In this series of posts, we will be using the flowchart below to follow the process of determining which adware we are dealing with. Our objective is to give you an idea of how many different types of adware are around for Windows systems. Though most are classified as PUPs, you will also see the occasional Trojan or rootkit, especially for the types that are more difficult to detect and remove.
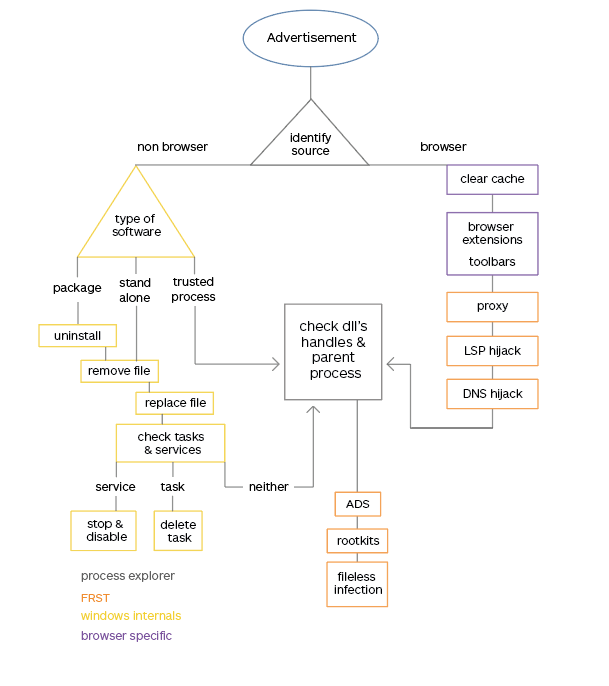
In this part of the series, we are going to have a look at types of adware that are very hard to find and remove. Luckily these are rare, but there are a few adware authors out there that are not afraid to swat a fly with an elephant gun. These hard to find and sometimes hard to remove types of malware, because that is what they are, even if their objective is “only” to show you advertisements, the methods they are using qualify them as malware, not as potentially unwanted.
ADS
ADS is short for Alternate Data Streams. It’s a feature on Windows NTFS systems where you can append any kind of data to a file using the $DATA attribute of the file. The convenient part for the adware author is that the regular user will not see the ADS attached to any file unless he uses some special tools or is familiar enough withRootkits Where Alternate Data Streams are hard to find, rootkits are invisible even for the Operating System (Windows in our case). By definition, a Rootkit is a software that hides itself or another application. The name, however, is derived from the fact that a rootkit has administrator level access (Unix: root) for the system. While there are many tools around that can detect and remove rootkits, the consensus among experts is that a system that has been infected with a rootkit, should never be fully trusted and it’s better to reformat the system drive and re-install the Operating System. This is harsh and some rootkits can be fully removed, but it is sound advice in many cases. You can find more information about the types of rootkits in our threat description “Rootkits”.
File-less infections
File-less infections come in different forms and sizes, but the ones we see most of the time in adware are encoded Powershell commands hidden in the registry. Famous examples are Poweliks and Kovter. Another file-less infection we have seen in use was the WMI hijacker, that used Windows Management Instrumentation to add a site as an argument to each browser shortcut it could find. Effectively making sure that the affected user was always hijacked to their search site.”>
Malwarebytes Anti-Rootkit (beta)
If you run into any of these hard to find and remove adware infections and Malwarebytes is unable to remediate them, please download our very special tool for these casesIndex Part 1
- Identify the process
- Clear browser caches
- Remove browser extensions
- Proxies
- Winsock hijackers
- DNS hijackers
- Type of software
- Uninstall
- Remove file
- Replace file
- Scheduled tasks
- Services
- DLL’s
- Handles
- Parent process
Part 6
- ADS
- Rootkits
- Fileless infections
Up next, part 7
- Tools to investigate with
“>
Pieter Arntz











