We recently observed a fresh malicious spam campaign pushed through the Necurs botnet distributing so far, two new variants of Locky ransomware.
In our last Q2 2017 report on tactics and techniques, we mentioned that Locky ransomware had reappeared with a new extension, but went dark again for months.
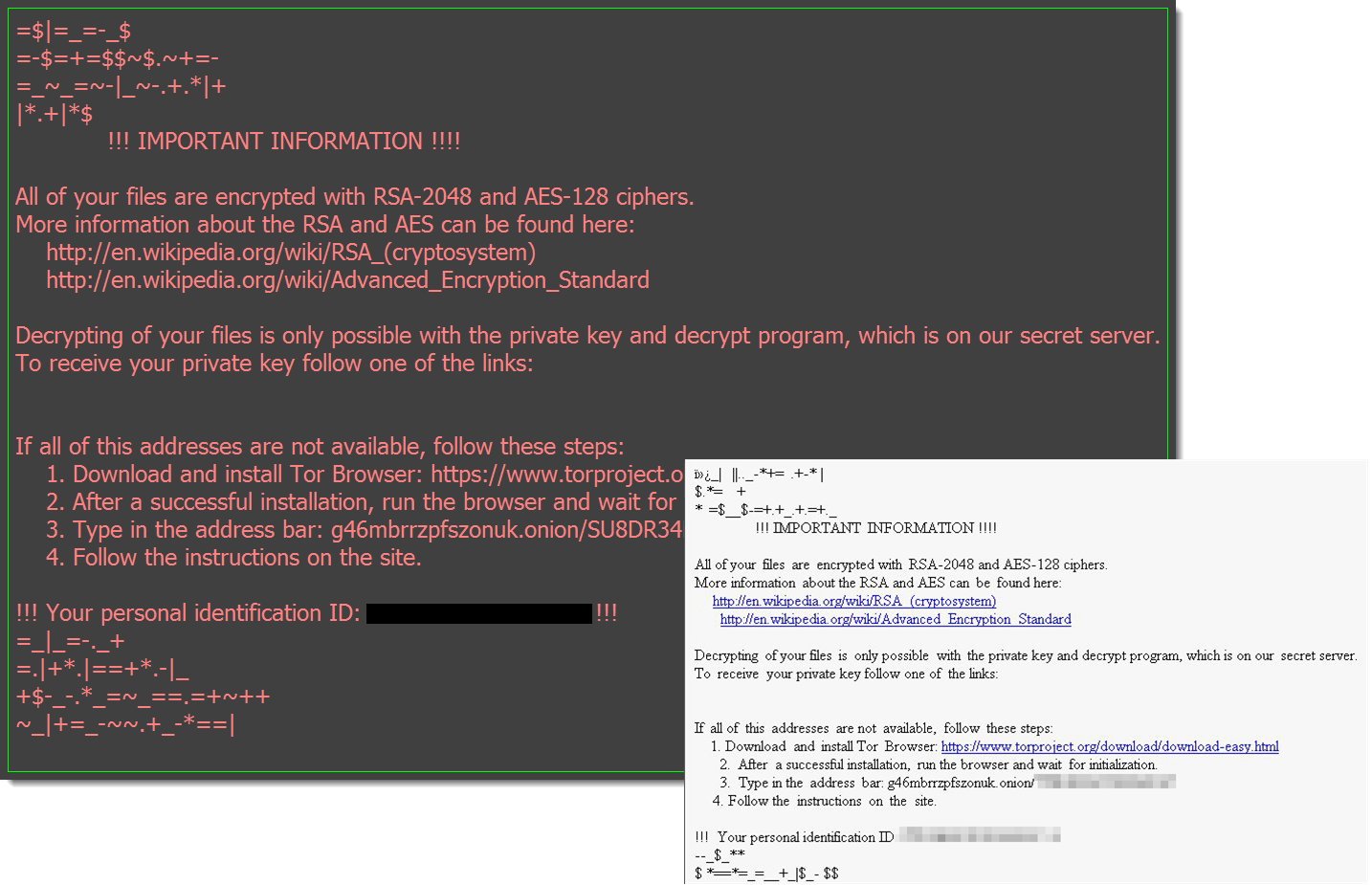
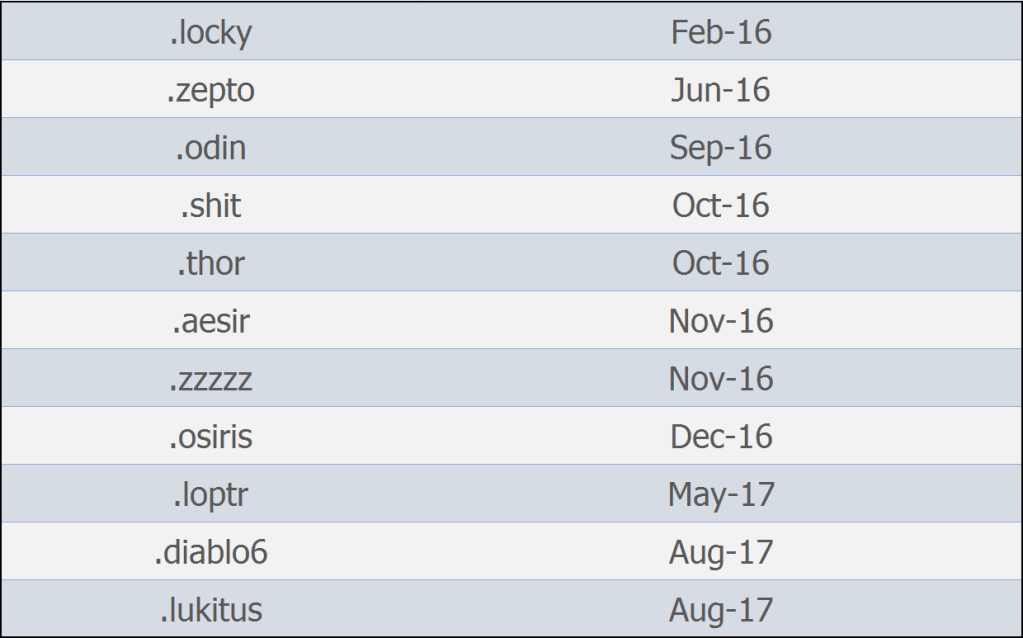
From August 9th, Locky made another reappearance using a new file extension “.diablo6” to encrypt files with the rescue note: “diablo6-[random].htm“.
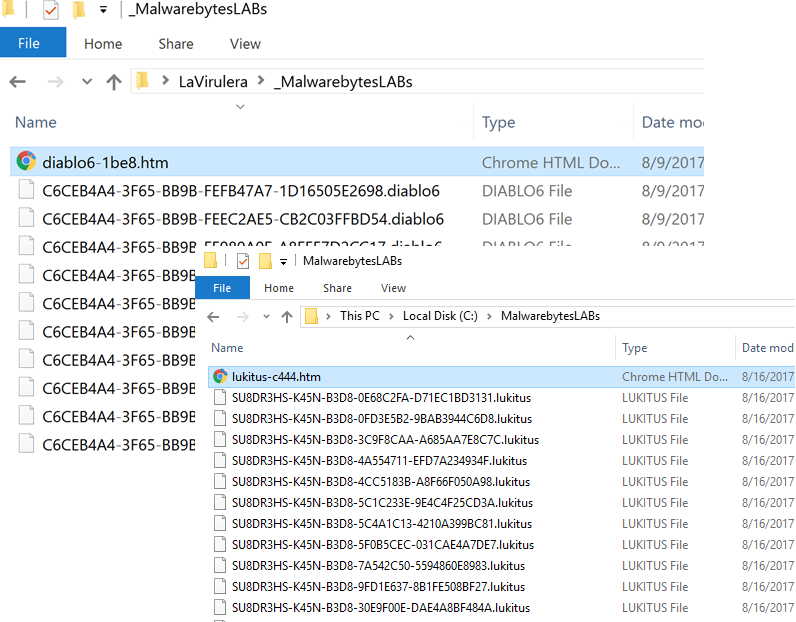
Today a new Locky malspam campaign is pushing a new Locky variant that adds the extension “.Lukitus” and the rescue note: “lukitus.html“.
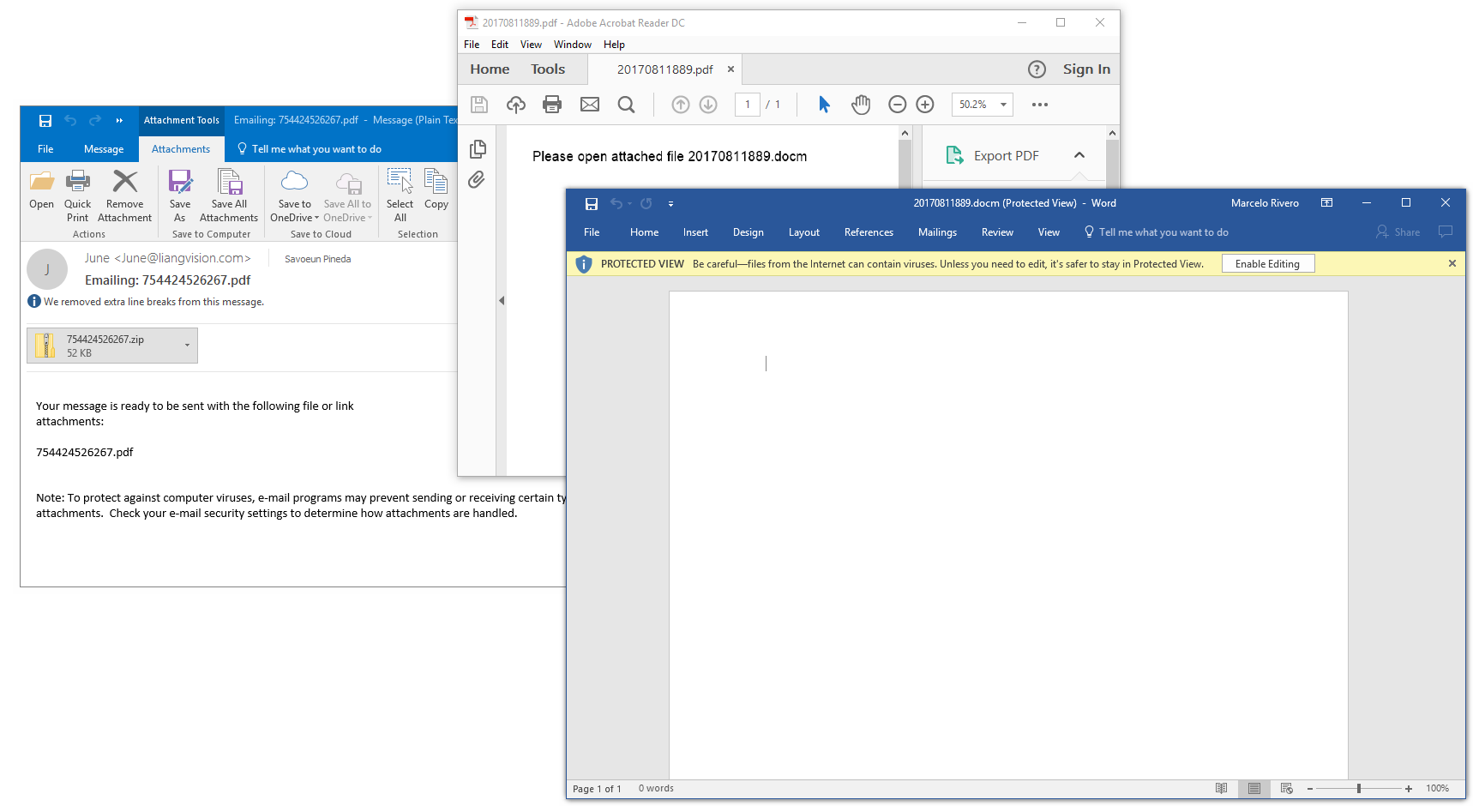
Locky, like numerous other ransomware variants, is usually distributed with the help of spam emails containing a malicious Microsoft Office file or a ZIP attachment containing a malicious script.
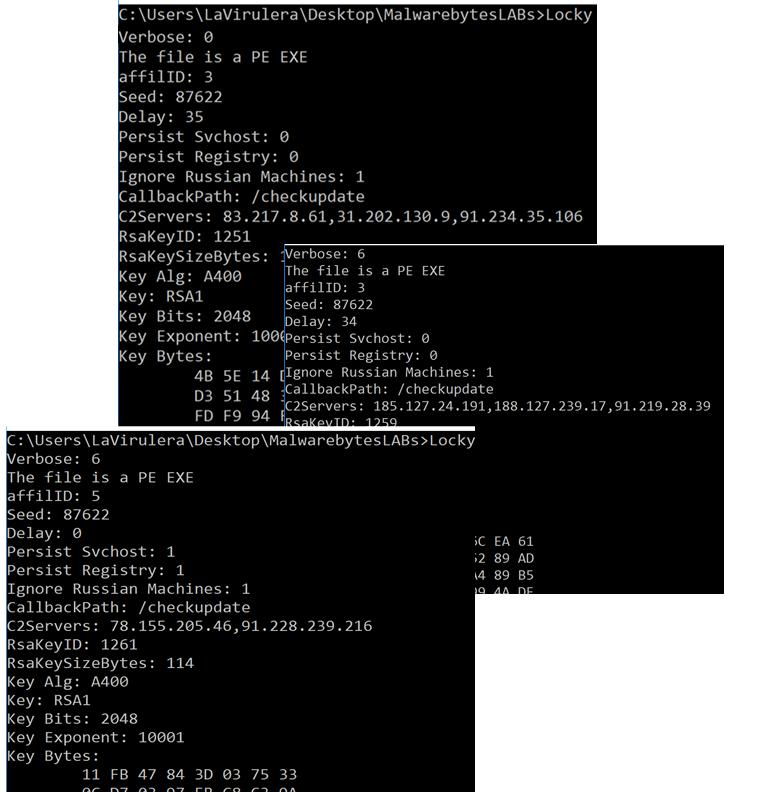
Locky variants, callback to a different command and control server (C2) and use the affiliate id: AffilID3 and AffilID5.
Over the last few months, Locky has drastically decreased its distribution, even failed to be distributed at all, then popped back up again, vanished and reappeared once more.
The ups and downs of Locky remain shrouded in mystery. One thing time has taught us is that we should never assume Locky is gone simply because it’s not active at a particular given time.
Locky extension history
Active Campaigns:
- Aug-09: MalSpam attached .zip with .vbs malware.
VBS: 4c1975295603dbb3994627a499416b71 Payload: 0d0823d9a5d000b80e27090754f59ee5
- Aug-11: MalSpam attached PDF with embedded .DOCM files.
PDF: 84fd7ba91a587cbf8e20d0f2d5fda285 DOC: 97414e16331df438b2d7da0dad75a8d5 Payload: 9dcdfbb3e8e4020e4cf2fc77e86daa76
- Aug-14: MalSpam attached RAR with .JS malware.
JS: badea58f10d5d2bb242962e3c47ff472 Exe: 6b4221adf0ecb55cd1a4810330b4e1e4
- Aug-15: MalSpam attached ZIP with .JS malware.
JS: 5f1af4f2702a6bc7f5250c9879487f66 Exe: 89ed8780cae257293f610817d6bf1a2e
- Aug-16: MalSpam attached ZIP with .JS malware.
JS: f2c97bd1793ff93073bfde61d12f482b Exe: 4baa57a08c90b78d16c634c22385a748
Protection
Malwarebytes protects against this attack at various layers including macro and ransomware mitigation, and neither of those required any signature update.










