For more than a month, Malwarebytes has worked with advocacy groups, law enforcement, and cybersecurity researchers to deliver helpful information in fighting stalkerware—the disturbing cyber threat that enables domestic abusers to spy on their partners’ digital and physical lives.
While we’ve ramped up our detections, written a safety guide for those who might have stalkerware on their devices, and analyzed the technical symptoms of stalkerware, we wanted to take a few steps back.
Many individuals need help before stalkerware even strikes. They need help with the basics, like how to protect a device from an abuser, how to secure sensitive data on a device, and how to keep their private conversations private.
At the end of July, we presented on data and device security to more than 150 audience-members at the National Network to End Domestic Violence’s Technology Summit. Malwarebytes broke down several simple, actionable device guidelines for domestic abuse survivors.
Let’s take a look.
Device security
Similar to our guide for domestic abuse survivors who suspected stalkerware was implanted on their devices, the following safety tips are options—not every tip can be used by every survivor. The survivor who just escaped their home has different options available to them than the survivor who still lives with their partner, or the survivor being supported at a domestic abuse shelter’s safe house.
Taken together, we hope these guidelines will give individuals the information they need to stay safe in the ways that help them most.
Create and use a device passcode
A device passcode is the first line of defense in device security. With it, you can prevent unwanted third parties from rummaging through your apps, reading your notes, viewing your messages and emails, and looking through your search history. It’s simple, it’s effective, and it’s available on nearly every single modern smart device available today.
When creating a passcode, create a string of at least six numbers that have no immediate connection to you. That way, another person can’t guess your passcode by inputting a few important numbers, like your birthdate, your zip code, or select digits from your phone number.
If you own a newer iPhone or Android device, you can also choose to lock your device by using your biometric information, like a scan of your face or thumbprint.
Finally, while it may seem like an annoyance, you should set your device to require a passcode for every attempted unlock. Some devices let their users keep a device unlocked if the passcode was entered within the past 10 minutes, or even an hour. Don’t do that. It leaves your device unnecessarily vulnerable to someone simply picking it up and accessing the important data inside.
Install an antivirus
Now that more cybersecurity companies are taking stalkerware seriously, you have a few options in best protecting yourself and your device.
The free-to-download version of Malwarebytes, available for iOS and Android devices, as well as Mac and PC computers, both detects and removes thousands of malware strings that we’ve identified as stalkerware. Even if you don’t recognize the names of popular stalkerware products, we’re still helping you find and remove them.
The premium version of Malwarebytes, which has a paid subscription, runs a 24-hour defense shield on your device, preventing stalkerware from being implanted on your device.
Practice good link hygiene
Stalkerware typically gets delivered onto a device when someone clicks on a link that has been sent through an email or text. Because of this easy installation process, you should be careful with the links you click.
Do not open any email attachments from unknown senders, and do not click on links sent in text messages from phone numbers you do not recognize.
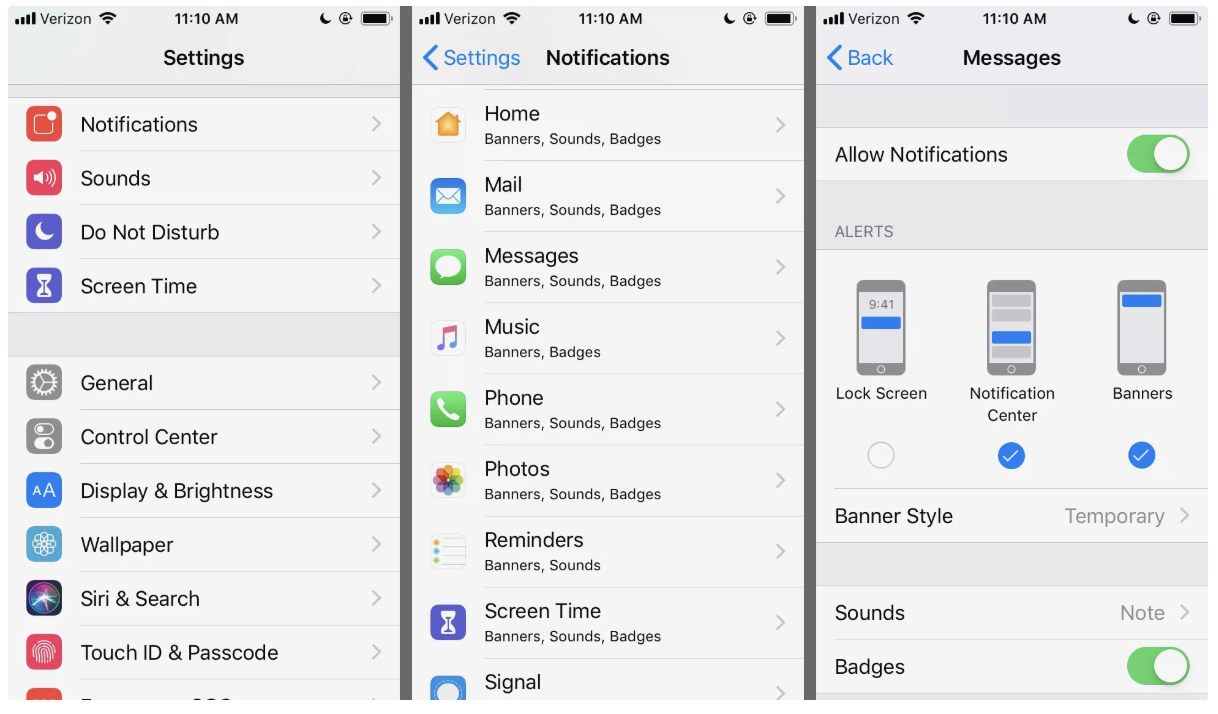
Check your notification settings
While helpful, the notifications that pop up on your device that tell you about the latest news alert or your most recent email have a security vulnerability. Depending on your phone settings, these notifications could reveal—even on your phone’s lock screen—the subject line of an email, the sender, and even the first few words of a text message.
To protect yourself, you can navigate to your device’s system settings and find the specific settings for notifications, blocking them from revealing any details on your lock screen.
On iPhones, you have the option of hiding all notifications, or choosing how notifications are shown: on the Lock Screen, on a pull-down menu, or in banners across the top of your device’s screen.
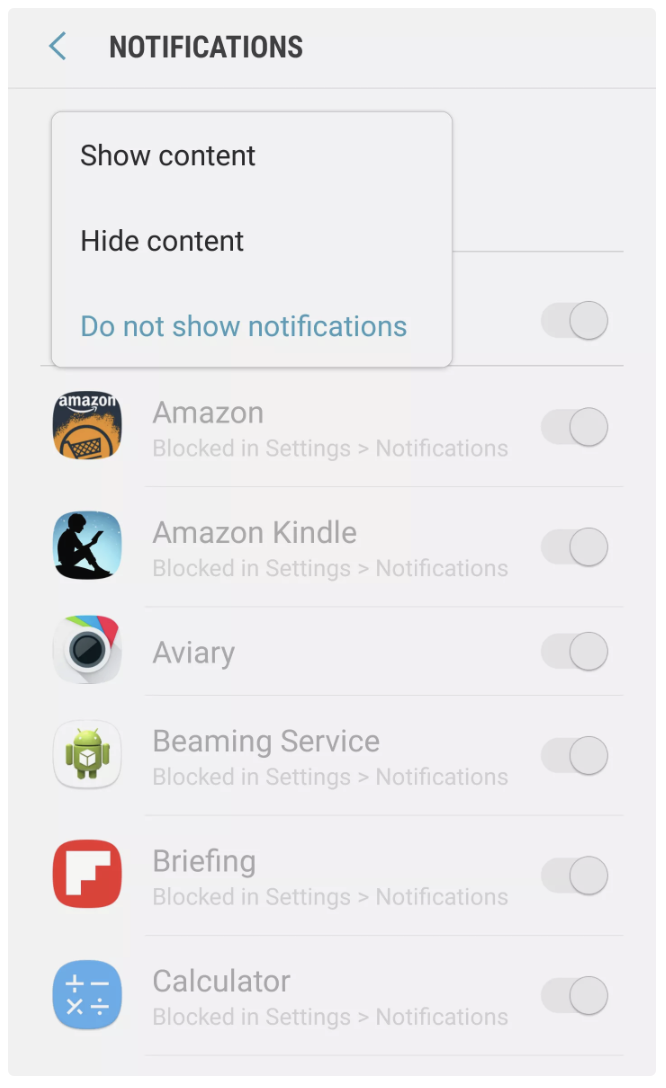
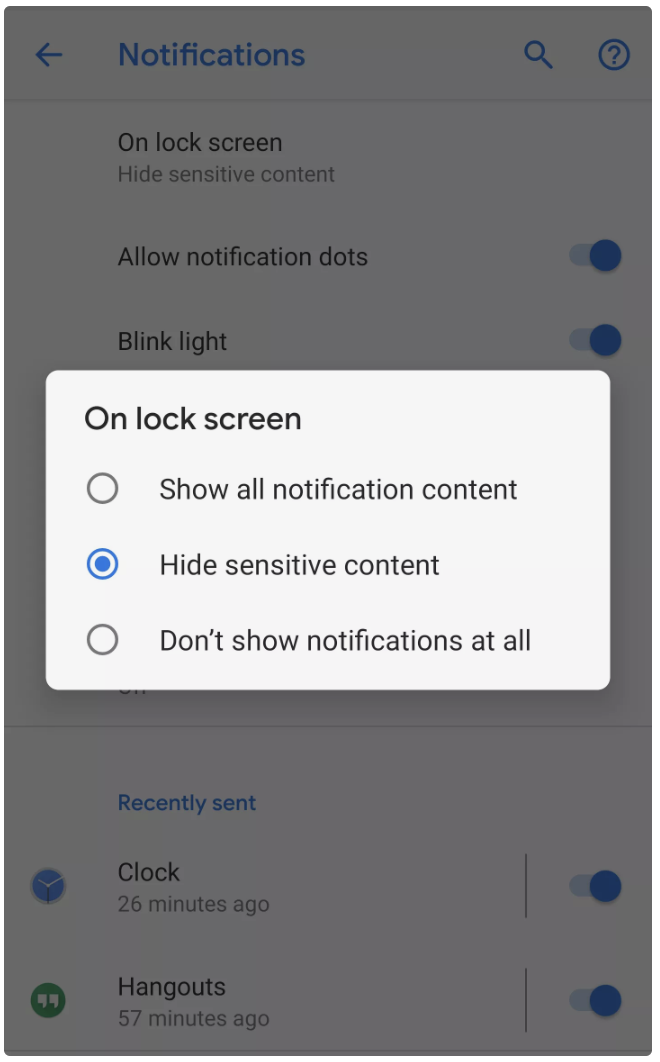
On Android devices, depending on the model, you can again go into your system settings, find the notification settings, and choose whether your notifications will “Show Content” or “Hide Content.”
Update your software
This last step for securing your device has two huge upsides: It’s easy to remember, and it’s extremely useful. Updating your software is the simplest, most efficient way to protect your device from known security vulnerabilities. The longer your software goes without an update, the longer it stays open to cyber threats.
Don’t take the risk.
Securing your sensitive data
Next, we’re going to explain the many ways to secure the data that lives on your device. Maybe you’re thinking of protecting photos that you will eventually send to law enforcement as evidence of abuse. Maybe you want to keep your private conversations private. Or maybe you’re trying to protect the online accounts that you access on your device.
Here are a few ways to protect yourself.
Use a secure messaging app
Secure messaging apps do just that—they keep messages secure. By implementing a feature called end-to-end encryption, these apps prevent third parties from eavesdropping on your conversations. For many of these apps, even the companies that develop them cannot access users’ messages, because those companies do not have the keys necessary to decrypt that data.
There are several options today for both iOS and Android devices, and you may have heard their names—Signal, WhatsApp, iMessage, Wire, and more.
Because there are several options, the important thing to remember is that there is no one, perfect secure messaging app—there is only the right secure messaging app for you. When choosing an app, think about what you need. The domestic abuse survivor who still lives with their partner might need to have their messages erased if their partner somehow finds a way into their device. The domestic abuse survivor with a new device might need to hide their phone number from new contacts.
Here is a brief rundown of some popular secure messaging apps that offer end-to-end encryption:
- iMessage
- Available only on iOS devices
- Requires a text messaging plan through your phone provider
- Apple has fought requests to reveal iMessages
- Signal
- “Ephemeral” messages that disappear entirely after a user’s chosen time limit
- Secondary lock screen to enter the application
- Users can “name” a conversation to obscure contact details. For example, a message thread with “Jane Doe” can be renamed “Mom”
- WhatsApp
- Users can manually clear chats
- Secondary lock screen based on an iPhone’s Face ID credentials
- Wire
- Easiest option for users who want to hide their phone numbers
- Relies on Wire account names to talk to other users
Securing data and online accounts—methods and challenges
There are several methods to protecting the data stored on your device, and each method comes with its own challenges. Below, we look at what you should know when using these methods.
Encrypting your device’s data
Encrypting the data stored on your device means that, if your device is stolen or lost, most anyone who gets their hands on it cannot read the data in any legible form without knowing your passcode. Even if a third party tries to copy the entire contents of your device onto a laptop or desktop computer, your data will still be encrypted and unable to read without your passcode.
Your photos, videos, notes, screenshots, and audio records will all be protected this way, so long as a third party does not have some very high-tech, currently-questionable forensic devices only sold to law enforcement.
On iPhones, your data is encrypted by default, and on Android devices, users can go into their settings and choose to encrypt their data.
The one caveat to remember here is that, if you choose this method to protect sensitive data, if you lose your device, you also lose that data.
Using a secure folder app
On the Apple App store and the Google Play Store, several apps let users choose specific pieces of data that they can encrypt and protect behind a separate passcode that is required to access the app itself.
On the Google Play Store, the app Secure Folder (easy enough name to remember, right?) lets users hide the Secure Folder app itself from appearing in a device’s app menu. This could provide a level of clandestine coverage to domestic abuse survivors who may not have the agency to have a secret, unshared device passcode.
But, if you use a secure folder app that does not have a cloud backup option, the same wrinkle applies—if you lose your device, you lose your data.
Uploading data to the cloud
Let’s talk about cloud storage.
Uploading your data to the cloud has become a popular option for both individuals and businesses that want to access data across multiple devices, removing the concern of losing a specific document, spreadsheet, or presentation because it only rests on one device.
Several popular cloud storage platforms today include iCloud, Google Drive, Dropbox, Box, and Amazon Drive.
Malwarebytes Labs has previously told readers that uploading their data to an encrypted cloud database is a secure model for protecting data, and we stand by that. But cloud storage presents another challenge: Privacy.
Uploading your data to the cloud is inherently not private because, rather than relying on only your device’s storage—whether it’s your phone’s memory or your laptop’s hard drive—you are relying on a separate company to hold your data.
What this means is that using cloud storage is a balancing act of your needs. If your data is for your eyes only, that need won’t be met with cloud storage. But if you want to protect your sensitive data outside of just one device, cloud storage fits that need.
If you do use cloud storage, remember to choose a provider that encrypts users’ data, create and use a secure and complex password that can’t be guessed, and enable two-factor authentication.
What’s two-factor authentication? Oh, right.
Two-factor authentication
Two-factor authentication (2FA), or multi-factor authentication, is a feature you can enable on the important online accounts that hold your banking information, health care info, emails, and social media presence.
By turning on 2FA, you will be telling an online service provider, like Facebook or Gmail, that when you sign in to the service from a new device, you’ll need more than just your password to access your account. You’ll need a second authenticator, which, for many platforms, is delivered to you as a multi-digit code sent in a text message to your mobile device. After you’ve entered the code, only then can you access your online account.
But, because so many 2FA schemes rely on sending a text message with a second code, you have to remember the importance of securing your notification settings. When an online service texts you to verify your account, the 2FA code might show up on your device’s lock screen if you haven’t hidden your notifications. This means that a third party could still log into your account if they are simply near your device and able to read the notifications that pop up.
Takeaways
Protecting your device, and the data on it, can be a long, complicated process, but we hope that some of the tips above help you start that process. If you need help understanding your own safety—and thus, your own available device security options—you can call the domestic abuse advocates at the National Domestic Violence Hotline at 1-800-799-7233.
You’re not alone in this. Stay safe.











