Terror EK is an exploit kit made from a mishmash of stolen code and with very limited distribution. In the past few months, we have seen a few minor updates to its code base which remains largely simplistic in comparison to professional-grade exploit kits of the past such as Angler EK, or modern-day Astrum EK.
We recently observed activity from one actor that appears to be doing some experiments with the toolkit. This post takes a look at a malvertising chain that leads to Terror EK in which the individual had set up his own redirect and bogus fraud page.
Campaign
This particular infection flow started with malvertising related to adult and file sharing traffic. The final redirection to the exploit landing page was handled via a bogus site acting as a direct referrer to Terror EK.
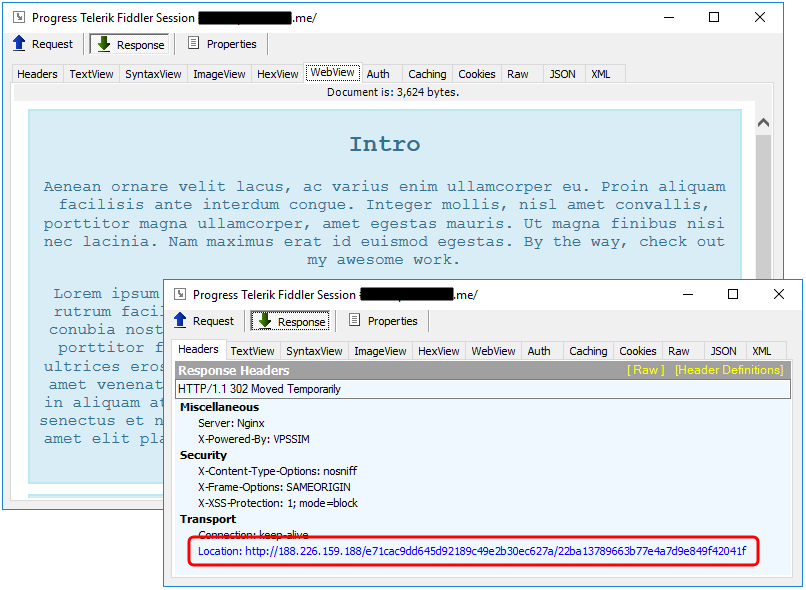
Exploit Kit
As mentioned by Cisco Talos, Terror EK collects some information about the user such as plugins that are installed, and their version which it then sends back to its server. Compared to earlier versions of Terror EK that loaded multiple Flash files at once, it now uses a single one that can target Flash Player up to version 20.0.0.228.
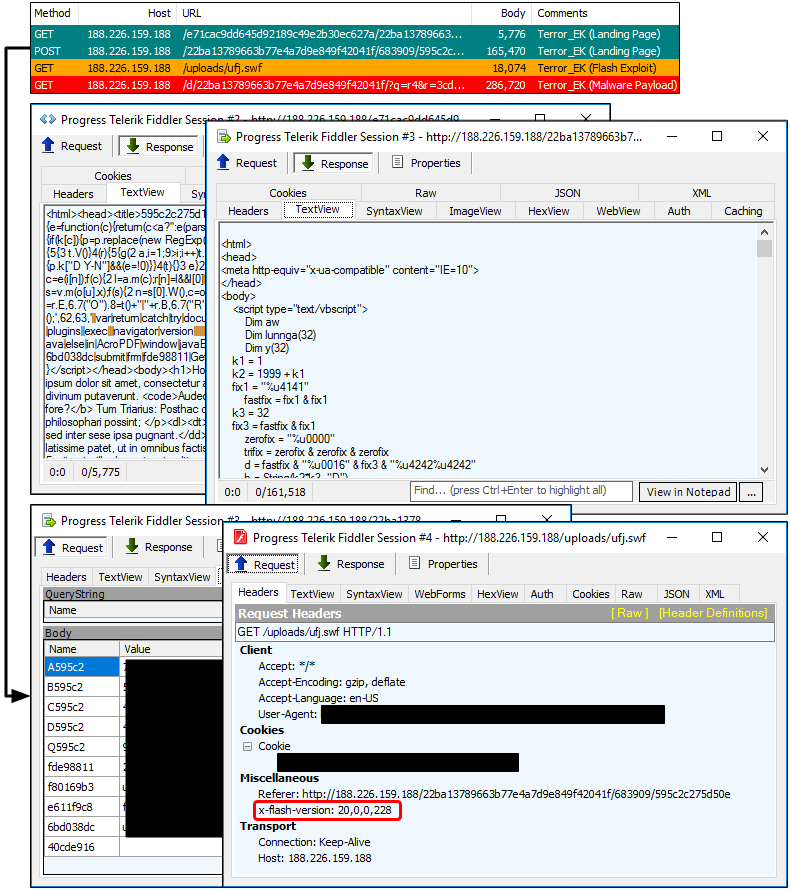
Payload
This campaign dropped the Neurevt bot which downloaded a secondary payload shortly after. The malware’s purpose is to cycle through a predefined list of URLs and open up a new browser window to the next URL every 90 seconds. This list is maintained via a simple user interface hosted on the same IP address as the initial redirector to the exploit kit. This makes us think that the threat actor is managing his small own operation from end to end.
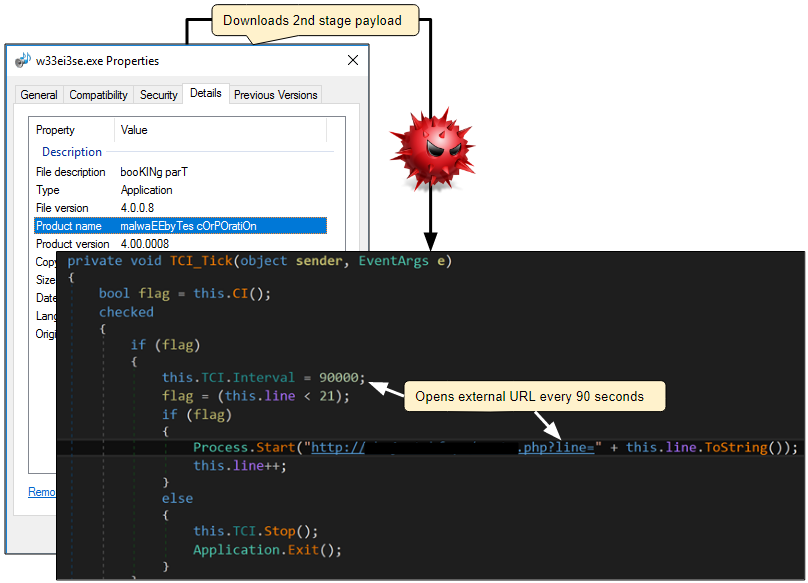
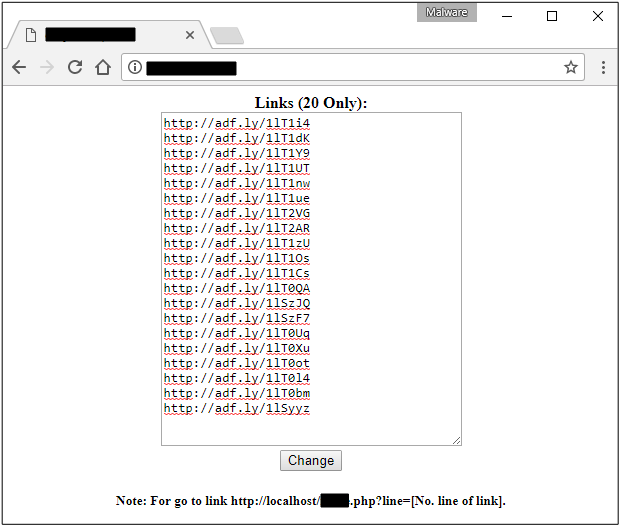
All these URLs are AdFly shortened links for fake remedies spam. AdFly typically pays you a small amount of money each time a new user clicks your link and visits the final URL. The way this business model works is by showing ads for a few seconds before allowing you to visit the URL you were looking for.
While the malware was running in our sandbox, one of such ads pushed a tech support scam:
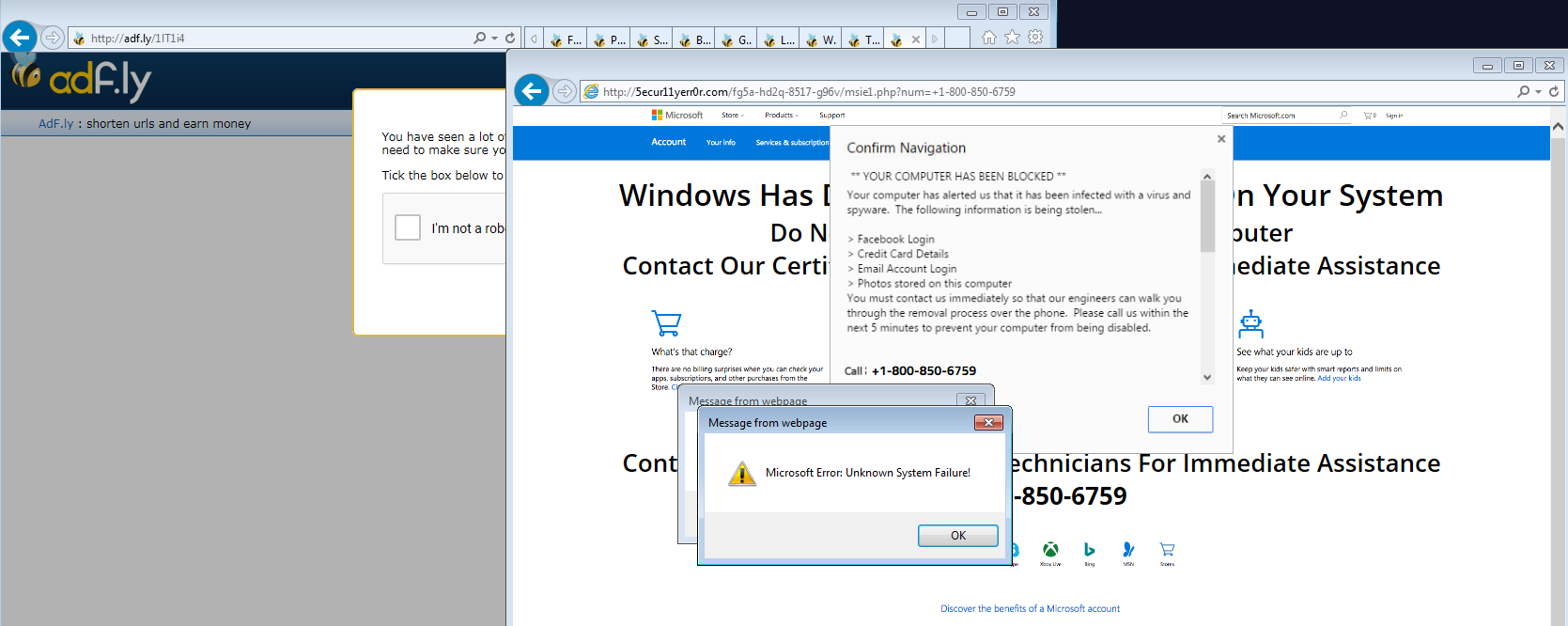
However, using this piece of malware to generate revenue via AdFly seems like a pretty inefficient method. Indeed, AdFly will very quickly detect the suspicious activity when those links are visited from the same computer at short intervals.
Upon notification, AdFly terminated all the fraudulent shortened links.
Mitigation
Like other exploit kits, Terror EK relies on software vulnerabilities that have already been patched. The distribution we have witnessed so far has mostly been via malvertising but on a small scale.
Malwarebytes blocks Terror EK’s exploits and associated malicious traffic.
Indicators of compromise (IOCs):
Terror EK
188.226.159 .188/e71cac9dd645d92189c49e2b30ec627a/22ba13789663b77e4a7d9e849f42041f 188.226.159 .188/22ba13789663b77e4a7d9e849f42041f/683909/595c2c275d50e 188.226.159 .188/uploads/ufj.swf 188.226.159 .188/d/22ba13789663b77e4a7d9e849f42041f/?q=r4&r=3cd3ad4d7992a73038ad37c07e219138&e=cve20150313
Malware drop
404108a0066f6df22bfb4abcec849c214eed089c69b115f5300a2ac631863b1a










