CryptoBlock is an interesting ransomware to keep an eye on. We expect this to be a ransomware that is in development to eventually develop into a RaaS (Ransomware as a Service).
Since the ransomware seems to be in development, we decided there might be some weak points and investigate if we could find one. Even though it is in development to be a RaaS, as it seems users have already been infected by this variant somehow.
After getting the name CryptoBlock, we decided to check at VirusTotal and see how many droppers for it we could find there, as well as to get some information on the ransomware. Finding a single dropper on VirusTotal, we noticed it was contacting the domain fliecrypter.in to send a key to and also to get a BTC wallet.
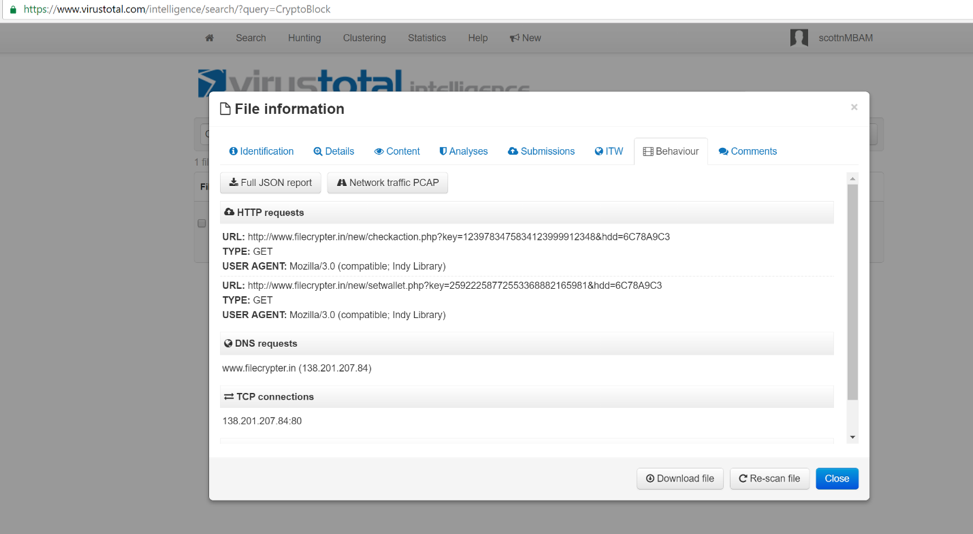
By going to this domain directly, we can see that the threat actor has left a note for interested, criminal consumers that the RaaS should be up and running soon.
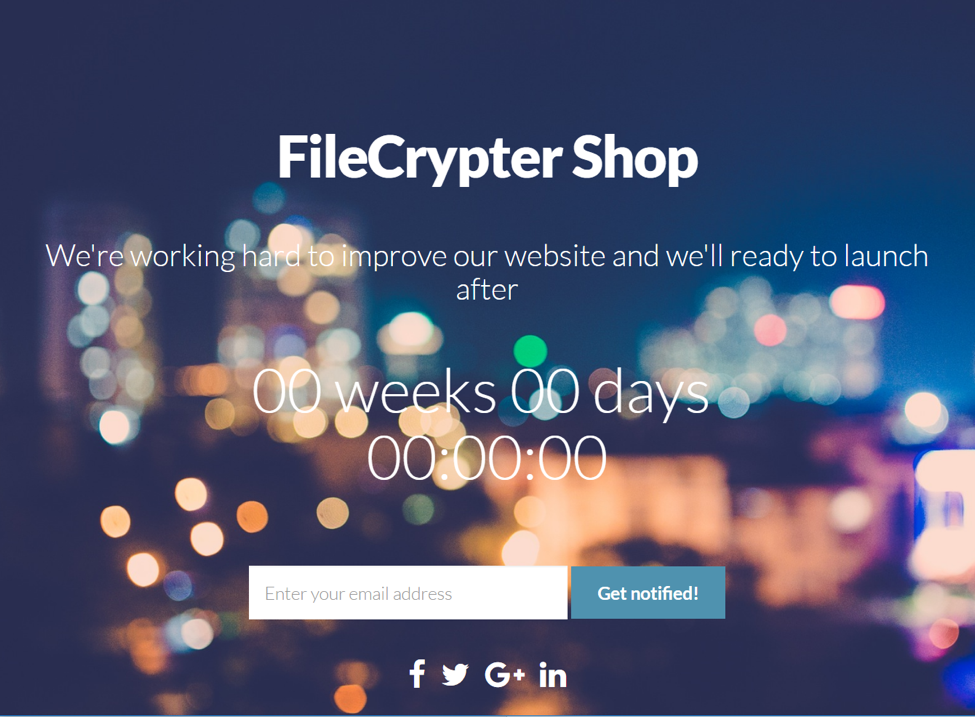
Even with the RaaS not up and running yet, it’s obvious that the ransomware itself was already fully working for the threat actor, and they either had made a few early victims or they ran it on some test computers.
At this point, we decided to run a static analysis on the EXE. Seeing that .NET dll’s were called in the VirusTotal report, we knew it was written in C# or VB. So we opened the EXE in DNSpy, only to find that it was completely obfuscated with ConfuserEX, which is very hard to unravel, especially when it comes to the later versions.
Given the fact that we had a server to work with from previous research, we decided to start on that side, before going through a painstaking de-obfuscation process.
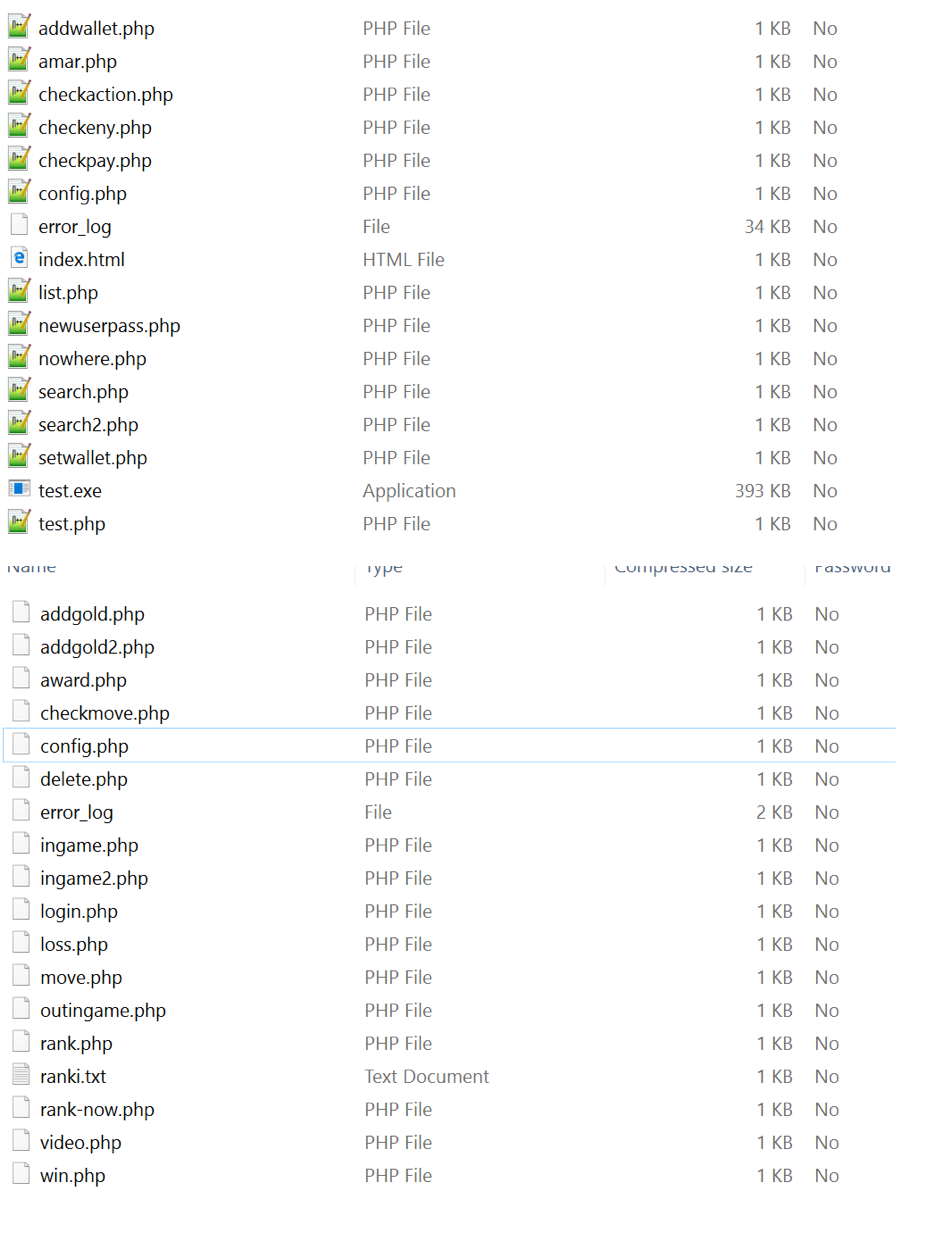
In the server we found some weird entries, pointing to what seemed to be a “Learn PHP game”.
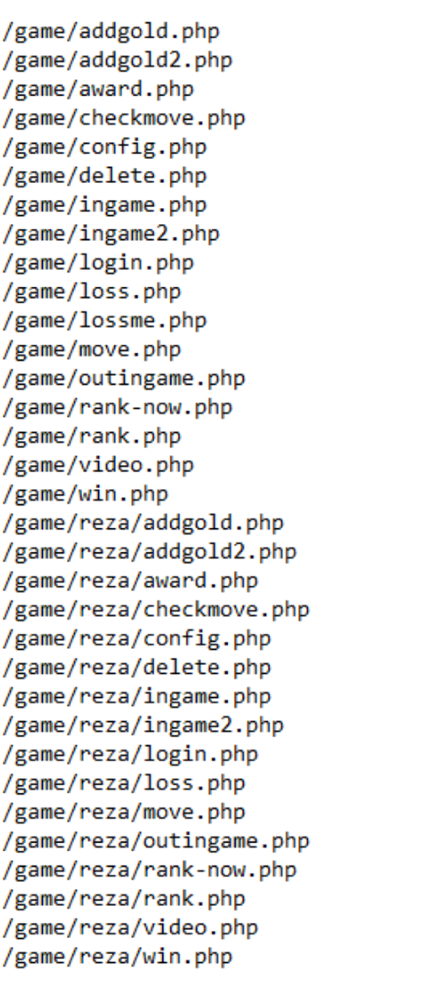
After a search for a lot of these filenames and it didn’t take long before we came across a Pastebin example of one of these php pages. It was quite crude, but it was exactly what we were hoping to find.
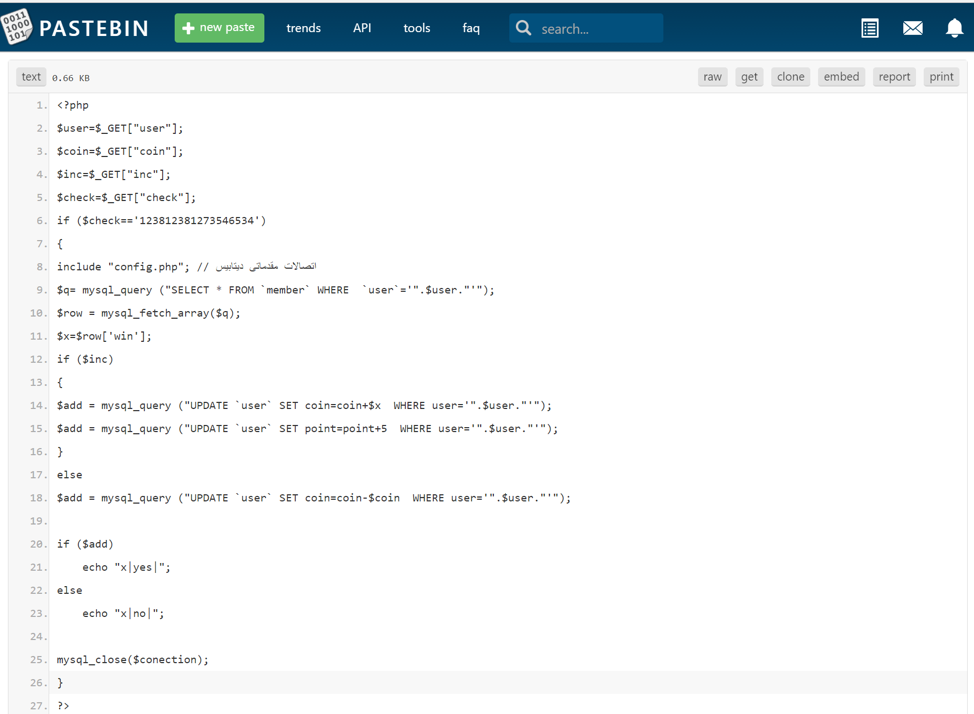
Using this newfound information, we were able to look at a copy of the config.php file on the server.
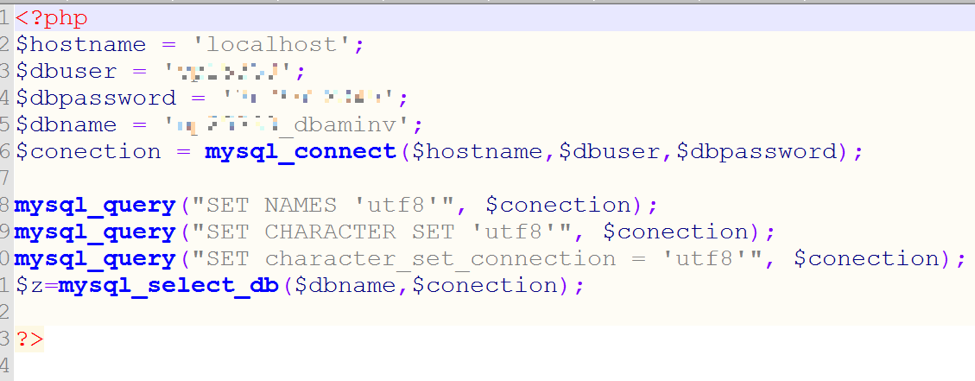
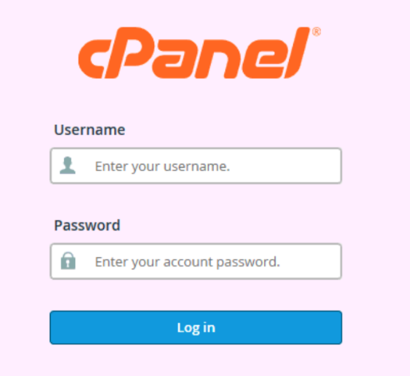
Uh oh! What’s that? Those are the complete master credentials (username and password) to the entire CryptoBlock server, valid for every email, database, SSH, cPanel, and more. Having this information, we went to the site’s cPanel interface and got the login page as such:
Typing in the shiny new credentials gave us all we ever wanted for Christmas…complete access to a threat actor’s overseas server.
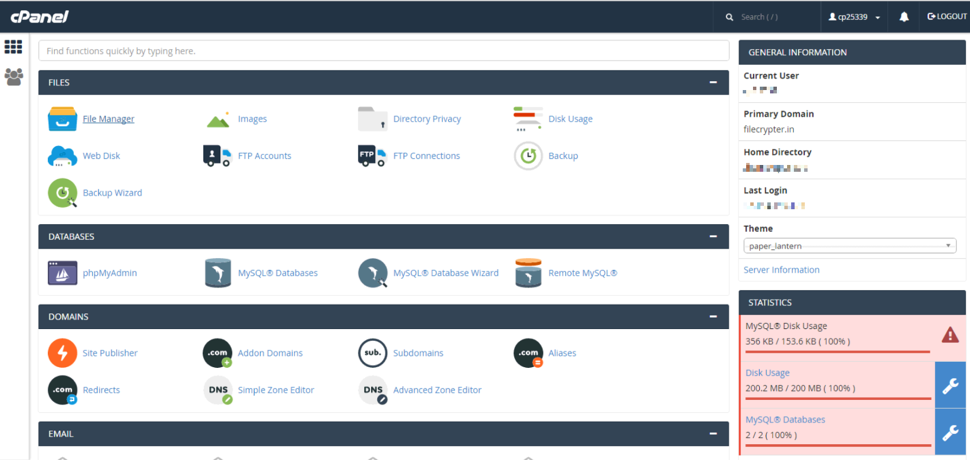
We have made copies of all databases, the PHP files, and the personal information used to rent the server.
Looking through the personal information, it became sadly obvious the hosting company didn’t require much more information than an email address to host this server. This email address turned out to be a fake one.
Let’s look at some of the stats for the server that were recovered from the apache logs and presented through statistics graphs.
One notable thing we can learn from these statistics, there is a possibility that this ransomware has been able to affect quite a few people. But even more interesting to us, it shows that there are a few IP addresses from Europe that have been visiting this server by the thousands since it was brought up. There is a huge chance that these IPs are the real IPs of the threat actor owning this server and were logged while they were performing their tests. This is further supported by the fact that the most used part of the site, is a PHP page that is used by the debug build of the ransomware server: checkaction.php.
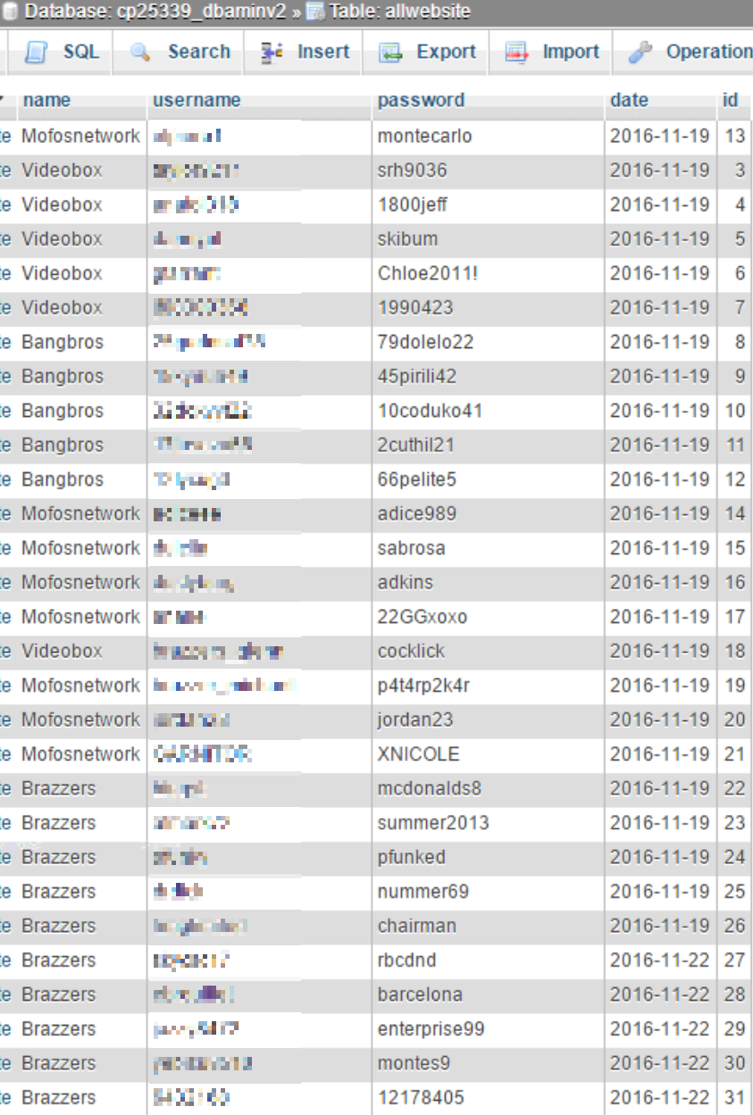
Weirdly, the threat actor seems to have a database full of stolen credentials from “Pay for Porn” sites besides the database the ransomware uses.
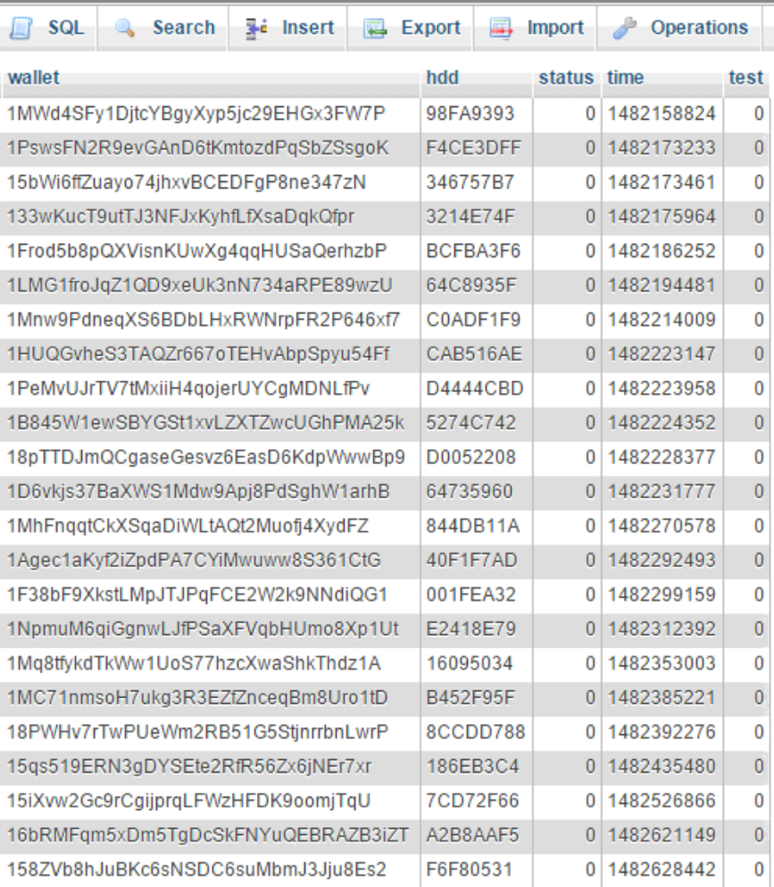
Here is an example of the first page of the database tables used by the ransomware for IDs, BTC addresses, payments, and keys.
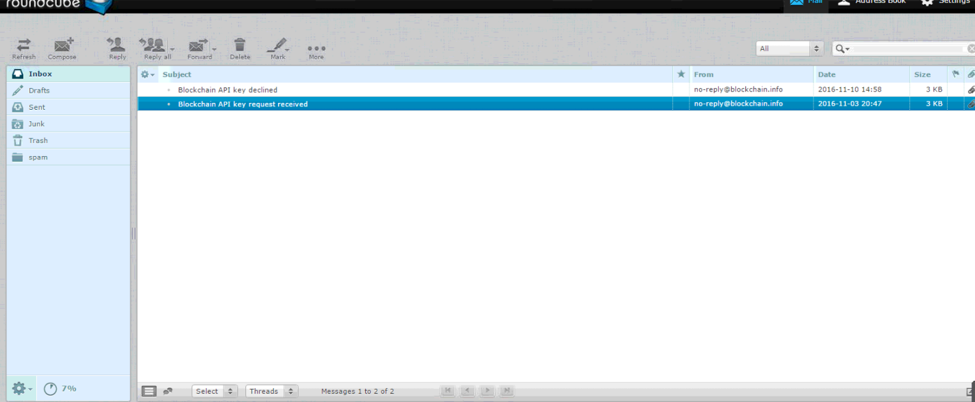
Another interesting fact we found is that the threat actor applied for a Blockchain API account, and was denied.
The threat actor is also distributing an exploitable Ammyy Admin executable from the server. It seems they either may be scamming people into letting them onto the machine remotely, or they are simply running it silently as a malicious drive-by. The file on the server is called test.exe.
We will keep an eye on the developments that this ransomware and the server will go through and try to keep you posted on any significant changes.
As far as protection from this threat though, if you are using Malwarebytes 3.0 with Anti-Ransomware technology, you are going to be protected from this ransomware at numerous levels, so please make sure you utilize it or a similar solution.










