Researchers at Sucuriinvestigated a number of WordPress websites complaining about unwanted redirects and found websites that use fake CAPTCHA forms to get the visitor to accept web push notifications.
These websites are a new wave of a campaign that leverages many compromised WordPress sites.
CAPTCHA
CAPTCHA (“Completely Automated Public Turing test to tell Computers and Humans Apart”) is one of the annoyances that we have learned to take for granted when we browse the Internet. Scientists developed CAPTCHA as a method to tell humans and bots apart so as to to keep bots from accessing sites or systems where they are not welcome.
Google bought and owns reCAPTCHA, which represents a CAPTCHA system expressly developed to reduce the needed amount of user interaction. The original version asked users to decipher hard to read text or match images. Version 2 required users to decipher text or match images if the analysis of cookies and canvas rendering suggested an automatic download of the page. Since version 3, reCAPTCHA doesn’t interrupt users, running automatically when users load pages or click buttons.
The basic version of a real reCAPTCHA the threat actors used as a template to create the fake ones looks like this:
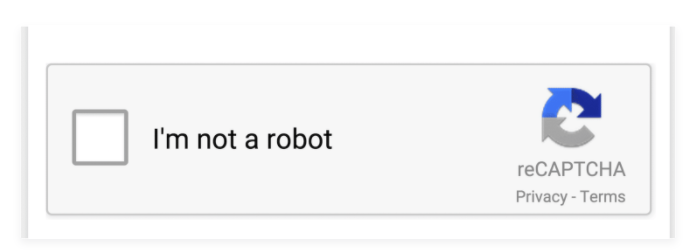
The campaign
The fake CAPTCHA sites are part of a long lasting campaign responsible for injecting malicious scripts into compromised WordPress websites. This campaign leverages known vulnerabilities in WordPress themes and plugins and has impacted an enormous number of websites over the years.
The compromised websites all share a common issue. The threat actors injected malicious JavaScript within the affected website’s files and database. Attackers attempted to automatically infect any .js file with jQuery in the name, on a compromised website. They then injected obfuscated code when successful. This malicious JavaScript was appended under the current script or under the head of the page where it was fired on every page load, redirecting site visitors to the destination chosen by the threat actor.
The Malwarebytes Threat Intelligence Team tracked a rogue affiliate’s traffic which flowed through the same local[.]drakefollow[.]comsubdomain that was mentioned in the Sucuri blog. The threat actor chose to promote a legitimate security product in this case, but might as well have led visitors to potentially unwanted programs (PUPs), adware, or tech support scams.
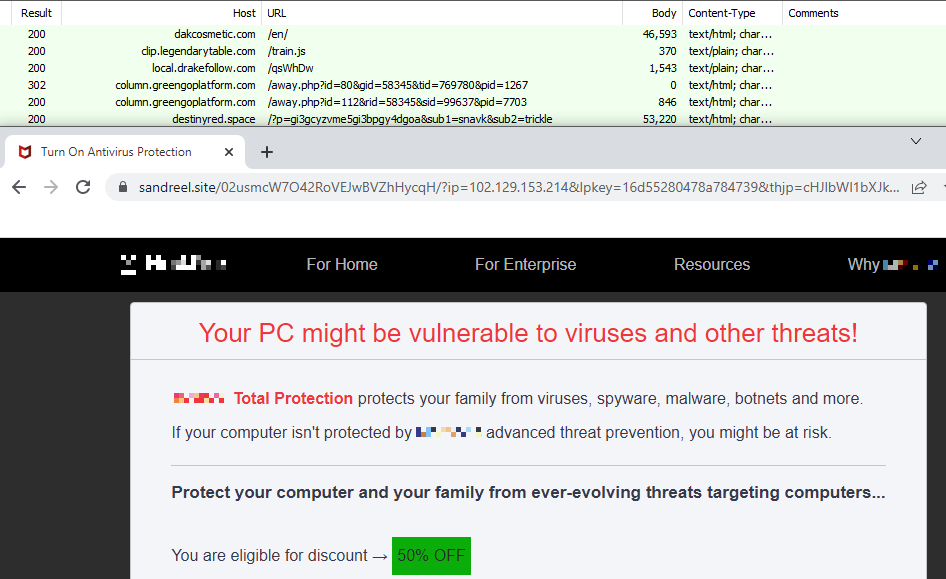
The fake CAPTCHA
At this point in the chain of redirections, the fake reCAPTCHA websites kick in. The fake reCAPTCHA sites are the final step towards duping the visitor. The unsuspecting visitor will land on a site that tries to trick them into accepting push notifications from the landing page’s domain.
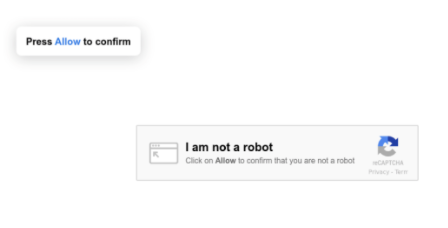
Visitors think they need to click “Allow” to get past the CAPTCHA screen, when in fact they are giving permission to the domain to send them push notifications.
By design, push notifications work similarly across different operating systems and web browsers. They appear outside of the browser window just above the taskbar on the right hand side. This is misleading as they may seem to originate from the operating system. Knowing the difference between a web push notification and an alert that comes from the operating system or another program installed on the device is hard, and that makes it difficult for the unsuspecting user of an affected system to know what is going on.
As we reportedin the past, adware, search hijackers, and PUP families have added push notifications as one of their attack vectors. Sucuri warns that it is also one of the most common ways attackers display “tech support” scams, where users are told their computer is infected or slow and they should call a toll-free number to fix the problem.
Removal and mitigation
Knowing that these fake reCAPTCHA sites exist and being able to spot the difference with a real one is your best protection. Also, many security programs, including Malwarebytes, will block access to the campaign’s domains.
If your system shows you push notifications, you can find detailed instructions on how to disable and remove permissions for browser push notifications in our article: Browser push notifications: a feature asking to be abused.
Website owners can use Sucuri’s free remote website scannerto detect the malware.
Stay safe, everyone!
Special thanks to the Malwarebytes Threat Intelligence Teamfor their contribution and the screenshot











