About three weeks ago, we published our second CrackMe. It triggered a lot of interest, and we got many high-quality write-ups. Choosing the winner was really difficult!
In this post, I am going to summarize the contest and comment on the received submissions.
CrackMe 2 challenge
The topic of the challenge was Python, and its goal was to teach how the Python scripts can be packaged and integrated with native executables. The involved Python script was not obfuscated, and the user was supposed to adapt it for the purpose of finding the solution.
The CrackMe was made of three components, cooperating with each other:
- a Python script (converted to EXE with the help of PyInstaller)
- a native DLL, loaded with the help of the above script
- a Python script unpacked by the DLL and injected into Actxproxy.dll
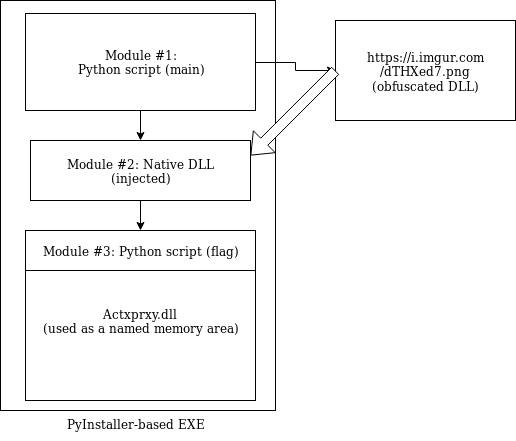
In the first level, the user was supposed to find a valid PIN to decode a URL, from which the next level was downloaded. The next level was a native DLL that was injected in the main, Pyinstaller-based EXE by the initial script.
After the second level was passed, the DLL was unpacking another piece of obfuscated Python script and injecting it into the header of Actxproxy.dll. When the DLL finished and the execution was passed back to the main script, the chunk of data was read from Actxproxy.dll, decoded, and executed. So, the Actxproxy.dll was used not as a DLL, but rather as a named memory area where the data was covertly passed from one component to another.
There were a number of other techniques used, such as:
- A covert way to host and download a PE file: a PE was encoded as an image (with file2png.py) and hosted on a image-hosting site
- A Reflective loader (based on the Steven Fewer’s template)
- A modified PE header, thanks to which the PE file can be injected like a piece of shellcode
- Changing the execution flow with the help of exception handlers
- Using a pseudo-random sequence as an AES key (taking advantage of the fact that the standard function rand() is not really random—a sequence generated with the same seed will be the same)
Statistics
The CrackMe has so far been downloaded 956 times (653 of those were in the first weekend after the release).
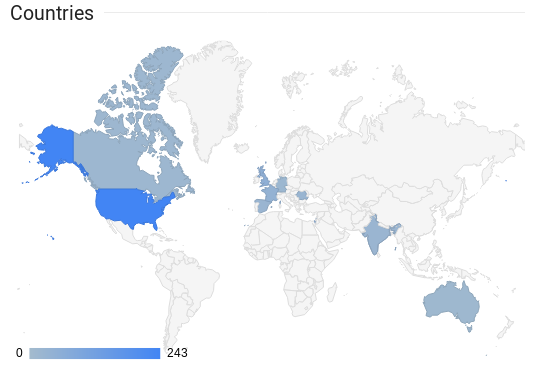
We had people from all around the world participating. The most downloads were from the US (243), Israel (59), and the UK (52).
Hall of fame
The submission was counted as valid if it contained the final flag:flag{“Things are not always what they seem; the first appearance deceives many; the intelligence of a few perceives what has been carefully hidden.” – Phaedrus}”>
In total, I got flags from 25 people. Congratulations to all of you, you did great!
12 people solved it during the first weekend:
The remaining 13 solved it in the following days:
- May 1: @x64_asm_user
- May 1: @fedox9
- May 2: @LadislavZezula [write-up] [video]
- May 2: @n3v___
- May 2: @tqkve [write-up]
- May 2: @vinod50rao
- May 3: @agschipor
- May 3: @voidm4p [write-up]
- May 3: @ravitiwari1989 [write-up]
- May 6: @MalwareLion
- May 10: @Jacob_Pimental [write-up]
- May 15: @th3m4ks [write-up]
- May 18: @nictln [write-up]
Write-up scoring
Due to the high quality of the received write-ups, it was hard to select the winner. In order to introduce some objective measures, several categories were used to assign points.
The first category involved an in-depth explanation of the inner workings of the CrackMe, guiding through the process of solving. This means writers should have:
- Explained how to identify that the executable is in reality a wrapped Python script
- Provided tools and an explanation of how to unpack the PyInstaller executable back to Python script
- Demonstrated how to find the password having an MD5
- Explained why the key generated is using rand() and is not really random
- Provided and explained a sourcecode of brutforcer for the PIN
- Explained how the PE file is decoded from the image
- Noticed and understood the PE header modification (shellcodified PE)
- Noticed and understood the Reflective Loader in the DLL
- Explained how the VEH was used to modify the execution flow
- Noticed what checks were made in order to prevent the DLL from running outside the Python
- Explained the mechanism behind the “secret console”
- Explained how the Actprxy.dll is used as a communication channel between the two independent modules
- Analyzed the injected data and minimized the set of the characters that has to be brutforced
- Explained what (and why) to expect in the output (in level 3 decoding)
- Provided and explained the script used to solve the final Python chunk
The second category was style. Writers should have:
- Introduced tools before they were used, showing the environment setup
- Provided detailed explanation of the used techniques, reaching beyond the CrackMe itself. For example, providing links where the reader can learn more.
- Provided graphical illustration of the taken steps. Diagrams, GIFs, videos, etc.
- Been especially clear and had a pleasant writing style
You could also get some bonus points for OSINT if you found:
- My tool to do exactly the same conversion as used in the CrackMe (file2png,py)
- My post explaining in detail how to unpack PyInstaller-based EXE
- A malware that previously used any of the descried techniques (i.e. shellcodified PE was used by Shakti Trojan, PyInstaller package was used by Telegram RAT, Reflective Loader is commonly used by multiple malware, for example the dropper of the original Petya)
Points per write-up (plus, their extra features that gave a bonus point)
- @Hexacorn’s write-up: 8
- @_qaz_qaz’s writeup: 13.5
- @pieceofsummer’s write-up: 8
- @KernelM0de‘s write-up: 8.5
- @Eleemosynator’s write-up: 16
- @LadislavZezula‘s write-up and video: 13.5
- adding the video to the write-up was really cool!
- @tqkve’s write-up: 7.5
- interesting explanation how to manually extract the pyc module from PyInstaller-based EXE
- @voidm4p‘s write-up: 12.5
- @ravitiwari1989’s write-up: 13.5
- @Jacob_Pimental’s write-up: 8
- @th3m4ks’s write-up: 12.5
- @nictln’s write-up: 12
- the best way to solve the last stage: plaintext attack instead of brutforce
The write-ups showed a diversity of ideas, each of them providing a fresh perspective and a valuable source of learning for the people who want to enter into our field. Thank you so much for your participation! As a small token of our appreciation, we decided to give Malwarebytes swag to each writeup author! You can contact me via twitter for details.
Winners
I decided to reward four authors, who’s solutions stood out:
- @Eleemosynator
- @ravitiwari1989
- @_qaz_qaz
- @LadislavZezula
Each winner can choose a book of their liking (in a printed or electronic form). Contact me on Twitter for receiving the reward. Congratulations again, and thank you for all the work that you put in writing the solution!