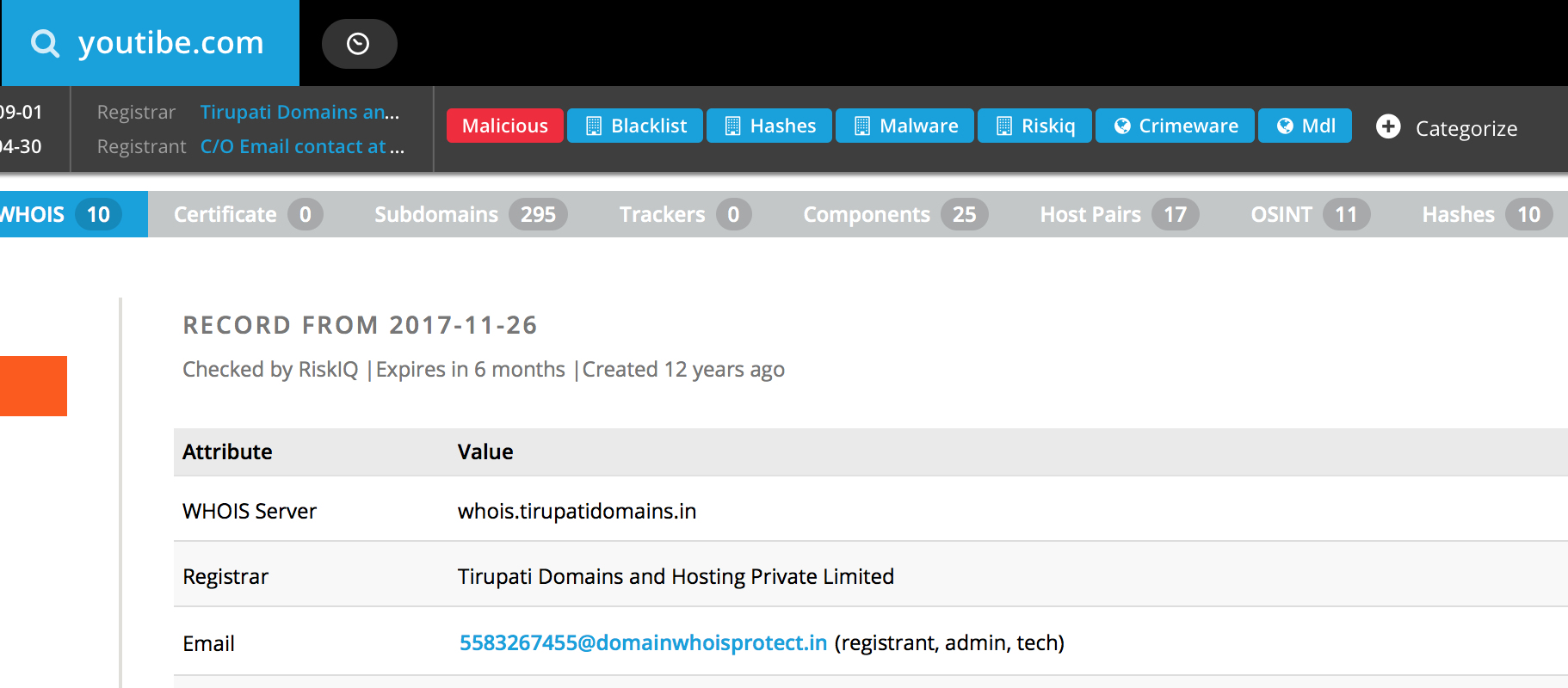
For about five years, we’ve maintained a blacklist of recognized tech support scammers, along with websites and phone numbers they might use to contact victims. The blacklist was part of our Tech support scams: help and resource page, which tells readers how scams work, what tricks to look out for, how to get help after you’ve been scammed, and who to contact to report the scam.
The blacklist was started long before the scale of tech support scamming was understood, and very quickly became unwieldy, hard to search, and, in many cases, outdated. Given the ease with which scammers can stand up low cost infrastructure and switch VOIP numbers on the fly, we decided that a static blacklist is not the best way to share information with other researchers and interested users.
What we’re doing instead
On the Malwarebytes forums, we now have a “Report a Scam” section. (You must be logged in to view it.) After logging in, post any scam number you encounter, along with the URL of the company, if you have it. Posting in the forums makes it much more likely that a researcher will see it and block the scam ASAP.

What if you haven’t been scammed, but still want to help? How do you find scammers to report?
Digging up fake tech support
Loading a typo squat for a large, popular website can be a good starting point to find a browser locker (which leads to a tech support scam). But varying user agents and locations can deliver actual malware instead of a locker, so use this method at your own risk.
It’s a bit safer to start with social media, where scammers spam links for their fake companies. Searching Twitter for “Malwarebytes Support” yields a few tweets like the following:
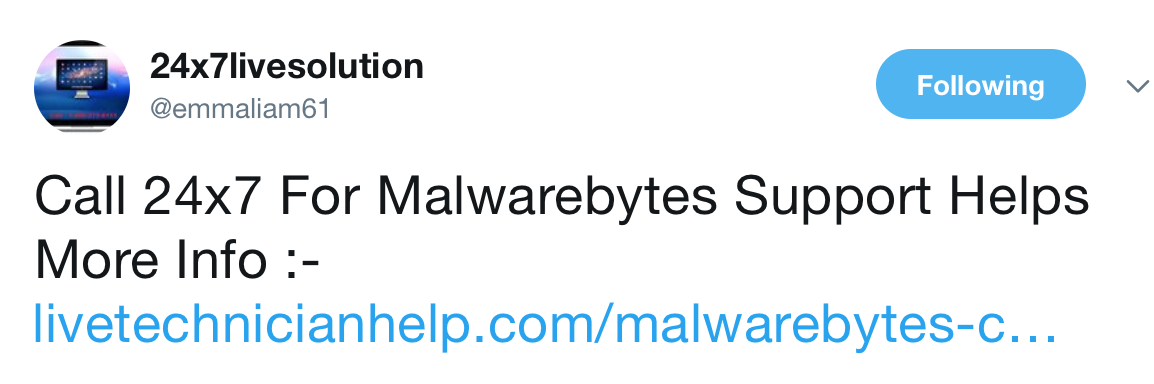
More competent scammers will make use of link shortening services so as to not expose their infrastructure to potential takedown requests. We chose an amateur example for simplicity. (Twitter declined to take down the account when we asked.)
Clicking through yields a convincing scam site:

Now that we’ve got a scam URL and phone number, we can stop there and make a report. Or we can take a look at the website metadata and see if the scammer decided to set up a few alternate sites.
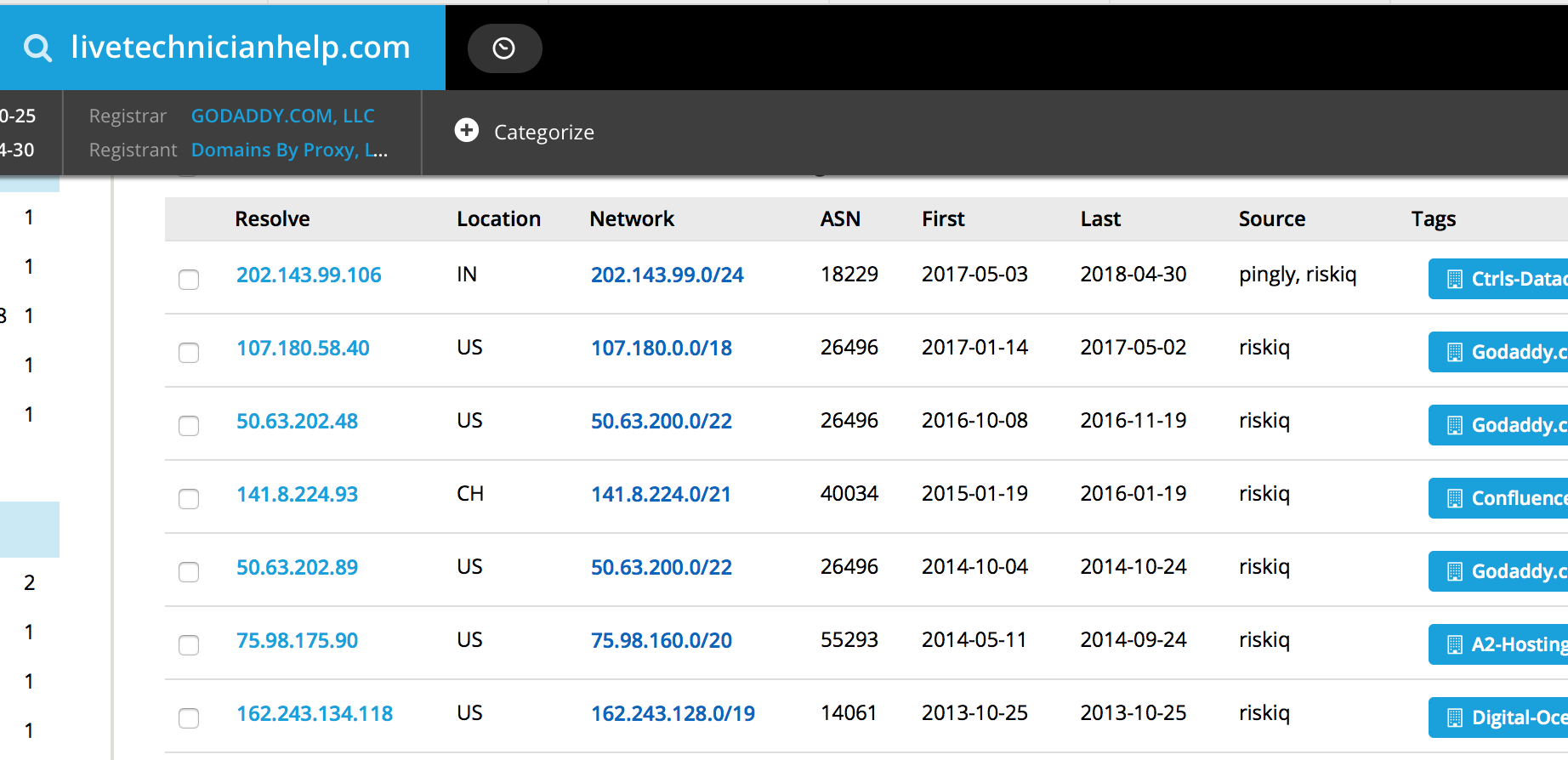
Throwing the latest IP into Passivetotal’s query tool yields a whopping 1,029 domains, including historical hits that are no longer active. Most look to be part of an SEO operation, which makes sense because tech support scammers generally hire third-party SEO services to get their sites in front of victims.
Moving to Hurricane Electric, who provides a free pDNS tool without any historical data, yields the following:
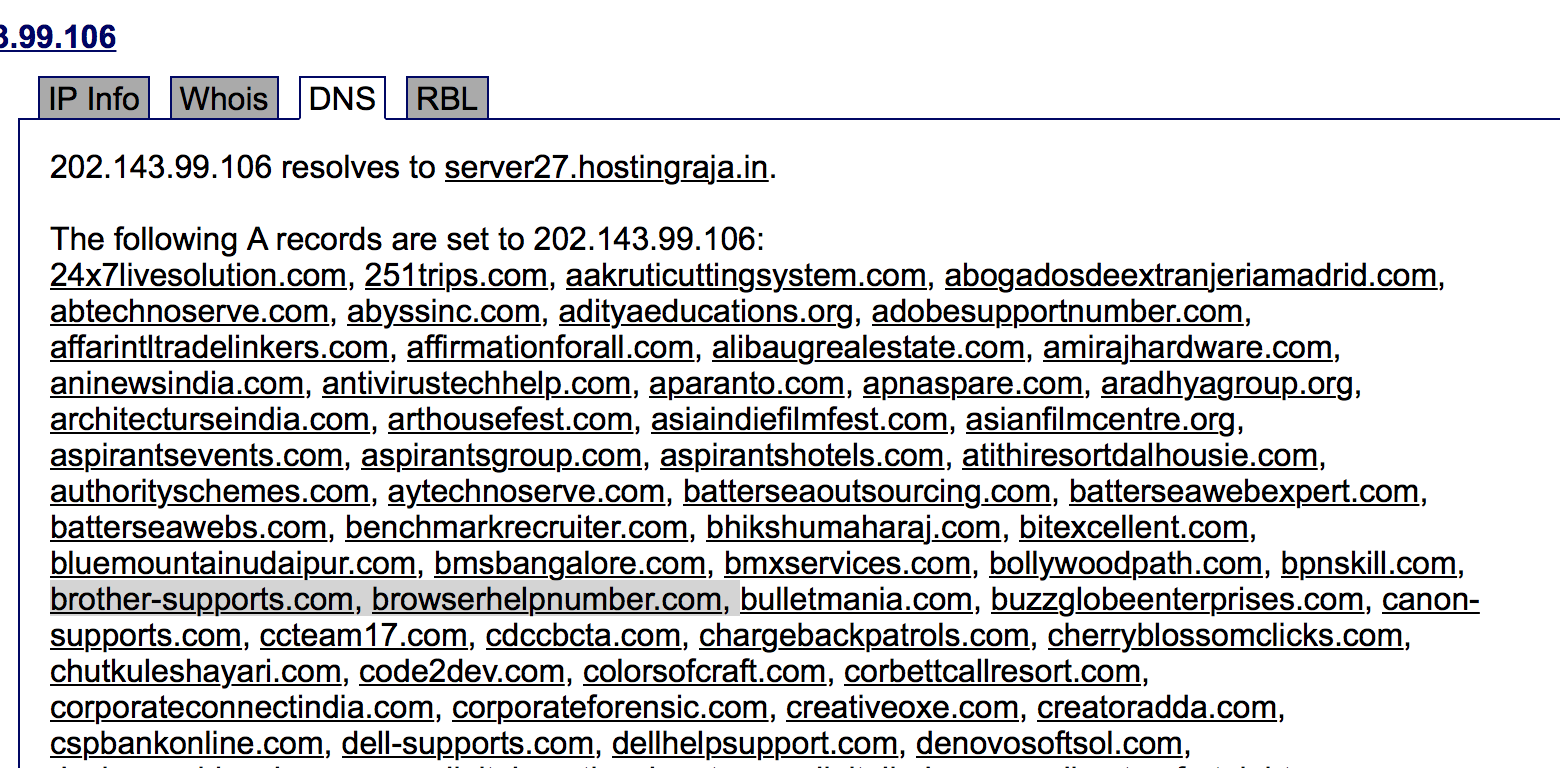
Right away we can see two probable candidates for additional scams. Sifting through pDNS can often improve your scam hunting results, as well as help attribute multiple scams to the same threat actor group. Be sure to actually load the sites to confirm scamming, as legitimate tech companies overseas can sometimes exhibit design cues and domain names similar to fake tech support.
Scam hunting is fun and fairly straightforward. But we can’t be everywhere, and tech support scammers excel at setting up infrastructure with bargain hosting companies quickly. So why not help us get better, and report a scam in our forums? Happy hunting—and stay safe.










