Tim Cotten, a software developer from Washington, DC, was responding to a request for help from a female colleague last week, who believed that her Gmail account has been hacked, when he discovered something phishy. The evidence presented was several emails in her Sent folder, purportedly sent by her to herself.
Cotten was stunned when, upon initial diagnosis, he found that those sent emails didn’t come from her account but from another, which Gmail—being the organized email service that it is—only filed away in her Sent folder. Why would it do that if the email wasn’t from her? It seems that while Google’s filtering and organizing technology worked perfectly, something went wrong when Gmail tried to process the emails’ From fields.
This trick is a treat for phishers
Cotten noted in a blog post that the From header of the emails in his coworker’s Sent folder contained (1) the recipient’s email address and (2) another text—usually a name, possibly for increased believability. The presence of the recipient’s address caused Gmail to move the email to the Sent folder while also disregarding the email address of the actual sender.
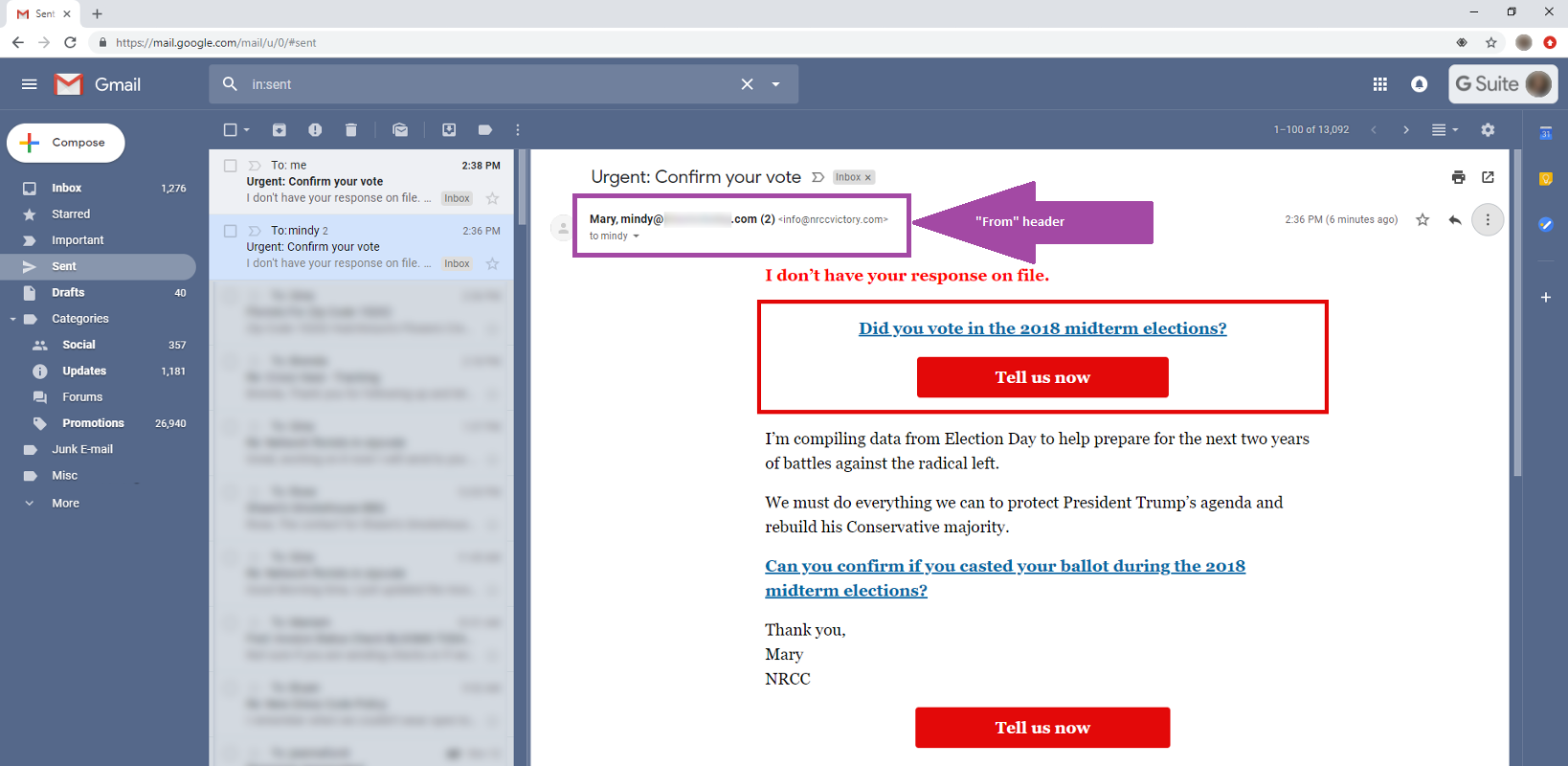
Why would a cybercriminal craft an email that never ends up in a victim’s inbox? This tactic is particularly useful for a phishing campaign that banks on the recipient’s confusion.
“Imagine, for instance, the scenario where a custom email could be crafted that mimics previous emails the sender has legitimately sent out containing various links. A person might, when wanting to remember what the links were, go back into their sent folder to find an example: disaster!” wrote Cotten.
Cotten provided a demo for Bleeping Computer wherein he showed a potentially malicious sender spoofing the From field by displaying a different name to the recipient. This may yield a high turnover of victims if used in a business email compromise (BEC)/CEO fraud campaign, they noted.
After raising an alert about this bug, Cotten unknowingly opened the floodgates for other security researchers to come forward with their discovered Gmail bugs. Eli Grey, for example, shared the discovery of a bug in 2017 that allowed for email spoofing, which has been fixed in the web version of Gmail but remains a flaw in the Android version. One forum commenter claimed that the iOS Mail app also suffers from the same glitch.
Another one stirs the dust
Days after publicly revealing the Gmail bug, Cotten discovered another flaw wherein malicious actors can potentially hide sender details in the From header by forcing Gmail to display a completely blank field.
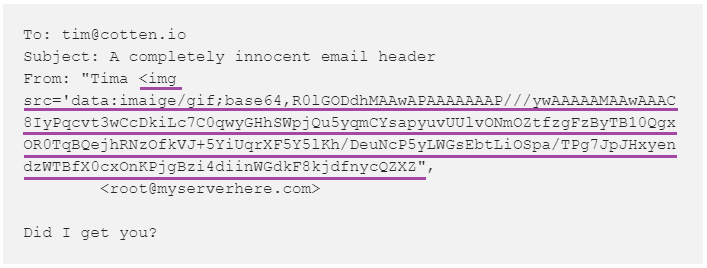
He pulled this off by replacing a portion of his test case with a long and arbitrary code string, as you can see below:
Average Gmail users may struggle to reveal the true sender because clicking the Reply button and the “Show original” option still yields a blank field.
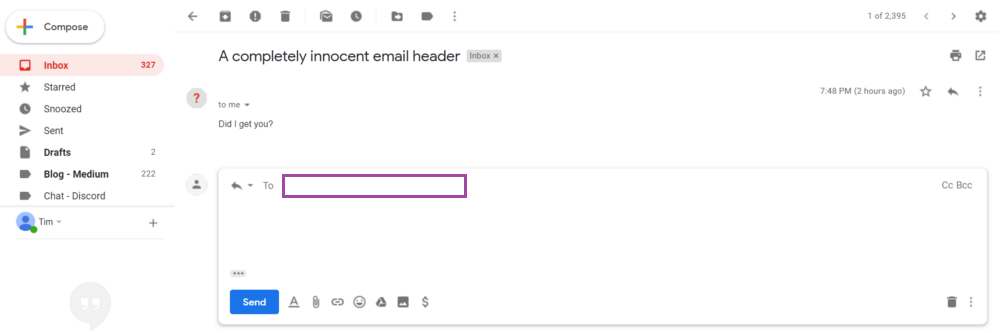
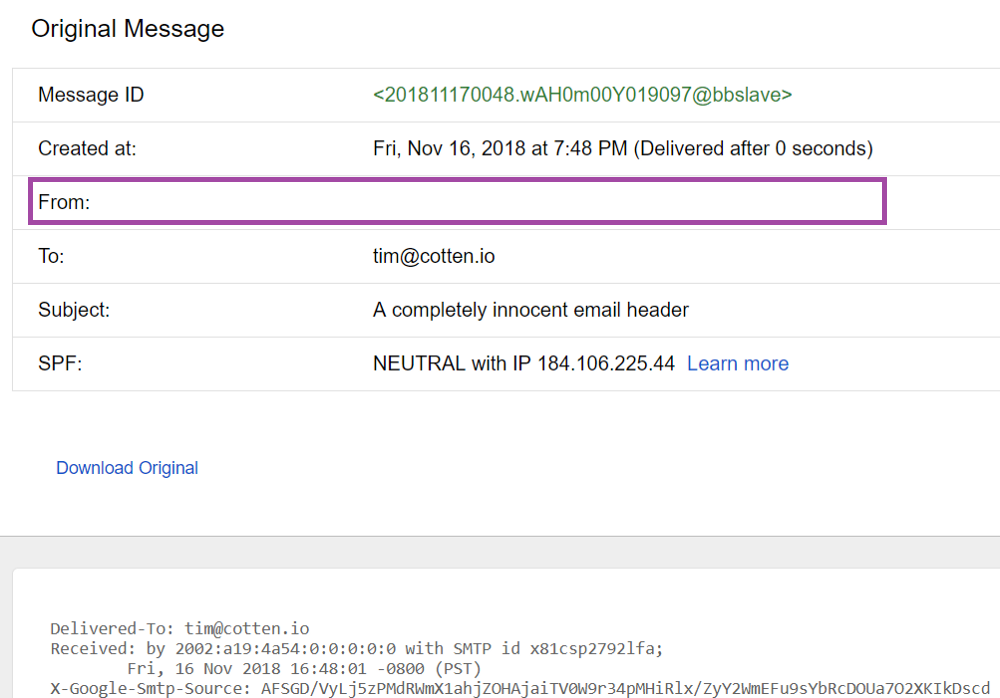
Missing sender details could potentially increase the possibility of users opening a malicious email to click an embedded link or open an attachment, especially if it contains a subject that is both actionable and urgent.
When met with silence
The Gmail vulnerabilities mentioned in this post are all related to user experience (UX), and as of this writing, Google has yet to address them. (Cotten has proposed a possible solution for the tech juggernaut.) Unfortunately, Gmail users can only wait for the fixes.
Spotting phishing attempts or spoofed emails can be tricky, especially when cybercriminals are able to penetrate trusted sources, but a little vigilance can go a long, long way.










