You’ve compromised a few accounts. You’ve worked up a list of people most likely to click your links or send you personal data. You’ve figured out your fake Twitter verification scam and the bogus accounts are ready to roll. You’re feeling good about your general angle of approach, but – watch out! – because things are about to go horribly wrong.
For my part, I don’t go to the zoo and put my head in a crocodile’s mouth. I try to avoid sunbathing on NASCAR tracks. I wouldn’t download a car.
With that in mind, then, I can’t quite fathom the rationale behind picking your an Infosec researcher as the target of a “Get verified on Twitter” scam, especially given that I’m already verified:
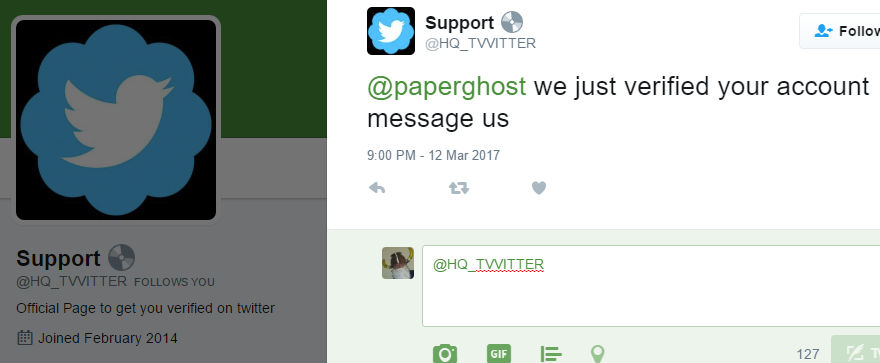
Yes, of course you did.
It’s highly likely they didn’t bother to check my profile bio or they’d have made their excuses and left. That’s what I keep telling myself, anyway. There’s no accounting for that rare breed of YOLO scammer.
I gave them a follow to see what they’d send by DM, because that’s usually how they do things. Not long after:
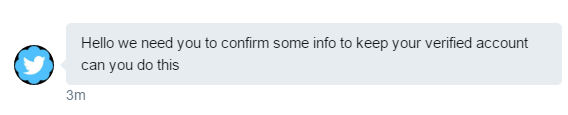
Things have now changed a little – they’re no longer telling me I can get verified, or that they have verified me; it’s now all about keeping said status.
I was all geared up to send some DMs their way in response but a technical hitch left me unable to do so. At this point, a game of “Please send me a message somehow” commenced in the hope that they might take the bait and show me what their scam consisted of:
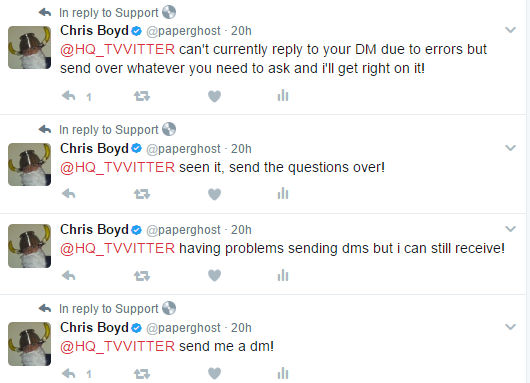
If the recipient had been a bot, then it’s possible nothing would be forthcoming because they’re not always created with the ability to reply. If there was a person at the other end, then I might get a DM to my inbox. If they were feeling particularly adventurous, they might fire over a message publicly. Would they send a security researcher who spends their time writing about scams and has “Malware Analyst @malwarebytes” on their bio a phish attempt? A phish attempt that would not only be hugely unproductive for them, but also likely end up as a bout of mockery, account cancellation, and a blog post?
To coin a phrase, “whoops”.
As it turns out, spelling “Twitter” like “TVVITTER” is not a key indicator of success. In the end, they couldn’t even muster a semi-decent phishing page, or a phishing page at all for that matter. Just a barebones attempt at being the Wallet Inspector and simply asking me to send them my credentials. In fact, the Wallet Inspector had been busy:
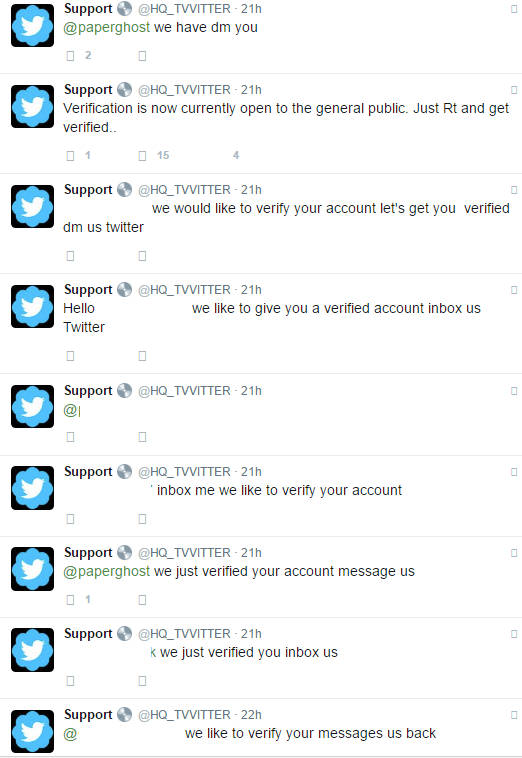
Lots of attempts at luring people into DM conversations, and making a beeline for their logins.
Immediately after being called out, the scammers went into panic mode and started deleting incriminating tweets which let me throw in a Watchmen reference, so that was nice.
Top tip: always screenshot everything before making a move. It’s one weird trick that scammers hate.
I’m not sure what use blocking me was at this point, because the damage (for them) was already done. At least it made them feel a bit better, I guess?
Time to play out their last, desperate, phishy moments…
Now that’s a fast takedown (roughly a minute or so?) by Twitter.
And so my brief encounter with an overly ambitious Twitter phisher comes to an end. I’d like to say parting is such sweet sorrow, but Banhammers are great so I guess I’m not that bothered. Remember: no random Twitter feed can grant you verified status and especially not one making creative use of the English language to spell “Twitter”. If someone asks you for login credentials either publicly or by DM, report them to the appropriate channels and go about your business.
Unless it’s inspecting wallets, in which case you’ll probably be appearing on the blog in the near future…
Christopher Boyd










