Security researcher Bosko Stankovic recently published an article explaining how an attacker could use Chrome, the SMB file sharing protocol, and Windows Explorer Shell Command File to steal victims credentials.
The basic elements
Chrome
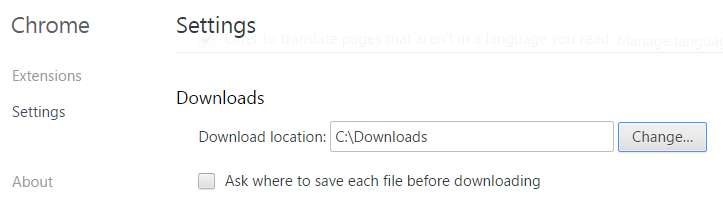
Similar attacks have been demonstrated using Internet Explorer and Edge, but being able to do this with a (very popular) third party browser increases the chances of this being used in the wild by a lot. Chrome uses a technique called MIME-sniffing for files with a text or text-like content and downloads files that contain a non-printable character. It downloads these files to the default download folder as specified in the Advanced Settings section of the Chrome Settings.
SMB protocol
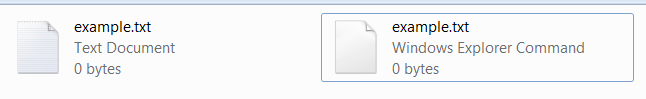
This file sharing protocol recently gained a lot of fame by being exploited to spread theSCF files Windows Explorer Shell Command File are basically shortcuts with a run command. A very noteworthy feature is that this extension is invisible even if you have your extensions set to show.”>
So you will have to take a really close look at a file that has a double extension like example.txt.scf to see the difference with an actual txt file.
Another thing that makes SCF files dangerous is that they are triggered as soon as the folder they are in is opened. Windows will send a request for the resource the very moment the file is showing in Windows explorer.
The possible attack
The attacker plants an SCF file containing a non-printable character on a website that he knows his victim(s) frequents (watering hole attack). Or if the threat actor is after a bigger audience he can rig a malvertising campaign or use social media.
Chrome users will get the SCF file downloaded to their default downloads folder and the next time they want to look at or move a file from that folder, the SCF file will be triggered as soon as the downloads folder is opened in Windows Explorer.
As explained, SCF files can be configured to contact a server with a request for resources (i.e. a file). There are no restrictions so this can be a remote server under control by the attacker. In order to make the resource request, it will need to send an authentication request via SMB, which can be captured on the server. The request would include the victims’ username, his domain, and the NTLMv2 password hash. This information can be extremely useful for an attacker who wants to expand his foothold on a network.
The consequences
Once the attacker has the hashed password it depends on the strength of the hash for how long it takes to find out the password. This can vary from mere seconds to a few days. In targeted attacks, you can be sure the username and hash will be checked against lists published after breaches to see whether a password has been re-used and can be matched with the hash even faster.
If the Windows 8/10 user is using Microsoft Authentication (MSA) to use Microsoft services like Office 365, OneDrive, Skype, and many others, the impact on the victims can be even bigger.
Mitigation
You probably heard this before this week, but if you don’t need SMB, disable it. This is the only part of the attack chain the end-user can easily manipulate by executing a simple Powershell command. Other options are:
- To always use the “Save as… ” option when you are knowingly downloading something, so you’d never have to open the default downloads folder.
- Alter the file association for SCF files, which you would have to do in the registry. Changing the default value under the key HKEY_CLASSES_ROOT.scf “ txtfile” makes the files visible and opens it in notepad.
But disabling SMB is more likely to be successful and it helps protect you against other malware like the WannaCry ransom worm and the Adylkuzz cryptocurrency miner.
Summary
This article explains how Chrome users are at risk of spilling their Microsoft Authentication credentials by simply visiting the wrong site.
[update]
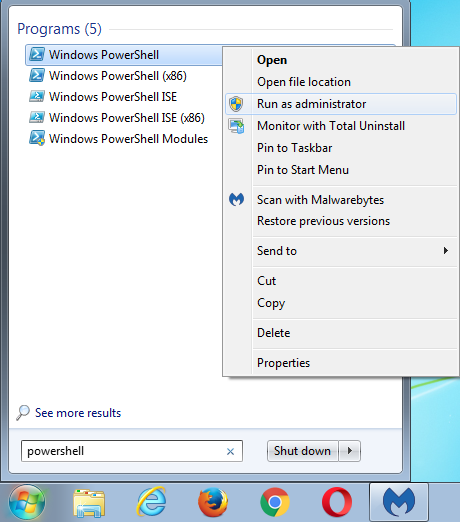
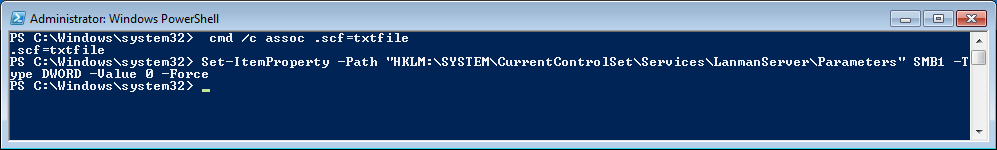
For those looking for an easy fix to disable some of these potentially dangerous “automatisms”, here are two Powershell commands you can use.
Run Powershell as an Adminstrator
To change the file association for scf files to text file you can copy and execute this command:
cmd /c assoc .scf=txtfile
and to disable SMB version 1 you can copy and execute this command:
Set-ItemProperty -Path “HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters” SMB1 -Type DWORD -Value 0 –Force
The source and more information about disabling and enabling SMB can be found in the Microsoft Help article How to enable and disable SMBv1, SMBv2, and SMBv3 in Windows and Windows Server.
Pieter Arntz