In a public announcement, Free Download Manager has acknowledged that a specific web page on its site was compromised by a Ukrainian cybercrime group, exploiting it to distribute malware.
Free Download Manager is—unsurprisingly—a download manager for Windows, macOS, Android, and Linux that allows users to manage their downloads and lets them grab large files, torrents, music, and videos.
In the announcement the service says the actual security incident took place in 2020. So why was the issue only recently discovered?
First and foremost, the cybercriminals only redirected users that aimed for the Linux version of the software.
Not all of these visitors were redirected to the malicious domain. They were “fingerprinted” based on as yet unknown criteria and only some were served the malicious Debian package. According to Free Download Manager the compromised website contained an exception list of IP addresses from various subnets, including those associated with Bing and Google. Visitors from these IP addresses were always given the correct download link.
Furthermore, the victims received a full functional Free Download Manger, so they had no reason to assume that something was amiss, even though some users reported errors that said “Waiting for process: crond” when they tried to shut down or reboot their system.
According to the statement made by Free Download Manager:
“It’s estimated that much less than 0.1% of our visitors might have encountered this issue.”
The number of victims might even have been less, if it weren’t for the fact that several posts on social media, Reddit, StackOverflow, YouTube, and Unix Stack Exchange, pointed to the malicious domain as a reliable source for getting the Free Download Manager tool.
Unfortunately, malware scanners for Linux are considered useless by many home users, and only some companies add them to their endpoint security solution. So, there is not much overlap to be expected between the users of Free Download Manager and those that have deployed an anti-malware solution for Linux systems.
Debian packages are typically used to install software on Debian-based Linux distributions, including Ubuntu. The malicious package dropped an information-stealing script and a crond backdoor that established a reverse shell from the C2 server. Crond is a daemon used to execute cron jobs in the background. It is a service process that handles and executes commands to run automated tasks (cron jobs) in accordance with a specified schedule.
The stealer in question was after system information, browsing history, saved passwords, cryptocurrency wallet files, as well as credentials for cloud services (AWS, Google Cloud, Oracle Cloud Infrastructure, Azure).
Remediation
The compromised Free Download Manager website has been replaced. All the Free Download Manager users who downloaded FDM for Linux between 2020 and 2022 should scan their computers for malware.
Malwarebytes Browser Guard users will receive a warning when they try to visit this domain.
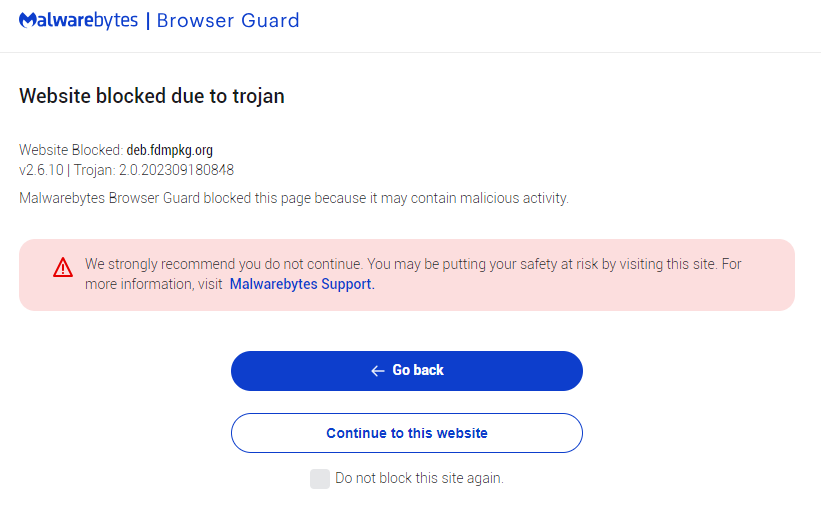
Browser Guard blocks fdmpkg.org
Indicators of Compromise (IOCs):
File hashes (SHA-256):
b77f63f14d0b2bde3f4f62f4323aad87194da11d71c117a487e18ff3f2cd468d
2214c7a0256f07ce7b7aab8f61ef9cbaff10a456c8b9f2a97d8f713abd660349
93358bfb6ee0caced889e94cd82f6f417965087203ca9a5fce8dc7f6e1b8a3ea
d73be6e13732d365412d71791e5eb1096c7bb13d6f7fd533d8c04392ca0b69b5
File locations:
/etc/cron.d/collect
/var/tmp/crond
/var/tmp/bs
/var/tmp/atd
IP and domain:
172.111.48.101
fdmpkg.org
Malwarebytes EDR and MDR removes all remnants of ransomware and prevents you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.











