Despite the decline in the number of ransomware infections over the last year, there are several ransomware families that are still active. Ransom.Troldesh, aka Shade, is one of them. According to our product telemetry, Shade has experienced a sharp increase in detections from Q4 2018 to Q1 2019.
When we see a swift spike in detections of a malware family, that tells us we’re in the middle of an active, successful campaign. So let’s take a look at this “shady” ransomware to learn how it spreads, what are its symptoms, why it’s dangerous to your business, and how you can protect against it.
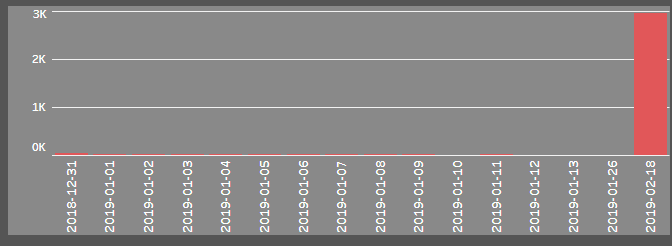
Troldesh spiked in February 2019
Infection vector
Troldesh, which has been around since 2014, is typically spread by malspam—specifically malicious email attachments. The attachments are usually zip files presented to the receiver as something he “has to” open quickly. The extracted zip is a Javascript that downloads the malicious payload (aka the ransomware itself). The payload is often hosted on sites with a compromised Content Management System (CMS).
Part of the obfuscated Troldesh Javascript
As the sender in Troldesh emails is commonly spoofed, we can surmise that the threat actors behind this campaign are phishing, hoping to pull the wool over users’ eyes in order to get them to open the attachment.
The origin of Troldesh is believed to be Russian because its ransom notes are written in both Russian and English.
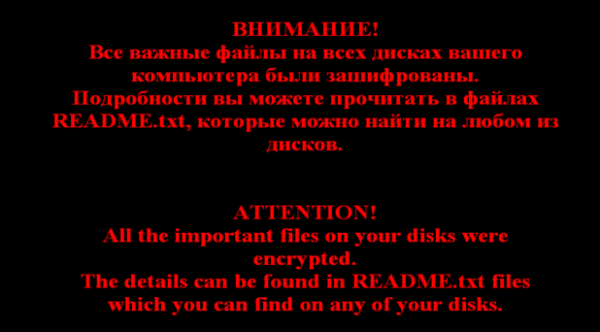
Target systems are running Windows OS. Victims will have to unzip the attachment and double-click the Javascript file to get the infection started.
Ransomware behavior
Once deployed, the ransomware drops a lot of numbered readme#.txt files on the infected computer after the encryption routine is complete, most likely to make sure that the victim will read at least one of them. These text files contain the same message as the ransom note.
Targeted file extensions
Troldesh looks for files with these extensions on fixed, removable, and remote drives:
.1cd, .3ds, .3fr, .3g2, .3gp, .7z, .accda, .accdb, .accdc, .accde, .accdt, .accdw, .adb, .adp, .ai, .ai3, .ai4, .ai5, .ai6, .ai7, .ai8, .anim, .arw, .as, .asa, .asc, .ascx, .asm, .asmx, .asp, .aspx, .asr, .asx, .avi, .avs, .backup, .bak, .bay, .bd, .bin, .bmp, .bz2, .c, .cdr, .cer, .cf, .cfc, .cfm, .cfml, .cfu, .chm, .cin, .class, .clx, .config, .cpp, .cr2, .crt, .crw, .cs, .css, .csv, .cub, .dae, .dat, .db, .dbf, .dbx, .dc3, .dcm, .dcr, .der, .dib, .dic, .dif, .divx, .djvu, .dng, .doc, .docm, .docx, .dot, .dotm, .dotx, .dpx, .dqy, .dsn, .dt, .dtd, .dwg, .dwt, .dx, .dxf, .edml, .efd, .elf, .emf, .emz, .epf, .eps, .epsf, .epsp, .erf, .exr, .f4v, .fido, .flm, .flv, .frm, .fxg, .geo, .gif, .grs, .gz, .h, .hdr, .hpp, .hta, .htc, .htm, .html, .icb, .ics, .iff, .inc, .indd, .ini, .iqy, .j2c, .j2k, .java, .jp2, .jpc, .jpe, .jpeg, , .jpf, .jpg, .jpx, .js, .jsf, .json, .jsp, .kdc, .kmz, .kwm, .lasso, .lbi, .lgf, .lgp, .log, .m1v, .m4a, .m4v, .max, .md, .mda, .mdb, .mde, .mdf, .mdw, .mef, .mft, .mfw, .mht, .mhtml, .mka, .mkidx, .mkv, .mos, .mov, .mp3, .mp4, .mpeg, .mpg, .mpv, .mrw, .msg, .mxl, .myd, .myi, .nef, .nrw, .obj, .odb, .odc, .odm, .odp, .ods, .oft, .one, .onepkg, .onetoc2, .opt, .oqy, .orf, .p12, .p7b, .p7c, .pam, .pbm, .pct, .pcx, .pdd, .pdf, .pdp, .pef, .pem, .pff, .pfm, .pfx, .pgm, .php, .php3, .php4, .php5, .phtml, .pict, .pl, .pls, .pm, .png, .pnm, .pot, .potm, .potx, .ppa, .ppam, .ppm, .pps, .ppsm, .ppt, .pptm, .pptx, .prn, .ps, .psb, .psd, .pst, .ptx, .pub, .pwm, .pxr, .py, .qt, .r3d, .raf, .rar, .raw, .rdf, .rgbe, .rle, .rqy, .rss, .rtf, .rw2, .rwl, .safe, .sct, .sdpx, .shtm, .shtml, .slk, .sln, .sql, .sr2, .srf, .srw, .ssi, .st, .stm, .svg, .svgz, .swf, .tab, .tar, .tbb, .tbi, .tbk, .tdi, .tga, .thmx, .tif, .tiff, .tld, .torrent, .tpl, .txt, .u3d, .udl, .uxdc, .vb, .vbs, .vcs, .vda, .vdr, .vdw, .vdx, .vrp, .vsd, .vss, .vst, .vsw, .vsx, .vtm, .vtml, .vtx, .wb2, .wav, .wbm, .wbmp, .wim, .wmf, .wml, .wmv, .wpd, .wps, .x3f, .xl, .xla, .xlam, .xlk, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xps, .xsd, .xsf, .xsl, .xslt, .xsn, .xtp, .xtp2, .xyze, .xz, and .zip
Encryption
Files are encrypted using AES 256 in CBC mode. For each encrypted file, two random 256-bit AES keys are generated: One is used to encrypt the file’s contents, while the other is used to encrypt the file name. The extensions mentioned above are added after the encryption of the filename.
Protect against Troldesh
Malwarebytes users can block Ransom.Troldesh through several different protection modules, which are able to stop the ransomware from encrypting files in real time.
Real-time protection against the files in our definitions stops the ransomware itself:
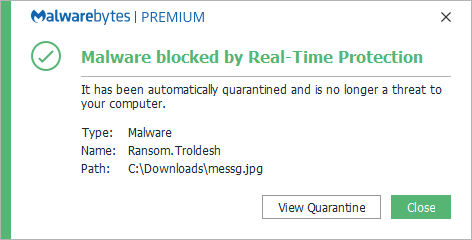
Our anti-exploit and anti-ransomware modules block suspicious behavior:
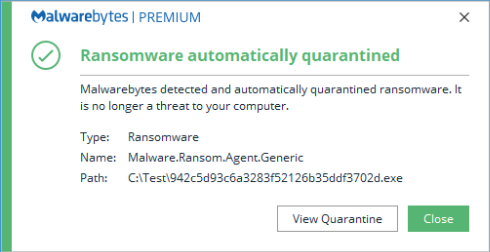
Meanwhile, Malwarebytes’ malicious website protection blocks compromised sites:
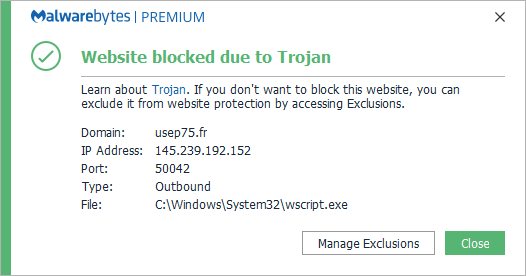
Other methods of protection
There are some security measures you can take to avoid getting to the phase where protection has to kick in or files need to be recovered.
- Scan emails with attachments. These suspicious mails should not reach the end user.
- User education. If they do reach the end user, they should be informed not to open attachments of this nature or run executable files in attachments. In addition, if your company has an anti-phishing plan, they should know who to forward the email to in the organization for investigation.
- Blacklisting. Most end users do not need to be able to run scripts. In those cases, you can blacklist wscript.exe.
- Update software and systems. Updating software can plug up vulnerabilities and keep known exploits at bay.
- Back up files. Reliable and easy-to-deploy backups can shorten the recovery time.
Remediation
If you should get to the point where remediation is necessary, these are the steps to follow:
- Perform a full system scan. Malwarebytes can detect and remove Ransom.Troldesh without further user interaction.
- Recover files. Removing Troldesh does not decrypt your files. You can only get your files back from backups you made before the infection happened or by performing a roll-back operation.
- Get rid of the culprit. Delete the email that was the root cause.
Decryption
Even though AES 256 is a strong encryption algorithm, there are free decryption tools available for some of the Troldesh variants. You can find out more about these decryption tools at NoMoreRansom.org (look under “Shade” in the alphabetical list).
Victims of Troldesh are provided with a unique code, an email address, and a URL to an onion address. They are asked to contact the email address mentioning their code or go to the onion site for further instructions. It is not recommended to pay the ransom authors, as you will be financing their next wave of attacks.
What sets Troldesh apart from other ransomware variants is the huge number of readme#.txt files with the ransom note dropped on the affected system, and the contact by email with the threat actor. Otherwise, it employs a classic attack vector that relies heavily on tricking uninformed victims. Nevertheless, it has been quite successful in the past, and in its current wave of attacks. The free decryptors that are available only work on a few of the older variants, so victims will likely have to rely on backups or roll-back features.
IOCs
Ransom.Troldesh has used the following extensions for encrypted files:
.xtbl .ytbl .cbtl .no_more_ransom .better_call_saul .breaking_bad .heisenberg .da_vinci_code .magic_software_syndicate .windows10 .crypted000007 .crypted000078 Contacts: Novikov.Vavila@gmail.com Selenadymond@gmail.com RobertaMacDonald1994@gmail.com IPs TCP 154.35.32.5 443 outgoing Bitcoin: 1Q1FJJyFdLwPt5yyZAQ8kfxfeWq8eoD25E Domain : cryptsen7fo43rr6.onion











