When looking at malicious traffic, one of the things we are interested in are the hosts involved in a particular attack. For example, we check the hostnames or IP addresses that were serving up malicious code.
Before getting further, let’s define a few concepts to better understand the topic we are discussing today. A host name can be:
- A domain name (i.e. http://example.com/)
- A fully qualified domain name (i.e. http://test.example.com/)
- An IP address (i.e. http://127.0.0.1/)
It’s not as usual, but IP addresses can indeed be directly used as the URL and when that happens it is called an IP-Literal Hostname (see Eric Lawrence’s post on this subject).
IP addresses (IPv4) follow the dot-decimal notation which is four numbers, each ranging from 0 to 255, separated by dots. But then, to make things a little more complicated, we have exceptions, such as the non-dotted IP literals, in decimal (http://2130706433/) or octal form (http://017700000001/).
This takes us to a recent infection chain for the RIG exploit kit where we came across such an occurrence. The host was:
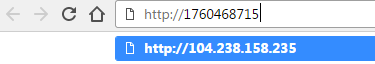
http://1760468715
While for us humans it makes little sense that this could even resolve, Internet Explorer and Chrome (Edge doesn’t seem to) can handle it just fine and convert that into a proper IP address (104.238.158.235):
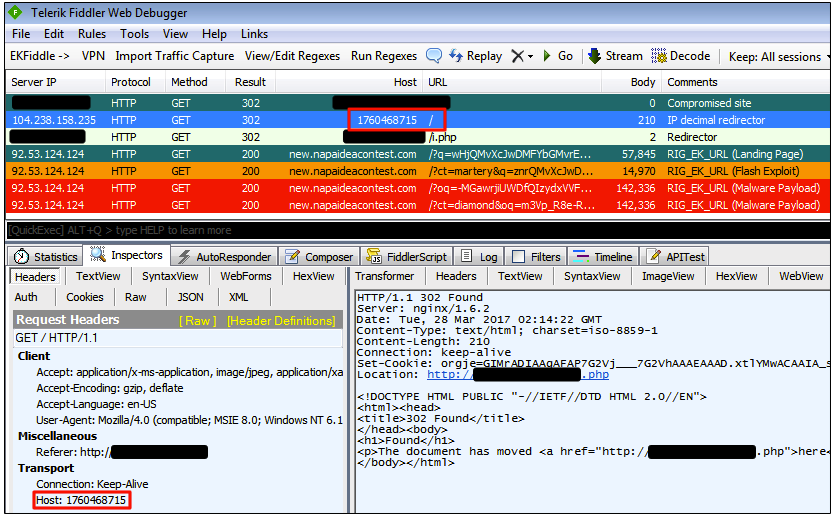
We observed websites that had been hacked and were pushing this non-orthodox URL via 302 redirects (the HTTP response code indicating that the site has moved to a new location):
HTTP/1.1 302 Found Server: nginx/1.10.1 Content-Type: text/html Content-Length: 0 Connection: keep-alive X-Powered-By: PHP/5.3.10-1ubuntu3.23 Access-Control-Allow-Origin: * Location: http://1760468715/ Vary: Accept-Encoding
This in turn leads to another redirector performing the final call to the RIG EK landing page and infecting the user with the Smoke Loader malware, as shown below:
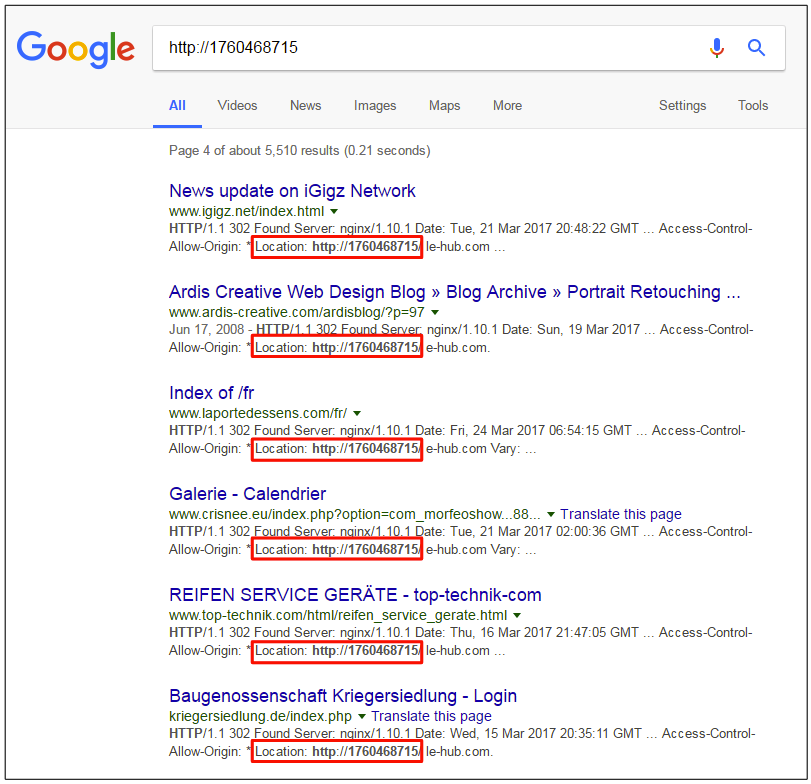
Upon Googling for that particular string (1760468715), we can find many sites that have been injected with the Decimal IP redirect:
There is a thread on StackExchange about a website owner dealing with such an infection and trying to find how to locate it. Some folks suggest to grep the entire server for the incriminating string, while others recommend a complete wipe and reinstallation.
Perhaps the malicious actors are trying to avoid some IP filters or maybe make identification harder by using a less common URL format. In any case, Malwarebytes users are protected from accessing this rogue server, no matter how the URL is formatted.
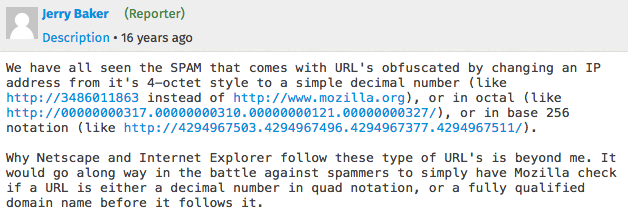
And if you wonder about real life purposes of these non-dotted IP-literal URLs and want to participate in the debate, feel free to join this 16 year old thread:
IOCs:
Redirect:Decimal IP:1760468715 IPv4 dot-decimal: 104.238.158.235Payload (Smoke Loader):
4bed780a55e6179e4a1236444c34398af50d3bea39f86eb877089265f833bda5










