In May of 2021, education underwent a siege of exploit attempts using the vulnerability CVE-2021-21551, which exploits a Dell system driver bug and helps attackers to gain access to a network. Considering that many schools across the United States use Dell hardware, it’s understandable to see such a large amount of this exploit.
In fact, both Rockland Schools in Massachusetts and Visalia USD in California were hit with ransomware attacks during this period. The states that detected this threat the most were Minnesota and Michigan, with Detroit being the biggest target in the US.
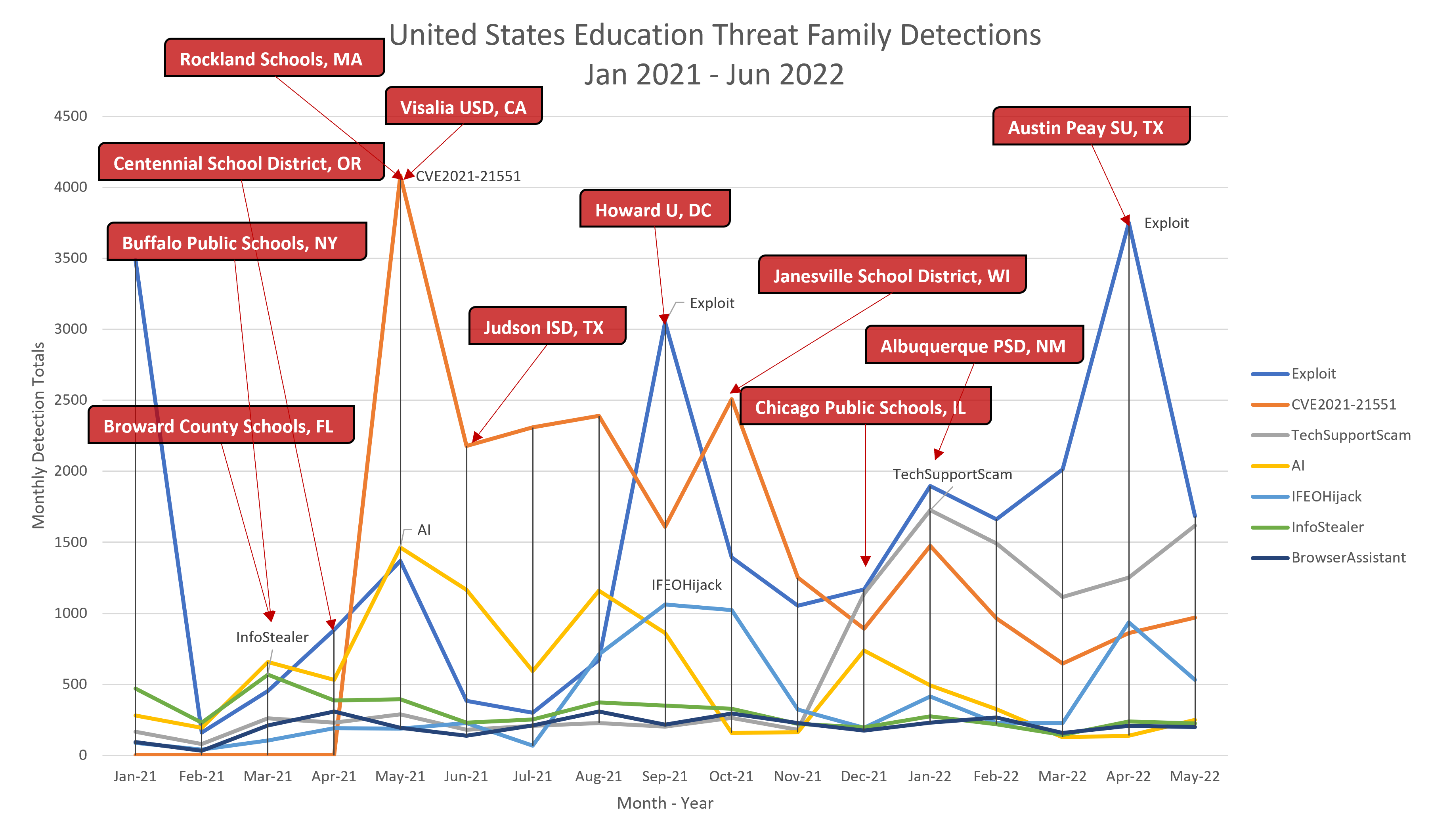
In September of 2021, there was a spike of the malicious setting, RiskwareTool.IFEOHijack, with detections having increased from July 2021 onward. This threat is flagged when malware modifies a registry setting that changes the default Windows debugger to a malware executable. It is a red flag that needs to be investigated immediately. Unfortunately, it doesn’t pinpoint which malware made the modification, but the increased presence of this threat, especially in Oklahoma and Washington State, calls for deeper threat hunting on the victims’ networks. During the same period, a spike in exploit detections was observed and Howard University was breached.
The Trojan TechSupportScam covers an array of applications all designed to fool users into calling a “tech support” number to solve a problem created by the application, such as a blue screen, error message, activation alert, etc. These tools started spiking in January of 2022. Educational institutions in New Jersey have had to deal with this threat more than any other state, however the public school district of Albuquerque, NM suffered a breach during the same month that could have been influenced by this spike in scams. Students and staff likely encountered these threats when installing risky software and/or visiting shady sites.
Finally, Pennsylvania schools have been dealing with an active campaign of backdoors, specifically QBot, since March of 2022, which will likely result in greater infections during the rest of 2022.
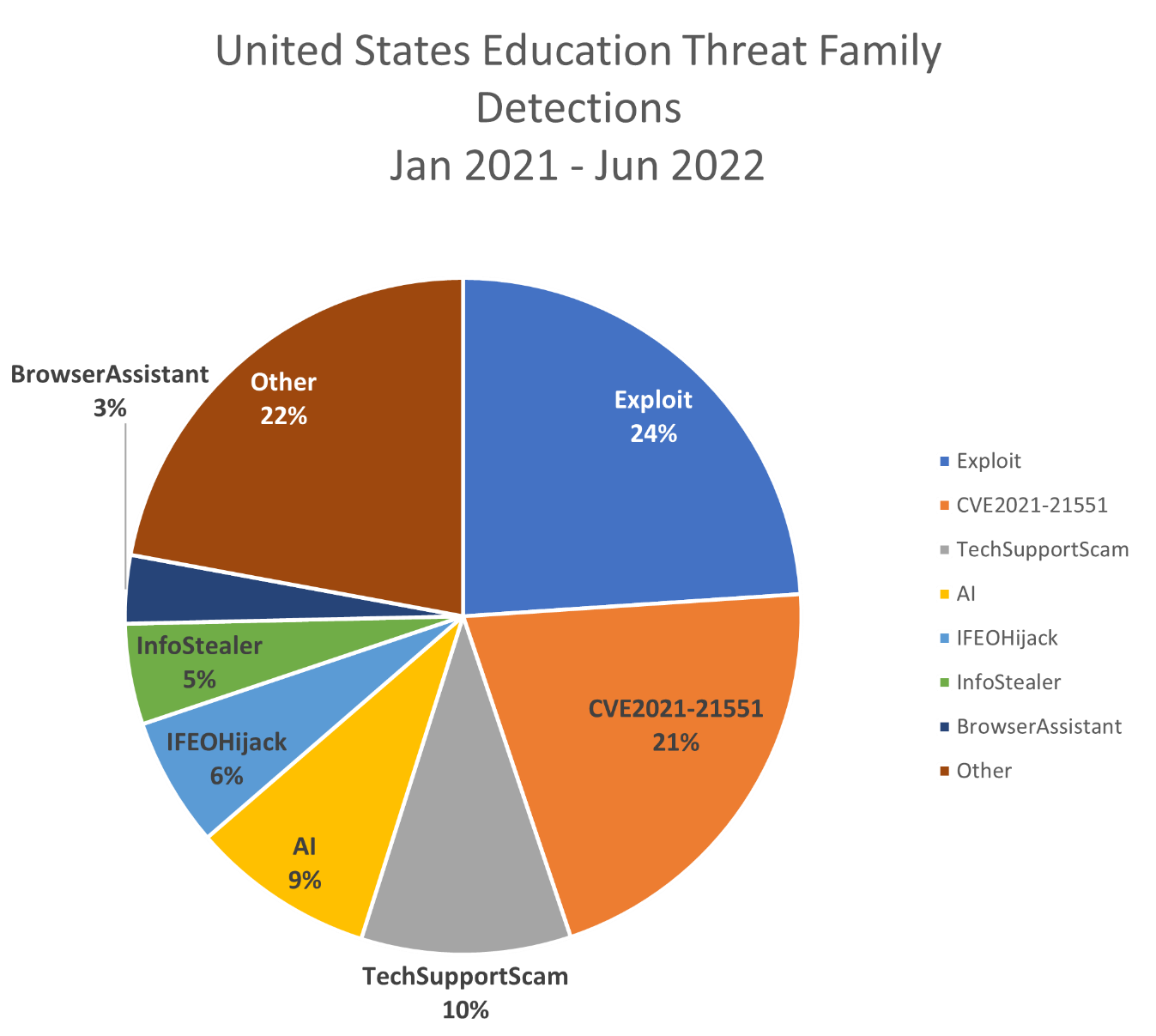
Beyond spikes in detections, the education sector has dealt with an onslaught of attacks ranging from spyware and denial of service tools to ransomware. Throughout the year, almost every month has a report of an educational institution under attack. The first half of 2021 saw attacks against schools in Florida, New York, Oregon, Massachusetts, and California, while the second half saw attacks against Texas, Washington D.C., Wisconsin, and Illinois. The biggest attack of 2022, so far, would be the breach of Austin Peay State University in April, though time will tell if that remains true.
The education industry has the largest userbase out of all industries, considering the constant rotation of students and faculty. Therefore, the greatest threat to these organizations are the users themselves, who may download their own applications, visit dangerous websites, and even make system modifications to get around monitoring tools.
Recommendations for education
Our recommendation for this sector includes keeping an eye out for all new exploits that might affect your organization, especially commonly used systems. In a lot of cases, organizations may have a difficult time updating quickly, because of operational needs, but in the case of schools, a single vulnerability might be duplicated across 99% of its endpoints, which turns each of those systems into backdoors for the bad guys. So, making vulnerability patching one of the highest priorities will reduce attacks and decrease malicious file installation.
Next, systems that have been infected may leave behind artifacts of its operations, for example the IFEOHijack registry setting. Additionally, threats that may be installed on day one, might not activate until a user does something specific, or a certain date comes around, allowing the threat to hide in the meantime. To combat this threat, consider creating a secure, default system image that can be easily duplicated to endpoints, returning them to a default state. While this is likely already done by many schools every year, consider increasing the frequency to every quarter, maybe even every month, and have students save their files on cloud-based storage solutions.
By utilizing a default image, an organization can erase hidden malware, reset modified settings, and provide confidence in quickly isolating or wiping out an infected system. For the education industry, it’s not so much about what threats are actively targeting schools, but rather what threats have been left behind, that open doors for other, future attacks.











