[Update 2018-06-22]: New URI patterns observed (probably for several days already).
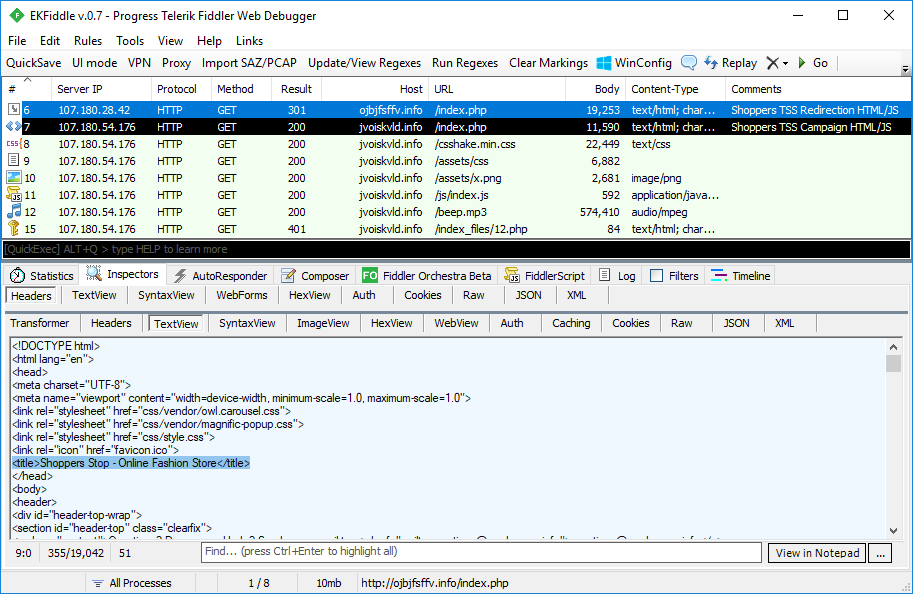
[Update 2018-05-17]: Shoppers Stop is a legitimate company based out of India and their brand was abused by scammers.
These days, there are a lot of browser locker campaigns fueled by malvertising or redirection from hacked sites. But the Shoppers Stop tech scam campaign is actually a bit of both, using compromised sites injected with advertising code that redirects users to other threats, including tech support scams, via malvertising.
We believe those ad injections came from pirated CMS themes. Normally, these are WordPress themes that people typically have to pay to download. Instead, they are offered for free, with a bonus bundle of malicious code.
One aspect we noticed as part of the redirection mechanism was an online shopping portal registered to domains with suspicious TLDs such as .trade, .accountant, .ml that quickly rotate to make blacklisting approaches futile. However, using that same artifact, we were able to flag other browser locker incidents for this particular campaign.
The browlock
The browser locker used in this campaign is a spin-off of the Google Chrome Safebrowing warning. The scammers have added scare tactics to it (e.g. Hard Drive Safety Delete Starting in: 5:00 minutes), as well as authentication pop-ups that prevent the user from closing the browser tab or window.
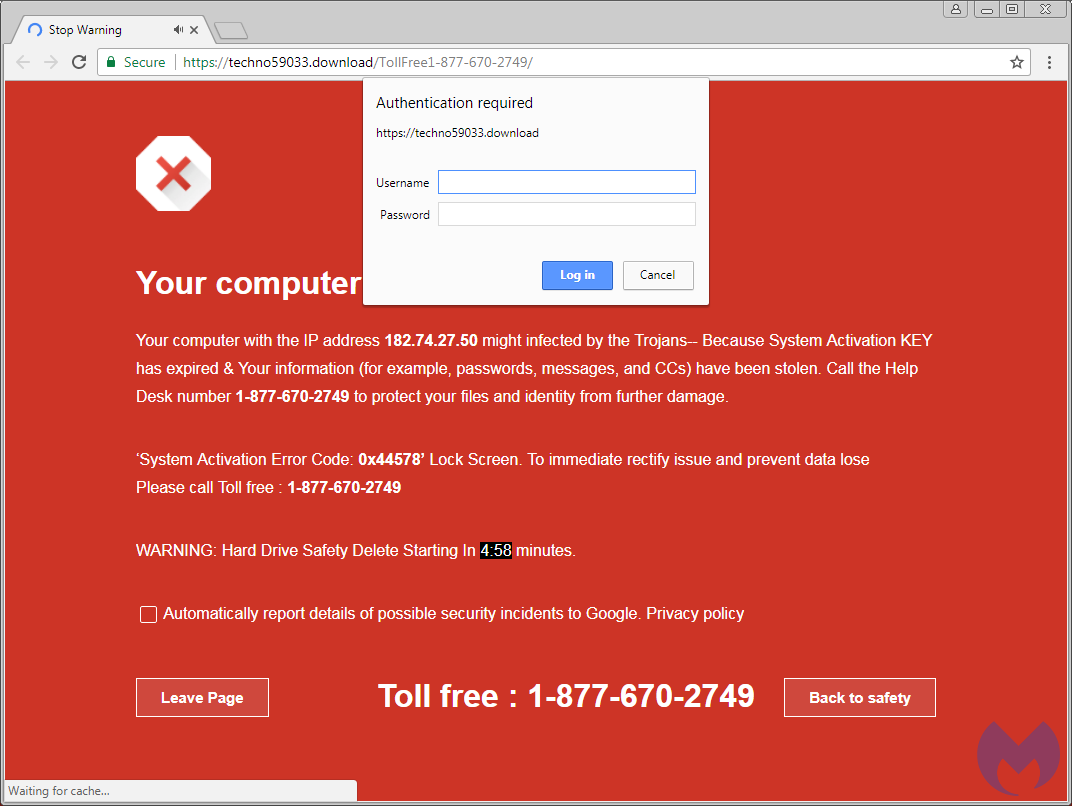
In this template, the crooks have not bothered with changing the IP address (supposedly of their victim), which still belongs to the original creator of that page, located somewhere in India. The toll-free number, dynamically populated both on the page and the URL, is what the scammers hope potential victims will dial.
Traffic
As mentioned earlier, the number one vector of traffic to these browser locker pages is advertising—more precisely, malvertising. Perpetrators can spend a small budget and attract a fair amount of visits through one of many ad networks. More and more, we are seeing ad platforms ensure that visitors are legitimate and not bots or others using anonymous proxies.
In some cases, this ‘lead funneling’ is doubled by the use of a traffic distribution system (TDS). Here’s an example we captured via the well-documented BlackTDS, redirecting users to ad networks and eventually to the browlock.
BlackTDS has been the source of many browser lockers that have been caught by other researchers as well. For example, on March 29, Vitali Kremez reported an infection chain to a browlock started via smarttraffics[.]ml.
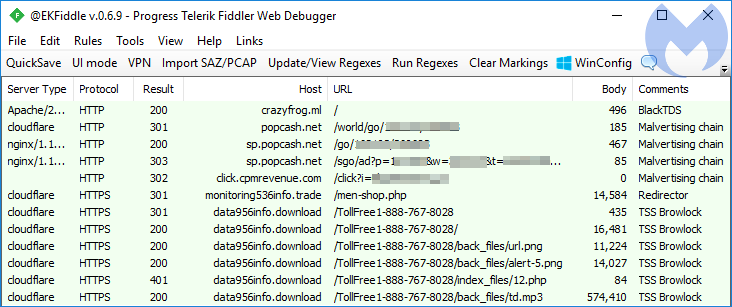
Another instance of the same threat was found as part of an ongoing campaign of compromised websites injected with ad network code. There have been reports from site owners since late last year, but the trend has increased recently.
Denis Sinegubko from Sucuri noted that an ad script with the same ID was injected into over 2,000 websites and drew the conclusion that this was not a case of webmasters using ads for monetization, but rather unwanted ad injections into their CMS. Using the Source Code Search Engine PublicWWW, we found thousands of websites with the same ad codes:
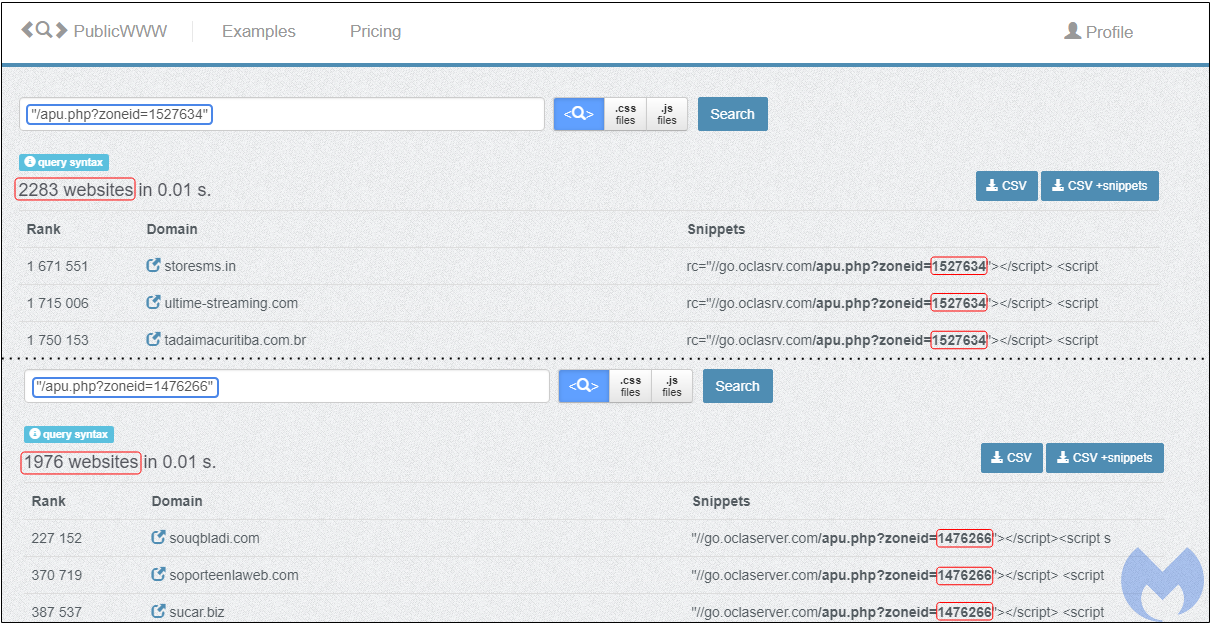
For several weeks now, we have reproduced numerous infection chains to exploit kits, browlocks, and other scams via those injected ads.
//go.oclaserver[.]com/apu.php?zoneid=removed //go.mobtrks[.]com/notice.php?p=removed&interstitial=1 //go.mobisla[.]com/notice.php?p=removed&interactive=1&pushup=1 //defpush[.]com/ntfc.php?p=removed
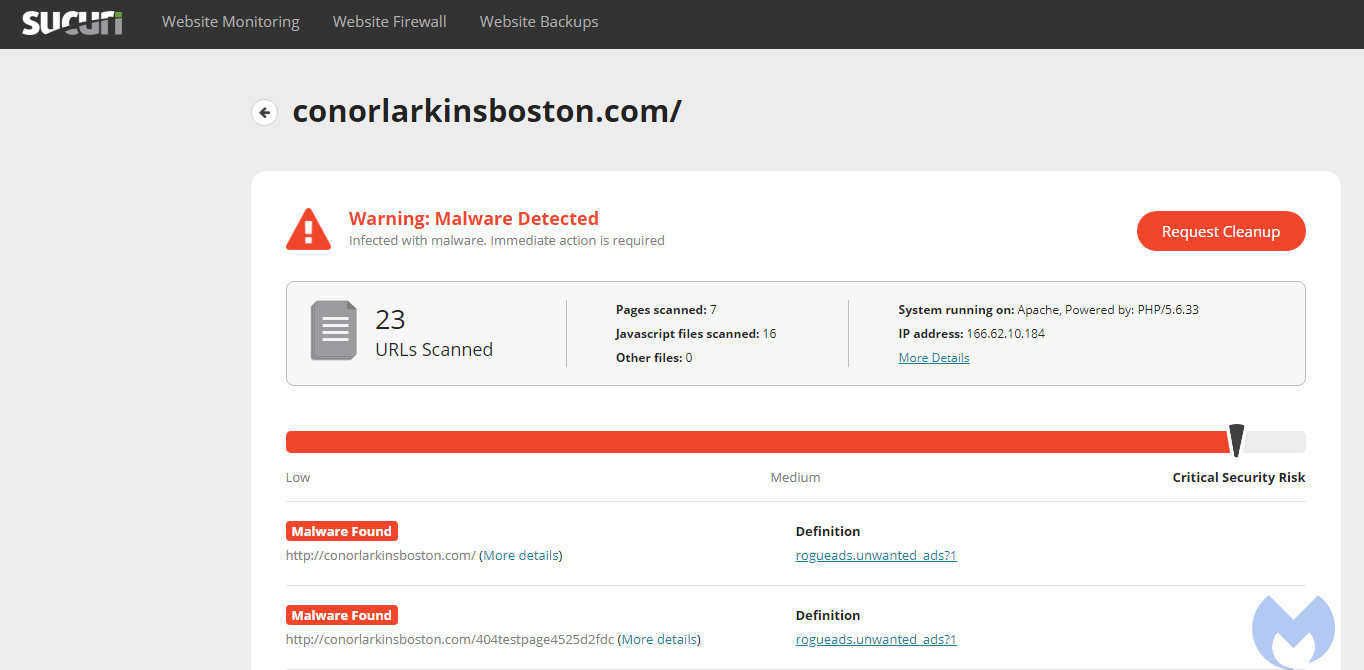
The server side PHP code (WP-VCD malware) used to load those ads can be seen below. Thanks to our friends at Sucuri for sharing it.
Sucuri’s SiteCheck detects these server-side injections as rogueads.unwanted_ads. The leading cause for these injections are Nulled themes, pirated copies of paid-for CMS themes. The free lunch often comes with backdoors, lack of future updates, and of course violating licensing and copyright laws.
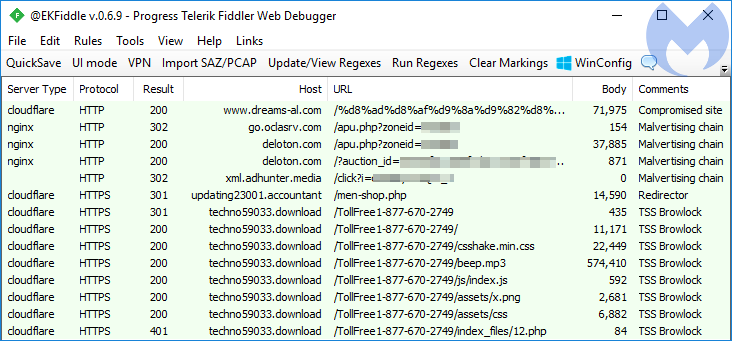
In the following traffic capture (thanks Baber Pervez), we notice the ad injection leading to a malicious redirection chain via the following sequence:
- dreams-al[.]com (Compromised site)
- oclasrv[.]com (PropellerAds ad network)
- deloton[.]com (PropellerAds ad network)
- xml.adhunter[.]media (XML feed)
- updating23001.accountant (Shoppers Stop Redirector)
- techno59033.download (Browlock)
- updating23001.accountant (Shoppers Stop Redirector)
- xml.adhunter[.]media (XML feed)
- deloton[.]com (PropellerAds ad network)
- oclasrv[.]com (PropellerAds ad network)
We have observed the same pattern (or similar pattern) from many sites that had been injected with the ad code snippet.
Redirector
The redirector page acts as a gateway to the browser locker. On the surface, it is an online shopping store called Shoppers Stop, offering merchandise for men and women. Shoppers Stop is also the name of a well-known Indian department store chain with over 83 outlets across the country. We believe the scammers may have been using that name to set up either a fake online store or a demo (many scammers are also into website design).
https://updating23001[.]accountant/men-shop

This domain is itself a clone of goshopper[.]info, which was registered via privacy protection on 2017-10-27 and is now parked:
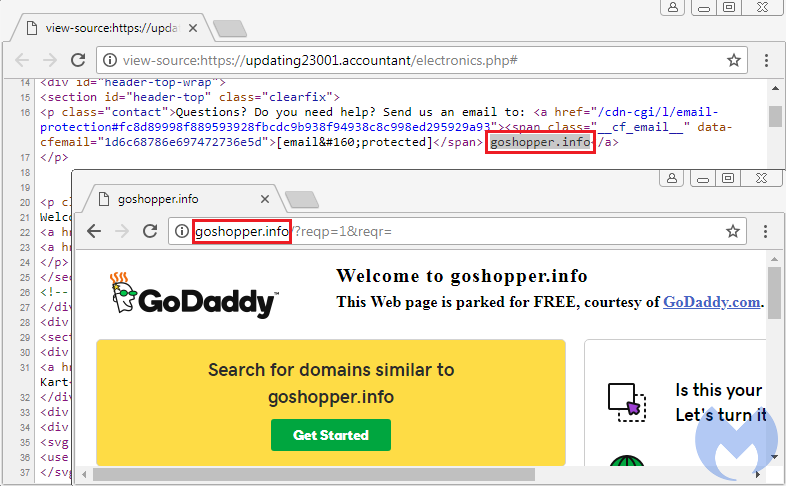
However, in these malicious redirections, the online shopping site is purely used as a redirection mechanism, which is done in such a way that victims will not actually view any of the content. The redirection is done via 301 redirect, also known as a permanent redirect, typically used for SEO purposes by website owners that have moved their property to another (permanent) location.
location: https://techno59033[.]download/TollFree1-877-670-2749
Performing a search on the address provided in the contact page gives us a lead about a .com domain called e-storekart[.]com created on November 7, 2017. While there may not seem to be anything special about it (it is yet another clone), its whois information provides us a bit more information than the other domains we had cataloged before.
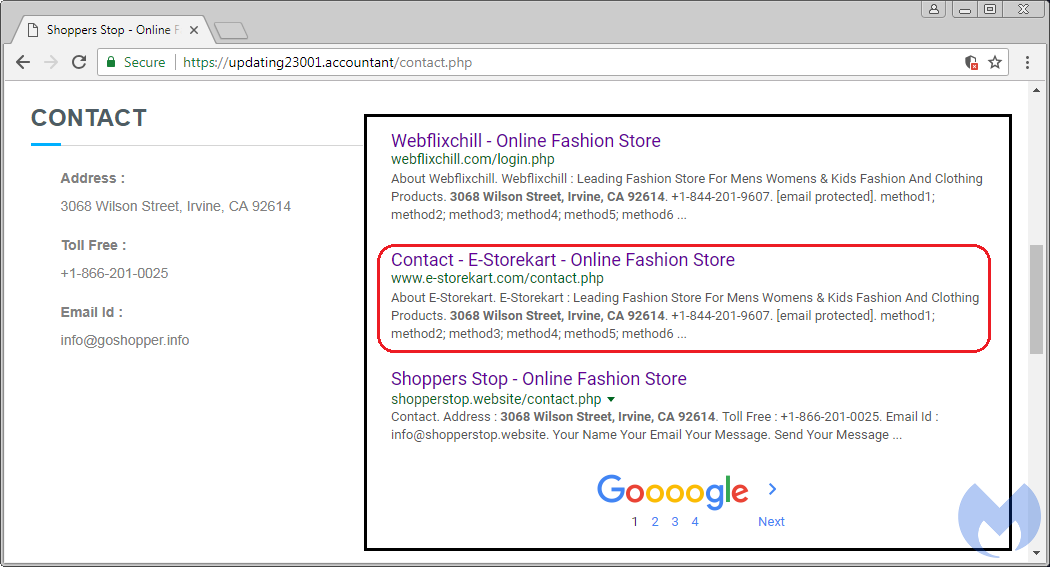
e-storekart
This domain was one of the few Shoppers Stop templates that didn’t have a completely anonymized whois. Querying on the string bhushan, we identified multiple other domains ranging from support sites for printers, help with email, web design, fashion, and more. Many of those domains no longer exist or have already been parked.
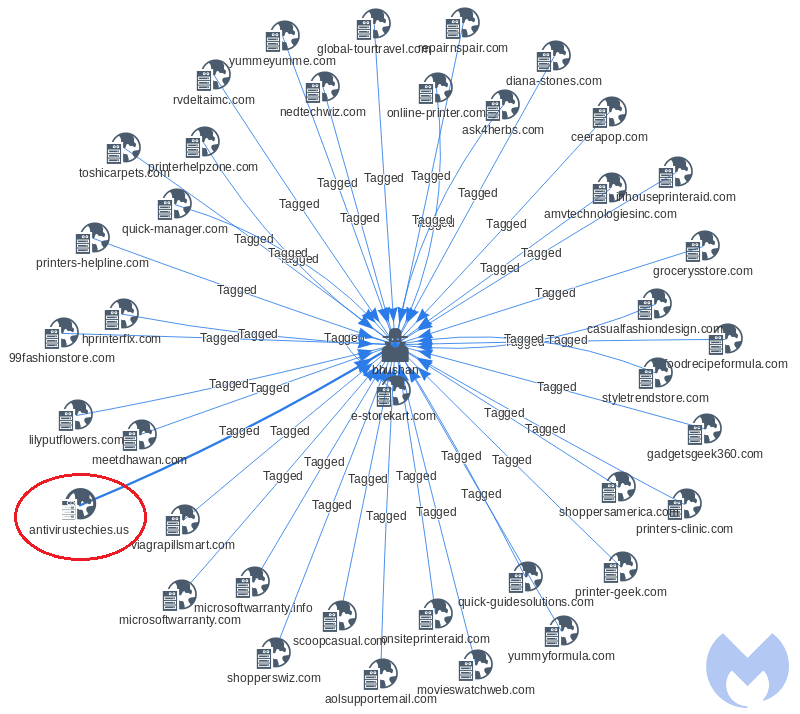
But even inactive domains can provide some valuable information. For example, we retrieved an archived copy of antivirustechies[.]us that shows it used to be a “legitimate” tech support page for several different antivirus products.
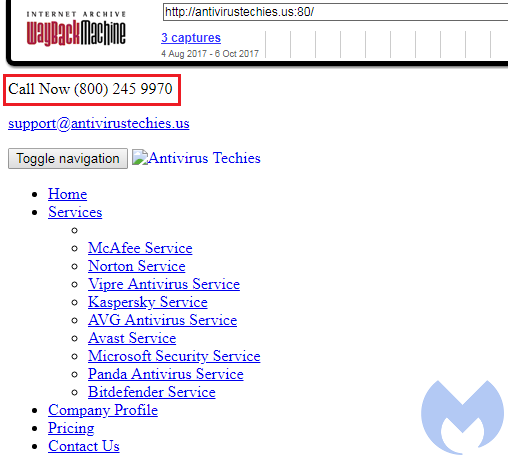
However, the legitimacy of this company was quickly undermined after a few searches for its phone number. It is associated with many complaint reports indicating that people were cold called with the usual scare tactics (fake Microsoft support):
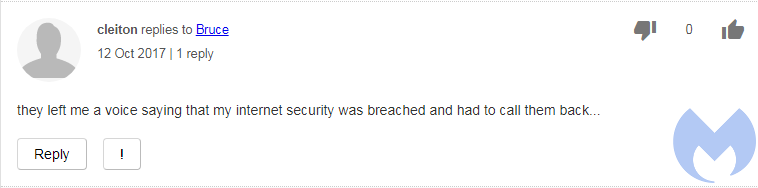
Additional evidence comes in the form of a browser-locker template with that exact phone number on a page hosted at palmreader[.]website/1-800-245-9970/. If you recall, the browser locker depicted at the beginning of this article is very much the same. The URL contains the phone number in its path, and the fake Safebrowsing template is similar as well.
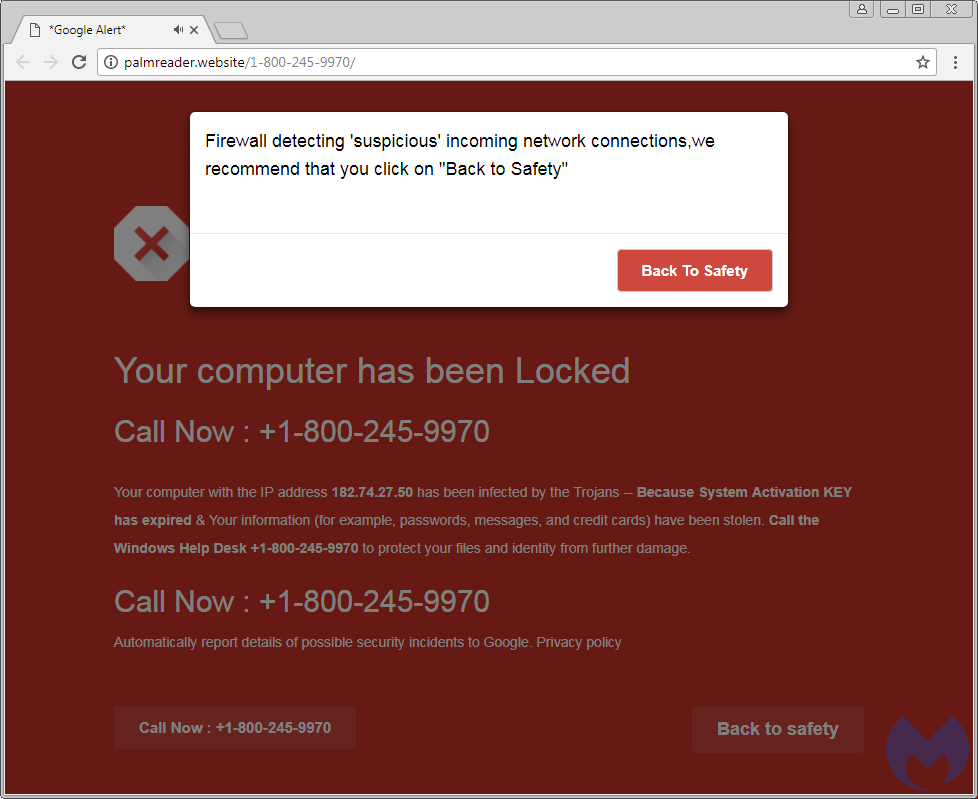
The registration date for that domain goes back to late August 2017. A couple of other phone numbers are also used here, and hardcoded in the URI path, rather than being generated via an API on-the-fly.

To summarize, the same scammer group that used the Shoppers Stop template late last year has already registered a tech support domain (antivirustechies[.]us) and a phone number with the same type of browser locker as used in their Shoppers Stop campaign.
While it can be tricky to link threats based on material that could have been stolen from others, this information can also be helpful in discovering interesting connections to additional web properties associated with fraudulent activities.
This tech support scam is among the top campaigns we are tracking (trailing just behind the .TK and .CLUB campaigns). It’s getting a lot of traffic leads from a large number of sites that have been injected with ads, on top of its other malvertising chains.
Malwarebytes users are protected against this threat thanks to domain blocks on oclasrv[.]com and deloton[.]com. We have also reported the advertising IDs we were able to collect to PropellerAds, and the malicious redirector domains/browlocks to CloudFlare.
Indicators of compromise
107.180.28[.]42
107.180.54[.]176
A list of the domains used for the browser lockers can be found here.










