By now, you might have heard about an adware infection operation that has allegedly spread to 250 million systems called Fireball. The threat intelligence and research teams at Check Point wrote a blog post last week describing the operation, what the threat does, the system, and the alarming potential the malware has for doing some serious damage.
Fireball, the malware
Fireball is currently being used as a browser-hijacker being frequently installed through bundling (the same infection method that brings you most of the PUPs we detect) modifying the default start page for your browsers as well as changing default search engines to the Rafotech search engine (the company that created Fireball). Also, it utilizes tracking pixels to collect private information about the user and their browsing habits.
The best case
As mentioned before, Fireball is most frequently classified as adware or malware that exists solely to push users to specific web pages and serve them loads of advertisements, getting paid on the back end through all the clicks the ads get by unwilling users. With this in mind, the best scenario is that Fireball continues just to be adware, being annoying and disruptive but not overly dangerous.
The worst case
Fireball also happens to have some additional features that make many security researchers very nervous; this includes the ability to download and execute additional malware.
When you think about 250 million endpoints being infected with this adware and any day it could just decide to drop and execute any malware on the system, it will make you nervous too. Here is what could potentially happen in the worst-case scenario:
- Fireball drops a botnet malware family on all the endpoints, turning it into the most powerful Distributed Denial Of Service weapon ever created, which could be used for taking down the web servers of critical infrastructure, competitor websites, game servers, social media and even our unfortunately designed internet backbone (registrars and top level DNS servers) which could prevent many people from accessing their favorite websites.
- Fireball drops ransomware on the systems and then waits to get paid, disrupting millions of systems and the users and organizations that rely on them
- Fireball drops any other malware (or a combination of malware) and can steal credentials, spy on users, hijack social media and communication accounts or just use the whole thing as a massive spam spreading operation.
Why this might not happen
Education is key when it comes to dealing with new cyber threats, Check Point did a fantastic job bringing this infection to the eyes of users at large and the media, it has had a lot of coverage over the last few days and hopefully folks are scanning their systems and removing unwanted plugins to help reduce the power this adware operation has to do anything worse.
In addition to that, while Rafotech (who created Fireball) is using the infection to spread advertisements, they are sitting in a legal gray area and shutting them down would be a bit difficult without some serious international cooperation. However, if Fireball started spreading additional malware, like ransomware or bots, then you’ve got an international crisis on your hands, and law enforcement for every country affected knows who the culprit is, safe to say it would be a bad move.
The worst, worst case
In a nightmare universe, the backend command and control systems that decide what Fireball does is compromised by malicious actors who then drop all kinds of nasty malware on the systems. If that were to happen, you would still have the international crisis but no attribution.
You can guarantee though, that even if the attackers cannot be stopped, Rafotech would take a lot of heat and face serious charges for their involvement in creating this threat, not securing it correctly and handing a nuke to whatever cybercriminal wanted it.
Removing yourself from the problem
Obviously, if your system is infected with Fireball then not only is your safety an issue but also the safety of every other system on the internet. It is easy to weaponize an infected system to be used for direct DDOS attacks, act as a proxy for traffic (hiding the bad guys) to spread malware itself in the case of some spambots.
So, how can you remove your system from being used in this way? It’s pretty easy actually.
- Check your browser
Are you being redirected to the Rafotech search engine or feel like you’ve seen an immense amount of advertisements being pushed to you without provocation recently? If either of those is true, it’s likely you are infected with Fireball.
- Run a scan
Your first step is to download, install, update and scan with Malwarebytes 3.0. This will identify any artifacts on the system belonging to the threat; we detect Fireball as “Adware.Elex.” We know exactly what Malwarebytes can detect concerning this threat, so we are only discussing remediation using our tool.
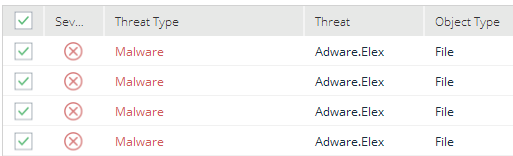
- Find any strange browser add-ons
Fireball utilizes browser extensions and add-ons to help it complete its goal of drowning you in ads. So, you want to make sure there aren’t any that you didn’t install yourself, if you find one that looks strange, go ahead and remove them. You can check out this resource that Facebook put together to help folks clean up the add-ons and extensions they have in their browser which may be causing problems.
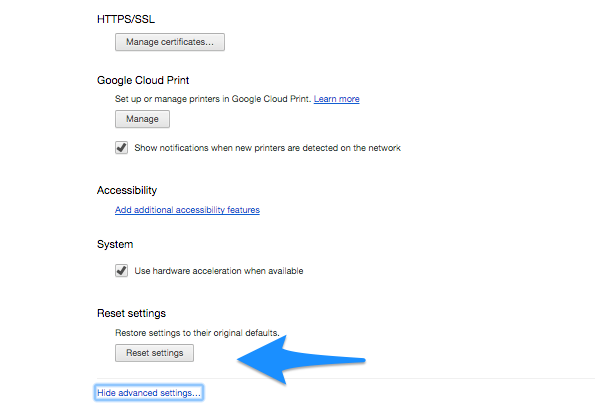
- Reset your defaults
After a Fireball infection, your default homepage and the search engine would have been modified; you can go into your browser settings to change them back to what you want or just restore the whole browser to its default state.
Conclusion
We want to thank Check Point for their fantastic analysis of this threat and bringing it to the attention of the world. We hope that those infected with this adware can find articles like this and learn how to clean up their systems before one of the worst-case scenarios listed above actually become a reality.
In the meantime, it’s best not to consider any malicious threat less dangerous than others, PUPs, adware, spyware, and others are still software installed on a system with the limitations (or lack thereof) of any other piece of software. Just because something is being used for one purpose today doesn’t mean it won’t be repurposed for something far more damaging next week.
Thanks for reading, stay alert, stay safe, and we’ll catch you next time.










