarrier.pdb
E:ProjectsComplexStatementShaktiCodePayloadReleasePayload.pdb
Both modules are written in Visual C++ and clearly belong to the same project, named Shakti.
Payload.dll comes with a hardcoded list of the extensions, for which the bot is looking: 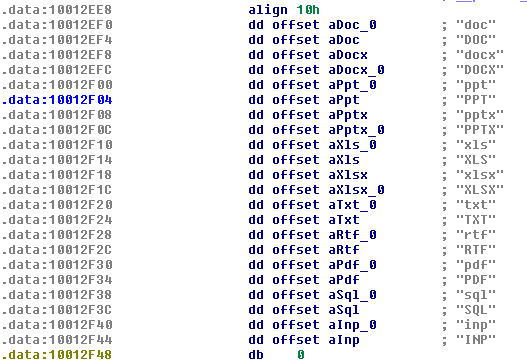
Clearly authors were interested in stealing documents. Majority of them are linked to MS Office packet:
inp, sql, pdf, rtf, txt, xlsx, xls, pptx, ppt, docx, doc
Most of the malware fingerprints a victim system, but rarely are they as precise in recognizing details as this Trojan is. It comes with a long list of Windows versions, including special editions: Cluster Server Edition, Datacenter Edition, Compute Cluster Edition, Advanced Server, and more:
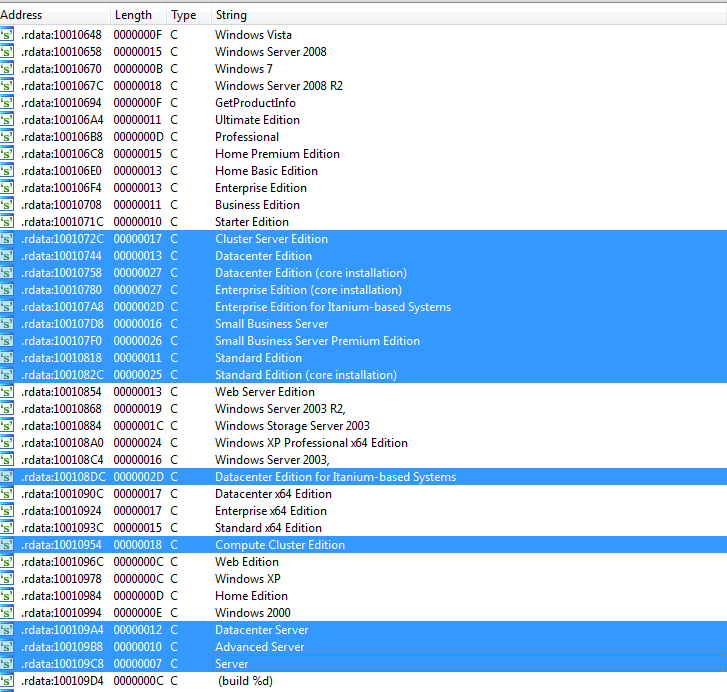
The lack of Windows 8 and 10 is notable on that hardcoded list. It may suggest that the payload is old, written before the release of those systems. Windows 8 was released in October 2012. Compilation timestamps of the main elements: Carrier.dll and Payload.dll point to February 2012. We can never be sure if the compilation date is not spoofed, but since those two facts match together, it is worth considering that this Trojan may have been created in 2012.
Tracing attribution
The domain used as a C&C, web4solution.net, is registered in India.
Source of the record: http://www.enom.com/whois/web4solution-net.html
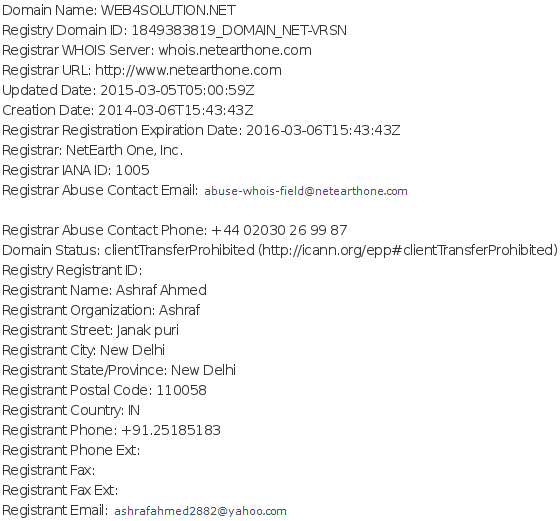
Interestingly, the same person was also an owner of the previously found C&Cs:
securedesignuk.com from sample: 6992370821f8fbeea4a96f7be8015967
Source of the record: http://domainbigdata.com/name/ashraf%20ahmed
Domain Name Create Date Registrar securedesignuk.com 2011-12-20 netearthone.com
securedesignus.com from sample: 8ea35293cbb0712a520c7b89059d5a2a
Source of the record: https://who.is/whois/securedesignus.com
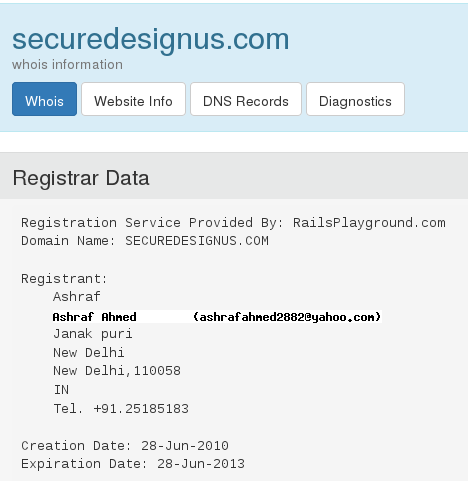
Indian attribution is possible, matching the Indian name of the Trojan.
Additionally, two of the C&C domains: web4solution.net and securedesignuk.com have been found using the same certificate – that confirms being owned by the same actor over years:
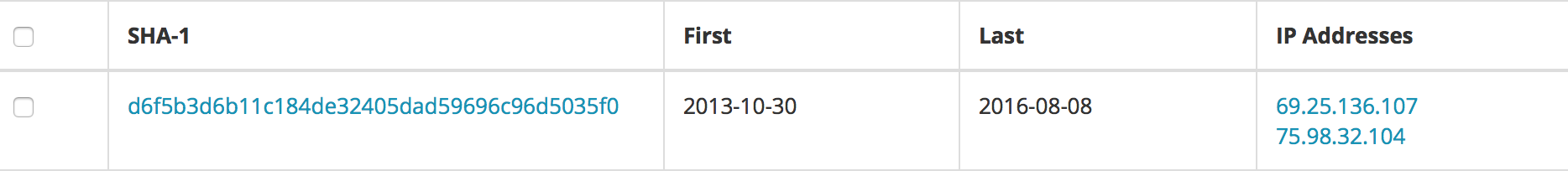
Conclusion
Shakti Trojan is very small and it seems to be written solely for the purpose of document stealing. So far we don’t have any information suggesting that this attack is widespread. The application is not new, yet it escaped from the radar and hasn’t been described so far. Its signature doesn’t match any known commodity malware. The only found trace points to the malware wereIt is possible that this tool was designed exclusively for small operations of corporate espionage.
This trojan is detected by Malwarebytes Anti-Malware as ‘Trojan.Shakti’.










