If the following message lands in your mailbox, you may wish to throw on your “This is highly suspicious” cap before proceeding further:
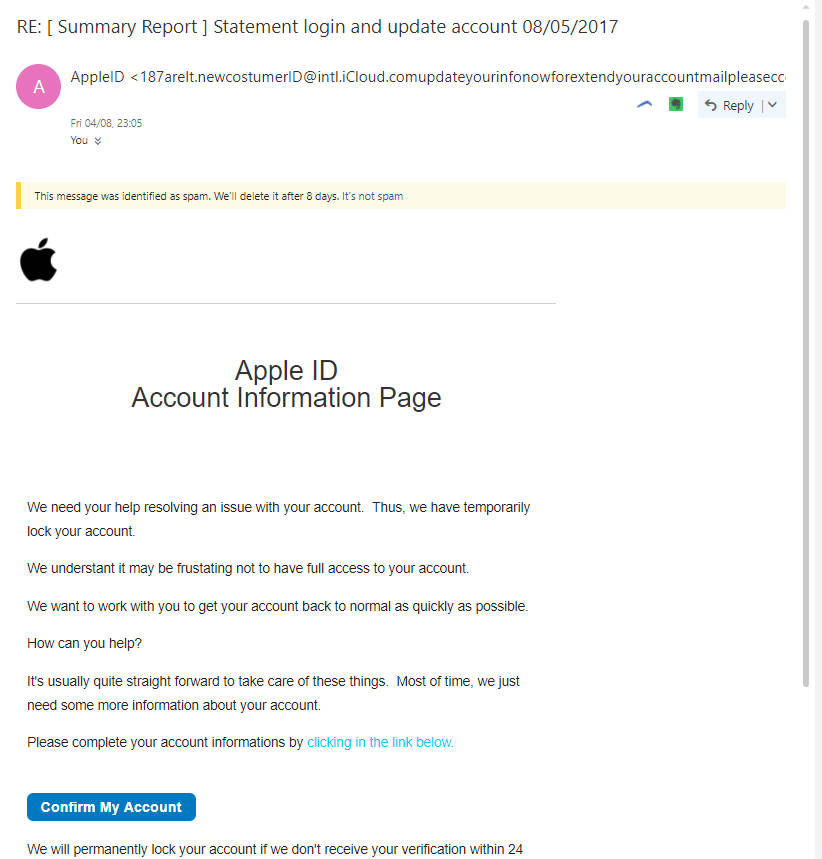
The email is titled
RE: [ Summary Report ] Statement login and update account 08/05/2017
Note the old spammer trick of placing “RE:” at the start to make you think there’s some sort of correspondence taking place.
Spoiler: there isn’t.
The message reads as follows:
Apple ID Account Information PageWe need your help resolving an issue with your account. Thus, we have temporarily lock your account.
We understant it may be frustating not to have full access to your account.
We want to work with you to get your account back to normal as quickly as possible.
How can you help?
It’s usually quite straight forward to take care of these things. Most of time, we just need some more information about your account.
Please complete your account informations by clicking in the link below.
Confirm My Account We will permanently lock your account if we don’t receive your verification within 24 hours.
Regards,
Apple Support
The URL used is a Goo(dot)gl shortener (now deactivated), which was bouncing users to the final destination below located at
online-appleidsupport-accountimportant(dot)net/Login(dot)php?
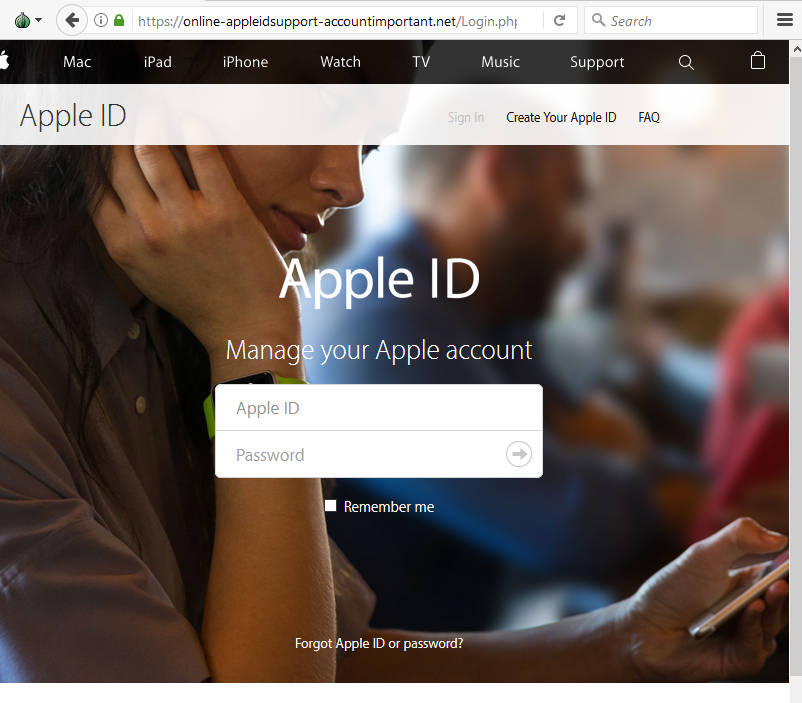
Entering an Apple ID and password results in the following (fake) message that the account has been locked:
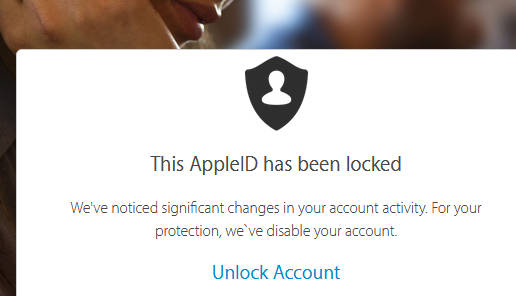
We’ve noticed significant changes in your account activity. For your protection, we’ve disable [SIC] your account.Unlock account
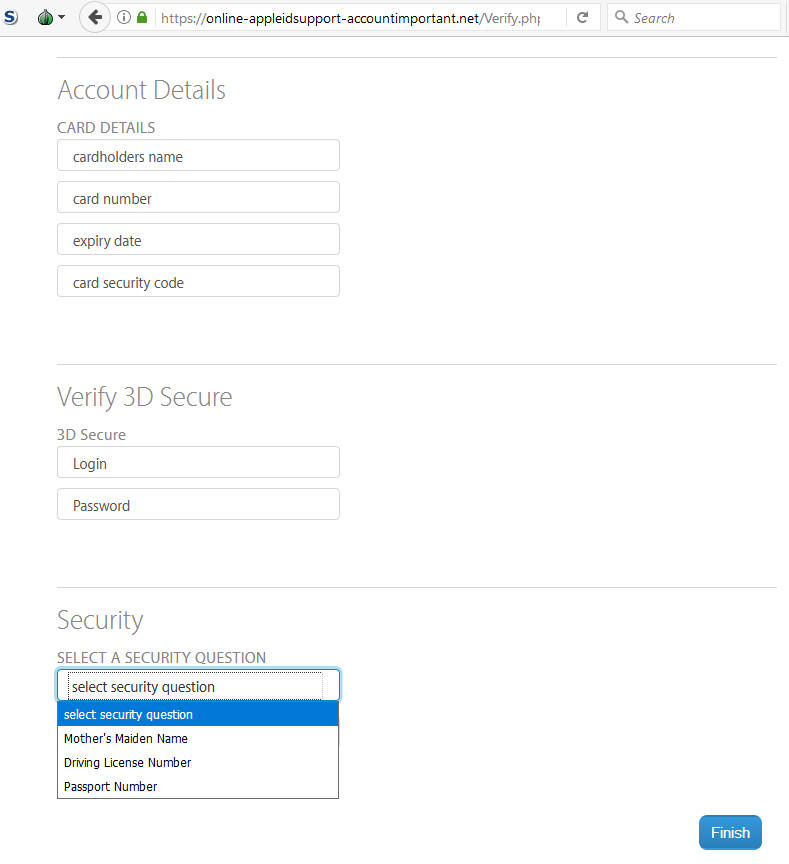
The next page asks for a lot of personal information, including: name, address, DOB, phone number, full card information, security question information, and even 3D secure details.
This is not something you want to hand your details over to. This site joins the ranks of phishing pages making use of HTTPs to appear more authentic – here’s the real Apple sign in page:

You’ll notice it mentions the company name. This is called an Extended Validation certificate. The one being used on the phish page claims to be from a service offering free certs to those possessing a web domain.
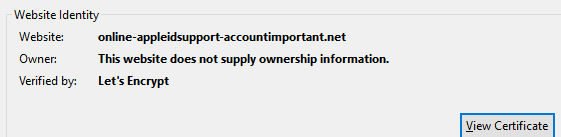
A good example of why you shouldn’t just believe the site in front of you is legit, purely because there’s HTTPs going on in the background. Emails directing you to pages asking for payment info via embedded links should set off all the warning alarms – and this particular email and website combo should be forever banished to your “ignore forever” folder.
Christopher Boyd










