When goods get sold in large quantities, the price goes down. This might not be the first law of economics, but it’s applicable. An extrapolation of this is that if there are practically no production costs and no raw materials involved, prices of such goods will drop to zero. Usually, they will be offered as free gifts to promote the sale of other, more costly goods.
Something like this has happened to SSL certificates. They are offered for free with web hosting packages by several companies, including those that don’t do a thorough check into the identity of the buyer. Better said: They couldn’t care less who buys the package as long as they pay the bills.
So, while users can now expect to see the green padlock on every site, especially the ones where they make financial transactions, the trust that we can put into the underlying certificates is going down.
Definitions
To clarify what we are talking about, let’s have a look at the definitions of the protocols we are about to discuss.
Hypertext Transfer Protocol Secure (HTTPS) is a variant of the standard web transfer protocol (HTTP) that adds a layer of security on the data in transit through a secure socket layer (SSL) or transport layer security (TLS) protocol connection.
Secure Sockets Layer (SSL) is a computer networking protocol for securing connections between network application clients and servers over an insecure network, such as the Internet.
Transport Layer Security (TLS) replaced SSL when it was deprecated, but TLS is backwards-compatible with SSL 3.0.
So, basically TLS is a computer networking protocol that provides privacy and data integrity between two communicating applications. It’s used for web browsers and other applications that require data to be securely exchanged over a network.
The green padlock
So, where does the green padlock come into play? The green padlock simply means that traffic to and from the website is encrypted. A certificate, provided by a certificate provider (Certificate Authority or CA), is used to set up this encryption. Sounds good, right? But the only thing you can actually be sure of when you see such a padlock is that your computer is connected to the site that you see in the address bar.
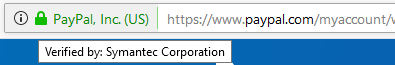
Let’s use the example above to explain some of this. A right-click on the padlock shows us some more information about the secure connection.
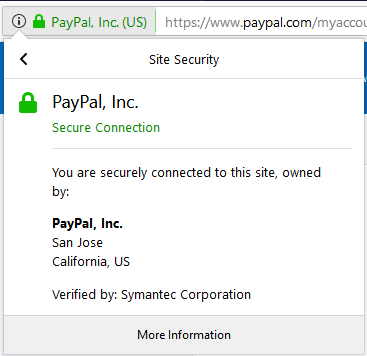
So, we have a secure connection to the domain paypal.com owned by PayPal, Inc. and the Certificate Authority is Symantec.
Let us compare this authentic one to the one in use by a known PayPal phishing site:
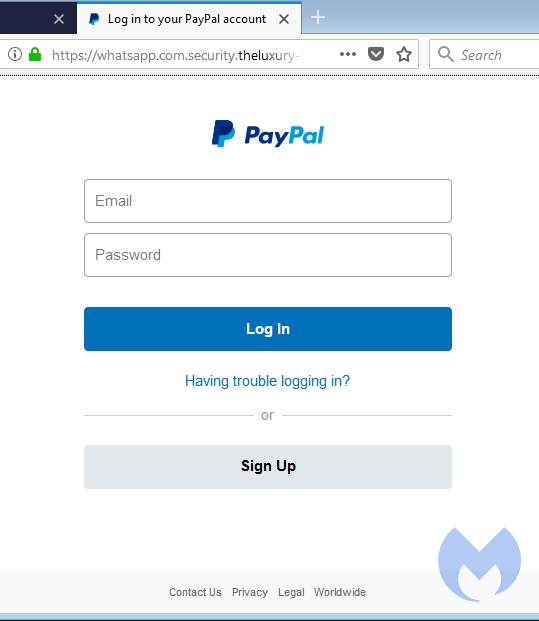
As you can see, the phishers have a green padlock on their site as well. But when we have a look at the details:
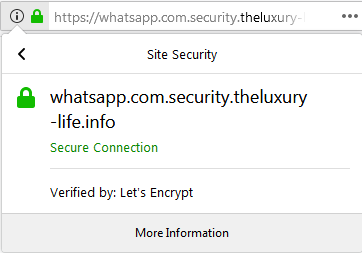
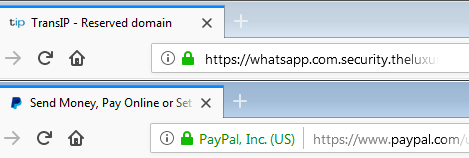
It is easy to see, from the browser address bar alone, that we are not connected to paypal.com. And in the additional information, we can see that the phishers used a free certificate from the CA Let’s Encrypt.
I do realize that in this example it was easy to see the wrong address in the browser’s address bar, but typosquatted domains can be a lot harder to spot, as they purposely use domain names that look similar to the legitimate site. PayPal has registered many such typosquatted domains to protect their customers.
So, we’ve established that the green padlock alone is not enough. In fact, over a million new phishing sites surface every month. Given how many new sites—not just phishing sites—are created every day, and knowing that hosting deals include free certificates and are cheap as dirt, we can easily assume that hosting providers do not have the resources to check each and every new site. Even if they did perform these checks, who is going to check whether the site does not get changed once it has gone live?
So, since the visitor is the one facing the consequences of entering his credentials on a phishing site, it looks like the ball is in his court.
But there is help
You do not need to feel helpless. The cavalry comes to the rescue in many shapes and forms. Some browsers warn you before they let you visit known phishing or other malicious sites. This method is based on blacklisting, so if you are among the first visitors, you could still wind up on such a site without a warning.
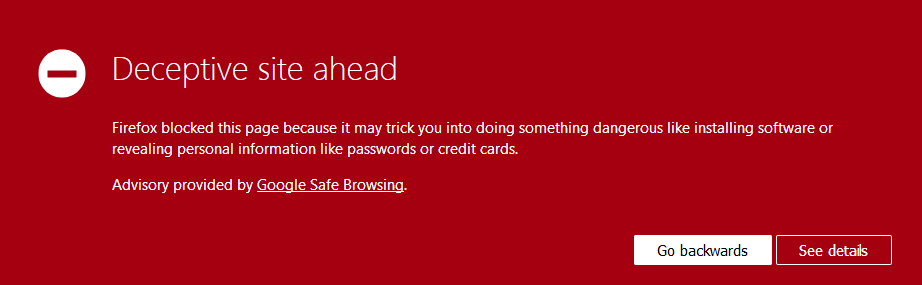
Some security software, including Malwarebytes, blocks known phishing and other malicious sites. These methods can be based both on blacklisting and behavioral analysis.
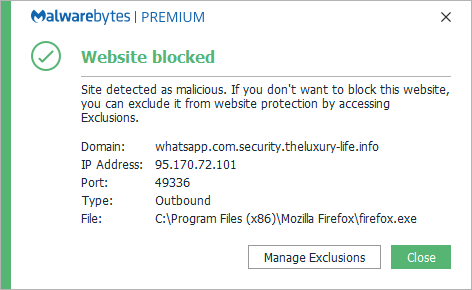
And there are certificates that do get issued only after extended checks. These are called EV (Extended Validation) certificates. To show the difference, we need to double back a bit.
The bottom screenshot is the original PayPal certificate, and it is an extended one. The top screenshot is a regular Domain Validation (DV) certificate (which was used by the phishing site). As you may notice, the EV certificates are displayed differently from the DV certificates. The difference in how they are displayed varies per browser, so you might want to familiarize yourself with the way that these are displayed in your browser of choice.
Check, check, triple-check
Since HTTPS and TLS are becoming commonplace and cheap, phishers are no longer barred in any way from using the green padlocks on their deceptive sites. As a consequence, users are under advise to pay attention to the kind of certificate behind the padlock.
The best practice is to have shortcuts for the websites that you use to transmit personal or financial data, rather then clicking on links sent to you by mail or found by other means. At first contact, the things to check on a website that require entering personal information or credentials are the following:
- Is there a green padlock in the address bar?
- Does the address in the browser’s address bar match your expectations?
- Is there an EV certificate or not?
Only when you are satisfied that the website belongs to the domain of the company that you wished to pay a visit, enter your credentials or personal data.
Stay safe!











