Since our last report on exploit kits, there have been some new developments with the wider adoption of the February Flash zero-day, as well as the inclusion of a new exploit for Internet Explorer. We have not seen that many changes in the drive-by landscape for a long time, although these are the results of improvements closely tied to malspam campaigns and exploits embedded within Microsoft Office.
Since both Flash and the VBScript engine are pieces of software that can be leveraged for web-based attacks, it was only natural to see their integration into exploit kits. While Internet Explorer is not getting any younger, CVE-2018-8174 brings an update to an otherwise 2-year-old vulnerability (CVE-2016-0189), which is still used in some drive-by campaigns. As far as Flash is concerned, CVE-2018-4878 has been adopted by almost all exploits kits. At the time of this writing, a newer Flash vulnerability (CVE-2018-5002) is available but has not been spotted in any EK so far.

RIG
RIG exploit kit remains the most commonly observed EK in the wild, with several different campaigns in action. RIG was the first to include the new VBScript engine exploit (CVE-2018-8174) in IE only days after a Proof of Concept became publicly available, on top of adding CVE-2018-4878. RIG has pushed various payloads such as Bunitu, Ursnif, and the popular SmokeLoader.
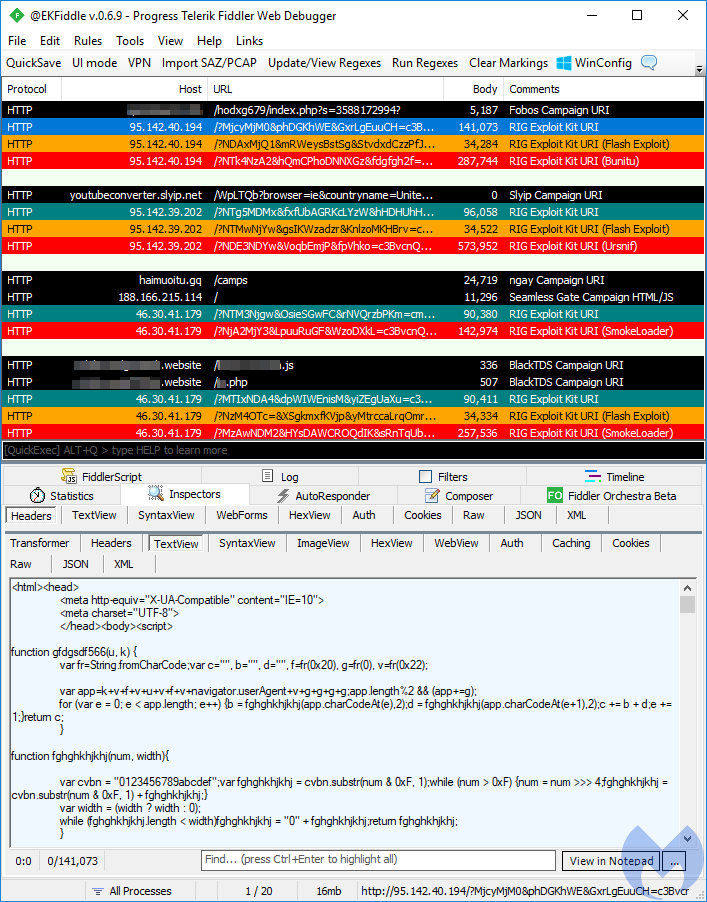
GrandSoft
GrandSoft is an IE-only exploit kit which is observed in a smaller range of distribution campaigns, mostly via malvertising on adult sites. In comparison to its counterparts, GrandSoft is still relying on the older Internet Explorer exploit (CVE-2016-0189) and lacks the obfuscation we normally see in landing pages. Some payloads pushed by GrandSoft include the AZORult stealer.
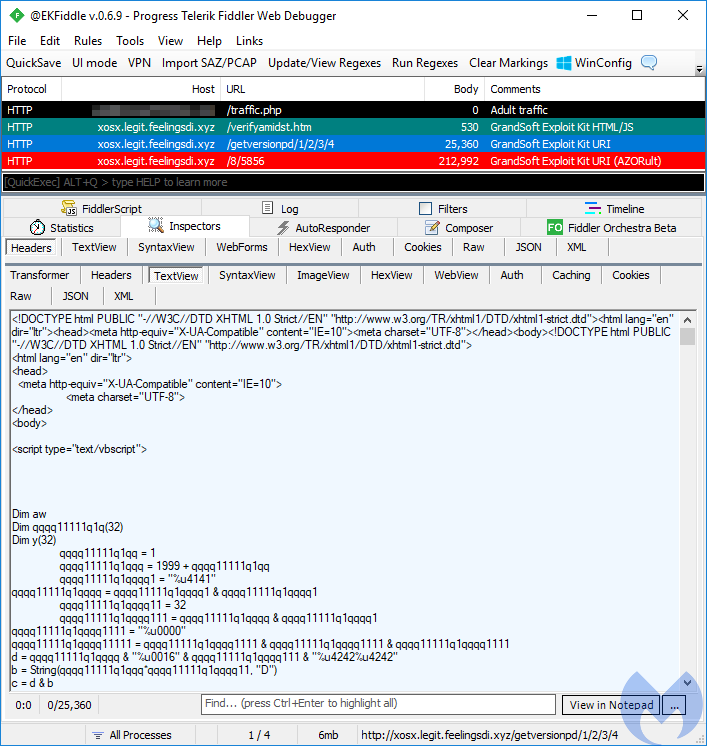
Magnitude
The South Korea–focused exploit kit is back to using its trusted EK Magniber after having a short stint with GandCrab ransomware. Magnitude added Flash (CVE-2018-4878) and went on to integrate IE’s CVE-2018-8174 after a hiatus of about a week with no activity. With its own Magnigate filtering, Base64-encoded landing page and fileless payload, Magnitude is one of the more sophisticated exploit kits on the market.
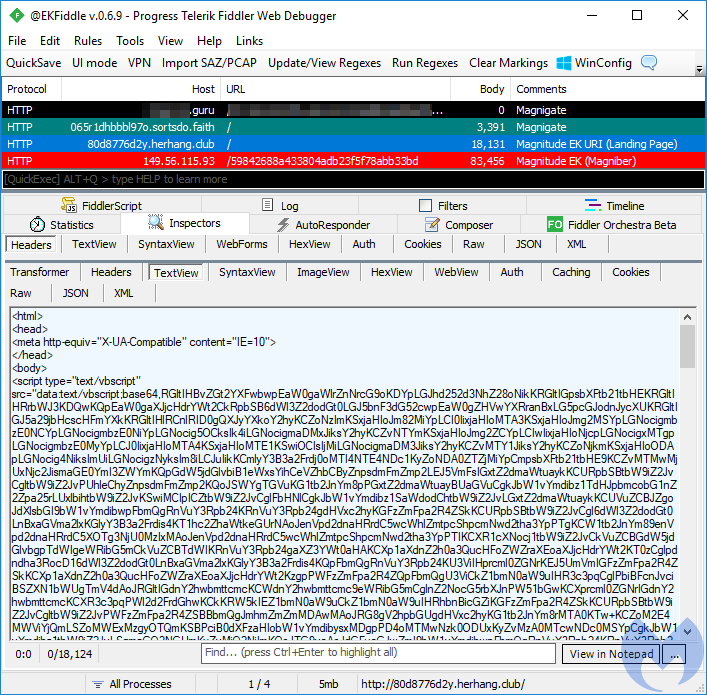
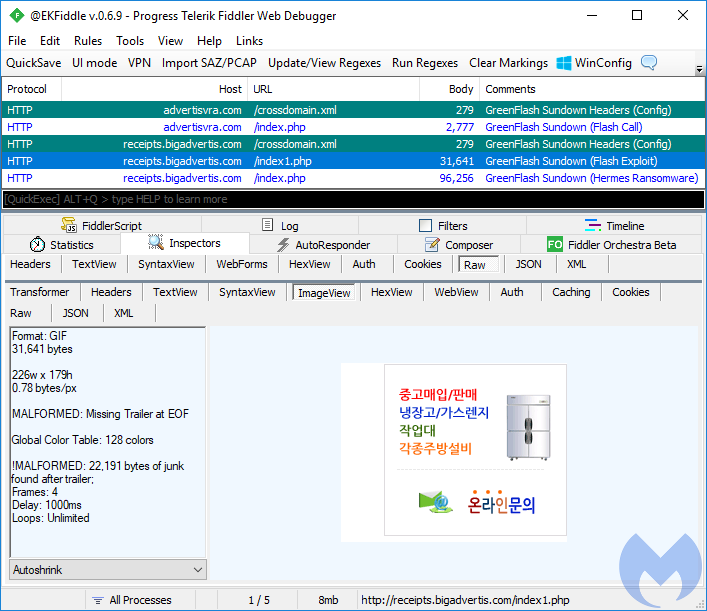
GreenFlash Sundown
The elusive GreenFlash Sundown continues to strike via compromised OpenX ad servers. Although it is usually seen distributing the Hermes ransomware, 360 Total Security observed a cryptocurrency miner via several Chinese websites running a vulnerable OpenX version. The ad banner used by GF Sundown in this attack, as well as some we documented before, is a Korean language picture that hides CVE-2018-4878 using steganography.
A busy 2018
There is no doubt that the recent influx of zero-days has given exploit kits a much-needed boost. We did notice an increase in RIG EK campaigns, which probably resulted in higher than usual successful loads for its operators. While attackers are concentrating on Microsoft Office–related exploits, we are observing a cascading effect into exploit kits.
So far, 2018 has been busier than usual with the discoveries of several directly applicable zero-days, and we can expect to see more in the coming months. For instance, we have already witnessed back-to-back Flash zero-days where attackers are capitalizing on ActionScript vulnerabilities.
Mitigation
We tested these exploit kits against Malwarebytes, and they were all blocked thanks to our signature-less anti-exploit engine:

Hashes for samples referenced in this post:
RIG
8CA1DEDCED7332AEDC94291F8DAA82E0837A1EFC612B581DD13165B29F2A6DBB 21358ACDEB60C456BC36B8E3481BF66CC5F4167D5994F097F71798341B9119FB 560031AC4C947B1E168704CA5E323BF00A801E2320E1F0FFFE08392179D38391 AC1FF2B2A18931C17A5D9D0305CE72CC69C1688DFC2BDF4BF74AA9E27123BFFD
GrandSoft
E659DD280514DD81BF8923315BD503E8781EB8CE7684F4888A838CF2A8B2ADF0
Magnitude (dumped from memory with PE-Sieve)
9491E8B30D37CB3BD0D206021EBE7396CA17BE3C8FBED2AC6DCE89D3CE0CAA27
GreenFlash (dumped from memory with PE-Sieve)
e600dec30c0f5080eab3d15f1210334429c3db0dd6a90f1e755709783ace6e85










