AMD is investigating the claim that the RansomHouse extortion group has its hands on more than 450GB of the company’s data.
AMD’s breach revelation came to light after RansomHouse teased on Telegram about selling data belonging to a popular ‘three-letter company that starts with the letter ‘A’. The event crescendoed with the addition of AMD to the group’s data leak site.
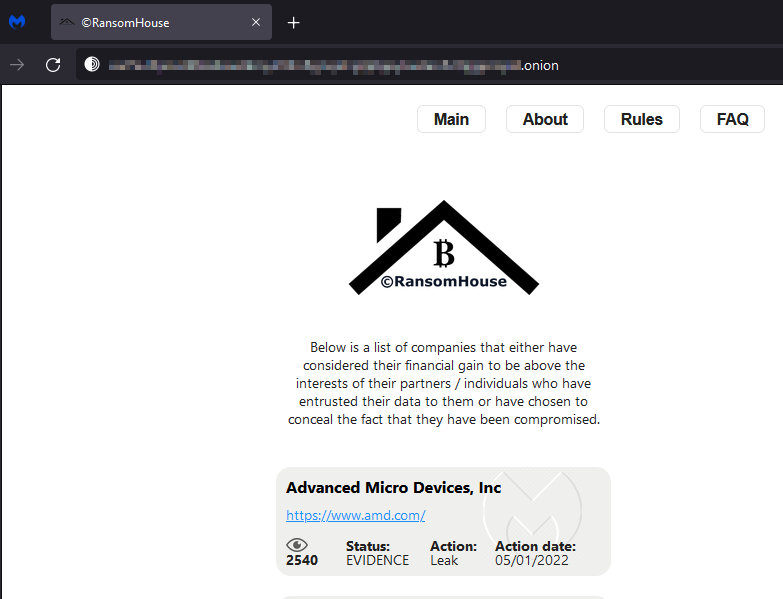
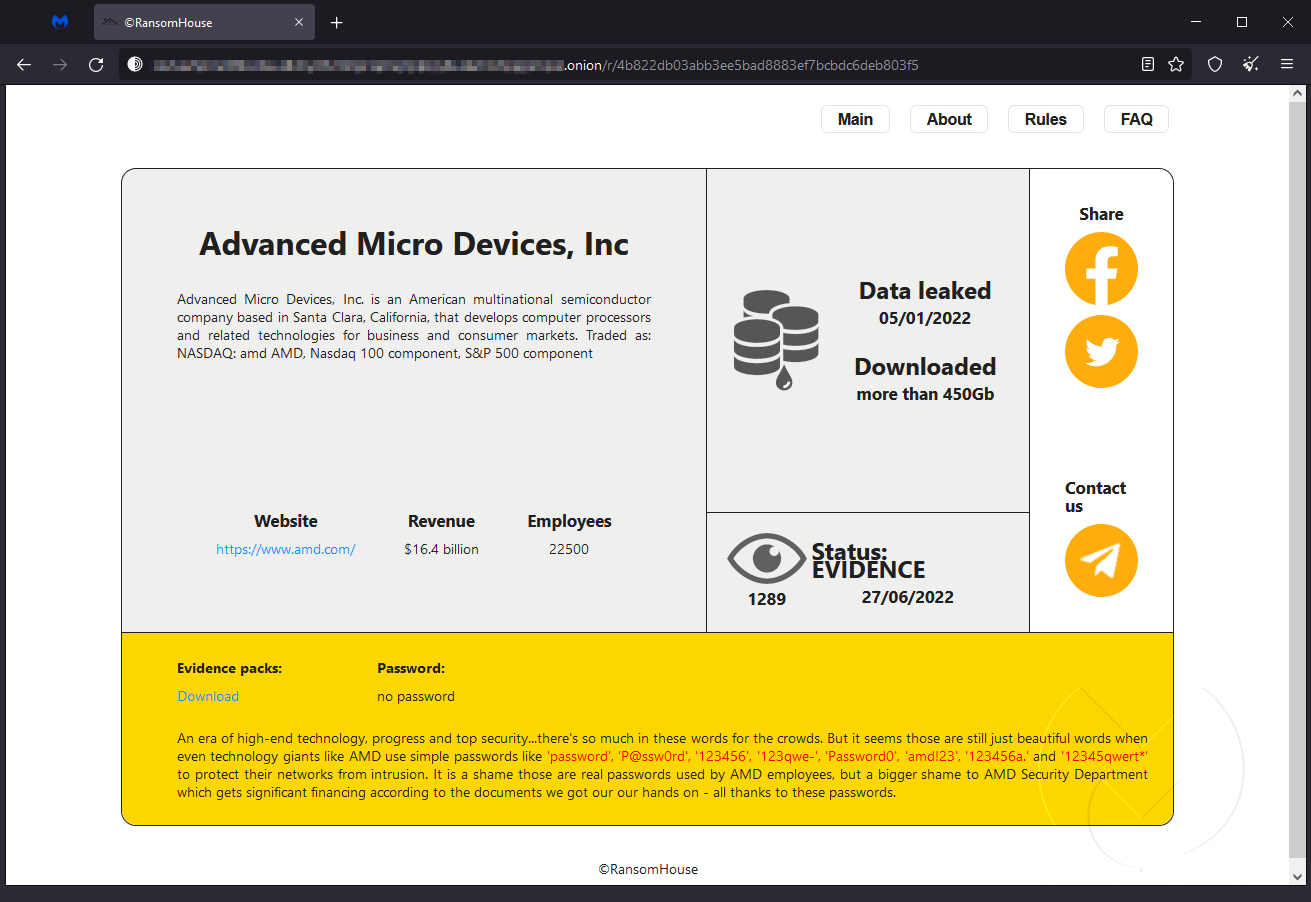
RansomHouse didn’t breach AMD, although it was once linked to such activity. The group revealed to BleepingComputer that its “partners” breached AMD’s network a year ago. Those partners are said to no longer have access to AMD’s network.
The extortion group didn’t bother informing the graphics drive company, thinking it was a “waste of time.”
“[I]t will be more worth it to sell the data rather then wait for AMD representatives to react with a lot of bureaucracy involved.”
The group hasn’t provided any substantial evidence of files belonging to AMD. Still, it claims the stolen data contains research, financial information, a list of 70,000 devices in AMD’s internal network, and alleged employee credentials, showcasing a collection of embarrassingly weak passwords. Some of these are ‘password’, ‘P@ssw0rd’, ‘amd!23’, and ‘Welcome1.’
The use of bad passwords is the reason why AMD got compromised, the extortion group said.
RansomHouse is a group-on-a-mission. As long as businesses have weaknesses in places—may these be passwords or in the software they use—expect a very quiet knock on the door when everyone is paying the slightest attention.
It’s never too late to extinguish weak passwords and tighten up the perimeter around accounts. Companies can start off by:
- Using a password manager. This tool creates complicated passwords and remembers them for you as well.
- Requiring two-factor authentication (2FA) for highly sensitive resource repositories and administrator accounts.
- Stressing the importance of not reusing a password. It’s so easy for an attacker to use a password breached on one site to get in to another, if the login credentials are the same. Stopping password reuse makes things much more difficult for them.
Good luck!